Petabyte-Scale Deployments Push Existing Storage Systems to the Brink
Today’s storage solutions are falling short in meeting customer needs. Because of these limitations, organizations are not realizing the full potential and value of their storage.We rebuilt Cloudflare’s developer documentation – here’s what we learned


We recently updated developers.cloudflare.com, the Cloudflare Developers documentation website, to a new version of our custom documentation engine. This change consisted of a significant migration from Gatsby to Hugo and converged a collection of Workers Sites into a single Cloudflare Pages instance. Together, these updates brought developer experience, performance, and quality of life improvements for our engineers, technical writers, and product managers.
In this blog post, we’ll cover the history of Cloudflare’s developer docs, why we made this recent transition, and why we continue to dogfood Cloudflare’s products as we develop applications internally.
What are Cloudflare’s Developer Docs?
Cloudflare’s Developer Docs, which are open source on GitHub, comprise documentation for all of Cloudflare’s products. The documentation is written by technical writers, product managers, and engineers at Cloudflare. Like many open source projects, contributions to the docs happen via Pull Requests (PRs). At time of writing, we have 1,600 documentation pages and have accepted almost 4,000 PRs, both from Cloudflare employees and external contributors in our community.
The underlying documentation engine we’ve used to build these docs has changed multiple times over the years. Documentation sites are often built with static site generators and, at Cloudflare, we’ve Continue reading
EVPN-VXLAN Explainer 4 – Route Type Three and Auto-Discovery
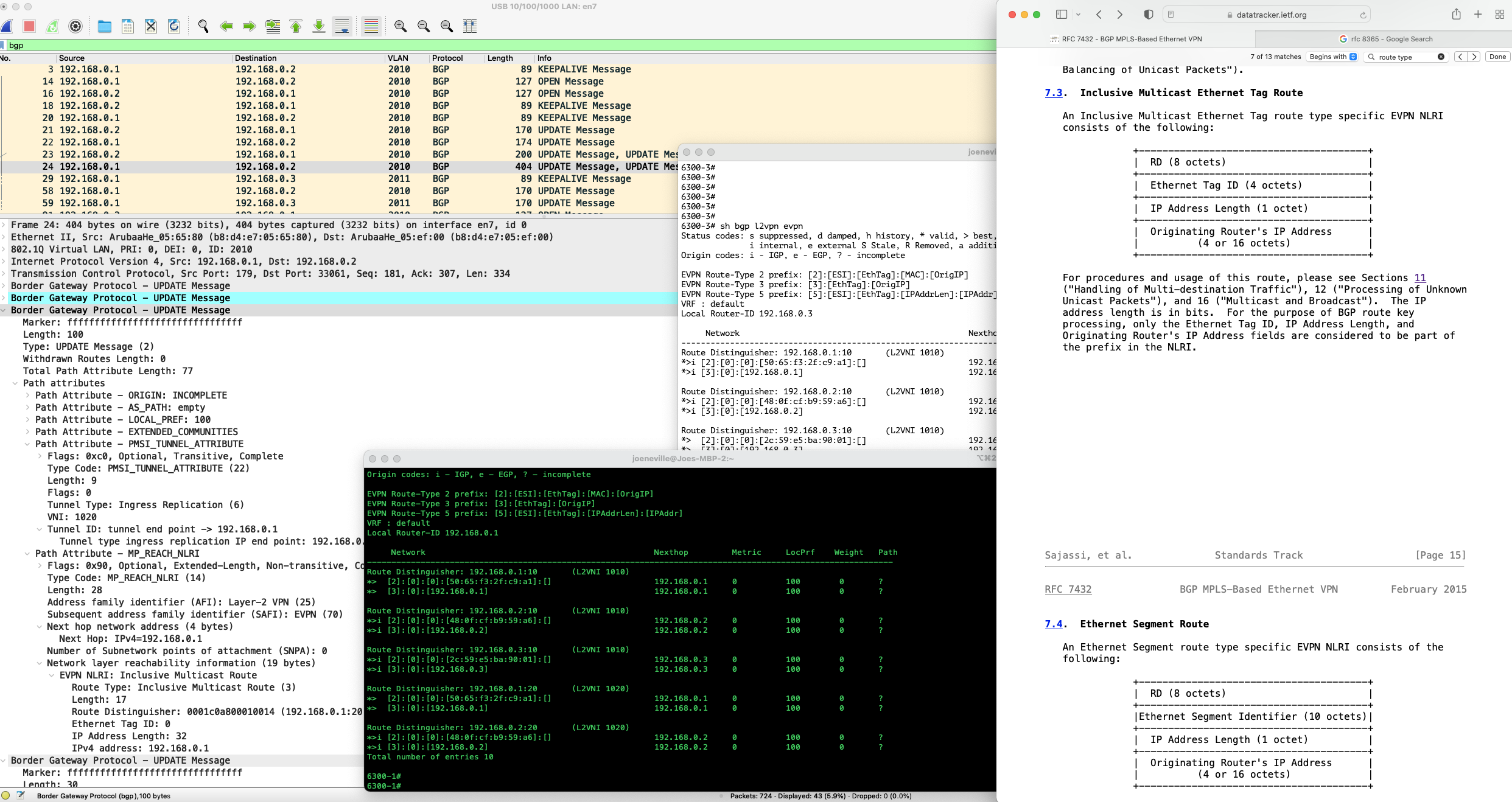
In this post we will have a look at another EVPN Route Type, that being RT-3, which goes by the rather opaque name of 'Inclusive Multicast Ethernet Tag'; and look at how it is used to ensure EVPN peers flood traffic to those neighbours that need it.
Firstly, we'll look at EVPN packet forwarding to provide some context around why this Route Type is important, then we will dive into its details, with all the usual show commands, packet captures and plethora of RFC name drops.
EVPN Packet Forwarding
Let's start off by running through EVPN Packet forwarding, for that we need an example network.
Example Network
- For this post, we'll use a slightly larger network, this time with three switches.
- As shown in Figure 1 below, this consists of three Aruba 6300s, all configured for OSPF and EVPN.
- To emulate customer workloads, I have a physical linux server attached to each 6300. I have configured the interconnecting port as a trunk to generate traffic in different VLANs.
- Each node is configured with customer-faced VLAN 10, which is bound to VNI 1010.
- However, only two of the three peers, 6300-1 and 6300-2, are configured with a second VLAN and VNI, Continue reading
Video: Ugly Challenges of Using AI/ML in Networking
Javier Antich concluded the AI/ML in Networking webinar with the ugly challenges of using AI/ML in networking. I won’t spoil the fun, you REALLY SHOULD watch the video (keeping in mind he was trying to stay polite and diplomatic).
Video: Ugly Challenges of Using AI/ML in Networking
Javier Antich concluded the AI/ML in Networking webinar with the ugly challenges of using AI/ML in networking. I won’t spoil the fun, you REALLY SHOULD watch the video (keeping in mind he was trying to stay polite and diplomatic).
Day Two Cloud 148: Understanding Cloud Security Roles And Responsibilities
If you're a security or network professional wondering if your skills aren't as applicable or useful when it comes to public cloud, don't worry: they are very, very useful. On today's Day Two Cloud podcast we talk with Brandon Carroll on how to properly map traditional infrastructure and network security to public cloud deployments.Pros and Cons of Radio Networking
Radio networking is a wireless communication method that uses radio waves to connect devices. It is commonly used in computer networks, cell phone networks, and other devices that need to communicate wirelessly.
Radio networking is often used in situations where it is not possible or convenient to use wired networking, such as in mobile or portable applications. Radio networking can be either peer-to-peer or infrastructure.
In peer-to-peer networking, each device acts as both a transmitter and receiver, and there is no central access point. Infrastructure networking uses one or more access points that act as repeaters, amplifiers, and signal boosters to extend the range of the network.
Advantages of radio networking
Radio networking has many advantages over other types of wireless communication. It is very reliable and can work in a variety of environments. Radio networking is also very secure and can be encrypted to protect data. Radio networking is also very fast and can support high-speed data transfers.
Low start-up costs
One of the biggest advantages of radio networking is that it has very low start-up costs. All you need is a radio transmitter and receiver, and you can start communicating.
This makes radio networking ideal for Continue reading
Broadcom Bolsters Enterprise Efforts with $61 Billion VMware Acquisition
Recently spun off VMware is to be acquired by Broadcom in the company's efforts to bolster its enterprise software presence.HS 024 – Is Shadow IT a Good Thing
Shadow IT does not always lead to bad outcom
The post HS 024 – Is Shadow IT a Good Thing appeared first on Packet Pushers.
HS 024 – Is Shadow IT a Good Thing
Shadow IT does not always lead to bad outcomCloudflare’s approach to handling BMC vulnerabilities


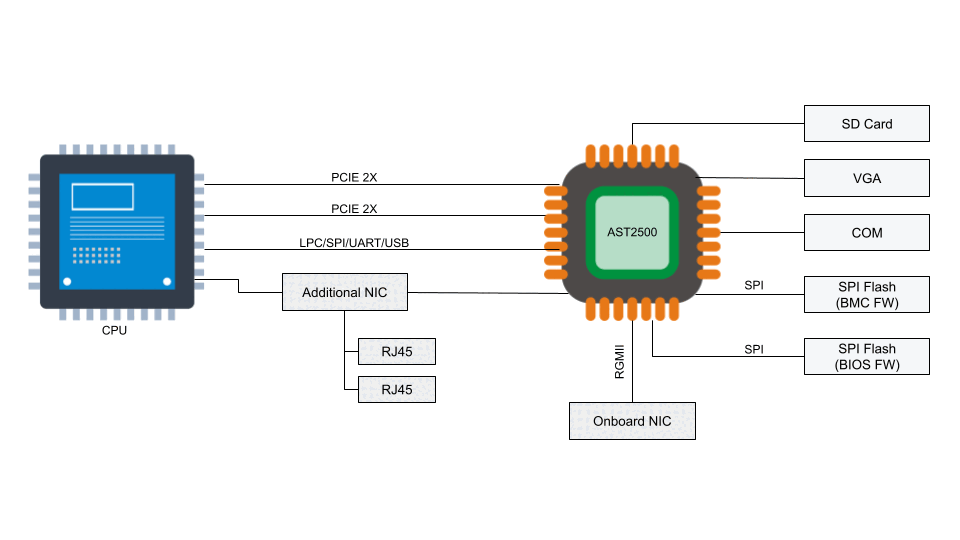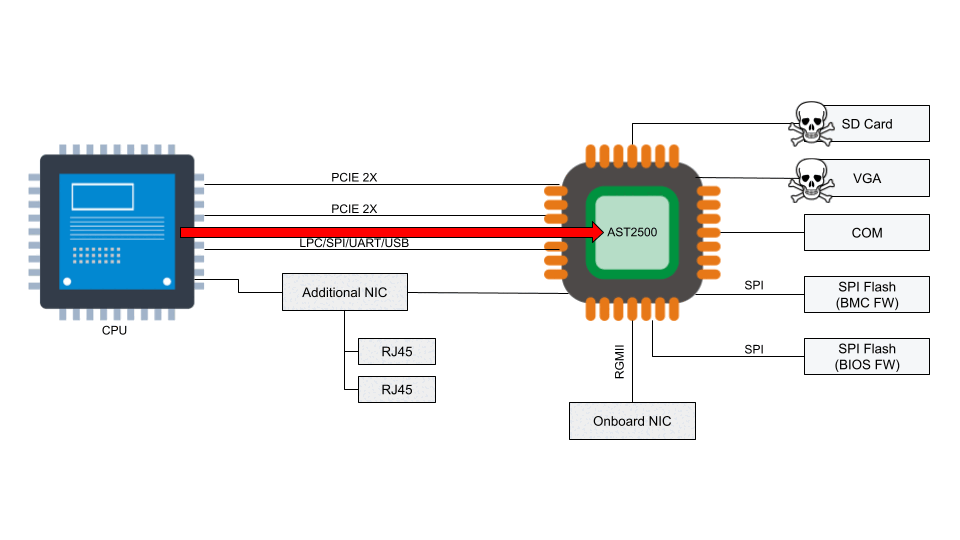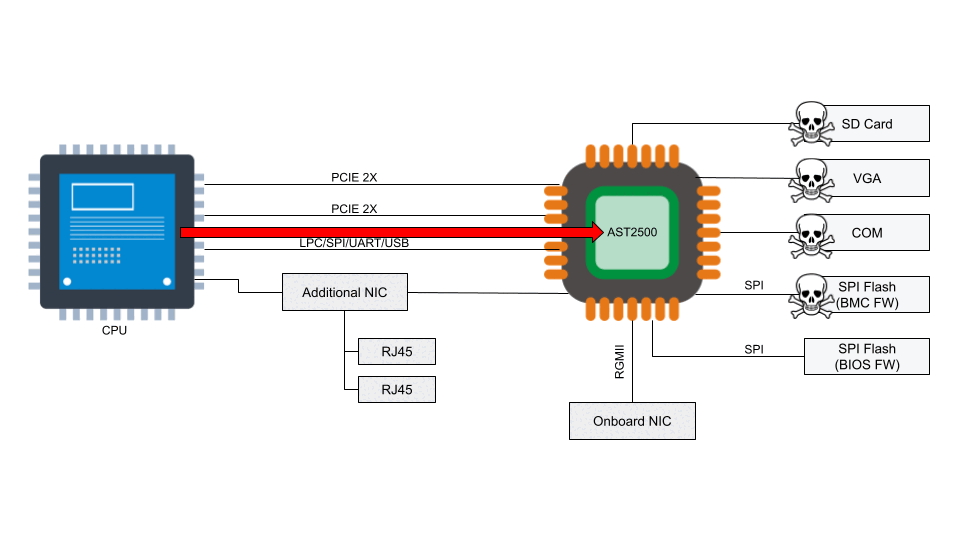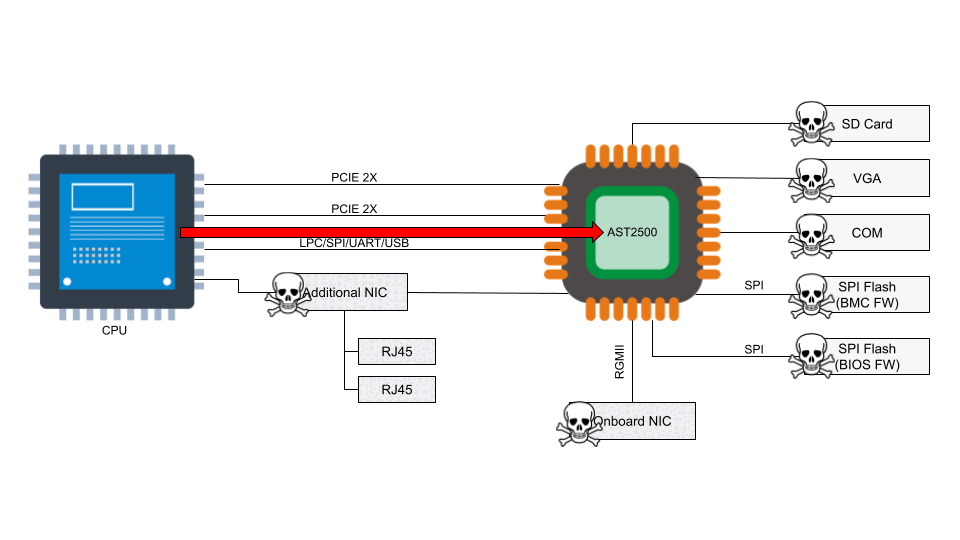
In recent years, management interfaces on servers like a Baseboard Management Controller (BMC) have been the target of cyber attacks including ransomware, implants, and disruptive operations. Common BMC vulnerabilities like Pantsdown and USBAnywhere, combined with infrequent firmware updates, have left servers vulnerable.
We were recently informed from a trusted vendor of new, critical vulnerabilities in popular BMC software that we use in our fleet. Below is a summary of what was discovered, how we mitigated the impact, and how we look to prevent these types of vulnerabilities from having an impact on Cloudflare and our customers.
Background
A baseboard management controller is a small, specialized processor used for remote monitoring and management of a host system. This processor has multiple connections to the host system, giving it the ability to monitor hardware, update BIOS firmware, power cycle the host, and many more things.
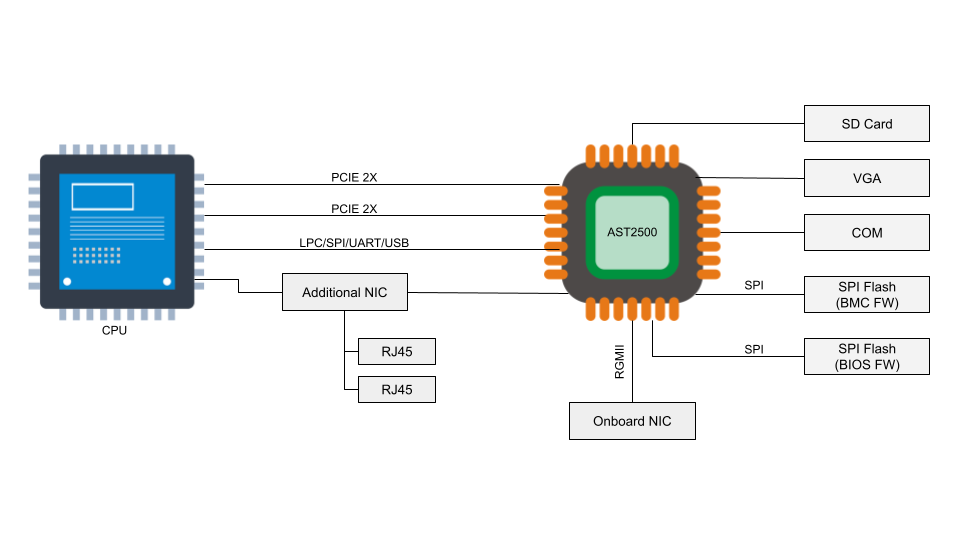
Access to the BMC can be local or, in some cases, remote. With remote vectors open, there is potential for malware to be installed on the BMC from the local host via PCI Express or the Low Pin Count (LPC) interface. With compromised software on the BMC, malware or spyware could maintain persistence on the server.
How we treat content as a product

At Cloudflare, we talk a lot about how to help build a better Internet. On the Product Content Experience (PCX) team, we treat content like a product that represents and fulfills this mission. Our vision is to create world-class content that anticipates user needs and helps build accessible Cloudflare products. We believe we can impact the Cloudflare product experience and make it as wonderful as possible by intentionally designing, packaging, and testing the content.
What is “content like a product”?
I like taking on projects. A singular goal is met, and I clearly know I’m successful because the meaning of “done” is normally very clear. For example, I volunteer some of my time editing academic papers about technology. My role as an editor is temporary and there is a defined beginning and end to the work. I send my feedback and my task is largely complete.
“Content like a product” is when you shift your mindset from completing projects to maintaining a product, taking into consideration the user and their feedback. Product content at Cloudflare is an iterative, living, breathing thing. Inspired by the success of teams that adopt an agile mindset, along with some strategic functions you might find Continue reading
Kubernetes Unpacked 001: Prerequisites For Kubernetes Success
Welcome to the inaugural episode of Kubernetes Unpacked, a new podcast in the Packet Pushers Community Channel. The goal of this podcast is to help IT professionals understand Kubernetes: how it works; how and why it's used; how to deploy, operate, and manage the platform on premises and in the cloud; Kubernetes networking and security concepts; and more.
The post Kubernetes Unpacked 001: Prerequisites For Kubernetes Success appeared first on Packet Pushers.