Let’s talk MPLS-VPLS, part 1 – use cases
Hey guys, today we’ll be taking a look at what are the main reasons that MPLS – and in particular VPLS – is a useful technology tool to get traffic from point A to point Z. There’s really 2 major use cases that I deal with regularly: IPv4 conservation and L2VPN.
Why am I talking about VPLS specifically? Well, mostly because many times I end up working with Mikrotik routers, which only support VPLS. What is VPLS? It stands for Virtual Private Line Service, and it’s a way to deliver layer 2 services over a layer 3 network. Said another way, it connects a single broadcast domain to multiple endpoints across a routed network. I’ll discuss why MPLS is better for you and your network than switching/bridging in part 2 of this series – for now just know that MPLS/VPLS will allow you to offer enhanced services without the risks of extending layer 2 (I’ll talk more about that below, and why that’s bad in part 2, also).
Use case 1: IPv4 Conservation
OK, so let’s visualize the problem with IP conservation on a small /24 allocation.

If you’re like most other service providers, you have a Continue reading
How Working ‘The Internet Way’ Helped the Middle East and North Africa Score Social and Economic Benefits

In the Middle East and North Africa (MENA), some countries have responded to the challenges of the global pandemic by enacting policy changes, like temporarily lifting VoIP bans so citizens can communicate more easily. It’s giving the region a glimpse of the instant social and economic benefits of a thriving Internet. But are there other […]
The post How Working ‘The Internet Way’ Helped the Middle East and North Africa Score Social and Economic Benefits appeared first on Internet Society.
VARs See You As Technical Debt

I’ve worked for a Value Added Reseller (VAR) in the past and it was a good run of my career before I started working at Tech Field Day. The market was already changing eight years ago when I got out of the game. With the advent of the pandemic that’s especially true today. Quite a few of my friends say they’re feeling the pressure from their VAR employer to stretch beyond what they’re accustomed to doing or outright being treated in such a way as to be forced out or leaving on their own. They tell me they can’t quite understand why that’s happening. After some thought on the matter I think I know. Because you represent debt they need to retire.
Skill Up
We don’t start our careers knowing everything we need to know to make it. The industry spends a lot of time talking about careers and skill paths and getting your legs under you. Networking people need to learn Cisco or Juniper or whatever configuration language makes the most sense for them. Wireless people need to learn how to do site surveys and configure access points. Server people need to learn operating systems and hypervisors. We start Continue reading
Heavy Networking 587: When Your Side Project Gets Billions Of Hits – The ICanHazIP Saga
Today on Heavy Networking, the icanhazip story. On the surface, icanhazip.com is simple enough: You hit the URL, and get back your external, public IP address. There are no ads, no blinky lights, just an IP. This free, simple utility has become widely popular, with billions of requests per day. We talk with creator Major Hayden about why and how he built icanhazip, the time and money he's invested, and the insane amount of personal effort it's taken to keep it going.
The post Heavy Networking 587: When Your Side Project Gets Billions Of Hits – The ICanHazIP Saga appeared first on Packet Pushers.
Heavy Networking 587: When Your Side Project Gets Billions Of Hits – The ICanHazIP Saga
Today on Heavy Networking, the icanhazip story. On the surface, icanhazip.com is simple enough: You hit the URL, and get back your external, public IP address. There are no ads, no blinky lights, just an IP. This free, simple utility has become widely popular, with billions of requests per day. We talk with creator Major Hayden about why and how he built icanhazip, the time and money he's invested, and the insane amount of personal effort it's taken to keep it going.What to Do If You Hate Networking?
Running a business isn’t the easiest when you are not social. A business requires connections and vendors. It involves networking and going out of the comfort zone to settle in and make friends with people you may generally not talk to. So, what can you do if you are a person who wants to run a business but doesn’t like the networking part?
Well, the answer is simple. There are a few ways to make it easier for yourself, and it won’t be that much of a burden on you. The fact of the matter is that networking is something that you can not get rid of. So, rather than suffering through it, all you need to do is see it differently. A way that will make it a more effective process for you and a beneficial strategy for your business.
Here are a few simple pointers that will help you stay on point.
Make Learning the Focus
Many people think it has to do with you forcing yourself to talk to a bunch of boring people when it comes to networking. Instead of focusing on the competition and thinking about how boring a networking event will Continue reading
From Zero Visibility to Zero Trust in the Data Center
Imagine someone breaking into your home. If you catch them in the act, they’re most likely leaving right away, and you’re upping your security system. Now imagine someone breaking into your home, and staying for nine months – now what? They’ve prolonged their stay completely unnoticed and destroyed the security system you once trusted and relied upon. Your next move? Trying to reinstate the faith you once had in security and completely reconfigure your security blueprint.
Let’s break down why data center security has taken center stage as of late with the increasing challenges of securing east-west traffic and the journey from zero visibility to Zero Trust thanks to Forrester and VMware’s collaborative webinar session. (Or, feel free to get straight to all the juicy details, and watch the webinar now.)
The Catapult for Enhanced Data Center Security
We’re on the heels of the global COVID-19 pandemic, and wow, have things changed. As a global community, we were trying to juggle the unknown and potential threats that COVID-19 had posed. From an industry perspective, we had to engage in an overhaul that changed the way we worked – forever. For organizations everywhere, remote work is now a part of the new normal routine. So, with these massive changes, Continue reading
The Packets Never Lie
In this episode, Phil and Brandon interview Kary Rogers, AKA PacketBomb, and discuss the need to drill down into packets when troubleshooting. The group shares a few stories from the trenches on how packets helped them solve issues and Kary explains how he got started looking at Packets for deeper information.
Reference Links:
The post The Packets Never Lie appeared first on Network Collective.
Beware the Abandoned Office and its Security Vulnerabilities
As an industry, we have not seen this problem at scale, but abandoned offices, abandoned assets, and out-of-business companies are a ripe target for cyber adversaries.MikroTik RouterOS – v7.0.3 stable (chateau) and status of general release
If you don’t already use it, the MIkroTik v7 BETA forum (forum.mikrotik.com) is a fantastic source of information
When will stable be released?
This is the million dollar question. Technically, it already has been for one hardware platform…
!! Spoiler Alert – There is *already* a stable release of ROSv7 – v7.0.3!!
The Chateau 5G router originally shipped with a beta version of ROSv7 but was quietly moved to a stable version that’s developed specifically for that platform.

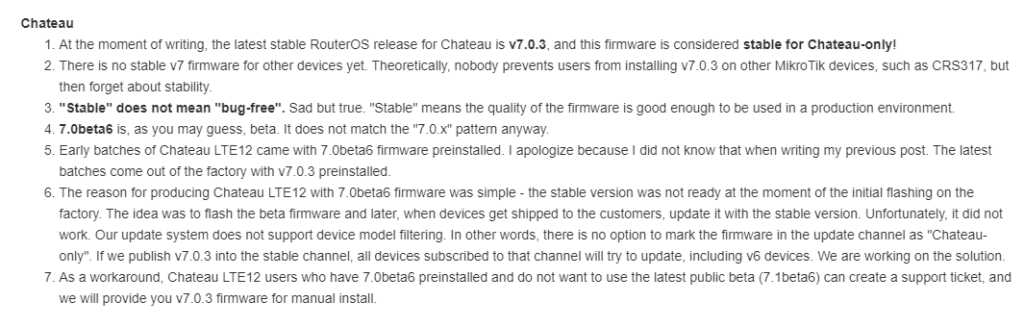
Because of the way MikroTik’s code repo works, this version can’t easily be added to the main download page and support provides the software:
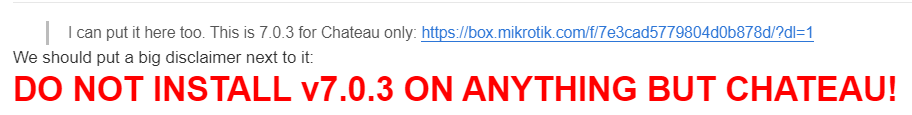
ROSv7.0.3 Stable Download (!!! Chateau Only – will brick other hardware !!!)
https://box.mikrotik.com/f/7e3cad5779804d0b878d/?dl=1
It’s worth repeating MikroTik’s warning about using this on any platform other than the Chateau

What’s holding up v7 from being released?
If you’ve been around MikroTik for a while, then you know that version 7 has been in the works for a long time to add new functionality and address limitations of the older Linux kernel in ROSv6.
MikroTik recently Continue reading
What’s new in Calico Enterprise 3.7: eBPF data plane, high availability, and more!
As our enterprise customers build out large, multi-cluster Kubernetes environments, they are encountering an entirely new set of complex security, observability, and networking challenges, requiring solutions that operate at scale and can be deployed both on-premises and across multiple clouds. New features in our latest release add to the already formidable capabilities of Calico Enterprise.
New feature: High-availability connectivity for Kubernetes with dual ToR
Many platform operators who run Kubernetes on-premises want to leverage Border Gateway Protocol (BGP) to peer with other infrastructure. Calico uses BGP to peer with infrastructure within the cluster as well as outside of the cluster, and integrates with top-of-rack (ToR) switches to provide that connectivity.
Calico ToR connectivity has existed for some time now. However, for cluster operators using BGP who need reliable, consistent connectivity to resources outside of the cluster as well as cluster nodes on different racks, Calico Enterprise dual ToR connectivity ensures high availability with active-active redundant connectivity planes between cluster nodes and ToR switches. A cluster that is peered to two ToR switches will still have an active link, even if one switch becomes unavailable, thus ensuring the cluster always has a network connection. Kubernetes cannot do this on its Continue reading
Distributed Cloud: The Future of Cloud Computing
Distributed cloud architectures enhance the benefits of traditional cloud adding more edge processing power and geo-specific data management.Convergence & Complexity Go Hand In Hand
 Many ways to converge .... Many types of converge
Many ways to converge .... Many types of converge
Private 5G is Anti-Cloud ?
 Because why own it ?
Because why own it ?


