How to Plan for a Data Center Migration
By migrating from a traditional data center environment to a cloud environment, teams will be able to more easily optimize their workloads using the tools that cloud platforms provide.Meet NFA v21.11: Interface names & descriptions, AS path prepends visibility, the use of AS names in Data Explorer, and more.
We’ve just rolled out some cool new features in Noction Flow Analyzer v 21.11 and hope you like them. Here’s what the
The post Meet NFA v21.11: Interface names & descriptions, AS path prepends visibility, the use of AS names in Data Explorer, and more. appeared first on Noction.
Sudan was cut off from the Internet for 25 days

Internet traffic started to come back in Sudan (with limitations) on Thursday, November 18, 2021. This happened after 25 days of an almost complete shutdown that affected the whole country. It’s a simple line going up on a chart for us, but for a country that also meant that Internet access was (at least in part) back on with all of what comes with it for businesses, communities, families and society as a whole.
You can see that trend on Cloudflare Radar, in particular after 13:00 UTC (15:00 local time). After that Internet traffic went up like we haven’t seen at all in the previous three weeks.
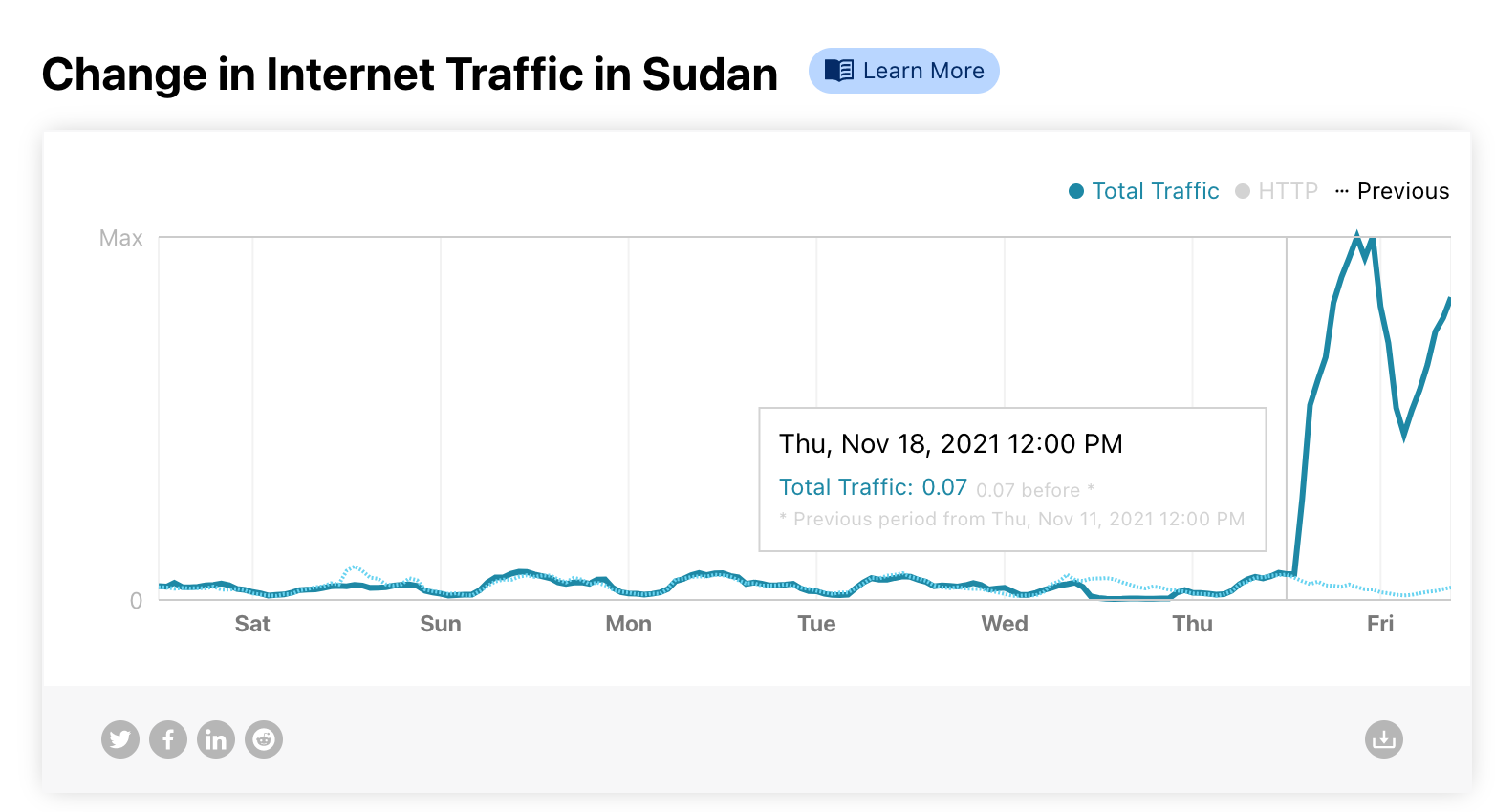
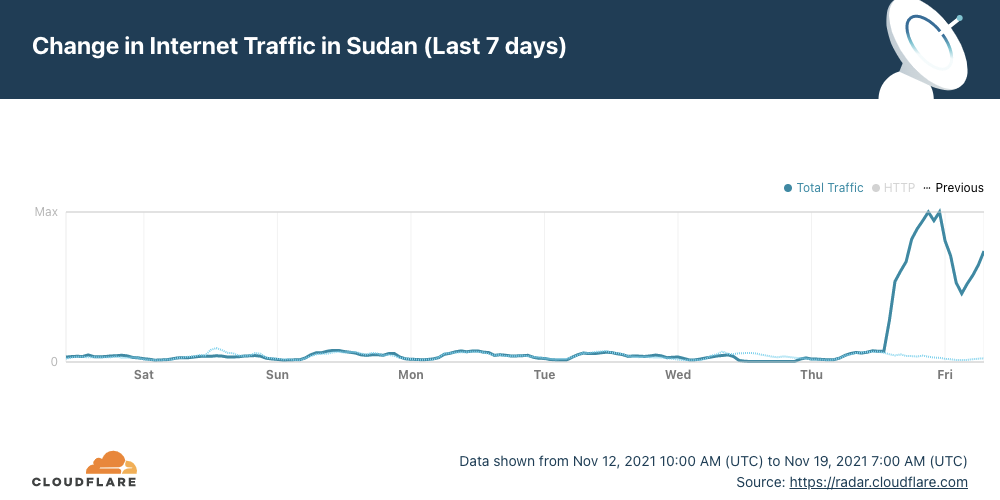
Internet access was mostly cut off on October 25, 2021, after a political turmoil in the country. A Sudanese court previously ordered the restoration of Internet access on November 9, but until last Thursday, November 18, there were no signs of services returning to normal. The biggest Internet access shutdown in recent history in the country was back in 2019 — for a full 36 days.
Looking back at the last 30 days Cloudflare Radar shows very distinctively a big difference from what was previously normal in the country.
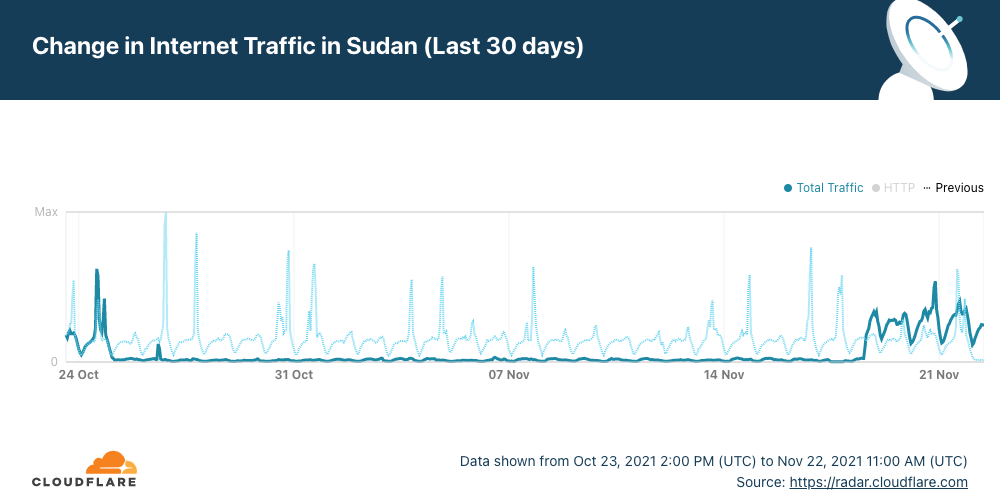
On Wednesday, Continue reading
Custom Groups and Deployment Templates in netsim-tools
Using custom templates to test IP anycast with MPLS was fun, but as I got into interesting discussions focusing on convoluted details, I found myself going through the same set of steps too many times.
It started with the need to specify individual devices in netlab config command to create new loopback interfaces on anycast servers but not on any other device in the lab. Wouldn’t it be nice to have a group of devices (similar to Ansible groups) that one could use in the limit parameter of netlab config?
netlab Custom Groups and Deployment Templates
Using custom templates to test IP anycast with MPLS was fun, but as I got into interesting discussions focusing on convoluted details, I found myself going through the same set of steps too many times.
It started with the need to specify individual devices in netlab config command to create new loopback interfaces on anycast servers but not on any other device in the lab. Wouldn’t it be nice to have a group of devices (similar to Ansible groups) that one could use in the limit parameter of netlab config?
Noction releases the new feature-rich NFA 21.11 version
The post Noction releases the new feature-rich NFA 21.11 version appeared first on Noction.
DINR 2021 Workshop Report
One of the more interesting recent events that acts as a showcase into early DNS research was the DNS and Internet Naming Research Directions (DINR) workshop.IETF 112
Here the rest of the notes from some selected working group meetings that caught my attention at the recent IETF 112 meeting that are not related to DNS work.RFC 9098: Operational Implications of IPv6 Extension Headers
It took more than seven years to publish an obvious fact as an RFC: IPv6 extension headers are a bad idea (RFC 9098 has a much more polite title or it would never get published).
RFC 9098: Operational Implications of IPv6 Extension Headers
It took more than seven years to publish an obvious fact as an RFC: IPv6 extension headers are a bad idea (RFC 9098 has a much more polite title or it would never get published).
Network Performance Update: Full Stack Week

This blog was published on November 20, 2021. As we continue to optimize our network we're publishing regular updates, which are available here.

A little over two months ago, we shared extensive benchmarking results of last mile networks all around the world. The results showed that on a range of tests (TCP connection time, time to first byte, time to last byte), and on a range of measurements (p95, mean), that Cloudflare was the fastest provider in 49% of networks around the world. Since then, we’ve worked to continuously improve performance until we’re the fastest everywhere. We set a goal to grow the number of networks where we’re the fastest by 10% every Innovation Week. We met that goal during Birthday Week (September 2021).
Today, we’re proud to report we blew the goal away for Full Stack Week (November 2021). Cloudflare measured our performance against the top 1,000 networks in the world (by number of IPv4 addresses advertised). Out of those, Cloudflare has become the fastest provider in 79 new networks, an increase of 14% of these 1,000 networks. Of course, we’re not done yet, but we wanted to share the latest results and explain how we did it.
However, Continue reading
Worth Reading: How to Get Useful Answers to Your Questions
Another must-read masterpiece by Julia Evans: how to get useful answers to your questions.
Worth Reading: How to Get Useful Answers to Your Questions
Another must-read masterpiece by Julia Evans: how to get useful answers to your questions.
A CIO’s Introduction to the Metaverse
The metaverse has arrived. Here's what CIOs need to know about it -- from business use cases, to risks, to vendor offerings from companies such as Microsoft, Nvidia, and Facebook.IP Class is Now in Session

You may have seen something making the rounds on Twitter this week about a couple of proposed drafts designed to alleviate the problems with IPv4 exhaustion by repurposing some old IP spaces that aren’t available for use right now. Specifically:
Ultimately, this is probably going to fail for a variety of reasons and looks like it’s more of a suggestion than anything else but I wanted to take a moment to talk about why this isn’t an effective way of fixing address issues.
Error Bearers
The first reason that the Schoen drafts are going to fail is because most of the operating systems in the world won’t allow you to use reserved spaces for a system address. Because we knew years ago that certain spaces were marked as non-usable the logic was configured into the system to disallow the use of those spaces. And even if the system isn’t configured to disallow that space there’s no guarantee the traffic is going to be transmitted.
Let’s take 127/8 as a good example. Was it a smart idea to mark 16 million addresses as loopback host-only space? Nope. But that ship has sailed and Continue reading
 Pathfinder plays an important
Pathfinder plays an important