Day Two Cloud 098: Cloud Centers Of Excellence – Should You Have One?
A fractured cloud strategy causes headaches such as duplicated services, unnecessary costs, poor security controls, and other problems. A cloud center of excellence can reduce the pain by developing and championing best practices, socializing adoption, and addressing inevitable exceptions. Fred Chagnon visits the Day Two Cloud podcast to advocate for building a cloud center of excellence in your org.
The post Day Two Cloud 098: Cloud Centers Of Excellence – Should You Have One? appeared first on Packet Pushers.
Day Two Cloud 098: Cloud Centers Of Excellence – Should You Have One?
A fractured cloud strategy causes headaches such as duplicated services, unnecessary costs, poor security controls, and other problems. A cloud center of excellence can reduce the pain by developing and championing best practices, socializing adoption, and addressing inevitable exceptions. Fred Chagnon visits the Day Two Cloud podcast to advocate for building a cloud center of excellence in your org.Why you don’t want to miss the upcoming Kubernetes Security and Observability Summit
The inaugural Kubernetes Security and Observability Summit will be a free, live, online experience full of Kubernetes-related security and observability content. On June 3, 2021, industry experts will gather under one virtual roof to discuss trends, strategies, and technologies for Kubernetes security and observability, to help you understand and navigate today’s pressing issues in the world of cloud-native applications.
Why attend?
The Summit is a great opportunity to:
- Network with the industry’s best security, DevOps, and site reliability engineer (SRE) teams for cloud-native platforms
- Learn how to secure, observe, and troubleshoot Kubernetes environments
- Explore real-world Kubernetes security and observability use cases presented by experts from industry-leading companies like Amazon, Box, Citi, EY, Mirantis, Morgan Stanley, PayPal, Salesforce, and of course, Tigera
Who should attend?
SREs, platform architects, and DevOps and security teams will all find value in attending the Summit.
- DevOps teams and SREs – Learn how to include security and observability in your CI/CD to enable security, observability, and troubleshooting
- Platform architects – Learn architecture patterns and best practices to secure and troubleshoot cloud-native applications
- Security teams – Learn how to holistically secure your cloud-native applications following today’s best practices
Speakers & sessions
An opening keynote address from Continue reading
The Hedge 84: David Brown and the Root of Trust
Many engineers just assume that secure hardware boot is, in fact, secure. How does this security work, and just how secure is it, though? David Brown joins Tom Ammon, Eyvonne Sharp, and Russ White on this episode of the Hedge to discuss the secure boot loader in some detail. For more information on the secure boot loader and IoT, see David’s presentation at the Open Source Summit.
Back to Basics: Unnumbered IPv4 Interfaces
In the previous blog post in this series, we explored some of the reasons IP uses per-interface (and not per-node) IP addresses. That model worked well when routers had few interfaces and mostly routed between a few LAN segments (often large subnets of a Class A network assigned to an academic institution) and a few WAN uplinks. In those days, the WAN networks were often implemented with non-IP technologies like Frame Relay or ATM (with an occasional pinch of X.25).
The first sign of troubles in paradise probably occurred when someone wanted to use a dial-up modem to connect to a LAN segment. What subnet (and IP address) do you assign to the dial-up connection, and how do you tell the other end what to use? Also, what do you do when you want to have a bank of modems and dozens of people dialing in?
Back to Basics: Unnumbered IPv4 Interfaces
In the previous blog post in this series, we explored some of the reasons IP uses per-interface (and not per-node) IP addresses. That model worked well when routers had few interfaces and mostly routed between a few LAN segments (often large subnets of a Class A network assigned to an academic institution) and a few WAN uplinks. In those days, the WAN networks were frequently implemented with non-IP technologies like Frame Relay or ATM (with an occasional pinch of X.25).
The first sign of troubles in paradise probably occurred when someone wanted to use a dial-up modem to connect to a LAN segment. What subnet (and IP address) do you assign to the dial-up connection, and how do you tell the other end what to use? Also, what do you do when you want to have a bank of modems and dozens of people dialing in?
The Time is Now for Remote Browser Isolation
By preventing the enemy from gaining a foothold in your organization from which they can move laterally within your network, RBI lets you take the high ground and gain control of the cyber battlefield.Redefining Low Latency Switching – Once Again!
Over a decade ago, we entered the high speed switching market with our low latency switches. Our fastest switch then, the 7124, could forward L2/L3 traffic in 500ns, a big improvement over store and forward switches that had 10x higher latency. Combined with Arista EOS®, our products were well received by financial trading and HPC customers.
Redefining Low Latency Switching – Once Again!
Over a decade ago, we entered the high speed switching market with our low latency switches. Our fastest switch then, the 7124, could forward L2/L3 traffic in 500ns, a big improvement over store and forward switches that had 10x higher latency. Combined with Arista EOS®, our products were well received by financial trading and HPC customers.
Multiplayer Doom on Cloudflare Workers


There are halls and corridors in Cloudflare engineering, dangerous places for innocent wanderers, filled with wild project ideas, experiments that we should do, and extremely convincing proponents. A couple of months ago, John Graham-Cumming, our CTO, bumped into me in one of those places and asked: "What if we ported Doom multiplayer to work with our edge network?". He fatally nerd-sniped me.
Aside by John: I nerd-sniped him because I wanted to show how Cloudflare Workers and Durable Objects are a new architectural paradigm where, rather than choosing between two places to write code (the client, the browser or app, and the server, perhaps in a cloud provider availability zone), there’s a third way: put code on the edge.
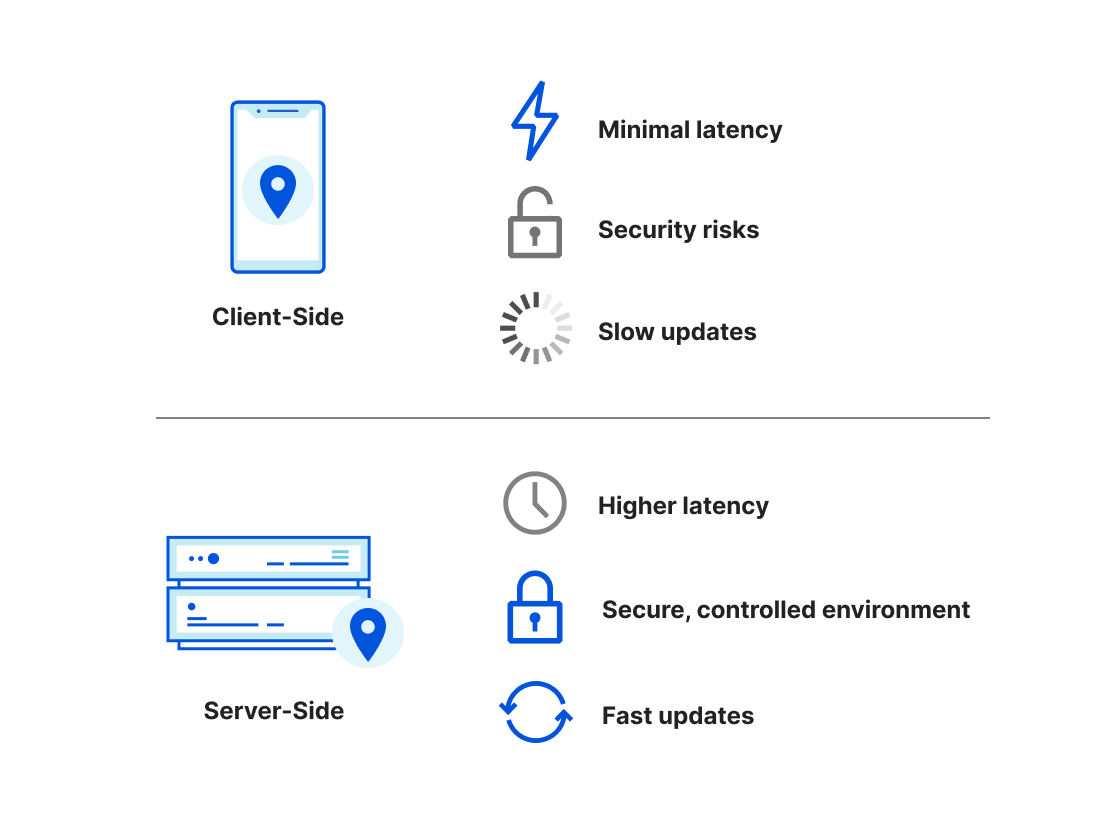
Writing code that runs on a client (such as JavaScript that runs in a browser or a native app on a phone) has advantages. Because the code runs close to the end-user it can be highly interactive, there’s almost no latency since it’s literally running on the device. But client-side code has security problems: it’s literally in the hands of the end-user and thus can be reverse engineered or modified. And client-side code can be slow to update as it Continue reading
MIRA Project to Provide Overview of Internet’s Resiliency in Africa

Internet resilience is the ability of a network to maintain an acceptable level of service at all times. The Internet plays a critical role in society and the COVID-19 pandemic has reinforced the importance of reliable and stable Internet connectivity. However, not all countries have Internet infrastructure that is robust enough to provide an acceptable […]
The post MIRA Project to Provide Overview of Internet’s Resiliency in Africa appeared first on Internet Society.
Born In The Cloud Enterprise Case Study With Tekion – Packet Pushers LiveStream With Alkira (Video 2)
Tekion builds cloud-based applications for the automotive retail industry. The company uses Alkira’s cloud networking product to connect a network of automobile dealerships to an array of cloud-hosted services. In this video, the Packet Pushers’ Ethan Banks talks to Tekion’s Jamie Fox. They discuss how the Alkira platform enables Tekion to leverage multiple clouds with […]
The post Born In The Cloud Enterprise Case Study With Tekion – Packet Pushers LiveStream With Alkira (Video 2) appeared first on Packet Pushers.

