Customer Experience Keys: Self-Service, Automation, and SD-WAN
Service providers can take simple steps to improve customer experience in their offerings by leveraging automation and offering self-service.Hedge 104: Automation with David Gee
Automation is often put forward as the answer to all our problems—but without a map, how can we be certain we are moving in the right direction? David Gee joins Tom Ammon and Russ White on this episode of the Hedge to talk about automata without a map. Where did we come from, what are we doing with automation right now, and what do we need to do to map out a truly better future?
Day Two Cloud 119: Unifying Multi-Cloud Security With Valtix (Sponsored)
Ethan Banks & Ned Bellavance have a tech discussion with CEO Doug Murray and CTO Vishal Jain about multi-cloud security startup Valtix. Along the way, we find out that Valtix is a cloud-delivered security control-plane paired with a data-plane of enforcement points (sort of firewalls, but not exactly) delivered between any two points in the cloud you need them. Engineers should walk away from this chat with a solid idea of Valtix architecture and how it fits into their cloud design.
The post Day Two Cloud 119: Unifying Multi-Cloud Security With Valtix (Sponsored) appeared first on Packet Pushers.
Day Two Cloud 119: Unifying Multi-Cloud Security With Valtix (Sponsored)
Ethan Banks & Ned Bellavance have a tech discussion with CEO Doug Murray and CTO Vishal Jain about multi-cloud security startup Valtix. Along the way, we find out that Valtix is a cloud-delivered security control-plane paired with a data-plane of enforcement points (sort of firewalls, but not exactly) delivered between any two points in the cloud you need them. Engineers should walk away from this chat with a solid idea of Valtix architecture and how it fits into their cloud design.As API Complexity Grows, Tame It With Centralized Governance
Axway CTIO Vince Padua believes the best path forward is to master growing API complexity, rather than attempt to simplify or consolidate IT ecosystems.Cloudflare and the IETF
The Internet, far from being just a series of tubes, is a huge, incredibly complex, decentralized system. Every action and interaction in the system is enabled by a complicated mass of protocols woven together to accomplish their task, each handing off to the next like trapeze artists high above a virtual circus ring. Stop to think about details, and it is a marvel.
Consider one of the simplest tasks enabled by the Internet: Sending a message from sender to receiver.
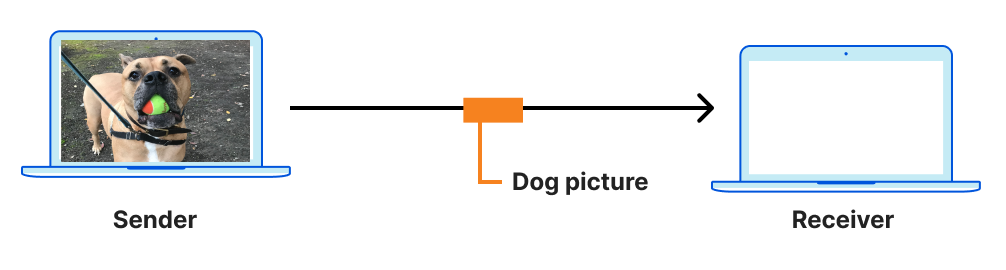
The location (address) of a receiver is discovered using DNS, a connection between sender and receiver is established using a transport protocol like TCP, and (hopefully!) secured with a protocol like TLS. The sender's message is encoded in a format that the receiver can recognize and parse, like HTTP, because the two disparate parties need a common language to communicate. Then, ultimately, the message is sent and carried in an IP datagram that is forwarded from sender to receiver based on routes established with BGP.
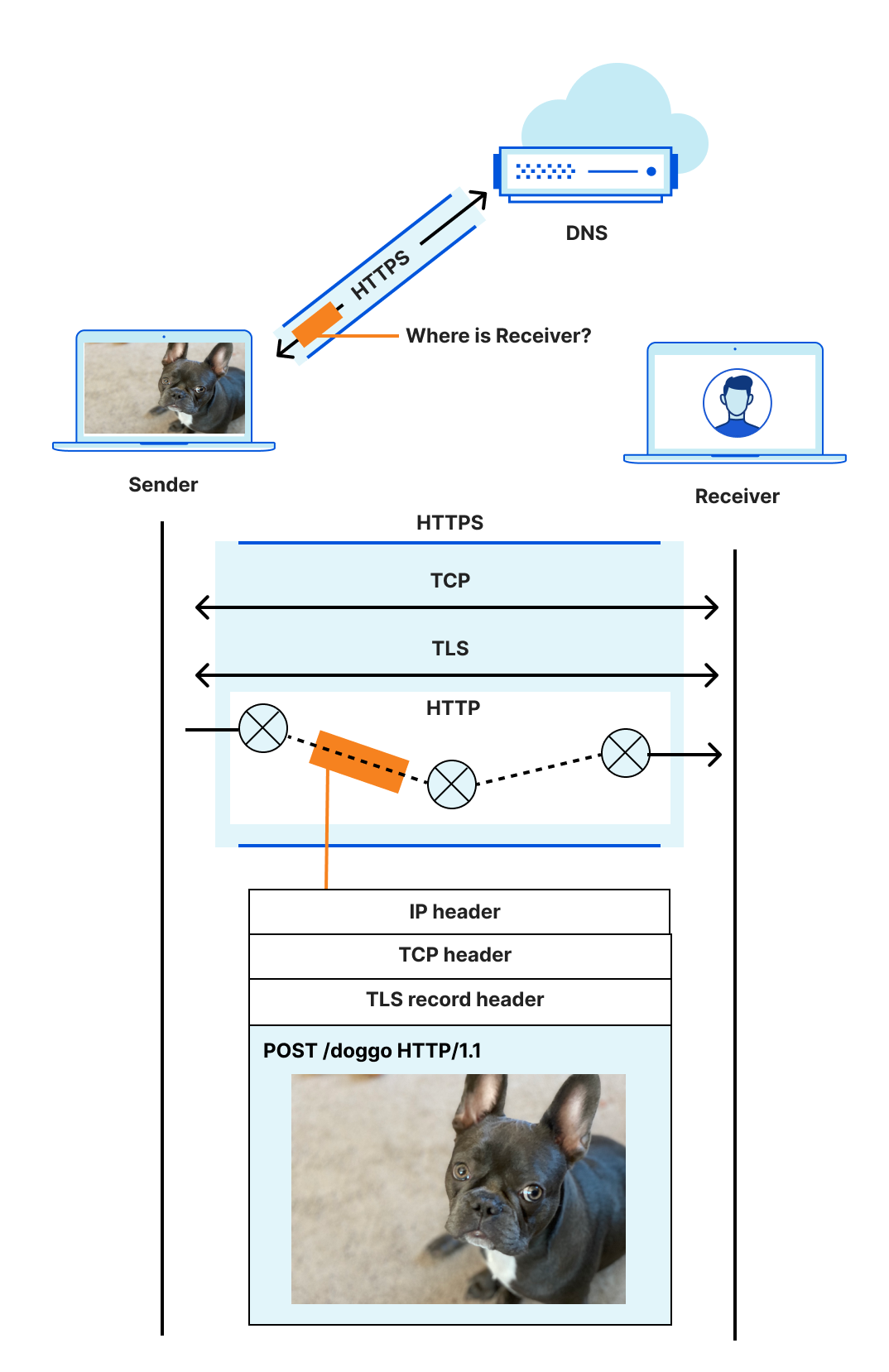
Even an explanation this dense is laughably oversimplified. For example, the four protocols listed are just the start, and ignore many others with acronyms of their own. The truth is that things are complicated. Continue reading
Pairings in CIRCL


In 2019, we announced the release of CIRCL, an open-source cryptographic library written in Go that provides optimized implementations of several primitives for key exchange and digital signatures. We are pleased to announce a major update of our library: we have included more packages for elliptic curve-based cryptography (ECC), pairing-based cryptography, and quantum-resistant algorithms.
All of these packages are the foundation of work we’re doing on bringing the benefits of cutting edge research to Cloudflare. In the past we’ve experimented with post-quantum algorithms, used pairings to keep keys safe around the world, and implemented advanced elliptic curves. Now we’re continuing that work, and sharing the foundation with everyone.
In this blog post we’re going to focus on pairing-based cryptography and give you a brief overview of some properties that make this topic so pleasant. If you are not so familiar with elliptic curves, we recommend this primer on ECC.
Otherwise, let’s get ready, pairings have arrived!
What are pairings?
Elliptic curve cryptography enables an efficient instantiation of several cryptographic applications: public-key encryption, signatures, zero-knowledge proofs, and many other more exotic applications like oblivious transfer and OPRFs. With all of those applications you might wonder what is Continue reading
Exported Authenticators: The long road to RFC
Our earlier blog post talked in general terms about how we work with the IETF. In this post we’re going to talk about a particular IETF project we’ve been working on, Exported Authenticators (EAs). Exported Authenticators is a new extension to TLS that we think will prove really exciting. It unlocks all sorts of fancy new authentication possibilities, from TLS connections with multiple certificates attached, to logging in to a website without ever revealing your password.
Now, you might have thought that given the innumerable hours that went into the design of TLS 1.3 that it couldn’t possibly be improved, but it turns out that there are a number of places where the design falls a little short. TLS allows us to establish a secure connection between a client and a server. The TLS connection presents a certificate to the browser, which proves the server is authorised to use the name written on the certificate, for example blog.cloudflare.com. One of the most common things we use that ability for is delivering webpages. In fact, if you’re reading this, your browser has already done this for you. The Cloudflare Blog is delivered over TLS, and by presenting a Continue reading
Coalescing Connections to Improve Network Privacy and Performance
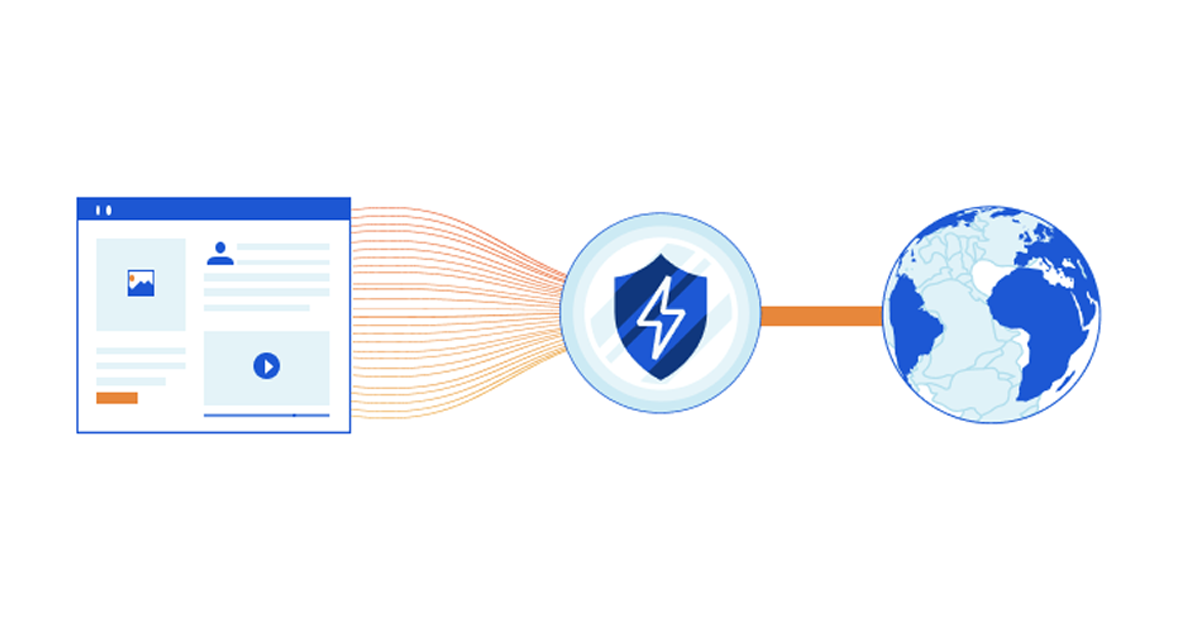
Web pages typically have a large number of embedded subresources (e.g., JavaScript, CSS, image files, ads, beacons) that are fetched by a browser on page loads. Requests for these subresources can prompt browsers to perform further DNS lookups, TCP connections, and TLS handshakes, which can have a significant impact on how long it takes for the user to see the content and interact with the page. Further, each additional request exposes metadata (such as plaintext DNS queries, or unencrypted SNI in TLS handshake) which can have potential privacy implications for the user. With these factors in mind, we carried out a measurement study to understand how we can leverage Connection Coalescing (aka Connection Reuse) to address such concerns, and study its feasibility.
Background
The web has come a long way and initially consisted of very simple protocols. One of them was HTTP/1.0, which required browsers to make a separate connection for every subresource on the page. This design was quickly recognized as having significant performance bottlenecks and was extended with HTTP pipelining and persistent connections in HTTP/1.1 revision, which allowed HTTP requests to reuse the same TCP connection. But, yet again, this was no Continue reading
Why Does DHCPv6 Matter?
In case you missed it, there’s a new season of Lack of DHCPv6 on Android soap opera on v6ops mailing list. Before going into the juicy details, I wanted to look at the big picture: why would anyone care about lack of DHCPv6 on Android?
The requirements for DHCPv6-based address allocation come primarily from enterprise environments facing legal/compliance/other layer 8-10 reasons to implement policy (are you allowed to use the network), control (we want to decide who uses the network) and attribution (if something bad happens, we want to know who did it).
Why Does DHCPv6 Matter?
In case you missed it, there’s a new season of Lack of DHCPv6 on Android soap opera on v6ops mailing list. Before going into the juicy details, I wanted to look at the big picture: why would anyone care about lack of DHCPv6 on Android?
The requirements for DHCPv6-based address allocation come primarily from enterprise environments facing legal/compliance/other layer 8-10 reasons to implement policy (are you allowed to use the network), control (we want to decide who uses the network) and attribution (if something bad happens, we want to know who did it).
Kubespray 2.17 released with Calico eBPF and WireGuard support
Congratulations to the Kubespray team on the release of 2.17! This release brings support for two of the newer features in Calico: support for the eBPF data plane, and also for WireGuard encryption.
Let’s dive into configuring Kubespray to enable these new features.
If you’re interested in getting started with Kubespray and Calico, you can refer to Using Calico with Kubespray, which covers some of the settings you might want to use, as well as how to enable Calico in several of the quick start guides.
To configure Calico options when using Kubespray to deploy a cluster, you’ll need to configure some variables. If you’re using the examples in the Kubespray repository, those files are under inventory/…/group_vars/k8s_cluster/, with the Calico options residing in k8s-net-calico.yml.
eBPF data plane
Calico offers several different data planes, ensuring that end users can choose the technology that’s right for their particular use case. eBPF is a relatively new set of facilities in the Linux kernel that lets developers write code to modify its functionality at runtime in a way that is safe and efficient.
Calico’s eBPF data plane offers increased efficiency, as well as functionality like providing source IP preservation Continue reading
Tech Bytes: Why Fortinet Zero Trust Works For You
Today on the Tech Bytes podcast we’re talking Zero Trust Network Access, or ZTNA, with sponsor Fortinet. As organizations grapple with controlling end user access to applications and services, particularly when those end users and applications could be anywhere, Fortinet is here to make the case that it’s the right platform for ZTNA. Our guest […]
The post Tech Bytes: Why Fortinet Zero Trust Works For You appeared first on Packet Pushers.
Tech Bytes: Why Fortinet Zero Trust Works For You
Today on the Tech Bytes podcast we’re talking Zero Trust Network Access, or ZTNA, with sponsor Fortinet. As organizations grapple with controlling end user access to applications and services, particularly when those end users and applications could be anywhere, Fortinet is here to make the case that it’s the right platform for ZTNA. Our guest... Read more »The Lingering Effect of Blind Spots in the Cloud
With visibility into your network, cloud services, product development, and your users, you can make significant gains across your security and compliance risks and your budget.Grafana Cloud
docker run -p 8008:8008 -p 6343:6343/udp --name sflow-rt -d sflow/prometheusUse Docker to run the pre-built sflow/prometheus image which packages sFlow-RT with the sflow-rt/prometheus application. Configure sFlow agents to stream data to this instance.
server:
Continue reading