Feedback: Azure Networking
When I started developing AWS- and Azure Networking webinars, I wondered whether they would make sense – after all, you can easily find tons of training offerings focused on public cloud services.
However, it looks like most of those materials focus on developers (no wonder – they are the most significant audience), with little thought being given to the needs of network engineers… at least according to the feedback left by one of ipSpace.net subscribers.
Feedback: Azure Networking
When I started developing AWS- and Azure Networking webinars, I wondered whether they would make sense – after all, you can easily find tons of training offerings focused on public cloud services.
However, it looks like most of those materials focus on developers (no wonder – they are the most significant audience), with little thought being given to the needs of network engineers… at least according to the feedback left by one of ipSpace.net subscribers.
Worth Reading: The Neuroscience of Busyness
In the Neuroscience of Busyness article, Cal Newport describes an interesting phenomenon: when solving problems, we tend to add components instead of removing them.
If that doesn’t describe a typical network (or protocol) design, I don’t know what does. At least now we have a scientific basis to justify our behavior ;)
Worth Reading: The Neuroscience of Busyness
In the Neuroscience of Busyness article, Cal Newport describes an interesting phenomenon: when solving problems, we tend to add components instead of removing them.
If that doesn’t describe a typical network (or protocol) design, I don’t know what does. At least now we have a scientific basis to justify our behavior ;)
EVE-NG Cloud NAT
This post explains how to configure EVE-NG as a DHCP server (isc-dhcp-server) assigning IPs to lab devices that are then dynamically NATed behind the primary EVE management IP address (iptables masquerade) to provide Internet breakout.
Worth Reading: Switching to IP fabrics
Namex, an Italian IXP, decided to replace their existing peering fabric with a fully automated leaf-and-spine fabric using VXLAN and EVPN running on Cumulus Linux.
They documented the design, deployment process, and automation scripts they developed in an extensive blog post that’s well worth reading. Enjoy ;)
Worth Reading: Switching to IP fabrics
Namex, an Italian IXP, decided to replace their existing peering fabric with a fully automated leaf-and-spine fabric using VXLAN and EVPN running on Cumulus Linux.
They documented the design, deployment process, and automation scripts they developed in an extensive blog post that’s well worth reading. Enjoy ;)
MikroTik – RouterOSv7 first look – MLAG on CRS 3xx switches
What is MLAG?
Multi-Chassis Link Aggregation Group or MLAG is an idea that’s been around for a while.
It allows for the ability to form LACP channels across multiple physical switches.
Wikipedia shows a few different topology examples here
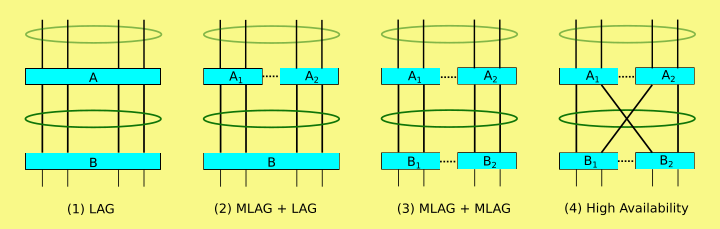
Vendor implementations are proprietary but the idea of MLAG was first mentioned in 802.1AX-2008 in 2008.
It first started to become popular in data center networking in the late 2000s
What makes the addition of MLAG to MikroTik’s RouterOS feature set notable is that it lowers the barrier to entry for this particular feature.
CRS 3xx switches are very inexpensive (starting at $149 USD) and may very well be the lowest cost MLAG capable hardware available on the market.

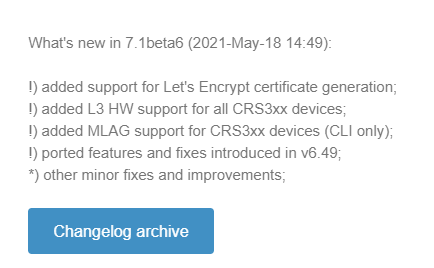
Introduced in 7.1beta6
MLAG has been asked for by the MikroTik community a number of times and the most active feature request thread started here in 2020:
new feature request MLAG!!! – MikroTik
MikroTik added several version 7 beta releases in 2021 and included MLAG for all CRS 3xx series switches in 7.1beta6 on May 18th, 2021.
Overview of protocol requirements
MLAG is fairly consistent across vendors with the need Continue reading
Heavy Networking 581: How Gluware Lab Brings DevOps To NetOps (Sponsored)
On today's Heavy Networking, we get practical with infrastructure-as-code, talking with sponsor Gluware about how their users have integrated network automation into their IT practices, bringing DevOps to NetOps. We also explore Gluware Lab, an IDE for network engineers can develop network features and workflows. Our guests are Olivier Huynh Van, Chief Science Officer and Co-Founder; and Michael Haugh, VP of Product Marketing.
The post Heavy Networking 581: How Gluware Lab Brings DevOps To NetOps (Sponsored) appeared first on Packet Pushers.
Heavy Networking 581: How Gluware Lab Brings DevOps To NetOps (Sponsored)
On today's Heavy Networking, we get practical with infrastructure-as-code, talking with sponsor Gluware about how their users have integrated network automation into their IT practices, bringing DevOps to NetOps. We also explore Gluware Lab, an IDE for network engineers can develop network features and workflows. Our guests are Olivier Huynh Van, Chief Science Officer and Co-Founder; and Michael Haugh, VP of Product Marketing.Network-based policies in Cloudflare Gateway
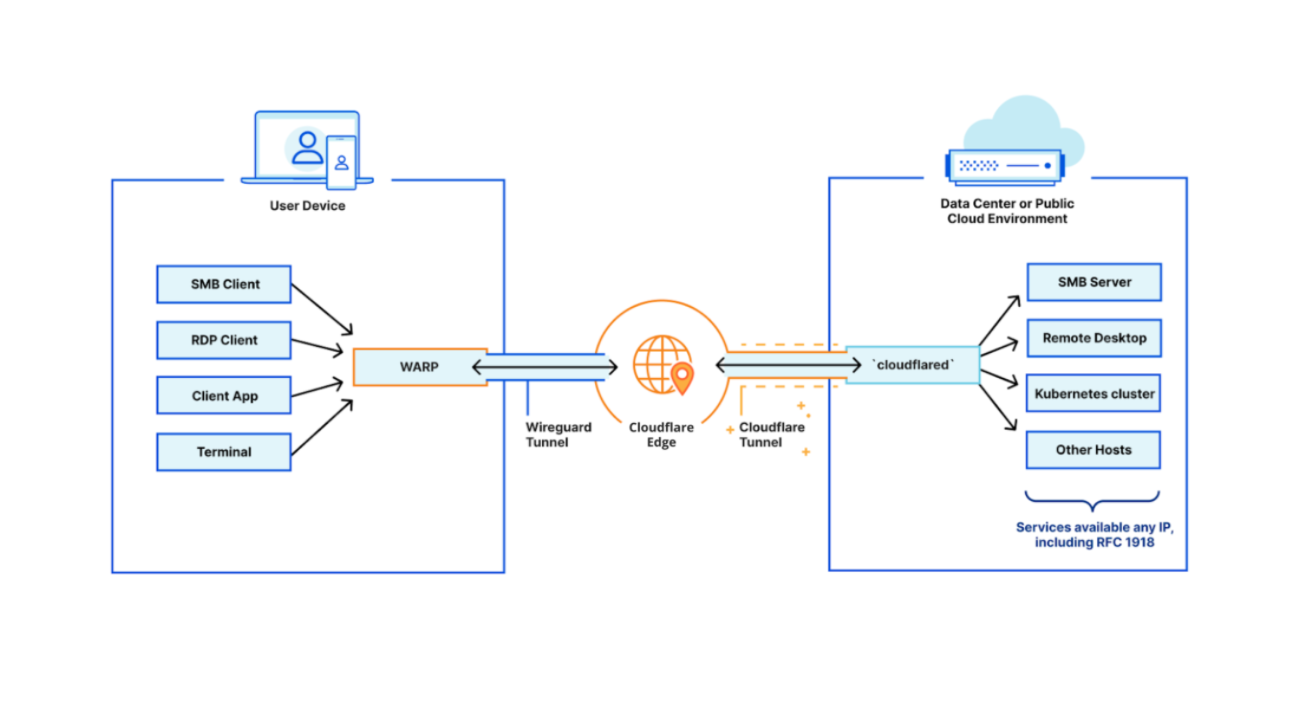
Over the past year, Cloudflare Gateway has grown from a DNS filtering solution to a Secure Web Gateway. That growth has allowed customers to protect their organizations with fine-grained identity-based HTTP policies and malware protection wherever their users are. But what about other Internet-bound, non-HTTP traffic that users generate every day — like SSH?
Today we’re excited to announce the ability for administrators to configure network-based policies in Cloudflare Gateway. Like DNS and HTTP policy enforcement, organizations can use network selectors like IP address and port to control access to any network origin.
Because Cloudflare for Teams integrates with your identity provider, it also gives you the ability to create identity-based network policies. This means you can now control access to non-HTTP resources on a per-user basis regardless of where they are or what device they’re accessing that resource from.
A major goal for Cloudflare One is to expand the number of on-ramps to Cloudflare — just send your traffic to our edge however you wish and we’ll make sure it gets to the destination as quickly and securely as possible. We released Magic WAN and Magic Firewall to let administrators replace MPLS connections, define routing decisions, and apply packet-based Continue reading
Charting the Course For Aruba

By now you’ve seen the news that longtime CEO of Aruba Keerti Melkote is retiring. He’s decided that his 20-year journey has come to a conclusion and he is stepping down into an advisory role until the end of the HPE fiscal year on October 31, 2021. Leaving along with him are CTO Partha Narasimhan and Chief Architect Pradeep Iyer. It’s a big shift in the way that things will be done going forward for Aruba. There are already plenty of hot takes out there about how this is going to be good or bad for Aruba and for HPE depending on which source you want to read. Because I just couldn’t resist I’m going to take a stab at it too.
Happy Trails To You
Keerti is a great person. He’s smart and capable and has always surrounded himself with good people as well. The HPE acquisition honestly couldn’t have gone any better for him and his team. The term “reverse acquisition” gets used a lot and I think this is one of the few positive examples of it. Aruba became the networking division of HPE. They rebuilt the husk that was HP’s campus networking division and expanded it Continue reading
Are You Ready to Support the “Branch Office of One”?
With a unified and integrated approach to security and networking, digital innovation can proceed uninterrupted, enabling users to effectively and securely operate from a branch office of one, or from just about any location.Tier 1 Carriers Performance Report: May, 2021
The post Tier 1 Carriers Performance Report: May, 2021 appeared first on Noction.