Video: Cisco SD-WAN Policy Design
In the final video in his Cisco SD-WAN webinar, David Penaloza discusses site ID assignments and policy processing order.
A carefully planned site scheme and ordered list of policy entries will save you complications and headaches when deploying the SD-WAN solution.
Video: Cisco SD-WAN Policy Design
In the final video in his Cisco SD-WAN webinar, David Penaloza discusses site ID assignments and policy processing order.
A carefully planned site scheme and ordered list of policy entries will save you complications and headaches when deploying the SD-WAN solution.
IPv6 Buzz 077: Revisiting World IPv6 Launch With Tim Martin
In this week's IPv6 Buzz podcast, Ed, Scott, and Tom discuss the 9th anniversary of World IPv6 Launch (and the 10th anniversary of World IPv6 Day) with Cisco alumnus and IPv6 expert (and IPv6 Buzz's first guest!) Tim Martin.
The post IPv6 Buzz 077: Revisiting World IPv6 Launch With Tim Martin appeared first on Packet Pushers.
IPv6 Buzz 077: Revisiting World IPv6 Launch With Tim Martin
In this week's IPv6 Buzz podcast, Ed, Scott, and Tom discuss the 9th anniversary of World IPv6 Launch (and the 10th anniversary of World IPv6 Day) with Cisco alumnus and IPv6 expert (and IPv6 Buzz's first guest!) Tim Martin.Spotlight on the Kenya Education Network, an Africa Peering Community Champion

The Kenya Education Network (KENET) supports communities that build Internet infrastructure in Kenya. For nearly a decade, KENET has been working with the Internet Society to grow capacity of higher education campuses, Technical and Vocational Education and Training (TVET) institutions, and young engineers. They peer at the Kenya Internet Exchange Point, and they’ve also been […]
The post Spotlight on the Kenya Education Network, an Africa Peering Community Champion appeared first on Internet Society.
Syria’s exam-related Internet shutdowns
To prevent cheating in exams many countries restrict or even shut down Internet access during critical exam hours. For most of June Syria is having planned Internet shutdowns during critical exam periods. The exam schedule is as follows:
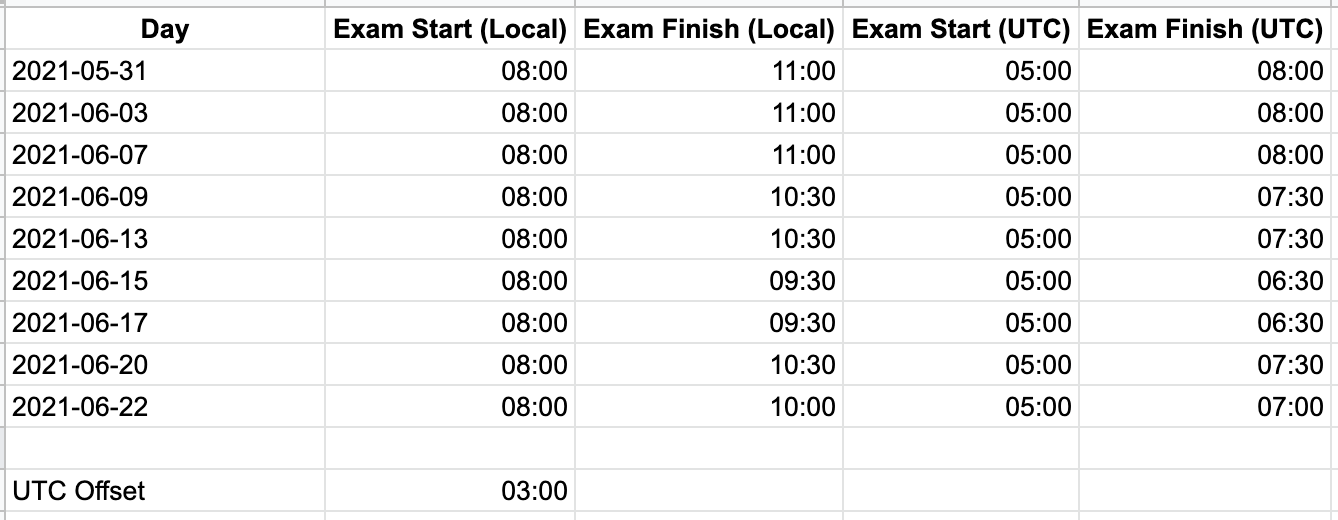
I’m grateful to a Twitter user for the translation from the original Arabic and collating the data.
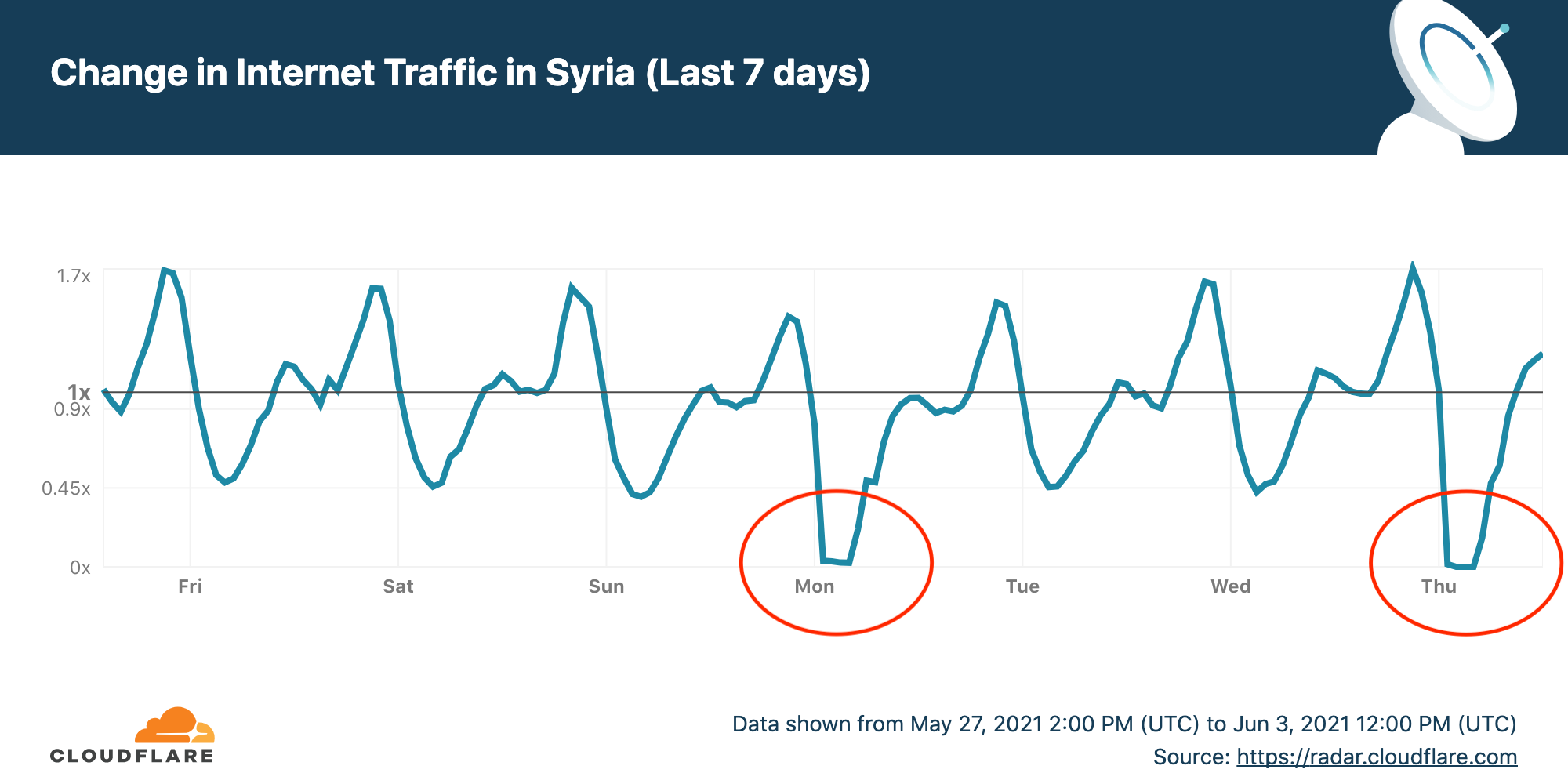
Cloudflare Radar allows anyone to track Internet traffic patterns around the world, and it has country-specific pages. The chart for the last seven days of Internet use in Syria as seen by Cloudflare shows two drops to almost zero corresponding to the first two exams on the schedule.
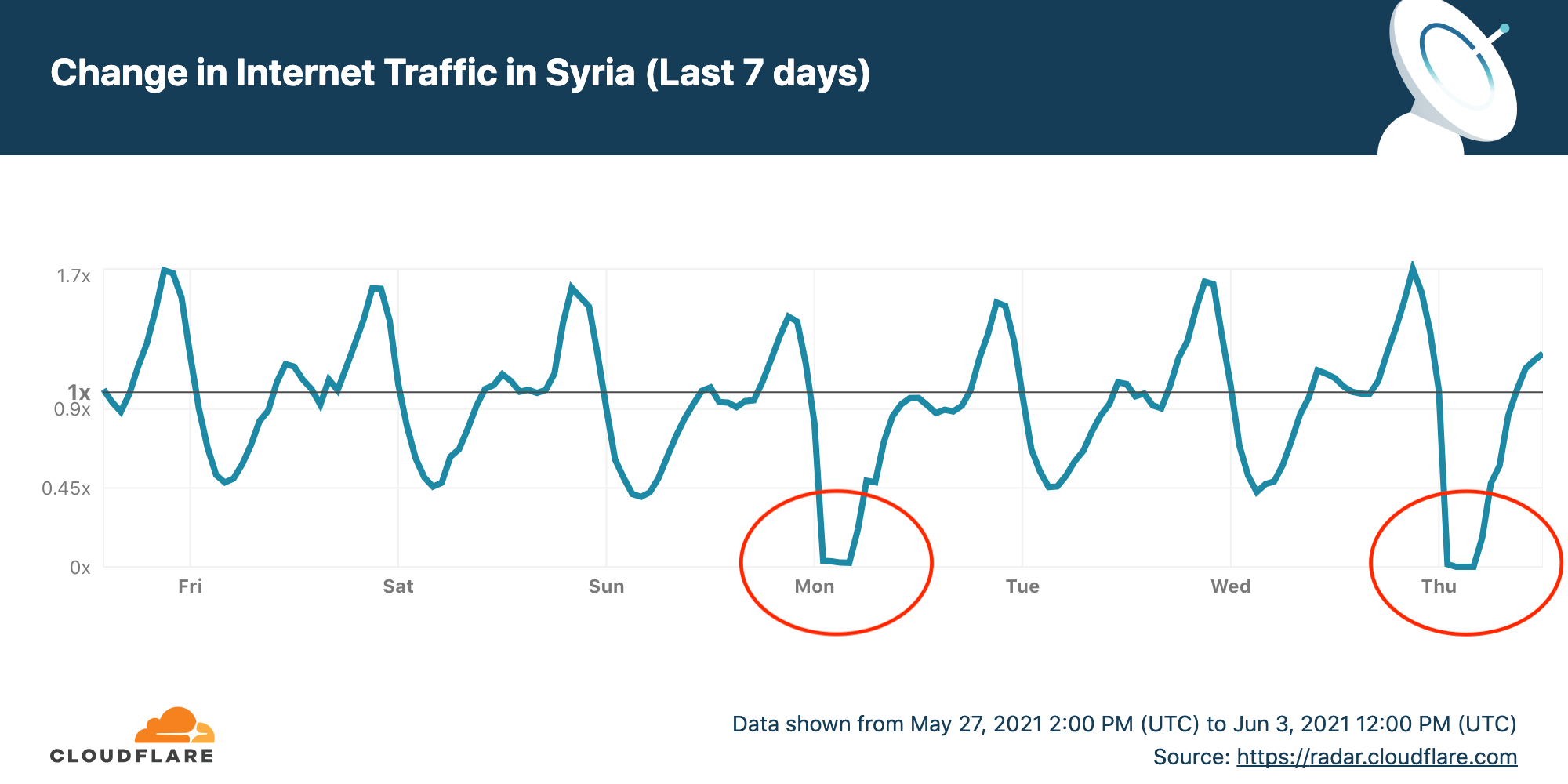
The Internet outage starts at around 0100 UTC (0400 local time) and ends about four and a half hours later at 0530 UTC (0830 UTC). This covers the period before the exams start apparently to prevent any figuring out the answers.
If you want to follow the other outages for the remaining seven exams you can see live data on the Cloudflare Radar Syria page.
Don’t Be Fooled by Agent Tesla’s Football Club Red Herring
Contributors: Subrat Sarkar (T-Rex), Jason Zhang (NSBU TAU)
Agent Tesla is a remote access tool (RAT) that is known for stealing credentials from several applications, including web browsers, VPN clients, and mail and FTP applications. It also supports keylogging, screen grabbing, and other functionality. Since it first came on to the scene in 2014, Agent Tesla has evolved into a fully customizable commercial malware tool, which is readily available on underground markets. Given the huge popularity of the malware, this threat has been thoroughly covered by the threat intelligence community, including our analysis in 2018 [1], our reports on COVID-19 related cyber threats [2] [3], and a recent article describing a surge of infections [4]. More recently, we detected a new wave of Agent Tesla attacks that exhibited some interesting characteristics, such as requesting a connection to top European football club websites.
In this blog post, we first present some of VMware’s NSX Advanced Threat Prevention telemetry and email metadata from the attack. We then provide our analysis detailing the most distinctive aspects of the attack, from the use of well-known European football club websites to key tactics, techniques, and procedures (TTPs).
The Agent Tesla Campaign
Figure 1 shows Continue reading
The Hedge 86: TCPLS
TCP and QUIC are the two primary transport protocols in use on the Internet today—QUIC carries a large part of the HTTP traffic that makes the web work, while TCP carries most everything else that expects reliability. Why can’t we apply the lessons from QUIC to TCP so we can merge these two protocols, unifying Internet transport? TCPLS is just such an attempt at merging the most widely used reliable transport protocols.
Four New IXPs Take off in Central America and the Caribbean

According to the global IXP Database, as of January 2021, of the 630 registered Internet Exchange Points (IXPs), 229 are in Europe, 126 in North America, 140 in Asia-Pacific, 96 in Latin America and the Caribbean (LAC), and 39 in Africa. Although the LAC region is second-last on the list, there has been a strong […]
The post Four New IXPs Take off in Central America and the Caribbean appeared first on Internet Society.
Four Factors Driving 100 Gbps Network Upgrades
As with all generational changes and upgrades, plan carefully, make sure that the monitoring fabric is an integral part of that plan, and put that monitoring in place early to ensure a smooth and secure transition to the new data rate.Musing: Cloud Fashion, Momentem and Resume Buffing
 Gotta have cloud on the resume to get the next job ?
Gotta have cloud on the resume to get the next job ?
Routing Protocols: Use the Best Tool for the Job
When I wrote about my sample katacoda hands-on lab on LinkedIn (mentioning how easy it is to set up an OSPF+BGP network), someone couldn’t resist asking:
I’m still wondering why people use two routing protocols and do not have clean redistribution points or tunnels.
Ignoring for the moment the fact that he missed the point of the blog post (completely), the idea of “using tunnels or redistribution points instead of two routing protocols” hints at the potential applicability of RFC 1925 rule 4.
Routing Protocols: Use the Best Tool for the Job
When I wrote about my sample OSPF+BGP hands-on lab on LinkedIn, someone couldn’t resist asking:
I’m still wondering why people use two routing protocols and do not have clean redistribution points or tunnels.
Ignoring for the moment the fact that he missed the point of the blog post (completely), the idea of “using tunnels or redistribution points instead of two routing protocols” hints at the potential applicability of RFC 1925 rule 4.
Dr. Kanchana Kanchanasut: On Connecting with Communities

Dr. Kanchana Kanchanasut is defined by many firsts. She is well known for being the first Thai to establish email connection to the world. She was among the pioneers to establish Thailand’s research and education network. She registered the .th domain name, conducted Thailand’s first TV White Spaces trial, and started the first open and […]
The post Dr. Kanchana Kanchanasut: On Connecting with Communities appeared first on Internet Society.
Day Two Cloud 100: Get To Know Crossplane: An Infrastructure Control Plane For K8s
Crossplane is an open-source project that plugs into Kubernetes to serve as a control plane that can run across multiple private and public clouds. It allows infrastructure teams to compose infrastructure with all the required policies, permissions, and guardrails, while also providing APIs for developer self-service. Today's Day Two Cloud podcast dives into Crossplane and how it works with maintainer Daniel Mangum.
The post Day Two Cloud 100: Get To Know Crossplane: An Infrastructure Control Plane For K8s appeared first on Packet Pushers.