CloudFlare’s New Dashboard
When we started CloudFlare, we thought we were building a service to make websites faster and more secure, and we wanted to make the service as easy and accessible as possible. As a result, we built the CloudFlare interface to put basic functions front and center and designed it to look more like a consumer app than the UI for the powerful network it controlled.
Over time, we realized there was a lot more to CloudFlare. In 2011, we added the concept of Apps, and a myriad of additional performance and security features from Rocket Loader to Railgun were added too. All these additional settings got buried under a lowly gear menu next to each site in a customer's account.
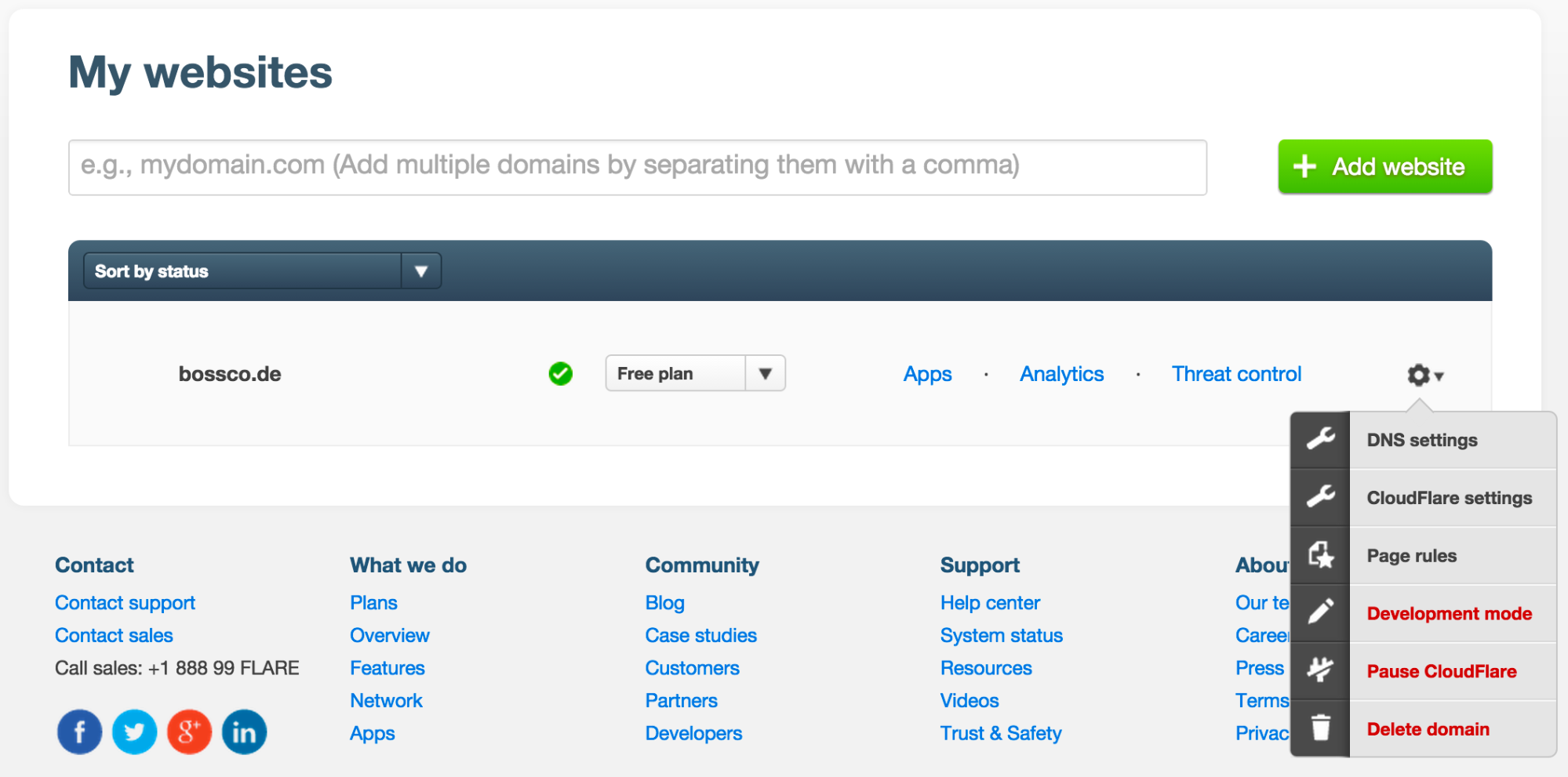
While still easier to navigate than the average enterprise app, using our UI could be a frustrating experience. For instance, imagine you wanted to turn on Rocket Loader for multiple sites. You'd have to go to My Websites, click the gear menu next to one of your domains, navigate to CloudFlare Settings, select the Performance Settings tab, scroll to Rocket Loader, then toggle it on. Then you had to go back to My Websites and repeat the process again for Continue reading
DMVPN for IPv6
As you probably already know, every DMVPN network consists of multiple GRE tunnels that are established dynamically. At the beginning, every Spoke in the Cloud is supposed to build a direct tunnel to the Hub. Then, once the Control Plane converges, the Spokes can possibly build tunnels with other DMVPN device(s), of course assuming that our DMVPN deployment (aka “Phase”) allows for that.
In most cases DMVPN tunnels will be deployed over an IPv4 backbone, interconnecting different sites running IPv4. But since GRE is a multi-protocol tunneling mechanism, we can use it to carry different protocol traffic, like for example IPv6. Frankly, in the newer versions of IOS code you could even change the underlying transport from IPv4 to IPv6. This basically means that you can use an IPv4 OR IPv6 network to tunnel IPv4 OR IPv6 traffic.
In this particular article I am going to discuss a scenario in which the Transport/NBMA network (“Underlay”) uses IPv4 addresses, but the goal will be to use the DMVPN to interconnect sites enabled only for IPv6.
As you can see from the topology below, our private sites are configured with prefixes starting with 2192:1:X::/64, and the VPN (“Overlay”) subnet used is Continue reading
Hacking Lessons From Security Compass’ Battle School
 What I learned in hacking school.
What I learned in hacking school.
Musing: Generalist to Specialist and Back Again
Recently I’ve been musing on IT Generalists vs Specialists. We used to have more generalist roles, covering all parts of the stack. ITIL then pushed us towards greater specialisation. I believe that we’ve gone back to valuing the Generalist, as the person who can glue components together. Will the pendulum swing again?
Generalists: Soup-to-Nuts
When I started working in IT, our roles were more generalist in nature. We did everything. To set up a new app, we racked the servers and switches, installed the OS, configured the network, installed the DB & application, and made it all work.
We weren’t specialists in any one area, but we knew how everything fitted together. So if something broke, we could probably figure it out. If we had to investigate a problem, we could follow it through all layers of the stack. When we found the problem, we had license to fix it.
ITIL takes over: Specialisation
Sometime around the early-mid 2000s the “ITIL Consultants” moved in. Their talk of structure, processes and SLAs seduced senior management. We couldn’t just have people who Got Shit Done. No, everyone needed to be placed in a box, with formal definitions around what they could & Continue reading
Auvik Release Notes – April 23 – RDP, VNC & UPS monitoring!
NEW! Remote Desktop & VNC Need to remotely log into a machine and troubleshoot? Say good-bye to clunky VPNs. Now you can launch aMay Mission: Bring home the bacon with Auvik
This month, we're pretty stoked to partner with our good friends at Auvik for our May "Sizzler" mission. This mission will get you usingVerizon’s Carrier SDN Makeover Includes Just About Everybody
 All the big vendors (well, not Huawei) get a piece of the action as Verizon goes all-in with SDN.
All the big vendors (well, not Huawei) get a piece of the action as Verizon goes all-in with SDN.
Last Call for the HP & SDxCentral NFV Report Webinar!
 Want to learn more about our 2015 NFV report? Sign up for the April 29th HP & SDxCentral NFV Report Webinar!
Want to learn more about our 2015 NFV report? Sign up for the April 29th HP & SDxCentral NFV Report Webinar!
Earthquake rocks Internet in Nepal

Saturday’s earthquake in Nepal, which claimed the lives of at least 4,000 victims and injured many more, took a toll on the country’s Internet connectivity, which was already one of the least developed in the region. A recent evaluation of Internet infrastructure in South Asia commissioned by the United Nations Economic and Social Commission for Asia and the Pacific (ESCAP) classified Nepal’s international connectivity as ‘weak’ and its fixed and mobile infrastructure as ‘limited’.

While the loss of Internet connectivity pales in comparison to the loss of life, the ability to communicate both domestically and internationally will be crucial in coming days for the coordination of relief efforts already underway. Innovative services from Facebook and Google to facilitate communicating the status of those affected by the massive earthquake would be largely useless if Nepal had been knocked entirely offline. In fact, Nepal’s international links generally survived the earthquake, however last mile connectivity is another matter.
As we reported on Saturday, we began seeing severe Internet outages and instabilities immediately following the earthquake at 6:11 UTC. On the left is a timeline of outages through today and on the right is the volume of DNS queries Continue reading
Why numbering should start at zero?
How does Internet work - We know what is networking
Please note: This has nothing to do with networking in particular! Not if you look from only one perspective. If you look from totally different perspective, with Cisco ACI and all other SDN solutions, you will probably meet with Python programming language (because you will) and then, somewhere in beginning of Python exploration this is the first question that will cross your mind. Of course, if you think like me! Although not directly related to networking, the question bothered me for some time now and the answer is not only really logical when you read it but it is also