Detecting Byzantine Link Failures with SNMP
One of my readers has to deal with a crappy Network Termination Equipment (NTE)1 that does not drop local link carrier2 when the remote link fails. Here’s the original ASCII art describing the topology:
PE---------------NTE--FW---NMS
<--------IP-------->
He’d like to use interface SNMP counters on the firewall to detect the PE-NTE link failure. He’s using static default route toward PE on FW, and tried to detect the link failure with ifOutDiscards counter.
Detecting Byzantine Link Failures with SNMP
One of my readers has to deal with a crappy Network Termination Equipment (NTE)1 that does not drop local link carrier2 when the remote link fails. Here’s the original ASCII art describing the topology:
PE---------------NTE--FW---NMS
<--------IP-------->
He’d like to use interface SNMP counters on the firewall to detect the PE-NTE link failure. He’s using static default route toward PE on FW, and tried to detect the link failure with ifOutDiscards counter.
Tools 10. Developing Our Own Cross-platform (AMD64/ARM32) Traceroute Prometheus Exporter for Network Monitoring using Python
Hello my friend,
This is the third and the last (at least for the time being ) blogpost about monitoring of the infrastructure with Prometheus, one of the most powerful and popular open source time series database and metrics collection framework. In today’s talk we’ll cover the build of our own Prometheus exporter, which performs trace route checks.
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
Why to Automate Monitoring?
Many tools nowadays give you possibility not only to collect metrics, but also to act perform a simple )(or complex) analysis and act based on the result of such an analysis. So can Prometheus. With a help of the Alertmanager, it is possible to send a REST API request upon certain condition, which would trigger an automation activity or a workflow to act upon the business logic needed for the condition, such as remediation and/or configuration. This is why you need to know how the network automation works at a good level.
And we Continue reading
Network Break 379: Nokia Goes SONiC For Microsoft Data Centers: Comcast Tests Hollowcore Fiber
This week's Network Break podcast discusses Nokia deal to sell switch hardware to Microsoft running the SONiC network OS. We also cover Dell's 4.0 release of its Enterprise SONiC distribution, a test of hollowcore fiber optics by Comcast, the British government making rules about watching TV in self-driving cars, and more tech news.Tech Bytes: Why The Network Is Essential For Securing Hybrid IT (Sponsored)
Today’s Tech Bytes podcast gets into networking and security. More specifically, despite what you might hear about cloud taking over, the network still matters, and is essential to an organization’s security strategy, especially as cloud adoption and remote work drive the need for hybrid IT. We’re going to address this topic with sponsor Fortinet.
The post Tech Bytes: Why The Network Is Essential For Securing Hybrid IT (Sponsored) appeared first on Packet Pushers.
Tech Bytes: Why The Network Is Essential For Securing Hybrid IT (Sponsored)
Today’s Tech Bytes podcast gets into networking and security. More specifically, despite what you might hear about cloud taking over, the network still matters, and is essential to an organization’s security strategy, especially as cloud adoption and remote work drive the need for hybrid IT. We’re going to address this topic with sponsor Fortinet.How Does Packet Loss and Delay Affect Performance?
Tony Fortunato of The Technology Firm walks you through the process of evaluating the impact of packet loss and delay on a network's or app's performance.Securing Private Cloud Workloads Using Zero Trust Methodologies
The utmost in workload security that fully adheres to zero trust principles can be obtained when using distributed network security agents that are installed at the hypervisor level.BGP Policies (Part 5)
At the most basic level, there are only three BGP policies: pushing traffic through a specific exit point; pulling traffic through a specific entry point; preventing a remote AS (more than one AS hop away) from transiting your AS to reach a specific destination. In this series I’m going to discuss different reasons for these kinds of policies, and different ways to implement them in interdomain BGP.
In this post I’m going to cover AS Path Prepending from the perspective of AS65001 in the following network—

Since the length of the AS Path plays a role in choosing which path to use when forwarding traffic towards a given reachable destination, many (if not most) operators prepend the AS Path when advertising routes to a peer. Thus an AS Path of [65001], when advertised towards AS65003, can become [65001,65001] by adding one prepend, [65001,65001,65001] by adding two prepends, etc. Most BGP implementations allow an operator to prepend as many times as they would like, so it is possible to see twenty, thirty, or even higher numbers of prepends.
Note: The usefulness of prepending is generally restricted to around two or three, as the average length of an AS Path in the Continue reading
Understanding Micro-segmentation Policy as Code: How Gitops Will Change Network Security
Micro-segmentation can help you reduce risk by isolating compromised applications and blocking lateral movement attacks.Top Considerations for Enterprise Use of Fixed Wireless Access
Carriers’ broadband deployment plans focus on fiber. But a growing number are also using FWA as well. What do IT managers need to know about the alternative to fiber as carrier decisions factor in your network expansion and enhancement plans?Practical Python For Networking: 5.3 Code Refactoring – Second Example – Video
This lesson walks through the second example of code refactoring. Course files are in a GitHub repository: https://github.com/ericchou1/pp_practical_lessons_1_route_alerts Eric Chou is a network engineer with 20 years of experience, including managing networks at Amazon AWS and Microsoft Azure. He’s the founder of Network Automation Nerds and has written the books Mastering Python Networking and Distributed […]
The post Practical Python For Networking: 5.3 Code Refactoring – Second Example – Video appeared first on Packet Pushers.
Email Routing Insights


Have you ever wanted to try a new email service but worried it might lead to you missing any emails? If you have, you’re definitely not alone. Some of us email ourselves to make sure it reaches the correct destination, others don’t rely on a new address for anything serious until they’ve seen it work for a few days. In any case, emails often contain important information, and we need to trust that our emails won’t get lost for any reason.
To help reduce these worries about whether emails are being received and forwarded - and for troubleshooting if needed - we are rolling out a new Overview page to Email Routing. On the Overview tab people now have full visibility into our service and can see exactly how we are routing emails on their behalf.
Routing Status and Metrics
The first thing you will see in the new tab is an at a glance view of the service. This includes the routing status (to know if the service is configured and running), whether the necessary DNS records are configured correctly, and the number of custom and destination addresses on the zone.
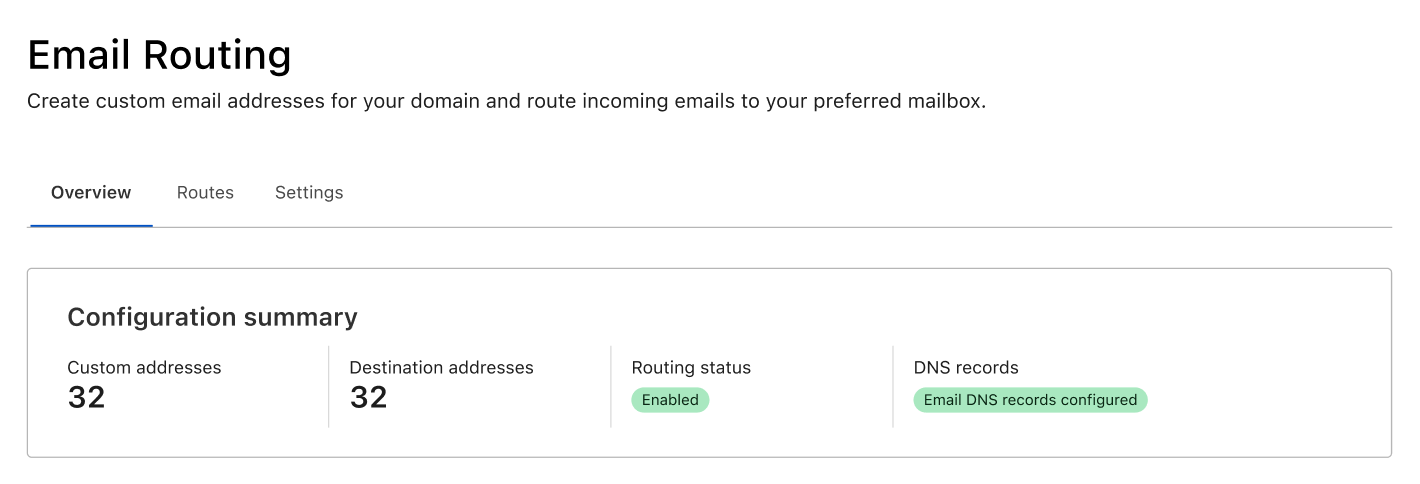
Below the configuration summary, you will see more Continue reading