Device Management From The Ground Up: Part 3 – Storage And Filesystems
Your Cisco devices store and interact with files. In this article I cover the different storage types and how to navigate and manipulate them in the device configuration, including printing directories, making new directories, and more.
The post Device Management From The Ground Up: Part 3 – Storage And Filesystems appeared first on Packet Pushers.
Network performance update: Security Week


Almost a year ago, we shared extensive benchmarking results of last mile networks all around the world. The results showed that on a range of tests (TCP connection time, time to first byte, time to last byte), and on different measures (p95, mean), Cloudflare was the fastest provider in 49% of networks around the world. Since then, we’ve worked to continuously improve performance towards the ultimate goal of being the fastest everywhere. We set a goal to grow the number of networks where we’re the fastest by 10% every Innovation Week. We met that goal last year, and we’re carrying the work over to 2022.
Today, we’re proud to report we are the fastest provider in 71% of the top 1,000 most reported networks around the world. Of course, we’re not done yet, but we wanted to share the latest results and explain how we did it.
Measuring what matters
To quantify network performance, we have to get enough data from around the world, across all manner of different networks, comparing ourselves with other providers. We used Real User Measurements (RUM) to fetch a 100kb file from several different providers. Users around the world report the performance of different providers. Continue reading
A New One-Stop Shop for Network Security Topics
Your trusty NSX blog is going through a big change.
We’re uniting our VMware security content in the newly designed VMware Security blog.
Don’t worry, you’ll still be able to find the latest on network automation, application mobility, and load balancing. All the networking content you count on, that’s staying right here.
However, if you’re looking for current and future articles on network security and threat research, those will now be found in a new home—a blog that centralizes security content across VMware into a single channel.
You no longer need to switch (blog) channels for security news, insights, and resources. The newly designed VMware Security Blog will become your new one-stop-shop for key perspectives from experts, specialists, and leaders across VMware NSX, Threat Analysis Unit, and Carbon Black.
On the new blog, you can expect to find all the network security content you know and love — including:
- Important insights and announcements regarding threat research, endpoint security, and network security
- Key analysis of recent ransomware attacks, insights on techniques deployed, and how threats can be detected and mitigated
- Infographics, data points, and award recognition illustrating the strength of VMware security solutions
- Invites Continue reading
Network Break 374: Pluribus Extends DC Fabric To NVIDIA DPUs; Intel Buries Three FPGAs
In this week's Network Break we discuss Pluribus porting its network OS to NVIDIA DPUs, why Intel is pulling the plug on three FPGA cards in its portfolio, the debut of a network operations startup that draws from multiple data sources to help NetOps teams troubleshoot problems faster, and more IT news.Application security: Cloudflare’s view


Developers, bloggers, business owners, and large corporations all rely on Cloudflare to keep their applications secure, available, and performant.
To meet these goals, over the last twelve years we have built a smart network capable of protecting many millions of Internet properties. As of March 2022, W3Techs reports that:
“Cloudflare is used by 80.6% of all the websites whose reverse proxy service we know. This is 19.7% of all websites”
Netcraft, another provider who crawls the web and monitors adoption puts this figure at more than 20M active sites in their latest Web Server Survey (February 2022):
“Cloudflare continues to make strong gains amongst the million busiest websites, where it saw the only notable increases, with an additional 3,200 sites helping to bring its market share up to 19.4%”
The breadth and diversity of the sites we protect, and the billions of browsers and devices that interact with them, gives us unique insight into the ever-changing application security trends on the Internet. In this post, we share some of those insights we’ve gathered from the 32 million HTTP requests/second that pass through our network.
Definitions
Before we examine the data, it is useful to define Continue reading
New cities on the Cloudflare global network: March 2022 edition
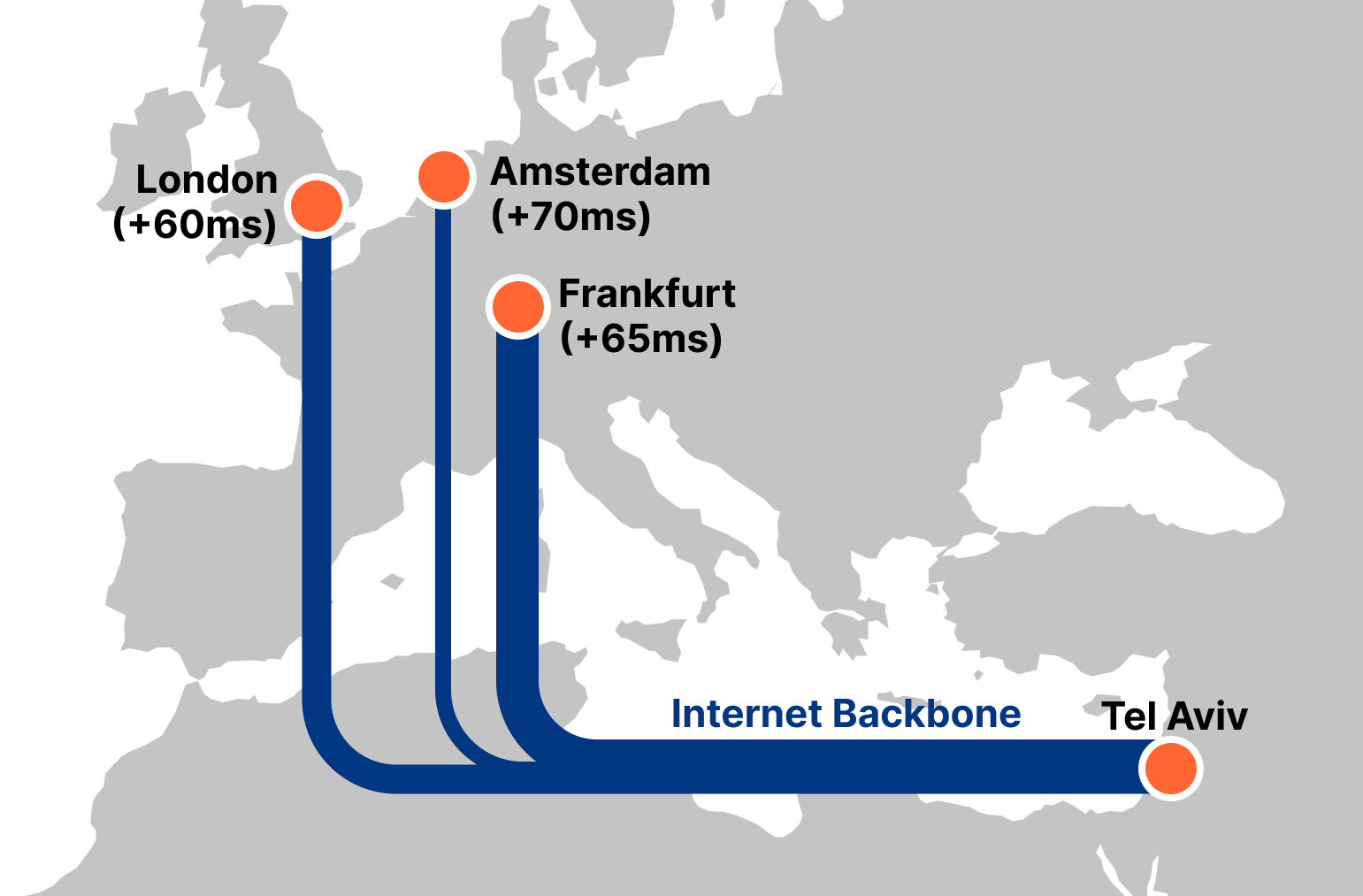
If you follow the Cloudflare blog, you know that we love to add cities to our global map. With each new city we add, we help make the Internet faster, more reliable, and more secure. Today, we are announcing the addition of 18 new cities in Africa, South America, Asia, and the Middle East, bringing our network to over 270 cities globally. We’ll also look closely at how adding new cities improves Internet performance, such as our new locations in Israel, which reduced median response time (latency) from 86ms to 29ms (a 66% improvement) in a matter of weeks for subscribers of one Israeli Internet service provider (ISP).
The Cities
Without further ado, here are the 18 new cities in 10 countries we welcomed to our global network: Accra, Ghana; Almaty, Kazakhstan; Bhubaneshwar, India; Chiang Mai, Thailand; Joinville, Brazil; Erbil, Iraq; Fukuoka, Japan; Goiânia, Brazil; Haifa, Israel; Harare, Zimbabwe; Juazeiro do Norte, Brazil; Kanpur, India; Manaus, Brazil; Naha, Japan; Patna, India; São José do Rio Preto, Brazil; Tashkent, Uzbekistan; Uberlândia, Brazil.
Cloudflare’s ISP Edge Partnership Program
But let’s take a step back Continue reading
DC Fabric Webinar

Sorry for the short notice … I’m teaching a three-hour webinar on DC fabrics and control planes this coming Friday, the 25th, through Safari Books Online. This course covers the basics of spine-and-leaf fabrics, as well as some high level information on various DC fabric control plane options (BGP, RIFT, and IS-IS). Please register here.
How to Pass AWS CLF
AWS CLF Exam
How to pass the Certified Cloud Practitioner from AWS, exam details and type, and what to expect
AWS CLF Exam Content & Topics
The exam agenda starts with the concept of cloud computing and differences of it with on-premise networks.
then it shows you all the AWS services that will be more than enough to migrate or establish a network on AWS’s cloud
which will have all the facilities and can be fully or partially managed by AWS for you.
and of course everything comes for a price, AWS will declare the prices of their services, what is for FREE and what is not
and will provide many easy tools for costs calculation and best practices with AWS.
Amazon’s Touch in the CLF Exam
Amazon provides a free tier 12-month access to whomever creates an account for the 1st time with them
the account has a free access to many AWS services that will allow for both studying and actual testing/benefiting from their services.
AWS CLF Exam Nature & Type
The current version of this exam CLF-C01 has a 65 written question in the exam.
all the questions are single/multi-answer MCQs and no other type of questions Continue reading
What is AWS CLF
What is AWS CLF
Amazon Web Services (AWS) CLF or CCP, how you want to name it (CLF is the official exam and badge name).
as it stands for Certified Cloud Practitioner, with the current version of CLF-C01.
AWS CLF is the very first step for any engineer, regardless of their experience in the IT domain,
to start understanding and put a step in the world of cloud computing.
CLF with AWS Services
The exam/certificate focuses on many different aspects, some are shared with other exams from AWS, some are CLF-Focused.
This includes the concept of cloud computing, comparison of many aspects of networking between On-premise networks and cloud networks.
Introduction to AWS and how much does AWS covers/offers of on-premise services on their cloud, ready to be directly initiated and used.
AWS most critical aspect when you decide to network on their infrastructure, and that is “Billing”, this is a very important and critical concept to really understand and know how to deal with when you start working with AWS networks.
Is AWS-CLF important?
Many tends to skip this exam, and keeps spreading the idea that “SAA is the Associate exam of AWS Services, and it should be the Continue reading
Automating NSX-T Deployments
Nicholas Michel open-sourced an automation solution (video) that deploys the whole NSX-T infrastructure stack including:
- NSX-T manager virtual machines
- NSX-T uplink profiles and IP pools
- Transport zones and transport nodes (NSX-T modules on ESXi hypervisors)
- Edge clusters including BGP, EVPN and BFD
Once the infrastructure is set up, his solution uses a Terraform configuration file to deploy multiple tenants: external VLANs, tier-0 gateways, BGP neighbors, tier-1 gateways, and application segments.
While the infrastructure part of his solution might be fully reusable, the tenant deployments definitely aren’t, but they provide a great starting point if you decide to build a fully automated provisioning system.
Automating NSX-T Deployments
Nicholas Michel open-sourced an automation solution (video) that deploys the whole NSX-T infrastructure stack including:
- NSX-T manager virtual machines
- NSX-T uplink profiles and IP pools
- Transport zones and transport nodes (NSX-T modules on ESXi hypervisors)
- Edge clusters including BGP, EVPN and BFD
Once the infrastructure is set up, his solution uses a Terraform configuration file to deploy multiple tenants: external VLANs, tier-0 gateways, BGP neighbors, tier-1 gateways, and application segments.
While the infrastructure part of his solution might be fully reusable, the tenant deployments definitely aren’t, but they provide a great starting point if you decide to build a fully automated provisioning system.
Tools 9. Monitoring Availability of Customers via HTTP GET, ICMP, and DNS via Dockerised Prometheus
Hello my friend,
in the previous blogpost we’ve started the discussion how you can improve your customers’ experience in your network via better observability of the network health with Prometheus by means of periodic automated speedtest and iperf3 measurements. Albeit it is very important and useful, it doesn’t tell you if the customers’ or your own resources are available. By resource we mean any exposed service, such as web page, streaming service, etc. Today you will learn how to setup a monitoring with Docekrised Prometheus to make sure that you know for sure if the services are available for customers.
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
Why to Automate Monitoring?
Monitoring allows to make you aware, what is the state of resources you are interested in. At a bare minimum, you shall be notified if the state of resources deviates from the acceptable value and, therefore, crosses some threshold. At the same time, this is just the first step. The end goal Continue reading
Unlocking QUIC’s proxying potential with MASQUE
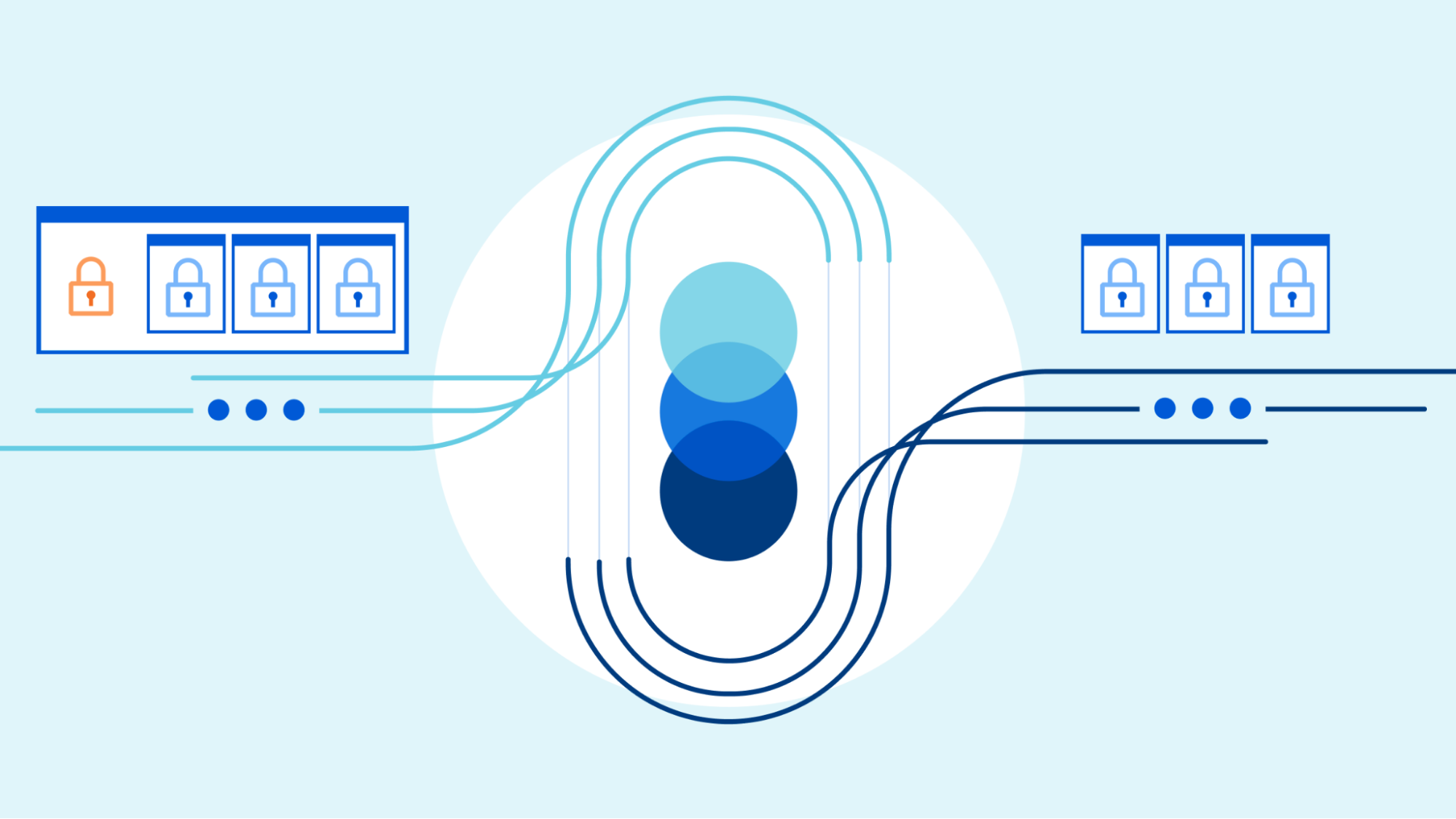
In the last post, we discussed how HTTP CONNECT can be used to proxy TCP-based applications, including DNS-over-HTTPS and generic HTTPS traffic, between a client and target server. This provides significant benefits for those applications, but it doesn’t lend itself to non-TCP applications. And if you’re wondering whether or not we care about these, the answer is an affirmative yes!
For instance, HTTP/3 is based on QUIC, which runs on top of UDP. What if we wanted to speak HTTP/3 to a target server? That requires two things: (1) the means to encapsulate a UDP payload between client and proxy (which the proxy decapsulates and forward to the target in an actual UDP datagram), and (2) a way to instruct the proxy to open a UDP association to a target so that it knows where to forward the decapsulated payload. In this post, we’ll discuss answers to these two questions, starting with encapsulation.
Encapsulating datagrams
While TCP provides a reliable and ordered byte stream for applications to use, UDP instead provides unreliable messages called datagrams. Datagrams sent or received on a connection are loosely associated, each one is independent from a transport perspective. Applications that are built on top of Continue reading
BGP communities for traffic steering – part 2: State Management across Data Centers
This post has been a while in the making and follows up on an article about BGP communities that can be found here. Then we followed it up with some more discussion about FW design and place, or lack there of, on this podcast which inspired me to finish up “part 2”.
Anyone who has ever had to run active/active data centers and has come across this problem of how do I manage state?
You can ignore it and prepare yourself for a late night at the worst time.
Take everyone’s word that systems will never have to talk to the a system in a different security zone in the remote DC
Utilize communities and BGP policy to manage state; which we’ll focus on here
One of the biggest reasons we see for stretching a virtual routing and forwarding (vrf) is to move DC to DC flows of the same security zone below FWs. This reduces the load on the firewall and makes for easier rule management. However, it does introduce a state problem.
We’ll be using the smallest EVPN-multisite deployment you’ve ever seen with Nexus 9000v and Fortinet FWs.
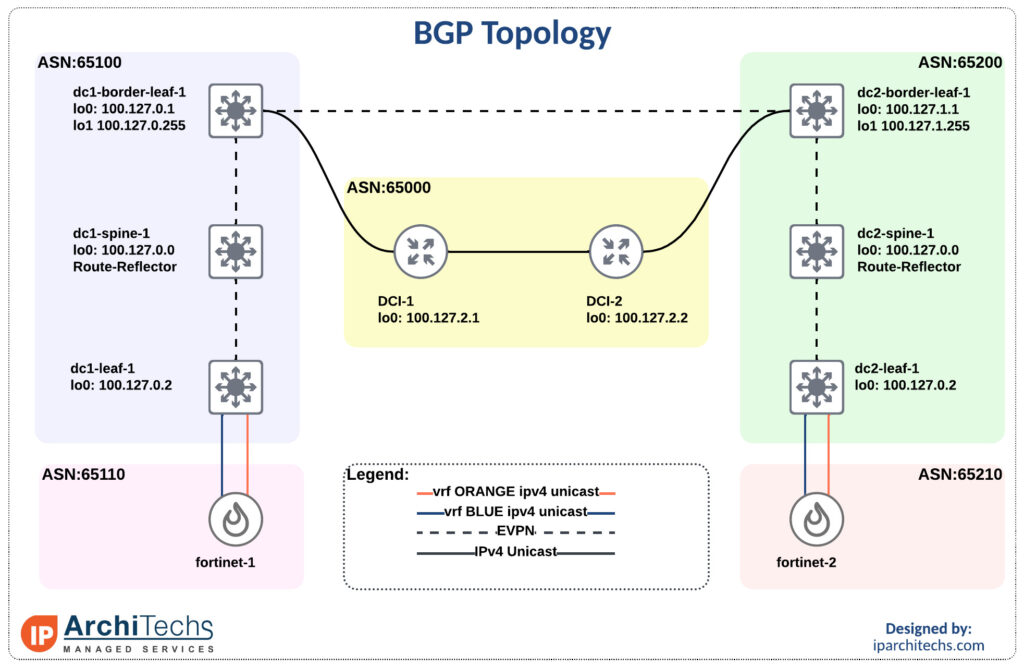
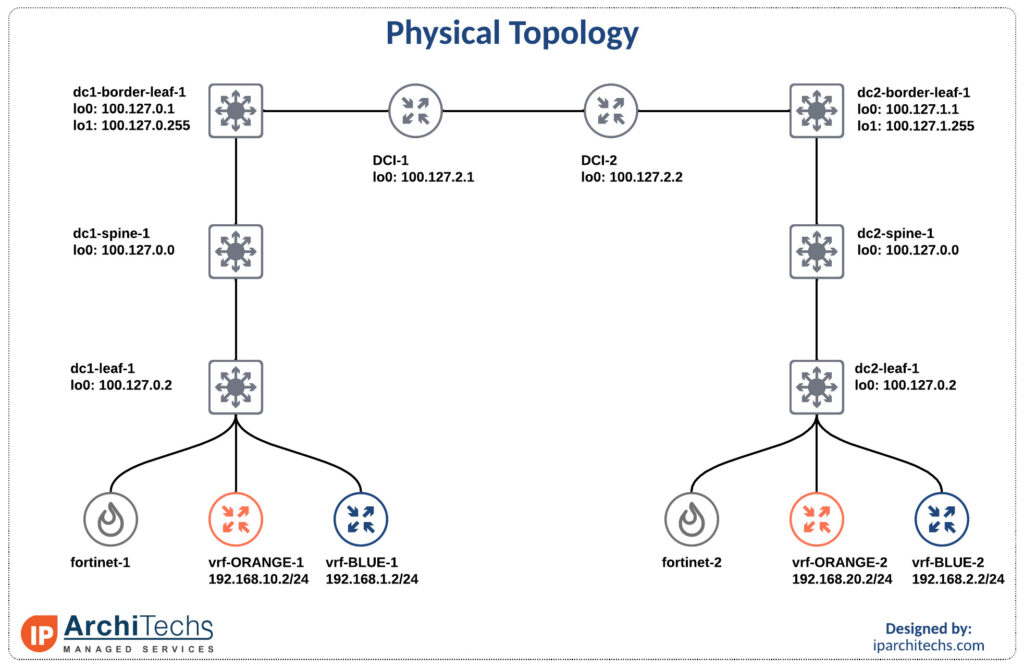

Inter vrf intra data center
The first flow we’ll look Continue reading
A Primer on Proxies

Traffic proxying, the act of encapsulating one flow of data inside another, is a valuable privacy tool for establishing boundaries on the Internet. Encapsulation has an overhead, Cloudflare and our Internet peers strive to avoid turning it into a performance cost. MASQUE is the latest collaboration effort to design efficient proxy protocols based on IETF standards. We're already running these at scale in production; see our recent blog post about Cloudflare's role in iCloud Private Relay for an example.
In this blog post series, we’ll dive into proxy protocols.
To begin, let’s start with a simple question: what is proxying? In this case, we are focused on forward proxying — a client establishes an end-to-end tunnel to a target server via a proxy server. This contrasts with the Cloudflare CDN, which operates as a reverse proxy that terminates client connections and then takes responsibility for actions such as caching, security including WAF, load balancing, etc. With forward proxying, the details about the tunnel, such as how it is established and used, whether or not it provides confidentiality via authenticated encryption, and so on, vary by proxy protocol. Before going into specifics, let’s start with one of the most common tunnels Continue reading