N4N031: When Is It Time For a Routing Protocol?
If you need to route in your network, you can program static routes into all your routing-capable devices. And this can work. But at some point, you’re probably going to want to switch to a dynamic routing protocol. On today’s N Is For Networking, Ethan and Holly discuss the differences between static and dynamic routes,... Read more »Defending the Internet: how Cloudflare blocked a monumental 7.3 Tbps DDoS attack
In mid-May 2025, Cloudflare blocked the largest DDoS attack ever recorded: a staggering 7.3 terabits per second (Tbps). This comes shortly after the publication of our DDoS threat report for 2025 Q1 on April 27, 2025, where we highlighted attacks reaching 6.5 Tbps and 4.8 billion packets per second (pps). The 7.3 Tbps attack is 12% larger than our previous record and 1 Tbps greater than a recent attack reported by cyber security reporter Brian Krebs at KrebsOnSecurity.

New world record: 7.3 Tbps DDoS attack autonomously blocked by Cloudflare
The attack targeted a Cloudflare customer, a hosting provider, that uses Magic Transit to defend their IP network. Hosting providers and critical Internet infrastructure have increasingly become targets of DDoS attacks, as we reported in our latest DDoS threat report. Pictured below is an attack campaign from January and February 2025 that blasted over 13.5 million DDoS attacks against Cloudflare’s infrastructure and hosting providers protected by Cloudflare.

DDoS attack campaign target Cloudflare infrastructure and hosting providers protected by Cloudflare
Let's start with some stats, and then we’ll dive into how our systems detected and mitigated this attack.
The 7.3 Tbps attack delivered 37.4 Continue reading
Everything you need to know about NIST’s new guidance in “SP 1800-35: Implementing a Zero Trust Architecture”
For decades, the United States National Institute of Standards and Technology (NIST) has been guiding industry efforts through the many publications in its Computer Security Resource Center. NIST has played an especially important role in the adoption of Zero Trust architecture, through its series of publications that began with NIST SP 800-207: Zero Trust Architecture, released in 2020.
NIST has released another Special Publication in this series, SP 1800-35, titled "Implementing a Zero Trust Architecture (ZTA)" which aims to provide practical steps and best practices for deploying ZTA across various environments. NIST’s publications about ZTA have been extremely influential across the industry, but are often lengthy and highly detailed, so this blog provides a short and easier-to-read summary of NIST’s latest guidance on ZTA.
And so, in this blog post:
We summarize the key items you need to know about this new NIST publication, which presents a reference architecture for Zero Trust Architecture (ZTA) along with a series of “Builds” that demonstrate how different products from various vendors can be combined to construct a ZTA that complies with the reference architecture.
We show how Cloudflare’s Zero Trust product suite can be integrated with offerings from other vendors Continue reading
Network Digital Twins: Between PowerPoint and Reality
A Network Artist left an interesting remark on one of my blog posts:
It’s kind of confusing sometimes to see the digital twin (being a really good idea) never really take off.
His remark prompted me to resurface a two-year-old draft listing a bunch of minor annoyances that make Networking Digital Twins more of a PowerPoint project than a reality.
NAN094: Automate and Iterate With the NetBox Labs Community
On today’s show, we’re joined NetBox Labs co-founders Mark Coleman and Kris Beevers. They recount how they founded NetBox Labs and discuss its growth and how it’s being used. We also delve into the NetBox Labs community and its importance for users. And of course, there’s the ever-present AI discussion. Mark and Kris also talk... Read more »Cloudflare Log Explorer is now GA, providing native observability and forensics
We are thrilled to announce the General Availability of Cloudflare Log Explorer, a powerful new product designed to bring observability and forensics capabilities directly into your Cloudflare dashboard. Built on the foundation of Cloudflare's vast global network, Log Explorer leverages the unique position of our platform to provide a comprehensive and contextualized view of your environment.
Security teams and developers use Cloudflare to detect and mitigate threats in real-time and to optimize application performance. Over the years, users have asked for additional telemetry with full context to investigate security incidents or troubleshoot application performance issues without having to forward data to third party log analytics and Security Information and Event Management (SIEM) tools. Besides avoidable costs, forwarding data externally comes with other drawbacks such as: complex setups, delayed access to crucial data, and a frustrating lack of context that complicates quick mitigation.
Log Explorer has been previewed by several hundred customers over the last year, and they attest to its benefits:
“Having WAF logs (firewall events) instantly available in Log Explorer with full context — no waiting, no external tools — has completely changed how we manage our firewall rules. I can spot an issue, adjust the Continue reading
Connect any React application to an MCP server in three lines of code
You can deploy a remote Model Context Protocol (MCP) server on Cloudflare in just one-click. Don’t believe us? Click the button below.
This will get you started with a remote MCP server that supports the latest MCP standards and is the reason why thousands of remote MCP servers have been deployed on Cloudflare, including ones from companies like Atlassian, Linear, PayPal, and more.
But deploying servers is only half of the equation — we also wanted to make it just as easy to build and deploy remote MCP clients that can connect to these servers to enable new AI-powered service integrations. That's why we built use-mcp, a React library for connecting to remote MCP servers, and we're excited to contribute it to the MCP ecosystem to enable more developers to build remote MCP clients.
Today, we're open-sourcing two tools that make it easy to build and deploy MCP clients:
use-mcp — A React library that connects to any remote MCP server in just 3 lines of code, with transport, authentication, and session management automatically handled. We're excited to contribute this library to the MCP ecosystem to enable more developers to build remote MCP clients.
Dear Vendors, EVPN Route Attributes Matter
Another scary tale from the Archives of Sloppy Code: we can’t decide whether some attributes are mandatory or optional.
When I was fixing the errors in netlab SR-OS configuration templates, I couldn’t get the EBGP-based EVPN with overlapping leaf AS numbers to work. I could see the EVPN routes in the SR-OS BGP table, but the device refused to use them. I concluded (incorrectly) that there must be a quirk in the SR-OS EVPN code and moved on.
PP067: Protecting Secrets With Vault and TruffleHog
Secrets trickle out through misconfigurations, poor tooling, and rushed Git commits. Today’s guest, John Howard, joins us on Packet Protector to walk through practical secrets management with Vault and TruffleHog to help make sure you don’t expose your privates. John discusses work he’s done to build an automated process in his organization for developers and... Read more »Is Cisco Live Still The Place To Be

You may recall from my post about Cisco Live last year that I talked about legacy and passing the torch to a new generation of people being active at the event. It was a moment where I was happy for what was occurring and thrilled to see the continuation of the community. It’s now a year later and I have a very different outlook on Cisco Live that isn’t nearly as rosy. Which is why I asked the question in the post title.
Destination Unknown
If you are a Cisco customer or partner that wants the latest news about Cisco products and services then Cisco Live is the place you need to be to get them. Sure, you can watch the keynotes virtually and read all the press releases online. However, if you really want to get up close and personal with the technology you have to be there. After all, it was this need to be in-person that inspired our community in the first place. We showed up. We met up. And we made the event even better because we were there.
That was then. 2025 is a different story. The first hints about the situation came when I Continue reading
Securing Kubernetes Traffic with Calico Ingress Gateway
If you’ve managed traffic in Kubernetes, you’ve likely navigated the world of Ingress controllers. For years, Ingress has been the standard way of getting our HTTP/S services exposed. But let’s be honest, it often felt like a compromise. We wrestled with controller-specific annotations to unlock critical features, blurred the lines between infrastructure and application concerns, and sometimes wished for richer protocol support or a more standardized approach. This “pile of vendor annotations,” while functional, highlighted the limitations of a standard that struggled to keep pace with the complex demands of modern, multi-team environments. The Ingress model was stretched well beyond what it was originally designed for, and over time that led to portability issues, inconsistent behaviour, and real security vulnerabilities.
Ingress NGINX Retirement: Why This Matters Now
The Kubernetes Security Response Committee recently announced the retirement of Ingress NGINX, with support ending in March 2026. This decision reinforces the exact challenges the community has been raising for years. The same flexibility that made it popular early on, especially features like snippet-based configuration, became a major source of technical debt, vendor lockin and security exposure.
After the retirement date, Ingress NGINX will no longer receive security updates or bug fixes. Running Continue reading
HS106: Planning for the Epochalypse
IT teams deal with technology lifecycle issues all the time–including Y2K, which enterprises across the world grappled with for years. The Epochalypse, or Year 2038 Problem, is similar. Specifically, some Linux systems’ date-time counters will go from positive to negative at a specific date in 2038, potentially wreaking havoc on embedded systems and any other... Read more »Public Videos: Whole IPv6 Curriculum

Based on the feedback I received on LinkedIn and in private messages, I made all my IPv6 content public; you can watch those videos without an ipSpace.net account.
Want to spend more time watching free ipSpace.net videos? The complete list is here.
NB531: Cisco Spotlights AI, Unified Management at CLUS; Ultra Ethernet 1.0 Unveiled
Take a Network Break! Our Red Alert for the week is a remote code execution vulnerability in open-source XDR platform Wazuh. In tech news, we dig into several announcements from Cisco Live US including: unified management of Meraki and Catalyst gear, new switches, an AI Assistant for the Meraki dashboard, a Deep Network Model LLM,... Read more »netlab 25.06: Fixing Nokia SR-OS Configuration Templates
TL&DR: netlab release 25.06 was published last week.
Before discussing the new features, let’s walk the elephant out of the room: I changed the release versions to YY.MM scheme, so I will never again have to waste my time on the existential question of which number in the release specification to increase.
Now for the new features:
A QUIC Progress Report
There has been a major change in the landscape of the internet over the past few years with the progressive introduction of the QUIC transport protocol. Here I’d like to look at where we are up to with the deployment of QUIC on the public Internet. In so doing we also need to consider whether the DNS is ossifying in front of our eyes!QO100 early success
I have heard and been heard via QO-100! As a licensed radio amateur have sent signals via satellite as far away as Brazil.
What it is
QO-100 is the first geostationary satellite with an amateur radio payload. A “repeater”, if you will. Geostationary means that you just aim your antenna (dish) once, and you can use it forever.
This is amazing for tweaking and experimenting. Other amateur radio satellites are only visible in the sky for minutes at a time, and you have to chase them across the sky to make a contact before it’s gone.
They also fly lower, meaning they can only see a small part of the world at a time. QO-100 can at all times see and be seen by all of Africa, Europe, India, and parts of Brazil.
Needs a bit more equipment, though
Other “birds” (satellites) can be accessed using a normal handheld FM radio and something like an arrow antenna. Well, you should actually have two radios, so that you can hear yourself on the downlink while transmitting.
There are also linear amateur radio satellites. For them you need SSB radios, which narrows down which radios you can use. And you still need Continue reading
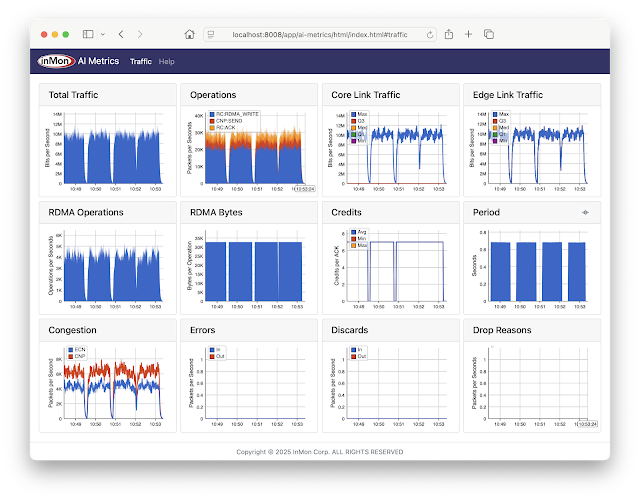
AI network performance monitoring using containerlab
AI Metrics is available on GitHub. The application provides performance metrics for AI/ML RoCEv2 network traffic, for example, large scale CUDA compute tasks using NVIDIA Collective Communication Library (NCCL) operations for inter-GPU communications: AllReduce, Broadcast, Reduce, AllGather, and ReduceScatter.The screen capture is from a containerlab topology that emulates a AI compute cluster connected by a leaf and spine network. The metrics include:
- Total Traffic Total traffic entering fabric
- Operations Total RoCEv2 operations broken out by type
- Core Link Traffic Histogram of load on fabric links
- Edge Link Traffic Histogram of load on access ports
- RDMA Operations Total RDMA operations
- RDMA Bytes Average RDMA operation size
- Credits Average number of credits in RoCEv2 acknowledgements
- Period Detected period of compute / exchange activity on fabric (in this case just over 0.5 seconds)
- Congestion Total ECN / CNP congestion messages
- Errors Total ingress / egress errors
- Discards Total ingress / egress discards
- Drop Reasons Packet drop reasons
Note: Clicking on peaks in the charts shows values at that time.
This article gives step-by-step instructions to run the demonstration.
git clone https://github.com/sflow-rt/containerlab.gitDownload the sflow-rt/containerlab project from GitHub.
git clone https://github.com/sflow-rt/containerlab.git cd containerlab ./run-clabRun the above commands Continue reading
Hedge 271: AI and Creativity
AI chatbots and image creators are all the rage right now–we are using them for everything from coding to writing books to creating short movies. One question we do not ask often enough, though, is how this impact human creators. How will these tools shape creativity and thinking skills?