Cumulus: Watch Out, Cisco, White Box Is Coming
 Price cuts are what's keeping hardware switch sales looking strong, Cumulus claims.
Price cuts are what's keeping hardware switch sales looking strong, Cumulus claims.
SDN: What Small and Mid-Sized Businesses Need to Know in 2015
by Alex Hoff, originally published on Packet Pushers Network industry pundits are calling for 2015 to be the year of software-definedA New Home: Looking Back
I have moved to a new blogging platform! The timing was interesting, since the wordpress installation on which Keeping It Classless has operated for so long is about 5 years old (I operated on an older domain before Keeping It Classless was born).
WOW. Five years is a long time in blog years. I could not have possibly predicted back then what this blog would do for me. In going over these old posts, I saw a very interesting progression of my own skillsets and mentality, and I figured I’d share. Call it a thank you for helping me grow the past 5 years. Please forgive the length of this post, but I wanted to make sure to call out everything of significance.
It’s also been crazy to witness the change in writing style. Early on I was not shy about using idioms, memes, and Borat references in blog posts, and now - while I am still humorous from time to time - I am a little more formal and succinct. Another way of looking at it is that early on, there was very little difference between the way that I wrote and the way that I spoke. Today, there Continue reading
Eschew Obfuscation (Communicate Clearly)
Many years ago, I worked for a manager who had two signs on his desk. The first was a pencil with the words, “Pencil 2.0″ printed above them. The rest of the sign went on to explain how the pencil had undo (the eraser), was renewable (it can be sharpened), etc. The second sign was simpler, just two black words printed across a white background.
Eschew Obfuscation
Being just out of the US Air Force, and not having quite the vocabulary I should have (have I ever told you that reading is the key to having a great vocabulary?), I didn’t really understand the point. Now I do. Okay, to make it more obvious, from the Collins English Dictionary, 8th edition:
eschew: tr to keep clear of or abstain from (something disliked, injurious, etc.); shun; avoid
obfuscation: the act or an instance of making something obscure, dark, or difficult to understand
Now do you see? Avoid using language people can’t understand. Far too often, in the technical world, we use abbreviations, acronyms, and all sorts of cute nonsense to say things. We pepper our language with shorthands and inside jokes (squirrel!). While this sometimes helps communication, Continue reading
Where are we with SDN in May 2015 ?
There is so much to talk about in SDN that I couldn’t finish any of the dozen or so blog posts that I started in the last three weeks. Instead I created a 15 minute Keynote presentation that had the key points that I wanted to blog about.
The post Where are we with SDN in May 2015 ? appeared first on EtherealMind.
On I-Shaped and T-Shaped Skills
Several of the conversations I had at the recent RIPE70 meeting were focused on career advice (usually along the lines of “which technology should I focus on next”) and inevitably we ended up discussing the benefits of T-shaped skills versus I-shaped skills… and I couldn’t resist drawing a few graphs illustrating them.
Read more ...A New Home: Looking Back
I have moved to a new blogging platform! The timing was interesting, since the wordpress installation on which Keeping It Classless has operated for so long is about 5 years old (I operated on an older domain before Keeping It Classless was born). WOW. Five years is a long time in blog years. I could not have possibly predicted back then what this blog would do for me. In going over these old posts, I saw a very interesting progression of my own skillsets and mentality, and I figured I’d share.A New Home: Looking Back
I have moved to a new blogging platform! The timing was interesting, since the wordpress installation on which Keeping It Classless has operated for so long is about 5 years old (I operated on an older domain before Keeping It Classless was born). WOW. Five years is a long time in blog years. I could not have possibly predicted back then what this blog would do for me. In going over these old posts, I saw a very interesting progression of my own skillsets and mentality, and I figured I’d share.YAMware Old Malware can still be fun!
YAMware Old Malware can still be fun!
(Side note, this blog post was written and then forgotten about quite a while ago, So I’ve finished it off, it was halfway done.)
While on holiday in the evenings with downtime to spare, I had realised that
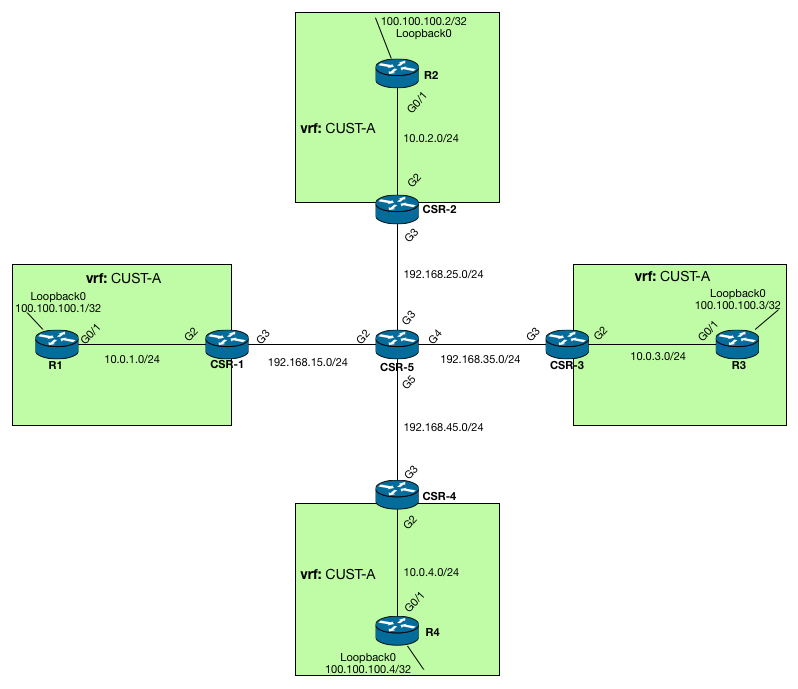
MPLS VPN’s over mGRE
This blog post outlines what “MPLS VPNs over mGRE” is all about as well as provide an example of such a configuration.
So what is “MPLS VPNs over mGRE”? – Well, basically its taking regular MPLS VPN’s and using it over an IP only core network. Since VPN’s over MPLS is one of the primary drivers for implementing an MPLS network in the first place, using the same functionality over an IP-only core might be very compelling for some not willing/able to run MPLS label switching in the core.
Instead of using labels to switch the traffic from one PE to another, mGRE (Multipoint GRE) is used as the encapsulation technology instead.
Be advised that 1 label is still being used however. This is the VPN label that’s used to identify which VRF interface to switch the traffic to when its received by a PE. This label is, just as in regular MPLS VPN’s, assigned by the PE through MP-BGP.
So how is this actually performed? – Well, lets take a look at an example.
The topology I will be using is as follows:
** Note: I ran into an issue with VIRL, causing Continue reading