Video: IPv6 RA Guard and Extension Headers
Last week’s IPv6 security video introduced the rogue IPv6 RA challenges and the usual countermeasure – RA guard. Unfortunately, IPv6 tends to be a wonderfully extensible protocol, creating all sorts of opportunities for nefarious actors and security researchers.
For years, the networking vendors were furiously trying to plug the holes created by the academically minded IPv6 designers in love with fragmented extension headers. In the meantime, security researches had absolutely no problem finding yet another weird combination of IPv6 headers that would bypass any IPv6 RA guard implementation until IETF gave up and admitted one cannot have “infinitely extensible” and “secure” in the same sentence.
For more details watch the video by Christopher Werny describing how one could use IPv6 extension headers to circumvent IPv6 RA guard
3 Key Strategies for Securing the Software Supply Chain
Software supply chain attacks can use a single breach to target software components that can then affect multiple companies' applications.Using OpenSSL With Ed Harmoush 5/6 Inspecting Certificates: Invalid Certificates – Video
ED, HIS TLS COURSE, AND THE FREE OPENSSL CHEATSHEET Twitter @ed_pracnet https://practicalnetworking.net Practical TLS course: https://pracnet.net/tls OpenSSL Cheatsheet: https://pracnet.net/openssl FILES FOR THE CERT/KEY MATCHING EXERCISE: ZIP VERSION: packetpushers-pracnet-openssl.zip https://ln5.sync.com/dl/1f1f63d90/kqztwkp9-hkcz3yvq-tuzx79ke-aewxgaip TAR.GZ VERSION: packetpushers-pracnet-openssl.tar.gz https://ln5.sync.com/dl/0791b8d50/q973jpyb-qrmz3cpd-xeiar9zn-qu99gi5w FOR MORE INFO Hashing, Hashing Algorithms, and Collisions – Cryptography Symmetric Encryption vs Asymmetric Encryption Public & Private Keys – Signatures & […]
The post Using OpenSSL With Ed Harmoush 5/6 Inspecting Certificates: Invalid Certificates – Video appeared first on Packet Pushers.
MLAG Deep Dive: Layer-2 Flooding
In the previous blog post of the MLAG Technology Deep Dive series, we explored the intricacies of layer-2 unicast forwarding. Now let’s focus on layer-2 BUM1 flooding functionality of an MLAG system.
Our network topology will have two switches and five hosts, some connected to a single switch. That’s not a good idea in an MLAG environment, but even if you have a picture-perfect design with everything redundantly connected, you will have to deal with it after a single link failure.
MLAG Deep Dive: Layer-2 Flooding
In the previous blog post of the MLAG Technology Deep Dive series, we explored the intricacies of layer-2 unicast forwarding. Now let’s focus on layer-2 BUM1 flooding functionality of an MLAG system.
Our network topology will have two switches and five hosts, some connected to a single switch. That’s not a good idea in an MLAG environment, but even if you have a picture-perfect design with everything redundantly connected, you will have to deal with it after a single link failure.
Cloudflare Zaraz launches new privacy features in response to French CNIL standards


Last week, the French national data protection authority (the Commission Nationale de l'informatique et des Libertés or “CNIL”), published guidelines for what it considers to be a GDPR-compliant way of loading Google Analytics and similar marketing technology tools. The CNIL published these guidelines following notices that the CNIL and other data protection authorities issued to several organizations using Google Analytics stating that such use resulted in impermissible data transfers to the United States. Today, we are excited to announce a set of features and a practical step-by-step guide for using Zaraz that we believe will help organizations continue to use Google Analytics and similar tools in a way that will help protect end user privacy and avoid sending EU personal data to the United States. And the best part? It takes less than a minute.
Enter Cloudflare Zaraz.
The new Zaraz privacy features
What we are releasing today is a new set of privacy features to help our customers enhance end user privacy. Starting today, on the Zaraz dashboard, you can apply the following configurations:
- Remove URL query parameters: when toggled-on, Zaraz will remove all query parameters from a URL that is reported to a third-party server. It will turn
Continue reading
Day Two Cloud 151: How To Tell If Infrastructure As Code Is Working For You
Today's Day Two Cloud podcast gets into Infrastructure as Code (IaC) and how to evaluate it so that IaC practices fit your organization, your processes, the infrastructure you're trying to support, and so on. Our guest lays out some guideposts to help you understand if IaC is working for you.Cisco Live 2022: A Kinder, Gentler, Cloudier Monster?
Cisco Live 2022 in Las Vegas kicked off with executive keynotes, including an address from CEO Chuck Robbins. My takeaways from the keynotes from Tuesday, June 14th are: Cisco knows it has to work harder to keep customers Cisco has big cloud ambitions Meraki is one key to Cisco’s cloud & simplicity goals Cisco Has […]
The post Cisco Live 2022: A Kinder, Gentler, Cloudier Monster? appeared first on Packet Pushers.
Internal Network Security Mistakes to Avoid
Network security begins at home. Here's how to effectively secure threats from within your organization.Hedge 134: Ten Things

One of the many reasons engineers should work for a vendor, consulting company, or someone other than a single network operator at some point in their career is to develop a larger view of network operations. What are common ways of doing things? What are uncommon ways? In what ways is every network broken? Over time, if you see enough networks, you start seeing common themes and ideas. Just like history, networks might not always be the same, but the problems we all encounter often rhyme. Ken Calenza joins Tom Ammon, Eyvonne Sharp, and Russ White to discuss these common traits—ten things I know about your network.
EVPN-VXLAN Explainer 5 – Layer 3 with Asymmetrical IRB
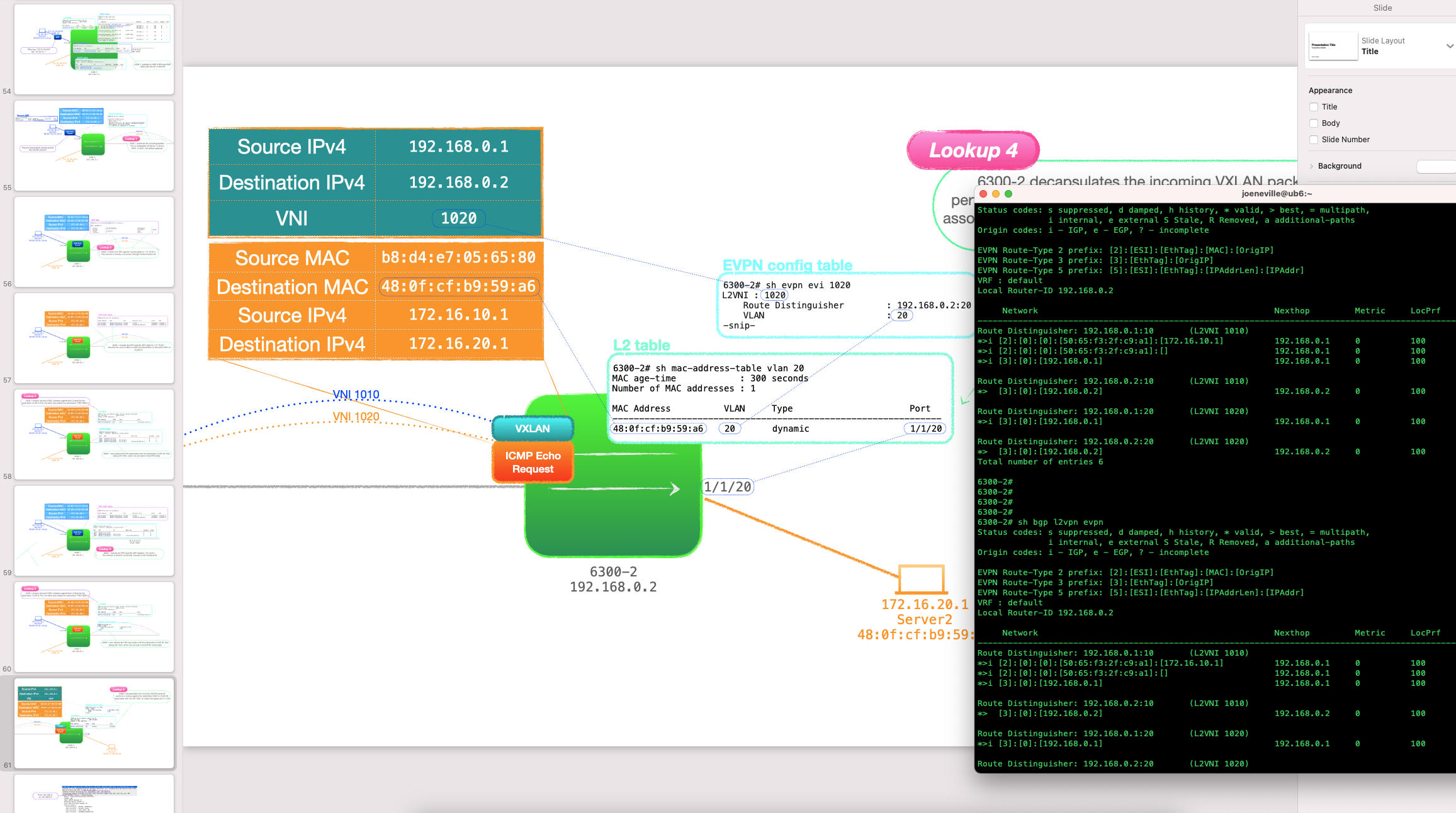
Thus far, this series of posts have all been about Layer 2 over Layer 3 models; the customer ethernet frames encapsulated in UDP, traversing L3 networks. The routing has been confined underlay, the customer traffic has stayed within the same network.
No longer! In this post, things start getting a little more interesting, as we look at routing the customer traffic with an EVPN feature called Integrated Routing and Bridging, or IRB.
- First we look at the concept of routing in VXLAN networks.
- Then we have an in-depth look at asymmetrical IRB (I'll be dealing with symmetrical in the next post).
✅ L2 is intra-subnet, L3 is inter-subnet
📥 Intra-subnet
To define terms, when I say 'intra-subnet', that is L2 traffic transferred between nodes in the same subnet.
📤 Inter-subnet
'Inter-subnet' refers to a traffic flow that traverses subnet boundaries.
☎️ The Centralized IP L3 Gateways of Old
- With VXLAN networks in the past, inter-subnet communication was often performed by a centralized, IP only, gateway on behalf of the rest of the network.
- Traffic from customer-side networks would need to be sent to this central device for routing, which often created inefficient traffic flows, and possibly a bandwidth choke-point.
- Imagine Continue reading