An Economic Perspective on Internet Centrality
What sustains a digital monopoly in today's world? It's not the amassing of a huge workforce, or even having access to large pool of capital. It's not even the use of proprietary technologies that are not accessible to others. So why isn't the Internet fulfilling its vision of profound and intense competitive pressure in every part of the digital supply chain? Whjat is sustaining the domination of the digital world by a select group of behemoths? And, can we change this picture?Kubernetes Security And Networking 4: Helpful Tips To Secure The API Server – Video
In the previous video, Michael Levan walked through some security essentials for protecting worker nodes in a Kubernetes cluster. In this video he focuses on essential protections for the API server. He looks at security benchmarks from CIS, using Kubescape for security scanning, and how to integrate the two. Michael Levan hosts the “Kubernetes Unpacked” […]
The post Kubernetes Security And Networking 4: Helpful Tips To Secure The API Server – Video appeared first on Packet Pushers.
Network Break 420: Cisco, HPE Buy Security Startups; Can We Finally Hold Vendors Responsible For Software Defects?
Take a Network Break! We begin with some FU on what constitutes on-prem and off-prem, and then dive into news. Cisco and T-Mobile are partnering on 5G gateways, Cisco Webex is getting installed as a feature(?) in Mercedes E-Class cars, and Cisco is buying multi-cloud security startup Valtix. Valtix offers firewalling, IPS, a cloud Web […]
The post Network Break 420: Cisco, HPE Buy Security Startups; Can We Finally Hold Vendors Responsible For Software Defects? appeared first on Packet Pushers.
Network Break 420: Cisco, HPE Buy Security Startups; Can We Finally Hold Vendors Responsible For Software Defects?
Take a Network Break! We begin with some FU on what constitutes on-prem and off-prem, and then dive into news. Cisco and T-Mobile are partnering on 5G gateways, Cisco Webex is getting installed as a feature(?) in Mercedes E-Class cars, and Cisco is buying multi-cloud security startup Valtix. Valtix offers firewalling, IPS, a cloud Web... Read more »Five Things You Need for Today’s Network Monitoring
By extending into environments such as the cloud, SD-WAN, and applications, today's network monitoring platforms are turning into powerful solution that can improve the overall operations IT environment. Let's drill down into the top five needs for networking monitoring.
The post Five Things You Need for Today’s Network Monitoring appeared first on Packet Pushers.
DDoS detection and remediation with Akvorado and Flowspec
Akvorado collects sFlow and IPFIX flows, stores them in a ClickHouse database, and presents them in a web console. Although it lacks built-in DDoS detection, it’s possible to create one by crafting custom ClickHouse queries.
DDoS detection
Let’s assume we want to detect DDoS targeting our customers. As an example, we consider a DDoS attack as a collection of flows over one minute targeting a single customer IP address, from a single source port and matching one of these conditions:
- an average bandwidth of 1 Gbps,
- an average bandwidth of 200 Mbps when the protocol is UDP,
- more than 20 source IP addresses and an average bandwidth of 100 Mbps, or
- more than 10 source countries and an average bandwidth of 100 Mbps.
Here is the SQL query to detect such attacks over the last 5 minutes:
SELECT * FROM ( SELECT toStartOfMinute(TimeReceived) AS TimeReceived, DstAddr, SrcPort, dictGetOrDefault('protocols', 'name', Proto, '???') AS Proto, SUM(((((Bytes * SamplingRate) * 8) / 1000) / 1000) / 1000) / 60 AS Gbps, uniq(SrcAddr) AS sources, uniq Continue reading
netlab: Change Stub Networks into Loopbacks
One of the least-documented limitations of virtual networking labs is the number of network interfaces a virtual machine could have. vSphere supports up to 10 interfaces per VM, the default setting for vagrant-libvirt is eight, and I couldn’t find the exact numbers for KVM. Many vendors claim their KVM limit is around 25; I was able to bring up a Nexus 9300v device with 40 adapters.
Anyway, a dozen interfaces should be good enough if you’re building a proof-of-concept fabric, but it might get a bit tight if you want to emulate plenty of edge subnets.
netlab: Change Stub Networks into Loopbacks
One of the least-documented limitations of virtual networking labs is the number of network interfaces a virtual machine could have. vSphere supports up to 10 interfaces per VM, the default setting for vagrant-libvirt is eight, and I couldn’t find the exact numbers for KVM. Many vendors claim their KVM limit is around 25; I was able to bring up a Nexus 9300v device with 40 adapters.
Anyway, a dozen interfaces should be good enough if you’re building a proof-of-concept fabric, but it might get a bit tight if you want to emulate plenty of edge subnets.
Why Application Security is Critical to Network Security
Application security is inseparable from network security. As such, enterprises must now take a holistic approach to securing networks and the applications within them.Controversial Reads 030423
A major escalation in official online censorship regimes is progressing rapidly in Brazil, with implications for everyone in the democratic world. Under Brazil’s new government headed by President Lula da Silva, the country is poised to become the first in the democratic world to implement a law censoring and banning “fake news and disinformation” online, and then punishing those deemed Continue reading
Gravity Model
Motivation
I recently read Google’s latest sigcomm paper: Jupiter Evolving on their Datacenter fabric evolution. It is an excellent paper with tons of good information, and the depth and width show what an engineering thought process should look like. The central theme talks about the challenges faced with deploying and scaling Clos fabrics and how they have evolved by replacing the spine layer with OCS that allows the blocks to be directly connected, calling it Direct connect topology.
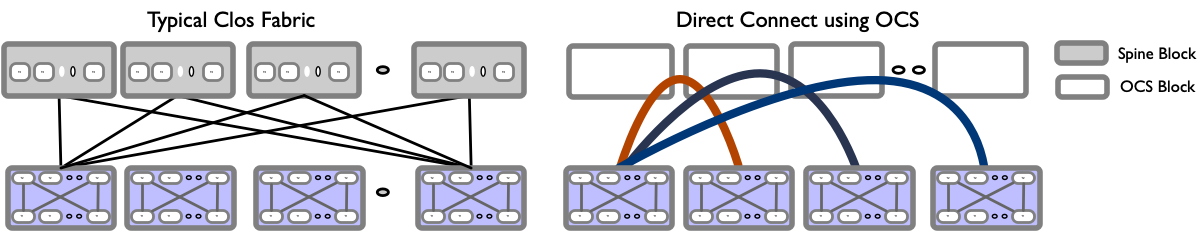
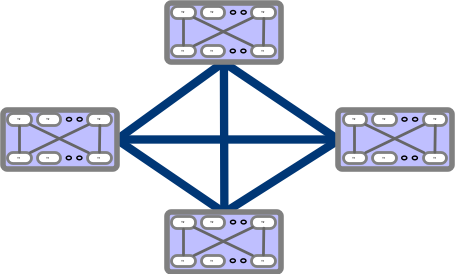
If you look closely, the Direct Connect topology resembles Dragonfly+, where you have directly connected blocks.
The paper has many interesting topics, including Traffic and Topology Engineering and Traffic aware routing. One of the most exciting parts to me, which will be understandably missing, is the formulation of Traffic engineering problems as Optimization problems. I would love to see some pseudo-real-world code examples made publicly available.
However, one thing that surprised me the most was from a Traffic characteristics perspective, a Gravity model best described Google’s Inter-Block traffic. When I studied Gravity Model, I thought this was such a simplistic model that I would never see that in real life, but it turns out I was wrong, and it still has practical Continue reading
Gravity Model
Motivation I recently read Google’s latest sigcomm paper: Jupiter Evolving on their Datacenter fabric evolution. It is an excellent paper with tons of good information, and the depth and width show what an engineering thought process should look like. The central theme talks about the challenges faced with deploying and scaling Clos fabrics and how they have evolved by replacing the spine layer with OCS that allows the blocks to be directly connected, calling it Direct connect topology.Datacenter System Makers Leary But Not Weary
The central banks of the world, led by the European Central Bank and the US Federal Reserve, want to curb inflation and they are willing to cause a small recession or at least get very close to one to shock us all into controlling the acquisitive habits we developed during the lockdowns of the early years of the coronavirus pandemic. …
Datacenter System Makers Leary But Not Weary was written by Timothy Prickett Morgan at The Next Platform.
Heavy Networking 668: Inside A Virtualization Consultant’s Home Lab
On Heavy Networking today we look at a home lab running VMware products including NSX, as well as infrastructure-as-code products Terraform, Packer, and Ansible. These use cases create a different hardware demand than virtualized network operating system images. Guest Maarten Van Driessen explains it all, including how he saves money on lab gear.
The post Heavy Networking 668: Inside A Virtualization Consultant’s Home Lab appeared first on Packet Pushers.
 s vulnerabilities — which so many young people share online.
s vulnerabilities — which so many young people share online.