MLAG Deep Dive: Layer-3 Forwarding
The layer-2 forwarding and flooding in an MLAG cluster are intricate but still reasonably easy to understand. Layer-3 gets more interesting; its quirks depend heavily on layer-2 implementation. While most MLAG implementations exhibit similar bridging behavior, expect interesting differences in routing behavior.
We’ll have to expand by-now familiar network topology to cover layer-3 edge cases. We’ll still work with two switches in an MLAG cluster, but we’ll have an external router attached to both of them. The hosts connected to the switches belong to two subnets (red and blue).
MLAG Deep Dive: Layer-3 Forwarding
The layer-2 forwarding and flooding in an MLAG cluster are intricate but still reasonably easy to understand. Layer-3 gets more interesting; its quirks depend heavily on layer-2 implementation. While most MLAG implementations exhibit similar bridging behavior, expect interesting differences in routing behavior.
We’ll have to expand by-now familiar network topology to cover layer-3 edge cases. We’ll still work with two switches in an MLAG cluster, but we’ll have an external router attached to both of them. The hosts connected to the switches belong to two subnets (red and blue).
Embrace Multi-Cloud Complexity to gain Competitive Advantage
If you embrace the inherent complexity of multi-cloud and address it by modernizing operations, you can effectively turn a challenge into a competitive advantage.Contributing Cool Community Content to Calico
It’s right there on our community page—the statement that “Project Calico is first and foremost a community.”
With that in mind, we wanted to make it easier for new contributors to get involved. It’s a win-win scenario—developers experience less frustration, they can get their work done, and have their contributions considered. Plus, the project can easily benefit from the contributions.
Recently, we have been doing a lot of work to simplify the contribution process, and to encourage, recognize, thank, and reward contributors. For example, earlier this year we announced our Calico Big Cats ambassador program and began using a single monorepo architecture. Read on and we’ll dig into that more.
In my role as Lead Developer Advocate for Project Calico, up until now, when I wanted to make a bug fix or improve something, I needed to feed that back to the development team for them to implement. In this blog post, though, I’m going to test out the new contribution process myself, document it for others, make improvements, and see what I can learn.
The Project Calico home page is a great place to find a contribution to make, so I headed there. Following the “Find a good Continue reading
BGP Intra-AS and Route Reflection

Since BGP is designed to be an overlay protocol, it doesn’t really have good mechanisms for carrying routes within an autonomous system. In this video, I’m discussing some of the techniques developed to carry routes within an AS, including route reflectors.
HS 026 So You Want to Develop A Technology Strategy ?
What are the right questions for developing and maintaining a technology strategy for your company ?
The post HS 026 So You Want to Develop A Technology Strategy ? appeared first on Packet Pushers.
HS 026 So You Want to Develop A Technology Strategy ?
What are the right questions for developing and maintaining a technology strategy for your company ?CLI Shortcut for Visual Studio Code on MacOS
I really do like Microsoft’s Visual Studio Code for editing code, so much so that I can forgive it for being an electron app. However when I code in go, the way the go’s syntax validation works means that each app folder needs to be opened in its own Visual Studio Code window – and as somebody supremely lazy I find this to be an irritating thing to have to do.
Opening a Folder in a New Window
It’s not actually that big of a deal, but having to execute File->New Window, then File->Open Folder…, then browsing to the folder I want to open often feels clunky and superfluous when half the time I’ve already browsed to that folder in the shell. So here’s the dumb shortcut which makes my life easy on MacOS:
/usr/local/bin/vsc:
#!/bin/zsh
#
"/Applications/Visual Studio Code.app/Contents/Resources/app/bin/code" --new-window "`pwd`"
So now if I’m in a folder I can just enter the command vsc and a new Visual Studio Code window opens focused on my current directory.
Stupidly simple, yes, yet I use it multiple times a day and I’m remarkably happy about it. It takes all sorts, I guess.
If you liked this post, Continue reading
Full Stack Journey 067: What The Heck Is GitOps?
What, exactly, it GitOps? It seems like a new "Ops" word pops up every week! On today's Full Stack Journey podcast, guest Christian Hernandez of Codefresh explains GitOps, what it is, and how you can get started using it.
The post Full Stack Journey 067: What The Heck Is GitOps? appeared first on Packet Pushers.
Full Stack Journey 067: What The Heck Is GitOps?
What, exactly, it GitOps? It seems like a new "Ops" word pops up every week! On today's Full Stack Journey podcast, guest Christian Hernandez of Codefresh explains GitOps, what it is, and how you can get started using it.Infinitely extensible Access policies


Zero Trust application security means that every request to an application is denied unless it passes a specific set of defined security policies. Most Zero Trust solutions allow the use of a user’s identity, device, and location as variables to define these security policies.
We heard from customers that they wanted more control and more customizability in defining their Zero Trust policies.
Starting today, we’re excited that Access policies can consider anything before allowing a user access to an application. And by anything, we really do mean absolutely anything. You can now build infinitely customizable policies through the External Evaluation rule option, which allows you to call any API during the evaluation of an Access policy.
Why we built external evaluation rules
Over the past few years we added the ability to check location and device posture information in Access. However, there are always additional signals that can be considered depending on the application and specific requirements of an organization. We set out to give customers the ability to check whatever signal they require without any direct support in Access policies.
The Cloudflare security team, as an example, needed the ability to verify a user’s mTLS certificate against a registry Continue reading
How Cloudflare One solves your observability problems


Today, we’re excited to announce Cloudflare One Observability. Cloudflare One Observability will help customers work across Cloudflare One applications to troubleshoot network connectivity, security policies, and performance issues to ensure a consistent experience for employees everywhere. Cloudflare One, our comprehensive SASE platform, already includes visibility for individual products; Cloudflare One Observability is the next step in bringing data together across the Cloudflare One platform.
Network taps and legacy enterprise networks
Traditional enterprise networks operated like a castle protected by a moat. Employees working from a physical office location authenticated themselves at the beginning of their session, they were protected by an extensive office firewall, and the majority of the applications they accessed were on-premise.
Many enterprise networks had a strictly defined number of “entrances” for employees at office locations. Network taps (devices used to measure and report events on a local network) monitored each entrance point, and these devices gave network administrators and engineers complete visibility into their operations.
Learn more about the old castle-and-moat network security model.
Incomplete observability in today’s enterprise network
Today’s enterprise networks have expanded beyond the traditional on-premise model and have become extremely fragmented. Now, employees can work from anywhere. People access enterprise networks Continue reading
Next generation intrusion detection: an update on Cloudflare’s IDS capabilities

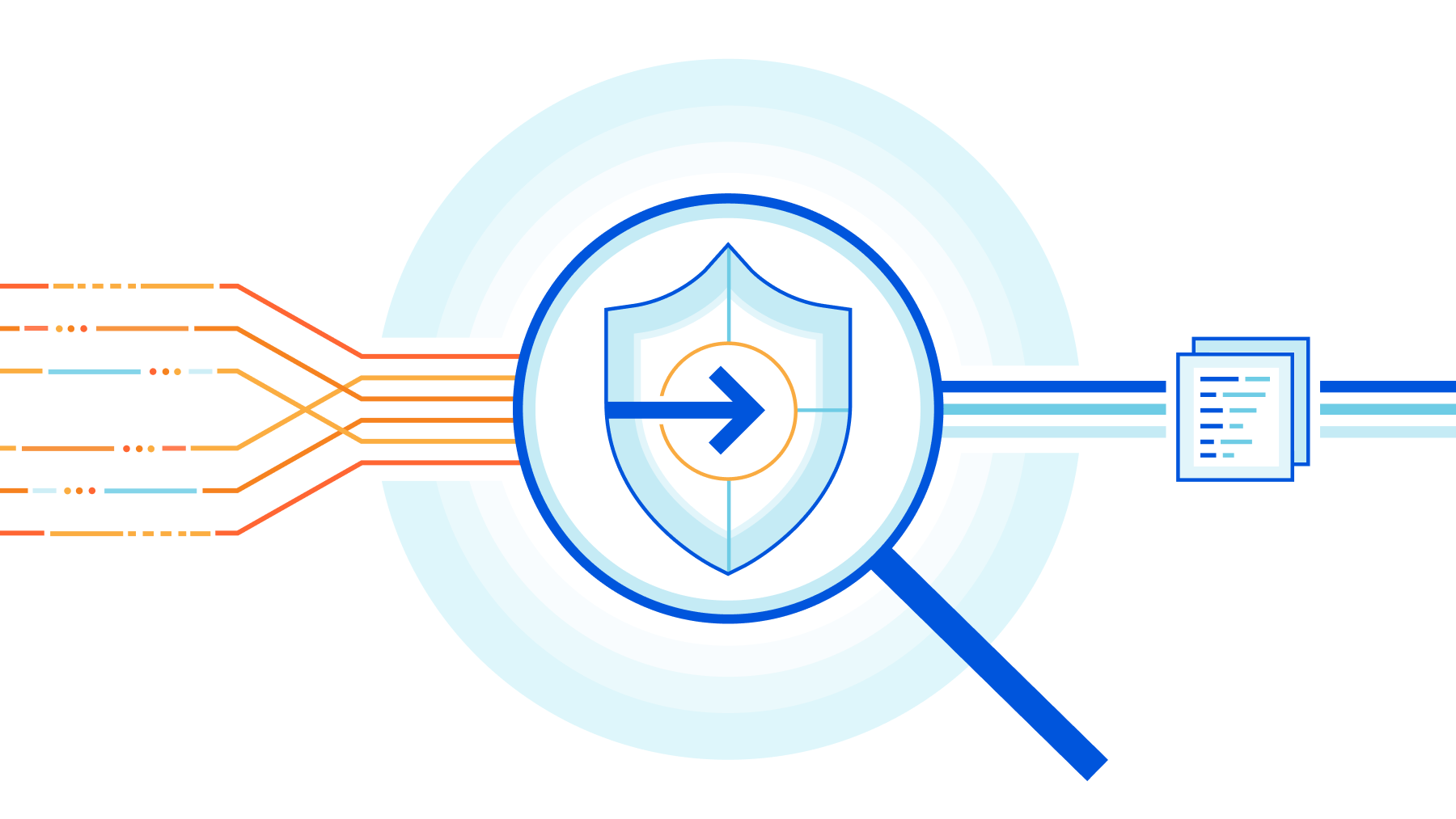
In an ideal world, intrusion detection would apply across your entire network - data centers, cloud properties, and branch locations. It wouldn’t impact the performance of your traffic. And there’d be no capacity constraints. Today, we’re excited to bring this one step closer to reality by announcing the private beta of Cloudflare’s intrusion detection capabilities: live monitoring for threats across all of your network traffic, delivered as-a-service — with none of the constraints of legacy hardware approaches.
Cloudflare’s Network Services, part of Cloudflare One, help you connect and secure your entire corporate network — data center, cloud, or hybrid — from DDoS attacks and other malicious traffic. You can apply Firewall rules to keep unwanted traffic out or enforce a positive security model, and integrate custom or managed IP lists into your firewall policies to block traffic associated with known malware, bots, or anonymizers. Our new Intrusion Detection System (IDS) capabilities expand on these critical security controls by actively monitoring for a wide range of known threat signatures in your traffic.
What is an IDS?
Intrusion Detection Systems are traditionally deployed as standalone appliances but often incorporated as features in more modern or higher end firewalls. They expand the security Continue reading