Privacy And Networking Part 5: The Data Lifecycle
In the previous posts in this series, I concluded that privacy is everyone’s responsibility, that IP addresses (and a lot of other information network engineers handle) are protected information, and while processing packets probably doesn’t trigger any privacy warnings, network logging should and does. In this post, I want to start answering the question—okay, what […]
The post Privacy And Networking Part 5: The Data Lifecycle appeared first on Packet Pushers.
Twilight Zone: File Transfer Never Completes
Ages ago when we were building networks using super-expensive 64kbps WAN links, a customer sent us a weird bug report:
Everything works fine, but we cannot transfer one particular file between two locations – the file transfer stalls and eventually times out. At the same time, we’re seeing increased number of CRC errors on the WAN link.
My chat with the engineer handling the ticket went along these lines:
Twilight Zone: File Transfer Never Completes
Ages ago when we were building networks using super-expensive 64kbps WAN links, a customer sent us a weird bug report:
Everything works fine, but we cannot transfer one particular file between two locations – the file transfer stalls and eventually times out. At the same time, we’re seeing increased number of CRC errors on the WAN link.
My chat with the engineer handling the ticket went along these lines:
An Overview Of Cisco’s SecureX Device Insights
Device Insights, a feature of Cisco's SecureX XDR service, aggregates, normalizes, and visualizes esssential details about all the devices on your network. SecureX can also automate workflows to respond to device-level security problems.
The post An Overview Of Cisco’s SecureX Device Insights appeared first on Packet Pushers.
Getting started with container security
A couple of days ago, I was checking my Twitter feed and saw a tweet from someone saying how frustrated he was that DockerHub (a renowned container registry) was down. Someone else replied to the tweet, recommending the tweet’s author to check out Google’s repository, where they have DockerHub mirrors in Google Cloud.
My first reaction was “Nice! How clever of this person (or Google) to have thought of this idea.” My next thought was, wait. This could lead to potential security risks for some developers who are not familiar with how these registries are updated and what images go into these mirrored sites. Imagine when application developers are busy scrambling to check-in their latest update to the CI/CD pipeline of the software they are building, and in that time crunch, their go-to container registry is down. Do developers really have the time to check if there are vulnerable images in every registry they use? Will there be an easy, streamlined way to automatically scan the images no matter which registry developers use to pull their images? The short answer is yes, and we will look into that in this blog.
Scan all your container assets with Calico Cloud
In a Digital World, Anti-Fraud and Security Teams Should be Partners
Sharing the right information at the right time is critical to extraordinary digital experiences and protecting customers and the business from fraud.Full Stack Journey 068: An Introduction To Pixie For Open-Source Kubernetes Observability
Today's Full Stack Journey podcast is all about Pixie, an "open source observability tool for Kubernetes applications." Pixie takes advantage of eBPF to capture telemetry data. Joining Scott to provide a beginner-level overview of Pixie is Fabian Ngala.
The post Full Stack Journey 068: An Introduction To Pixie For Open-Source Kubernetes Observability appeared first on Packet Pushers.
Full Stack Journey 068: An Introduction To Pixie For Open-Source Kubernetes Observability
Today's Full Stack Journey podcast is all about Pixie, an "open source observability tool for Kubernetes applications." Pixie takes advantage of eBPF to capture telemetry data. Joining Scott to provide a beginner-level overview of Pixie is Fabian Ngala.LiveAction Unifies Flow, Packets For Deep Network Visibility
LiveAction provides network and application monitoring that integrates flow records and packets. This integration gives network management teams a clear, clean view of network topology and applications traffic–even for the most complex, multi-vendor networks. LiveAction can also capture and analyze packets to help engineers troubleshoot problems and investigate incidents.
The post LiveAction Unifies Flow, Packets For Deep Network Visibility appeared first on Packet Pushers.
When the window is not fully open, your TCP stack is doing more than you think
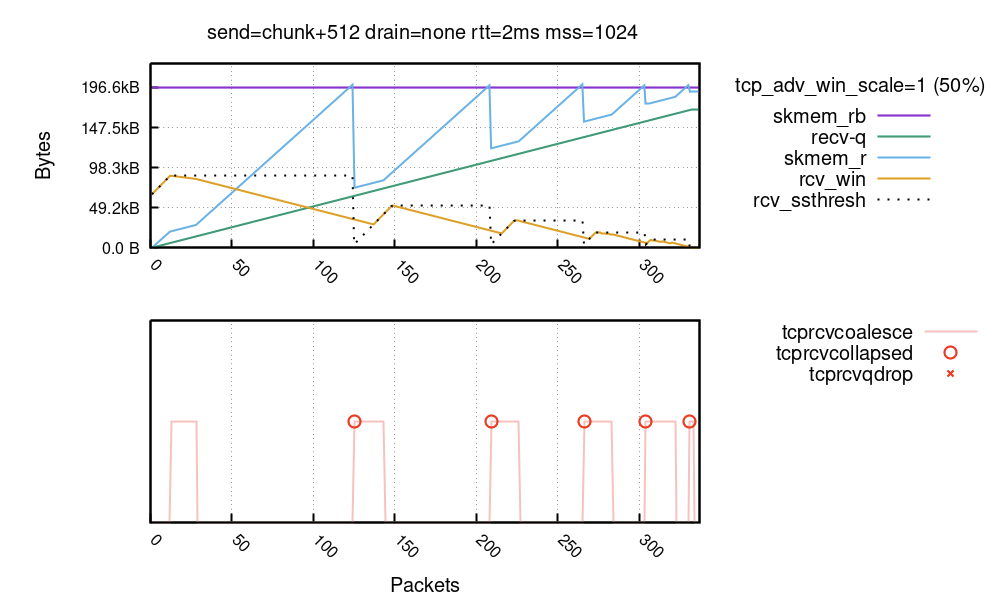
Over the years I've been lurking around the Linux kernel and have investigated the TCP code many times. But when recently we were working on Optimizing TCP for high WAN throughput while preserving low latency, I realized I have gaps in my knowledge about how Linux manages TCP receive buffers and windows. As I dug deeper I found the subject complex and certainly non-obvious.
In this blog post I'll share my journey deep into the Linux networking stack, trying to understand the memory and window management of the receiving side of a TCP connection. Specifically, looking for answers to seemingly trivial questions:
- How much data can be stored in the TCP receive buffer? (it's not what you think)
- How fast can it be filled? (it's not what you think either!)
Our exploration focuses on the receiving side of the TCP connection. We'll try to understand how to tune it for the best speed, without wasting precious memory.
A case of a rapid upload
To best illustrate the receive side buffer management we need pretty charts! But to grasp all the numbers, we need a bit of theory.
We'll draw charts from a receive side of a TCP flow, Continue reading
The DISH-SpaceX 5G Spectrum Dispute; Enterprise Impact and Possible Outcomes
If the FCC rules interference is a concern, spectrum sharing systems could provide a solution for all parties by maximizing the use of the 12GHz band.Ansible For Network Automation Lesson 8: Ansible And Idempotency – Video
This lesson covers the concept of idempotency and why it’s essential to Ansible. You can find the full playlist with all 8 videos on the Packet Pushers’ YouTube channel. You can subscribe to the Packet Pushers’ YouTube channel for more videos as they are published. It’s a diverse a mix of content from Ethan and […]
The post Ansible For Network Automation Lesson 8: Ansible And Idempotency – Video appeared first on Packet Pushers.
Tech Bytes: Nokia Fabric Services System Streamlines Network Automation For Application Stacks (Sponsored)
Today on the Tech Bytes podcast we welcome back sponsor Nokia to talk about a compelling feature in Nokia’s Fabric Services System. This feature, called Connect, lets Fabric Services System integrate with platforms such as VMware, OpenStack, and Kubernetes to streamline the provisioning of network services in Top Of Rack switches when new workloads or services are instantiated.
The post Tech Bytes: Nokia Fabric Services System Streamlines Network Automation For Application Stacks (Sponsored) appeared first on Packet Pushers.