How portable is your network operating system?
Conversations are swirling throughout the tech industry about whether white box switches are disrupting the networking industry, similarlyShow 216 – HP & SDN In The Campus – Sponsored
At HP Discover Barcelona 2014, the Packet Pushers had the chance to chat with Heather Giovanni, Craig Mills, and Chris Young about the HP 5400R and SDN in the campus. HP has a full line of switches and routers that some know about, and some just haven’t yet explored. The 5400R is a multi-slot chassis […]
Author information
The post Show 216 – HP & SDN In The Campus – Sponsored appeared first on Packet Pushers Podcast and was written by Ethan Banks.
Facebook Next-Generation Fabric
Facebook published their next-generation data center architecture a few weeks ago, resulting in the expected “revolutionary approach to data center fabrics” echoes from the industry press and blogosphere.
In reality, they did a great engineering job using an interesting twist on pretty traditional multi-stage leaf-and-spine (or folded Clos) architecture.
Read more ...CoreOS – Getting your second (and 3rd) host online
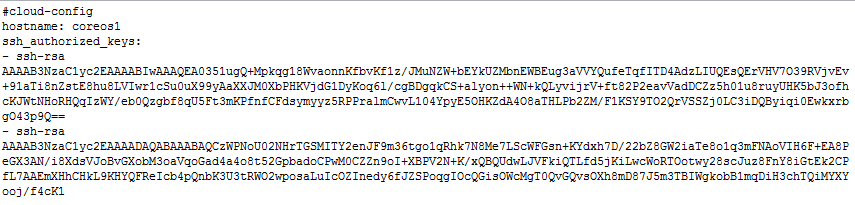
Quick note: For the sake of things formatting correctly on the blog I’m using a lot of screenshots of config files rather than the actual text. All of the text for the cloud-configs can be found on my github account here – https://github.com/jonlangemak/coreos/
Now that we have our first CoreOS host online we can start the cool stuff. We’re going to pick up where we left off in my last post with our first installed CoreOS host which we called ‘coreOS1’. Recall we had started with a very basic cloud-config that looked something like this…
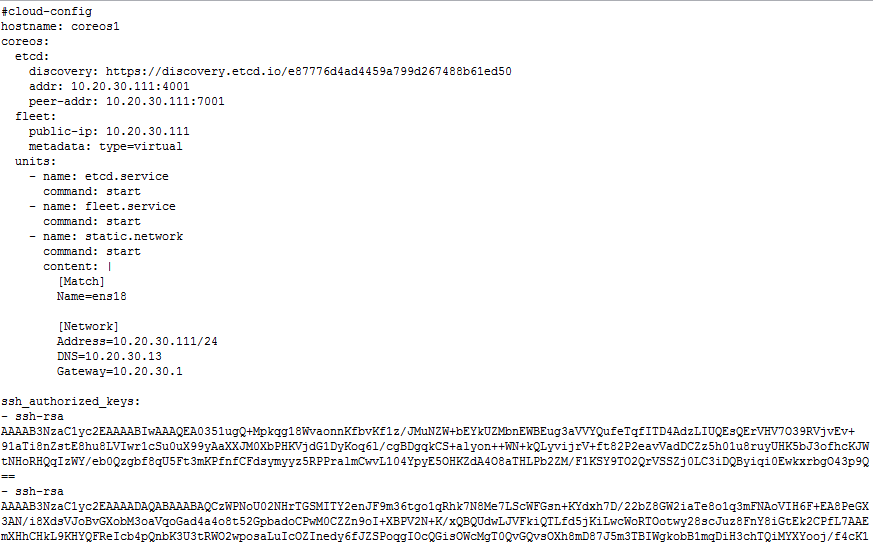
All this really did was get us up and running with a DHCP address and the base system services running. Since we’re looking to do a bit more in this post, we need to add some sections to the cloud-config. Namely, I’m going to configure a static IP address for the host, configure and start etcd, and configure and start fleet. So here’s what my new cloud config for coreOS1 will look like…
So there’s a lot more in this cloud-config. This config certainly deserves some explaining. However, in this post, I want to just get Continue reading
3 Ways To Get Started With VMware NSX
Over the past 12 months, VMware NSX momentum has continued to grow, as we’ve added  new platform capabilities, expanded our partner ecosystem, and of course, had more than 250+ customers purchase NSX for deployment. And as interest in VMware NSX has grown with both customers and IT professionals looking to evolve their careers by adding certification in network virtualization, one of the most common questions that we get is “How can I get started with NSX?.”
new platform capabilities, expanded our partner ecosystem, and of course, had more than 250+ customers purchase NSX for deployment. And as interest in VMware NSX has grown with both customers and IT professionals looking to evolve their careers by adding certification in network virtualization, one of the most common questions that we get is “How can I get started with NSX?.”
We understand that there is a strong demand for individuals and organizations to get their hands on the NSX technology. Many of you are working towards your initial VCP-NV certification. Others of you are exploring NSX as a way to improve your organization’s agility and security while reducing overall costs.
Here are three ways individuals and companies can get started with NSX.
Complete NSX: Install, Configure, Manage Training – for individuals on the NSX career path, we offer “NSX: Install, Configure, Manage” training. We are offering ICM training as part of our On-Demand Curriculum, or you can take a 5-day instructor led course. Here is the detailed course description and class schedule. ICM training is a pre-requisite for VMware NSX certification. Once Continue reading
Some common networking operations in Perl
A collection of various network- and socket API-related functions with code snippets.2014 in review
Looking back at 2014, it feels like a lot of progress was achieved in the past year in both the cloud infrastructure and NFV infrastructure markets. Some of that progress is technical, some is in terms of increased understanding of the key business and technical aspects. This post is my attempt to capture some changes I’ve observed from my particular vantage point.
This December marks the second anniversary of the acquisition of Contrail Systems by Juniper Networks. In the last year the Contrail team managed to deploy the Contrail network virtualization solution in several marquee customers; to solidify the image of the OpenContrail project as a production-ready implementation of the AWS VPC functionality; but, probably, more importantly to help transform attitudes at Juniper (and in the industry) regarding NFV.
In the late 90s and early naughts, the carrier wireline business went through a significant change with the deployment of provider managed virtual networks (using BGP L3VPN). From a business perspective, this was essentially outsourcing the network connectivity for distributed enterprises. Instead of a mesh of frame relay circuits managed by the enterprise; carriers provide a managed service that includes the circuit but also the IP connectivity. This is a service Continue reading
Will I Be Blogging Again?
Dan wrote in with a question:
Hey, I like your site as well… are you going to be doing any more posts? It just seems odd that your last blog post was the analyzation of the site and how it portends to your future work. anyway, good luck
I know it’s tacky to write a blog post about how you’re not writing enough blog posts… but here goes.
Yes, I will be blogging again. And I have lots of content ideas. And I’m actually itching to get back to writing. I’ve been working on something else for the past few months and I decided I couldn’t take that on and blog at the same time. So for now my writing is on hold, however I do see and respond to all comments in the articles and am reachable via email as well.
Thanks to everyone who reads and posts comments. I look forward to writing more posts in the new year!
Copyright Joel Knight. All Rights Reserved.
www.packetmischief.ca
The Resolvers We Use
The theme of a workshop, held at the start of December 2014 in Hong Kong, was the considerations of further scaling of the root server system, and the 1½ day workshop was scoped in the form of consideration of approaches to that of the default activity of adding further anycast instances of the existing 13 root server anycast constellations. This was a workshop operating on at least three levels. Firstly there was the overt agenda of working through a number of proposed approaches that could improve the services provided by the DNS root service. The second was an unspoken agenda concerned with protecting the DNS from potential national measures that would “fragment” the DNS name space into a number of spaces, which includes, but by no means not limited to, the DNS blocking activities that occur at national levels. The third level, and an even less acknowledged agenda, is that there are various groups who want to claim a seat at the Root Server table.More education needed to realize the Internet of Everything
The Internet of Everything (IoE) is essentially about connections, bringing people, processes, data and things together in unprecedented ways. IoE delivers the right information to the right person (or machine) at the right time, and converts data into intelligence to make better decisions.
Organizations will use the connections made by IoE to transform our work and private lives, creating smarter products and services, more convenience for consumers and new forms of work-life integration. However, in order to capitalize on these connections, organizations will need well-trained staff. Cisco predicts that approximately 220,000 new engineers will be needed globally every year for the next 10 years to keep up with the technological surge of IoE. This is a gap that must be filled if the potential of IoE is to be realized.
To read this article in full or to leave a comment, please click here
iWARP update advances RDMA over Ethernet for data center and cloud networks
The challenge for data center operators selecting a high performance transport technology for their network is striking the ideal balance between acquisition, deployment and management costs, and support for high performance capabilities such as the remote direct memory access (RDMA) protocol.
The iWARP protocol is the open Internet Engineering Task Force (IETF) standard for RDMA over Ethernet, and offers an interchangeable, RDMA verbs-compliant alternative to specialized fabrics such as InfiniBand. iWARP adapters are fully supported within the Open Fabrics Alliance Enterprise software distribution (OFED), with typically no changes needed for applications to migrate from InfiniBand to Ethernet.
To read this article in full or to leave a comment, please click here
Community Podcast: 8xCCIE Neil Moore and Orhan Ergun – CCIE Preparation
Neil Moore is the first and only 8 x CCIE in the world. Neil shares his CCIE preparation tricks, study methodology and many other important points.
Author information
The post Community Podcast: 8xCCIE Neil Moore and Orhan Ergun – CCIE Preparation appeared first on Packet Pushers Podcast and was written by Orhan Ergun.
Community Podcast: 8xCCIE Neil Moore and Orhan Ergun – CCIE Preparation
Neil Moore is the first and only 8 x CCIE in the world. Neil shares his CCIE preparation tricks, study methodology and many other important points.
The post Community Podcast: 8xCCIE Neil Moore and Orhan Ergun – CCIE Preparation appeared first on Packet Pushers.
4 Inevitable Questions When Joining a Monitoring Group, Pt.3
Leon Adato, Technical Product Marketing Manager with SolarWinds is our guest blogger today, with a sponsored post — the third in a four-part series on the topic of alerting. In the last two posts in this series, I described two of the four (ok, really five) questions that monitoring professionals are frequently asked: Why did […]
Author information
The post 4 Inevitable Questions When Joining a Monitoring Group, Pt.3 appeared first on Packet Pushers Podcast and was written by Sponsored Blog Posts.
Packet Flow with FirePower.
As I was going through some CiscoLive365 sessions (Remember CiscoLive365 is great!) just this last weekend I came across the slides for BRKSEC-2028 – Deploying Next Generation Firewall with ASA & Firepower services. Unfortunately there is no video for this session yet but the presentation slides are there and luckily the slides are detailed enough so […]DHCP Snooping – Filter those broadcasts!
I had a specific requirement recently and I wanted to test it’s behaviour. In particular the feature is DHCP snooping. Let’s quickly go over the DHCP process at a high level to see how it works: DHCP Let’s take the following simple diagram to show what’s going on. We have a switch with two hosts […]The Network as a Complex Distributed System
Through http://blog.ipspace.net I landed on this article on acm.org discussing the complexity of distributed systems. Through some good examples, George Neville-Neil makes it clear that creating and scaling distributed systems is very complex and “any one that tells you it is easy is either drunk or lying, and possibly both”.
Networks are of course inherently distributed systems. Most everyone that has managed a good sized network before knows that like the example in the article, minor changes in traffic or connectivity can have huge implications on the overall performance of a network. In my time supporting some very large networks I have seen huge chain reactions of events based on what appear to be some minor issues.
Very few networks are extensively modeled before they are implemented. Manufacturers of machines, cars and many other things go through extensive modeling to understand the behaviors of what they created and their design choices. Using modeling they will look at all possible inputs and outputs, conditions, failure scenarios and anything else we can think of to see how their product behaves.
There are few if any true modeling tools for networks. We build networks with extensive distributed protocols to control connectivity Continue reading
Performance Tests and Out-of-Box Performance
Simonp made a perfectly valid point in a comment to my latest OVS blog post:
Obviously the page you're referring to is a quick-and-dirty benchmark. If you wanted the optimal numbers, you would have to tune quite a few parameters just like for hardware benchmarks (sysctl kernel parameters, Jumbo frames, ...).
While he’s absolutely right, this is not the performance data a typical user should be looking for.
Read more ...InfluxDB and Grafana
Cluster performance metrics describes how to use sFlow-RT to calculate metrics and post them to Graphite. This article will describe how to use sFlow with the InfluxDB time series database and Grafana dashboard builder.The diagram shows the measurement pipeline. Standard sFlow measurements from hosts, hypervisors, virtual machines, containers, load balancers, web servers and network switches stream to the sFlow-RT real-time analytics engine. Over 40 vendors implement the sFlow standard and compatible products are listed on sFlow.org. The open source Host sFlow agent exports standard sFlow metrics from hosts. For additional background, the Velocity conference talk provides an introduction to sFlow and case study from a large social networking site.
It is possible to simply convert the raw sFlow metrics into InfluxDB metrics. The sflow2graphite.pl script provides an example that can be modified to support InfluxDB's native format, or used unmodified with the InfluxDB Graphite input plugin. However, there are scaleability advantages to placing the sFlow-RT analytics engine in front of the time series database. For example, in large scale cloud environments the metrics for each member of a dynamic pool isn't necessarily worth trending since virtual machines are frequently added and removed. Instead, sFlow-RT tracks all the Continue reading
RPKI: BGP Security Hammpered by a Legal Agreement
Resource Public Key Infrastructure (RPKI) is a relatively new standard for establishing BGP route origination. I wrote a brief introductory article here. Apologies for the self-promotion, but rather than rehash the basics here, I raise another issue that needs community attention: ARIN’s Relying Party Agreement (RPA: PDF link). Having said that, some basics are needed. […]