In a Digital World, Anti-Fraud and Security Teams Should be Partners
Sharing the right information at the right time is critical to extraordinary digital experiences and protecting customers and the business from fraud.Full Stack Journey 068: An Introduction To Pixie For Open-Source Kubernetes Observability
Today's Full Stack Journey podcast is all about Pixie, an "open source observability tool for Kubernetes applications." Pixie takes advantage of eBPF to capture telemetry data. Joining Scott to provide a beginner-level overview of Pixie is Fabian Ngala.
The post Full Stack Journey 068: An Introduction To Pixie For Open-Source Kubernetes Observability appeared first on Packet Pushers.
Full Stack Journey 068: An Introduction To Pixie For Open-Source Kubernetes Observability
Today's Full Stack Journey podcast is all about Pixie, an "open source observability tool for Kubernetes applications." Pixie takes advantage of eBPF to capture telemetry data. Joining Scott to provide a beginner-level overview of Pixie is Fabian Ngala.LiveAction Unifies Flow, Packets For Deep Network Visibility
LiveAction provides network and application monitoring that integrates flow records and packets. This integration gives network management teams a clear, clean view of network topology and applications traffic–even for the most complex, multi-vendor networks. LiveAction can also capture and analyze packets to help engineers troubleshoot problems and investigate incidents.
The post LiveAction Unifies Flow, Packets For Deep Network Visibility appeared first on Packet Pushers.
When the window is not fully open, your TCP stack is doing more than you think
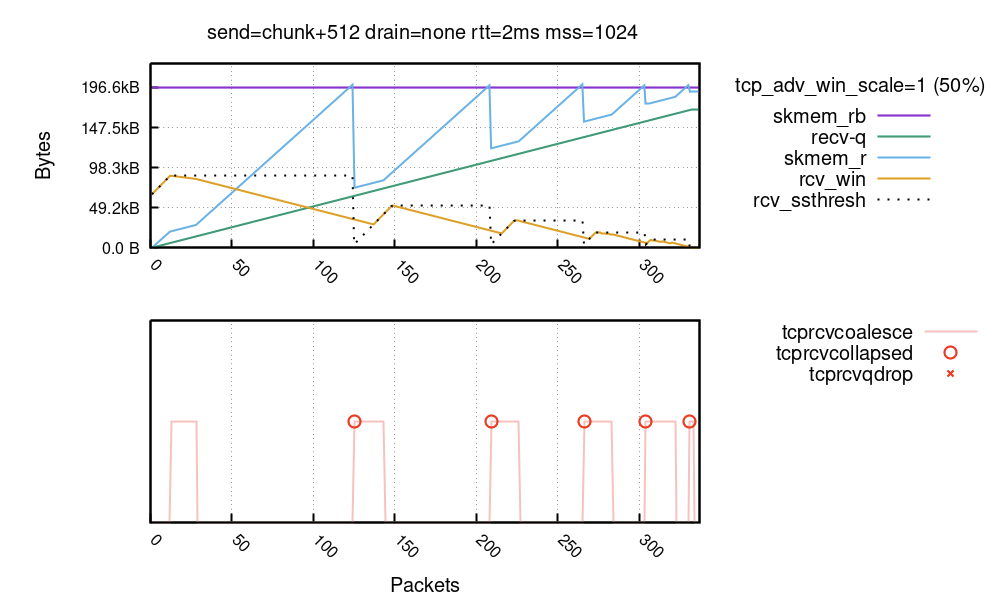
Over the years I've been lurking around the Linux kernel and have investigated the TCP code many times. But when recently we were working on Optimizing TCP for high WAN throughput while preserving low latency, I realized I have gaps in my knowledge about how Linux manages TCP receive buffers and windows. As I dug deeper I found the subject complex and certainly non-obvious.
In this blog post I'll share my journey deep into the Linux networking stack, trying to understand the memory and window management of the receiving side of a TCP connection. Specifically, looking for answers to seemingly trivial questions:
- How much data can be stored in the TCP receive buffer? (it's not what you think)
- How fast can it be filled? (it's not what you think either!)
Our exploration focuses on the receiving side of the TCP connection. We'll try to understand how to tune it for the best speed, without wasting precious memory.
A case of a rapid upload
To best illustrate the receive side buffer management we need pretty charts! But to grasp all the numbers, we need a bit of theory.
We'll draw charts from a receive side of a TCP flow, Continue reading
The DISH-SpaceX 5G Spectrum Dispute; Enterprise Impact and Possible Outcomes
If the FCC rules interference is a concern, spectrum sharing systems could provide a solution for all parties by maximizing the use of the 12GHz band.Ansible For Network Automation Lesson 8: Ansible And Idempotency – Video
This lesson covers the concept of idempotency and why it’s essential to Ansible. You can find the full playlist with all 8 videos on the Packet Pushers’ YouTube channel. You can subscribe to the Packet Pushers’ YouTube channel for more videos as they are published. It’s a diverse a mix of content from Ethan and […]
The post Ansible For Network Automation Lesson 8: Ansible And Idempotency – Video appeared first on Packet Pushers.
Tech Bytes: Nokia Fabric Services System Streamlines Network Automation For Application Stacks (Sponsored)
Today on the Tech Bytes podcast we welcome back sponsor Nokia to talk about a compelling feature in Nokia’s Fabric Services System. This feature, called Connect, lets Fabric Services System integrate with platforms such as VMware, OpenStack, and Kubernetes to streamline the provisioning of network services in Top Of Rack switches when new workloads or services are instantiated.
The post Tech Bytes: Nokia Fabric Services System Streamlines Network Automation For Application Stacks (Sponsored) appeared first on Packet Pushers.
Tech Bytes: Nokia Fabric Services System Streamlines Network Automation For Application Stacks (Sponsored)
Today on the Tech Bytes podcast we welcome back sponsor Nokia to talk about a compelling feature in Nokia’s Fabric Services System. This feature, called Connect, lets Fabric Services System integrate with platforms such as VMware, OpenStack, and Kubernetes to streamline the provisioning of network services in Top Of Rack switches when new workloads or services are instantiated.Network Break 391: IT Spending To Rise; Rating Your Emotional Response To Vendor Products
Take a Network Break! This week we cover new DLP capabilities from Cato Networks, updates to the open-source Cilium project for your eBPF and service mesh needs, why Cisco is streamlining how partners can offer Webex as a managed service, and more IT news coverage.Introducing Network RPA No-Code Process Automation: Gluware LiveStream June 28, 2022 (5/7) – Video
Gluware is introducing a new feature on its network automation platform, Network RPA, or Robotic Process Automation. Network RPA enables no-code process automation, meaning network engineers can easily stitch together automation workflows using a visual interface. Network RPA integrates with Stackstorm out of the box, meaning engineers can create workflows with everything Stackstorm supports, which […]
The post Introducing Network RPA No-Code Process Automation: Gluware LiveStream June 28, 2022 (5/7) – Video appeared first on Packet Pushers.
Cloudflare deployment in Guam
Having fast Internet properties means being as few milliseconds as possible away from our customers and their users, no matter where they are on Earth. And because of the design of Cloudflare's network we don't just make Internet properties faster by being closer, we bring our Zero Trust services closer too. So whether you're connecting to a public API, a website, a SaaS application, or your company's internal applications, we're close by.
This is possible by adding new cities, partners, capacity, and cables. And we have seen over and over again how making the Internet faster in a region also can have a clear impact on traffic: if the experience is quicker, people usually do more online.
Cloudflare’s network keeps increasing, and its global footprint does so accordingly. In April 2022 we announced that the Cloudflare network now spans 275 cities and the number keeps growing.
In this blog post we highlight the deployment of our data center in Hagatna, Guam.
Why a blog about Guam?
Guam is about 2,400 km from both Tokyo in the north and Manila in the west, and about 6,100 km from Honolulu in the east. Honolulu itself is the most remote major city in Continue reading