TNO017: Lead People, Manage Machines and Processes
Lead people. Manage machines and processes. That’s the the advice from Bill Hunter, today’s guest on Total Network Operations. Bill shares lessons of resilience and adaptability he learned early in his career, including the power of good habits. Bill and Scott discuss how to identify processes that can be automated and when and where to... Read more »Hedge 260: The State of the DFZ
Trends in the global BGP table–the Default Free Zone (DFZ) table–can tell us a lot about the state of the global Internet. Is the Internet growing? Is IPv6 growing, or are we still in a world of “all things IPv4?” Geoff Huston joins Tom Ammon and Russ White to review the state of the routing table from 2024.
download
Run BGP Across a Firewall
When I asked my readers what they would consider a good use case for EBGP multihop (thanks again to everyone who answered!), many suggested running BGP across a layer-3 firewall (Running BGP across a “transparent” (bump-in-the-wire) firewall is trivial). I turned that suggestion into a lab exercise in which you have to establish an EBGP multihop session across a “firewall” simulated by a Linux host.
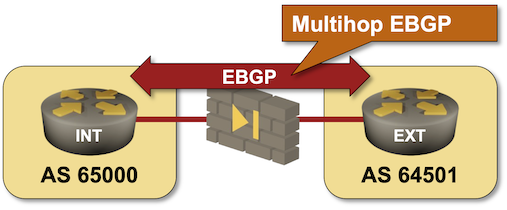
If you haven’t set up your own lab infrastructure, click here to start the lab in your browser using GitHub Codespaces. After starting your codespace, change the directory to basic/e-ebgp-multihop and execute netlab up.
IPB169: 10 Years of the UK IPv6 Council
IPv6 Buzz welcomes back Veronika McKillop, the founder and President of the UK IPv6 Council, to talk about the council’s formation and achievements in the past ten years. We look at IPv6 adoption in the UK and its challenges, and what the future holds for IPv6. Veronika highlights the need for improved IPv6 education in... Read more »N4N014: Spanning Tree Part 2 – Root Bridge, Edge Port, Forwarding and Blocking
Welcome to part 2 of our spanning tree series. We start with a quick review and then discuss root bridges, root ports, designated ports, and forwarding and blocked ports. We explain the impact of topology changes on spanning tree and network performance, and discuss how topology changes and convergence events are communicated. Last but not... Read more »High-Performance Kubernetes Networking with Calico eBPF
Kubernetes has revolutionized cloud-native applications, but networking remains a crucial aspect of ensuring scalability, security, and performance. Default networking approaches, such as iptables-based packet filtering, often introduce performance bottlenecks due to inefficient packet processing and complex rule evaluations. This is where Calico eBPF comes into play, offering a powerful alternative that enhances networking efficiency and security at scale.
Understanding Kubernetes Networking
Kubernetes networking consists of two primary components:
- Physical Network Infrastructure – Connects cloud resources to external networks, ensuring communication between nodes and the broader internet.
- Cluster Network Infrastructure – Manages internal workload communication within the Kubernetes cluster, including service-to-service traffic and pod-to-pod interactions.
Choosing the right data plane is critical for optimal performance. Factors such as cluster size, throughput, and security requirements should guide this choice. Poor networking choices can lead to congestion, excessive latency, and resource starvation.
Data Plane Options in Kubernetes Networking
Networking in Kubernetes is an abstract idea. While Kubernetes lays the foundation, your Container Networking Interface (CNI) is in charge of the actual networking. To better understand networking, we usually divide it into two sections: a control plane and a data plane.
- Control Plane – Control plane is the part that manages how Continue reading
Worth Reading: Using SDN Controller with RSVP/TE
Dmytro Shypovalov published another article well worth reading: why should you use an SDN controller for RSVP-TE. It covers:
- The reasons people might still prefer RSVP-TE over SR-MPLS and the current state of RSVP-TE
- What an SDN controller might bring to the RSVP-TE world
- SR/RSVP coexistence and interworking
Have fun!
Python Getters, Setters and @property Decorator

When I first started working with Python classes, some of the most confusing topics were getters, setters, and @property. There are plenty of tutorials on how to use them, but very few actually explain why do we need them or what problem do they solve. So, I thought I’d write a dedicated post covering what they are and the problems they solve. Let’s get to it.
As always, if you find this post helpful, press the ‘clap’ button. It means a lot to me and helps me know you enjoy this type of content.

Python Classes
Before diving in, let's have a quick look at a Python class. Here’s a simple example of a Person class with two attributes name and age.
class Person:
def __init__(self, name, age):
self.name = name
self.age = age
I'm going to create an instance of the class called p1, passing Continue reading
D2DO265: How Do We Measure Developer Experience?
Developer experience is a hard metric to measure qualitatively. On today’s show, we talk with Kristen Foster-Marks about Developer Experience, or DevEx. We start with the controversial concept of “ghost engineering,” which claims many software engineers do not contribute meaningfully to their work. We delve into the validity of this claim, and discuss the scientific... Read more »Do You Need To Answer That Question?

Photo by Pixabay on Pexels.com
We’ve all been in a situation where we’re listening to a presentation or in a class where someone is sharing knowledge. The presenter or expert finishes a point and stops to take a breath or move on to the next point when you hear a voice.
“What they meant to say was…”
You can already picture the person doing it. I don’t need to describe the kind of person that does this. We all know who it is and, if you’re like me, it drives you crazy. I know it because I’ve found myself being that person several times and it’s something I’m working hard to fix.
Info to Share
People that want to chime in feel like they have important things to share. Maybe they know something deeper about the subject. Perhaps they’ve worked on a technology and have additional information to add to the discussion. They mean well. They’re eager to add to the discussion. They mean well. Most of the time.
What about the other times? Maybe it’s someone that thinks they’re smarter than the presenter. I know I’ve had to deal with that plenty of times. It could be an Continue reading
Goodbye, Cumulus Community Vagrant Boxes
Last Monday, I decided to review and merge the “VXLAN on Cumulus Linux 5.x with NVUE” pull request. I usually run integration tests on the modified code to catch any remaining gremlins, but this time, all the integration tests started failing during the VM creation phase. I was completely weirded out, considering everything worked a week ago.
Fortunately, Vagrant debugging is pretty good1 and I was quickly able to pinpoint the issue (full printout):
Network Automation and AI at NANOG 93
The dominant theme of the presentations this time around at NANOG 93 was the combination of automation of network command and control and the application of Artificial Intelligence tools to this control function. The interest in AI appears to have heightened of late, and while the hype levels are impressive even for an industry that can get totally fixated on hype, the deliverables so far still appear to fall somewhat short.PP050: Understanding–and Protecting Yourself From–the Malware Economy
There’s a robust malware economy with an active market for exploits, brokered access to compromised systems, ransomware, bots-as-a-service, and more. And this malware economy is targeted at you. On today’s Packet Protector we talk with Jake Williams, a security researcher, consultant, and instructor, about the malware economy, how it operates, and the most effective strategies... Read more »HW046: The Flipper Zero: A Swiss Army Knife for Tech Enthusiasts
The Flipper Zero is like a Swiss Army knife for wireless tech enthusiasts. Today’s guest, Jason Beshara, is teaching a course on the Flipper Zero device at WLPC Phoenix 2025. He discusses its functions, including its ability to send and receive a variety of radio signals including Bluetooth, NFC, and sub-gigahertz frequencies. The conversation covers... Read more »Tech Bytes: Nokia Event-Driven Automation: Simple, Reliable Data Center Automation (Sponsored)
Nokia’s Event-Driven Automation, or EDA, is a network automation platform that aims to help network engineers achieve predictable, error-free operations so you can keep up with all the change tickets coming your way while ensuring the data center is reliable and performant. On today’s Tech Bytes podcast, sponsored by Nokia, we’ll talk about how EDA... Read more »NB514: Cisco, Juniper Announce New Switches; SolarWinds Goes Private in $4.4 Billion Buyout
Take a Network Break! We start with some Red Alert vulnerabilities to get your blood pumping, and then dive into networking news. Cisco announces new data center switches with AMD Pensando DPUs that let you deploy security and other services directly on to the switch. Cisco ThousandEyes is previewing Traffic Insights, which correlates flow records... Read more »HS095: The Journey to a Self-Healing Network: Intelligence, Agents, and Complexity (Sponsored)
Can AI and automation create a truly autonomous network, one that’s self-diagnosing and self-healing? Join Vitria CTO and Founder Dale Skeen and industry analyst Charlotte Patrick in this sponsored episode of Heavy Strategy to discuss the challenges–and limitations–of using AI to create autonomous networking. This discussion covers the “intelligence architecture” required to implement automation, and ... Read more »Loopback as a Service
Methods of steering traffic into MPLS and Segment Routing LSP is one of the least standardized and most confusing parts of traffic engineering.
The mess of nexthop resolution
Despite some existing interoperability issues, in general, the MPLS and SR control …
BalticNOG Meeting (September 2025)
Donatas Abraitis asked me to spread the word about the first ever Baltic NOG meeting in the second half of September 2025 (more details)
If you were looking for a nice excuse to visit that part of Europe (it’s been on my wish list for a very long time), this might be a perfect opportunity to do it 😎.
On a tangential topic of fascinating destinations 😉, there’s also ITNOG in Bologna (May 19th-20th, 2025), Autocon in Prague (May 26th-30th, 2025), and SWINOG in Bern (late June 2025).
