Extending Panorama’s firewall address groups into your Kubernetes cluster using Calico NetworkSets
When deploying cloud-native applications to a hybrid and multi-cloud environment that is protected by traditional perimeter-based firewalls, such as Palo Alto Networks (PAN) Panorama, you need to work within the confines of your existing IT security architecture. For applications that communicate with external resources outside the Kubernetes cluster, a traditional firewall is typically going to be part of that communication.
A good practice is to enable enterprise security teams to leverage existing firewall platforms, processes, and architectures to protect access to Kubernetes workloads.
Calico Enterprise already extends Panorama’s firewall manager to Kubernetes. The firewall manager creates a zone-based architecture for your Kubernetes cluster, and Calico reads those firewall rules and translates them into Kubernetes security policies that control traffic between your applications.
With its 3.11 release, Calico Enterprise extends its integration with PAN firewalls to include Panorama address groups in sync with Calico NetworkSets. The new release provides granular application security for your cloud-native application and eliminates workflow complexity.
This integration helps users to:
- Eliminate complex workflows when using existing PAN firewalls with Kubernetes workloads
- Extend their Panorama firewall investment to cloud-native applications
- Provide granular application security for their cloud-native applications
Why Calico’s integration is important
Cloud-native workloads require Continue reading
Internet shut down in Kazakhstan amid unrest

In Kazakhstan, the year had barely got going when yesterday disruptions of Internet access ended up in a nationwide Internet shutdown from today, January 5, 2022 (below you’ll find an update). The disruptions and subsequent shutdown happened amid mass protests against sudden energy price rises.
Cloudflare Radar shows that the full shutdown happened after 10:30 UTC (16:30 local time). But it was preceded by restrictions to mobile Internet access yesterday.
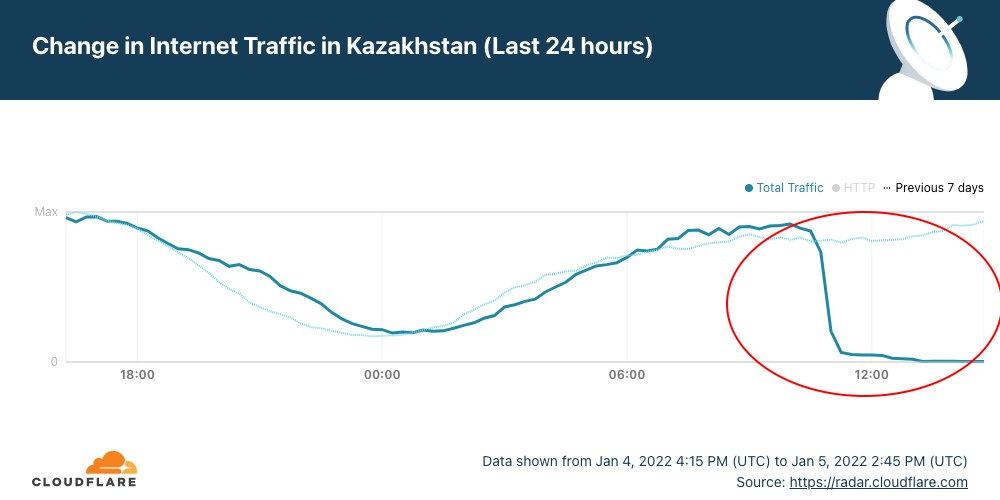
Our data confirm that Kazakhstan’s ASNs were affected after that time (around 18:30 local time). That’s particularly evident with the largest telecommunication company in the country, Kaz Telecom, as the next chart shows.
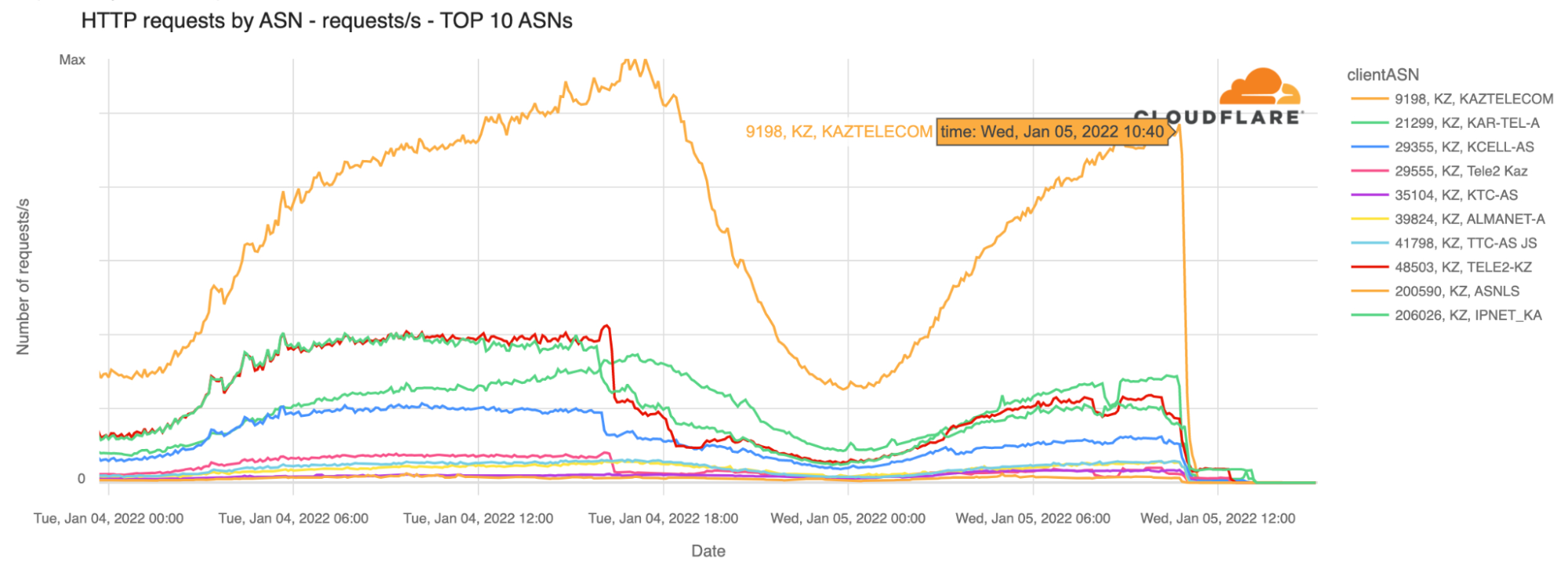
The first disruptions reported affected mobile services, and we can see that at around 14:30 UTC yesterday, January 4, 2022, there was significantly less mobile devices traffic than the day before around the same time. Kazakhstan is a country where mobile represents something like 75% of Internet traffic (shown on Radar), a usual trend in the region. So mobile disruption has a big impact on the country’s Internet, even before the shutdown that affected almost all connectivity.
When we focus on other ASNs besides Kaz Telecom such as the leading mobile Internet services Tele2 or Continue reading
Hedge 113: The PLM with Jeff Jakab
Over the last few episodes of the Hedge, we’ve been talking to folks involved in bringing network products to market. In this episode, Tom Ammon and Russ White talk to Jeff Jakab about the role of the Product Line Manager in helping bring new networking products to life. Join us to understand the roles various people play in the vendor side of the world—both so you can understand the range of roles network engineers can play at a vendor, and so you can better understand how products are designed, developed, and deployed.
How The Gambia lost access to the Internet for more than 8 hours


Internet outages are more common than most people think, and may be caused by misconfigurations, power outages, extreme weather, or infrastructure damage. Note that such outages are distinct from state-imposed shutdowns that also happen all too frequently, generally used to deal with situations of unrest, elections or even exams.
On the morning of January 4, 2022, citizens of The Gambia woke up to a country-wide Internet outage. Gamtel (the main state-owned telecommunications company of the West Africa country), announced that it happened due to "technical issues on the backup links" — we elaborate more on this below.
Cloudflare Radar shows that the outage had a significant impact on Internet traffic in the country and started after 01:00 UTC (which is the same local time), lasting until ~09:45 — a disruption of over 8 hours.

Looking at BGP (Border Gateway Protocol) updates from Gambian ASNs around the time of the outage, we see a clear spike at 01:10 UTC. These update messages are BGP signaling that the Gambian ASNs are no longer routable.
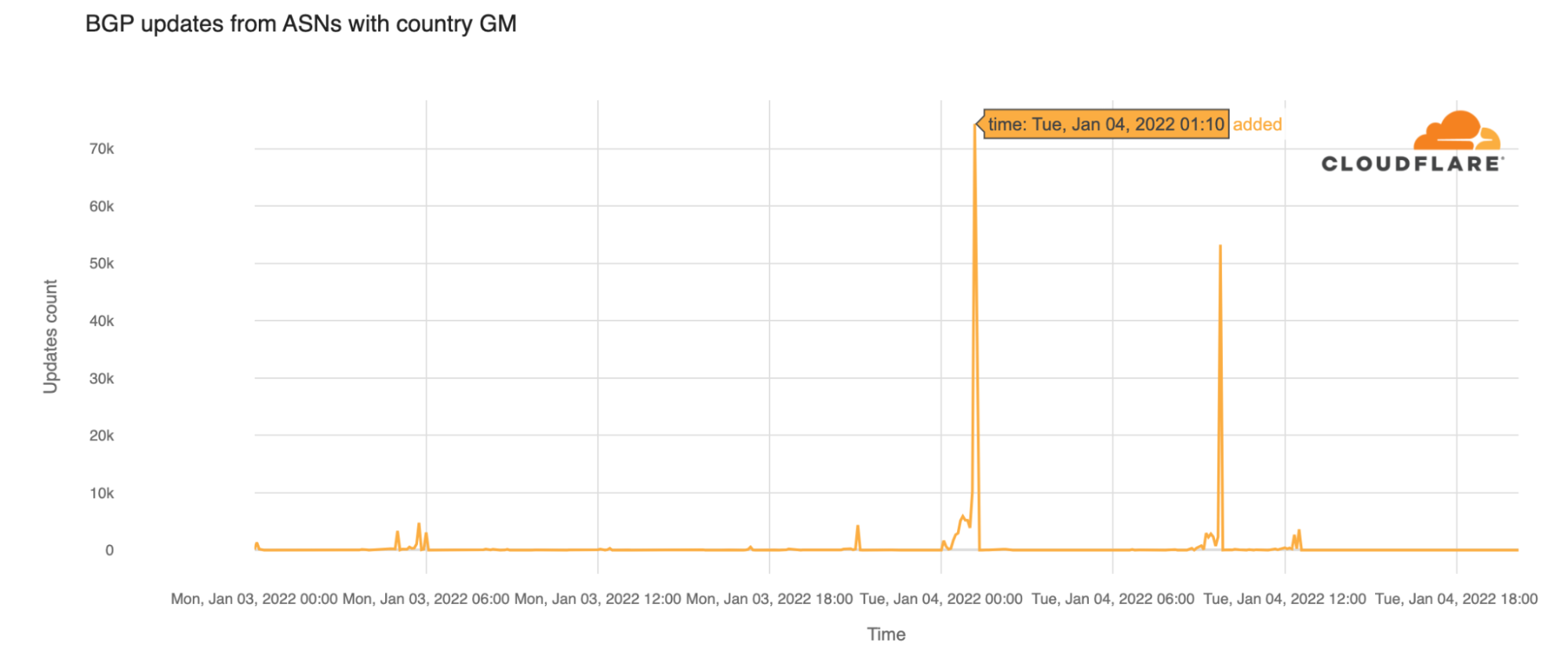
It is important to know that BGP is a mechanism to exchange routing information between autonomous systems (networks) on the Internet. The routers that make the Continue reading
Setting Flow Table Sizes on Juniper Routers
The post Setting Flow Table Sizes on Juniper Routers appeared first on Noction.
An Application-Layer Approach To Multi-Cloud Network Fabrics
This post was originally published on the Packet Pushers’ Ignition site on September 21, 2021. It sounds trite to say that enterprise IT environments are multi-cloud, but the extent of cloud heterogeneity might shock those not paying attention. A recent survey found that 44 percent of organizations had more than half of their workloads deployed […]
The post An Application-Layer Approach To Multi-Cloud Network Fabrics appeared first on Packet Pushers.
Recursive BGP Next Hops: an RFC 4271 Quirk
All BGP implementations I’ve seen so far use recursive next hop lookup:
- The next hop in the IP routing table is the BGP next hop advertised in the incoming update
- That next hop is resolved into the actual next hop using one or more recursive lookups into the IP routing table.
Furthermore, all BGP implementations I’ve seen used multiple recursive next hops (if available) to implement load balancing toward the BGP next hop – that’s how we made EBGP load balancing work in Stone Age of networking.
Recursive BGP Next Hops: an RFC 4271 Quirk
All BGP implementations I’ve seen so far use recursive next hop lookup:
- The next hop in the IP routing table is the BGP next hop advertised in the incoming update
- That next hop is resolved into the actual next hop using one or more recursive lookups into the IP routing table.
Furthermore, all BGP implementations I’ve seen used multiple recursive next hops (if available) to implement load balancing toward the BGP next hop – that’s how we made EBGP load balancing work in Stone Age of networking.
Procuring IPv4 Addresses: Wait in Line, Buy, or Lease
Scarce IPv4 addresses demand top dollar, opening up leasing opportunities and in some cases accelerated IPv6 migration timeframes.New Year, New Us?
It’s been a while, hope all are well. This is a behind the scenes update to share with you what has been going on with us at NC and where we are headed. Short story, we’ve taken a break but are getting back to it with new content, new ideas, and quite a few changes. If you want a heads up on what is coming, give this episode a listen. If you like surprises, well just ride it out and you’ll see soon enough. It’s good to be back.
The post New Year, New Us? appeared first on Network Collective.
Microsegmentation Terminology
While I liked reading the Where to Stick the Firewall blog post by Peter Welcher, it bothered me a bit that he used microsegmentation to mean security groups.
I know that microsegmentation became approximately as well-defined as cloud or SDN1, but let’s aim our shiny lance 2 at the nearest windmill and gallop away…
Microsegmentation Terminology
While I liked reading the Where to Stick the Firewall blog post by Peter Welcher, it bothered me a bit that he used microsegmentation to mean security groups.
I know that microsegmentation became approximately as well-defined as cloud or SDN1, but let’s aim our shiny lance 2 at the nearest windmill and gallop away…