Docker Compose and Docker Machine, Swarm, Compose Interworking
This is a continuation of my previous 2 blogs on Docker machine, Swarm. In this blog, I will cover Docker Compose and how Docker Machine, Swarm and Compose can work with each other. The interworking part is actively being developed by Docker team and is still at the preliminary stages. Docker Compose: Docker Compose comes from … Continue reading Docker Compose and Docker Machine, Swarm, Compose InterworkingDocker Swarm
This is a continuation of my previous blog on Docker machine. In this blog, I will cover Docker Swarm. Swarm manages a set of Docker nodes as a single cluster. This has the following advantages: Rather than managing individual Docker nodes, the cluster can be managed as a single entity. Swarm has an in-built scheduler … Continue reading Docker SwarmDocker Machine
As part of Docker Orchestration, Docker has released 3 new tools Machine, Swarm, Compose. In the last few weeks, I was playing with these tools and I will share my experiences in this blog. I will start with Docker machine in this blog and I will cover Swarm, Compose in the next set of blogs. Only … Continue reading Docker MachineConnecting VMs between Virtualbox and VMWare Player
I had written blogs earlier on using Virtualbox and VMWare Player. I recently had a need to connect VMs running on Virtualbox and VMWare player. This is for my Windows laptop. I found the procedure mentioned in this link to be very useful. There are 2 options. Use bridged mechanism. Create a networking interface with … Continue reading Connecting VMs between Virtualbox and VMWare PlayerAccess-list Vs Prefix-list
General Query about access-list and prefix list ?
ACCESS-LIST
Access-list is sequential series of filters
Action :Either deny or permit
Matching Criteria can be source address in case of standard access-list or may be source address ,destination address,protocol,port or socket in case of extended access-list.
Its Implicit Deny means that no match occur through all filter in access-list ,it will tend to automatically dropped.
Its sequential,means that filter is checked from top to bottom.If the first match is encountered,the rest of the access -list is ignored.
**Always try to put filtering line in right sequence to avoid access-list mulfunctioning.
Standard Access-list
access-list 1 permit 10.10.10.1 0.0.0.0
access-list 1 permit 10.10.10.20 0.0.0.0
OR
ip access-list standard 1
10 permit 10.10.10.1 0.0.0.0
20 permit 10.10.10.20 0.0.0.0
Extended Access-list
access-list 100 permit ip 10.10.10.10 0.0.0.0 172.16.10.0 0.0.0.255
access-list 111 permit port access-list 111 permit tcp 10.0.0.0 0.255.255.255 172.1.141.0 0.0.0.255 eq 23
access-list 112 permit udp Continue reading
P4 Language Aims to Take SDN Beyond OpenFlow
 Jennifer Rexford and Nick McKeown have kicked off what could be the next generation of SDN.
Jennifer Rexford and Nick McKeown have kicked off what could be the next generation of SDN.
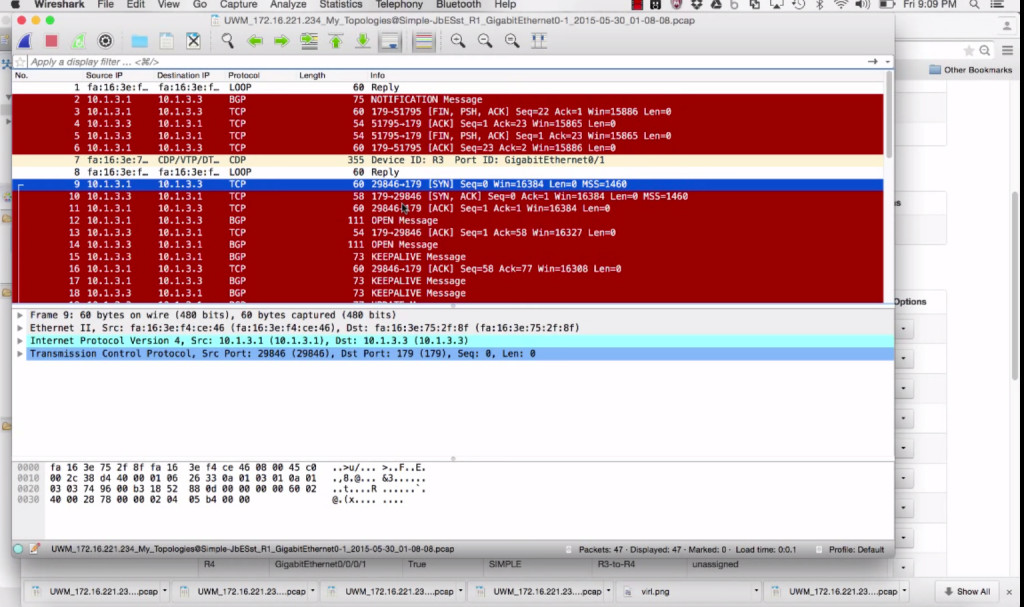
YouTube: Packet Capturing with VIRL
Tried VIRL when it first came out. “Why?”, you ask, when you know I work in a Cisco Customer Proof of Concept lab with lots of “real” networking hardware? Answer is because it would be nice to be able to toss together networks to play with… without having to reserve gear, load line cards that are on shelves into empty chassis, cable, code, config… etc etc.
But there was, for me, a major item missing from VIRL when it first came out — the ability to packet capture easily. For what I wanted VIRL for, that was a showstopper for me. So, back into the lab for my “playing” and teaching.
Now?  Very very happy to pass on to you that VIRL supports packet capturing now!!! Tossed together a quick ~12minute youtube.
Very very happy to pass on to you that VIRL supports packet capturing now!!! Tossed together a quick ~12minute youtube.
Think Bigger
I get frustrated by those who take a narrow view of technology, and progress in general. They see things in terms of where they are now, and where they were. But they struggle to see a bit further out. The Internet of Things is a good example of this.
I made the mistake of reading the comments on a recent El Reg article (I know, I know: Never read the comments). I came across this comment about the IoT:
…The innocent child asked “but why would the toaster need to talk to the ‘fridge?” The marketing gurus had no answer and a few years later the outfit went bankrupt. In all the time since, no one has been able to answer that question.
From there the comments devolved into a rather pointless discussion about milk, bread, spam on toast and Twitter. This is a fairly common theme on El Reg articles (along with “cloud has little appeal for 90% of SM server/computing requirements”, but that’s another issue).
I find it frustrating when people take a narrow, short-sighted view when looking at technology trends. We all see things from our own perspective, but it’s good to lift your head Continue reading
SDxCentral Weekly News Roundup — May 29, 2015
 Executive moves at Cisco and Ruckus, new training at Juniper, and a DevOps-minded monitoring startup.
Executive moves at Cisco and Ruckus, new training at Juniper, and a DevOps-minded monitoring startup.
iPexpert’s Newest “CCIE Wall of Fame” Additions 5/29/2015
Please join us in congratulating the following iPexpert students who have passed their CCIE lab!
This Week’s CCIE Success Stories
- Garrison Botts, CCIE #48589 (Data Center)
- Craig Stork, CCIE #48824 (Wireless)
We Want to Hear From You!
Have you passed your CCIE lab exam and used any of iPexpert’s self-study products, or attended a CCIE Bootcamp? If so, we’d like to add you to our CCIE Wall of Fame!