Tech Bytes: An Introduction To Nokia’s Edge Network Controller (Sponsored)
Today on the Tech Bytes podcast we talk with sponsor Nokia about its Edge Network Controller, a Kubernetes-based application that lets you configure switch hardware in edge cloud locations and support a NetOps environment for edge deployments.Upcoming Training: Network Troubleshooting

I’m teaching a three-hour webinar on troubleshooting on the 22nd of April:
This training focuses on the half-split system of troubleshooting, which is widely used in the electronic and civil engineering domains. The importance of tracing the path of the signal, using models to put the system in context, and the use of a simple troubleshooting “loop” to focus on asking how, what, and why are added to the half-split method to create a complete theory of troubleshooting. Other concepts covered in this course are the difference between permanent and temporary fixes and a review of measuring reliability. The final third of the course contains several practical examples of working through problems to help in applying the theory covered in the first two sections to the real world.
This is offered on Safari Books Online through Pearson. I think that if you register for the course, you can watch a recording later.
The 2022 French Presidential election leaves its mark on the Internet


The first round of the 2022 French presidential elections were held this past Sunday, April 10, 2022, and a run-off will be held on April 24 between the top two candidates, Emmanuel Macron and Marine Le Pen. Looking at Internet trends in France for Sunday, it appears that when people were voting Internet traffic went down, and, no surprise, it went back up when results are coming in — that includes major spikes to news and election-related websites.
Cloudflare Radar data shows that Sundays are usually high-traffic days in France. But this Sunday looked a little different.
The seven-day Radar chart shows that there was a decrease in traffic compared to the previous Sunday between 08:00 and 16:00 UTC, that’s 10:00 and 18:00 in local time — bear in mind that polling stations in France were open between 08:00 and 19:00 (or 20:00 in big cities) local time. So, the decrease in traffic was ‘inside’ the period when French citizens were allowed to vote.
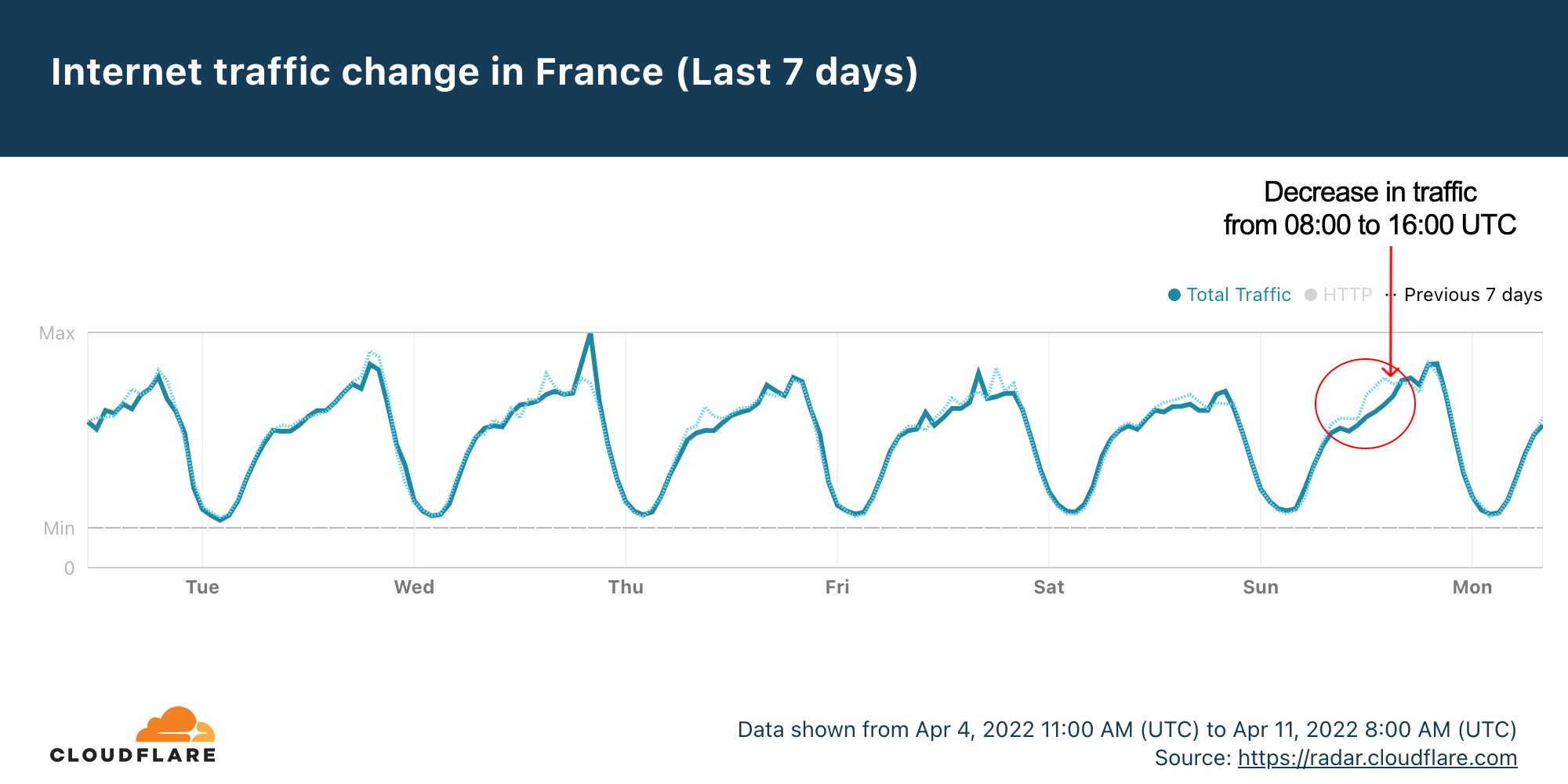
That’s a similar trend we have seen in other elections, like the Portuguese one back in January 2022.
The time of the French election day with the largest difference compared to the previous Sunday was 14:00 Continue reading
Device Management From The Ground Up: Part 8 – Configuration Archiving
If you want to create routine backups on your device or a local server, Cisco offers the “archive” feature on its IOS platform. I cover the various options we can pass to the archive command and go over an example of its use.
The post Device Management From The Ground Up: Part 8 – Configuration Archiving appeared first on Packet Pushers.
Network Break 377: AMD Buys Pensando; IBM Mainframe Marches On With z16
This week's Network Break discusses AMD's $1.9 billion bid for Pensando, why Juniper is partnering with Synopsys on silicon photonics, a new application access control feature from Cato Networks, and a new mainframe from IBM and a new lawsuit against it. Plus more tech news!Multicast PIM SSM – Source Specific Multicast
Multicast PIM SSM – Source Specific Multicast from a design point of view will be explained in this post. The Shortest Path Tree concept, Advantages, and disadvantages of Multicast PIM SSM will be covered as well.
What is Source Specific Multicast – PIM SSM?
PIM is a Multicast Routing Protocol. There are two categories of PIM protocol. PIM Dense mode and PIM Sparse Mode.
PIM Sparse Mode has 3 different modes of deployment. PIM SSM – Source Specific Multicast, PIM ASM – Any Source Multicast, and PIM Bidir – Bidirectional Multicast.
In this post, we will only cover PIM SSM but for the other PIM Sparse mode and PIM Dense mode design and deployment posts, place check Multicast category.
PIM SSM is called Source-Specific because Multicast receivers not only specify the Multicast Group that they are interested in but also they can signal to the network which course they are interested in or they are not interested in.
PIM SSM in the Routing Table
In the routers, we have multicast routing tables. SSM Multicast routing entries in the routers are seen as S, G.
S stands for multicast Source and G is used for multicast Group.
Source information has to Continue reading
BGP Private and Public AS Range
BGP Private and Public AS Range: On the internet, we have 2byte AS Numbers and 4 Byte AS Numbers. In this post, we will explain what are the BGP Private and Public AS Range for 2 byte AS and 4 byte AS numbers. Where Private BGP AS number is used and should be used and where Public AS Numbers in BGP is used and should be used. Not just where they should be used but also we will discuss where they shouldn’t be used too.
BGP Private AS Range for 2 Byte AS Numbers
A 2 byte AS number is a 16-bit number. This format provides for 65536 ASNs (0 to 65535). From these ASNs, the Internet Assigned Numbers Authority (IANA) reserved 1,023 of them (64512 to 65534) for private/internal usage.
BGP Private AS Range for 2-byte AS Number is between 64512 to 65535.
So we have 1023 BGP AS Numbers to use in a 2-byte ASN schema. Private AS numbers, similar to the Private IP address range (RFC 1918), should be used internally in the networks.
Not, external networks, such as the Internet. On Internet, in the Global Routing table, which is also known as Default Free Continue reading
Creating VRF Lite Labs With netsim-tools
I always found VRF lab setups a chore. On top of the usual IPAM tasks you have to create VRFs, assign route targets and route distinguishers, do that on every PE-router in your lab… before you can start working on interesting things.
I tried to remove as much friction as I could with the netsim-tools VRF configuration module – let me walk you through a few simple examples1 which will also serve to illustrate the VRF configuration differences between Cisco IOS and Arista EOS.
Creating VRF Lite Labs With netlab
I always found VRF lab setups a chore. On top of the usual IPAM tasks you have to create VRFs, assign route targets and route distinguishers, do that on every PE-router in your lab… before you can start working on interesting things.
I tried to remove as much friction as I could with the netlab VRF configuration module – let me walk you through a few simple examples1 which will also serve to illustrate the VRF configuration differences between Cisco IOS and Arista EOS.
AUSNOG ’21’
AUSNOG was held in April 2022 in Sydney over two days. Here are a few notes from presentations at the meeting that I found interesting.Events. My first MPLS World Congress: Impressions, Feelings, and Raise of AI.
Hello my friend,
This year I had an incredible opportunity to attend an event, which I wanted to attend for quite a bit back in past, when I was working for service providers (e.g., Vodafone, A1 BLR / Telekom Austria Group). The full name of the event is MPLS SDN and AI World Congress 2022, or simply #mplswc22.
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
Thanks
I’m very helpful to my friends and colleagues Pau Nadeu Rabat and Jose Manuel Roman Fernandez Checa for inviting me to take part in the event.
Brief History of the Event
MPLS SDN AI World Congress is one of the biggest events in the networking industry in the Europe. Originally it was called simple MPLS World Congress (hence, the name #mplswc22) and was aiming to bring together the biggest service providers (like the guys I worked for before, Deutsche Telekom, Orange, etc) and vendors of telecom equipment and software (like, Nokia, which I also Continue reading
BGP LU – Labeled Unicast – RFC 3107
BGP LU – BGP Labeled Unicast was defined in RFC 3107. BGP LU is used so commonly in many different network architectures and frameworks. In this post, BGP LU is explained with its use cases.
BGP LU – Labeled Unicast allows BGP to advertise an MPLS Label for the IPv4 and IPv6 Unicast prefixes.
Those who know MPLS may know but let me remind you if an IP prefix is learned via IGP routing protocols such as OSPF and IS-IS, then LDP, RSVP, and Segment Routing can assign an MPLS Label. But if the prefix is learned via BGP, only BGP can assign an MPLS Label. Assigning a label by BGP for the IPv4 or IPv6 Unicast prefix is known as BGP Labeled Unicast.
It is quite easy to understand what is BGP LU but at the beginning of the post, as I said, let’s have a look at its use cases.
BGP LU – RFC 3107 in Inter-AS MPLS VPN
It is used in Inter-AS MPLS VPN Option C, between the ASBRs (Autonomous System Boundary Routers).
In Inter-AS Option C, infrastructure prefixes of ASes are exchanged and for those prefixes, MPLS Label is assigned by BGP. Inter-AS MPLS Continue reading
Worth Reading: Full-Stack Network Automation
Lívio Zanol Puppim published a series of blog posts describing a full-stack network automation, including GitOps with GitLab, handling secrets with Hashicorp Vault, using Ansible and AWX to run automation scripts, continuous integration with Gitlab CI Runner, and topped it off with a REST API and React-based user interface.
You might not want to use the exact same components, but it’s probably worthwhile going through his solution and explore the source code. He’s also looking for any comments or feedback you might have on how to improve what he did.
Worth Reading: Full-Stack Network Automation
Lívio Zanol Puppim published a series of blog posts describing a full-stack network automation, including GitOps with GitLab, handling secrets with Hashicorp Vault, using Ansible and AWX to run automation scripts, continuous integration with Gitlab CI Runner, and topped it off with a REST API and React-based user interface.
You might not want to use the exact same components, but it’s probably worthwhile going through his solution and explore the source code. He’s also looking for any comments or feedback you might have on how to improve what he did.
Hedge: April Update
You can register for my network troubleshooting course here.
Information about the IEEE Network Softwarification Conference can be found here.
Our upcoming episodes for this month are George Michaelson on the death of ISDN and old networks; an update on the FR Routing project; and Rick Graziani on college and network engineering. Thanks for listening to the Hedge!
Unicast Multicast Broadcast Anycast and Incast Traffic Types
Unicast Multicast Broadcast Anycast and Incast Traffic Types will be explained in this post. Traffic flow/traffic types are important information that needs to be considered in Network Design, thus understanding each one of them by every IT Engineer is critical and Important for Application requirements, Security, and Performance of the overall system.
In this blog post, Unicast, Multicast, Broadcast, and Anycast traffic types/patterns will be explained with examples and the topologies.
Unicast Traffic Flow
Unicast traffic type is a point-to-point communication type. Usually from a scalability perspective, Unicast is not the desired traffic type. But if there are only two points that communicate with each other, Unicast is an optimal choice.
Multicast Traffic Flow
Point to Multipoint or Multi-Point to Multi-Point Traffic type. If the communication is targeted to a group of recipients, then the Multicast traffic type is more suitable. Multicast source/sender, receivers, and multicast groups are the components of Multicast communication. A classical example is IPTV – IP Television.
One multicast group is assigned for each IPTV channel and only interested receivers get the stream.
Broadcast Traffic Flow
If traffic is sent to everyone, regardless of considering if there is an uninterested receiver, then it is a broadcast Continue reading
Worth Reading: The AI Illusion
Russ White’s Weekend Reads are full of gems, including a recent pointer to the AI Illusion – State-of-the-Art Chatbots Aren’t What They Seem article. It starts with “Artificial intelligence is an oxymoron. Despite all the incredible things computers can do, they are still not intelligent in any meaningful sense of the word.” and it only gets better.
While the article focuses on natural language processing (GPT-3 model), I see no reason why we should expect better performance from AI in networking (see also: AI/ML in Networking – The Good, the Bad, and the Ugly).
Worth Reading: The AI Illusion
Russ White’s Weekend Reads are full of gems, including a recent pointer to the AI Illusion – State-of-the-Art Chatbots Aren’t What They Seem article. It starts with “Artificial intelligence is an oxymoron. Despite all the incredible things computers can do, they are still not intelligent in any meaningful sense of the word.” and it only gets better.
While the article focuses on natural language processing (GPT-3 model), I see no reason why we should expect better performance from AI in networking (see also: AI/ML in Networking – The Good, the Bad, and the Ugly).
