New Webinar: Network Automation Concepts
There’s one more thing I feel needs to be done before I go for that coffee break: a webinar focusing on network automation concepts (as opposed to replacing Excel with YAML and Ansible or Becoming a Python Coder). Here’s a rough list of concepts I think should be in there:
- Data models and data stores
- Data model transformations
- Single source of truth
- Abstraction layers
- Idempotency
Elixir Using Mix To Create A Package
Elixir is a functional programming language with a syntax inspired by Ruby that runs on the Erlang virtual machine. In this post I will cover the process of creating an Elixir package with Mix and publishing it to Hex.pm which is the package repository for Elixir progect....Learning Elixir
Why and how i'm learning Elixir.Demystifying Private Cellular for the Enterprise
Understanding some of the key technical differences between new private LTE/5G technology and Wi-Fi is an essential step for enterprises to maximize their investments in both.Juniper to MikroTik – BGP commands
About the Juniper to MikroTik series
In the world of network engineering, learning a new syntax for a NOS can be daunting if you need a specific config quickly. Juniper is a popular option for service providers/data centers and is widely deployed across the world.
This is a continuation of the Rosetta stone for network operating systems series. We’ll be working through several protocols over series of posts to help you quickly move between different environments.
While many commands have almost the exact same information, others are as close as possible. Since there isn’t always an exact match, sometimes you may have to run two or three commands to get the information needed.
Using EVE-NG for testing
We conducted all of this testing utilizing EVE-NG and the topology seen below.
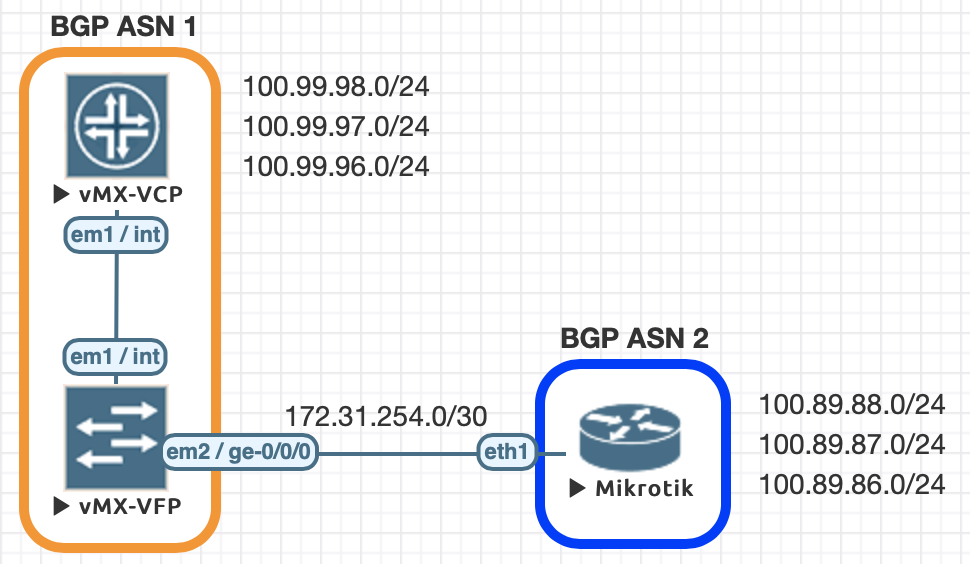
| Juniper Command | MikroTik Command |
|---|---|
| show bgp summary | routing bgp peer print brief |
| show bgp neighbor | routing bgp peer print status |
| show route advertising-protocol bgp 172.31.254.2 | routing bgp advertisements print peer=peer_name |
| show route receive-protocol bgp 172.31.254.2 | ip route print where received-from=peer_name |
| show route protocol bgp | ip route print where bgp=yes |
| clear bgp neighbor 172.31.254.2 soft-inbound | Continue reading |
Networking and Infrastructure News Roundup: January 22 Edition
In the news this week: A solution to help manage multiple Kubernetes environments, a new storage-as-a-service that tackles regulatory-safe, long-term retention of data, and more.Learning Elixir
Elixir is a dynamic functional programming language that runs on the Erlang virtual machine. In this post I will outline my reasoning for learning Elixir and document the resources used in the process. I will update the Books, Videos and Blogs section as I move through the learning...Worth Reading: Cloud Complexity Lies
Anyone who spent some time reading cloud providers' documentation instead of watching slide decks or vendor keynotes knows that setting up infrastructure in a public cloud is not much simpler than doing it on-premises. You will outsource hardware management (installations, upgrades, replacements…) and might deal with an orchestration system provisioning services instead of configuring individual devices, but you still have to make the same decisions, and take the same set of responsibilities.
Obviously that doesn’t look good in a vendor slide deck, so don’t expect them to tell you the gory details (and when they start talking about the power of declarative API you know you have a winner)… but every now and then someone decides to point out the state of emperor’s clothes, this time Gerben Wierda in his The many lies about reducing complexity part 2: Cloud.
For public cloud networking details, check out our cloud webinars and online course.
Worth Reading: Cloud Complexity Lies
Anyone who spent some time reading cloud providers’ documentation instead of watching slide decks or vendor keynotes knows that setting up infrastructure in a public cloud is not much simpler than doing it on-premises. You will outsource hardware management (installations, upgrades, replacements…) and might deal with an orchestration system provisioning services instead of configuring individual devices, but you still have to make the same decisions, and take the same set of responsibilities.
Obviously that doesn’t look good in a vendor slide deck, so don’t expect them to tell you the gory details (and when they start talking about the power of declarative API you know you have a winner)… but every now and then someone decides to point out the state of emperor’s clothes, this time Gerben Wierda in his The many lies about reducing complexity part 2: Cloud.
For public cloud networking details, check out our cloud webinars and online course.
VMware After Gelsinger: Integrating Fiefdoms For A Post-Hypervisor World
VMware's next CEO has two tasks: to construct a narrative about VMware's role and value as a company in a post-hypervisor world, and to integrate its various fiefdoms into a cohesive set of products that can provide greater utility when used together than when used individually.
The post VMware After Gelsinger: Integrating Fiefdoms For A Post-Hypervisor World appeared first on Packet Pushers.
Podcast: IPv6 in the Cloud
In December 2020 Ed Horley invited me to a chat about IPv6 in the public cloud. While I usually don’t want to think about a protocol that’s old enough to buy its own beer in US, we nonetheless had interesting discussions (including the need for frequent RA messages in AWS VPC).
Podcast: IPv6 in the Cloud
In December 2020 Ed Horley invited me to a chat about IPv6 in the public cloud. While I usually don’t want to think about a protocol that’s old enough to buy its own beer in US, we nonetheless had interesting discussions (including the need for frequent RA messages in AWS VPC).
Heavy Networking 558: No Time For Hardware – The Case For NFV
Network Functions Virtualization (NFV) transforms routers, load balancers, firewalls and other network devices into virtual instances that can be service-chained, spun up and down as needed, and are cloud-friendly. But if you're a hardware hugger or have been been burned by virtualization in the past, should you avoid NFV? Today's Heavy Networking guests want to change your mind. The Packet Pushers speak with Michael Pfeiffer, a Cloud Networking Architect for a VAR; and Brad Gregory, Senior Product Manager at Equinix.
The post Heavy Networking 558: No Time For Hardware – The Case For NFV appeared first on Packet Pushers.
Heavy Networking 558: No Time For Hardware – The Case For NFV
Network Functions Virtualization (NFV) transforms routers, load balancers, firewalls and other network devices into virtual instances that can be service-chained, spun up and down as needed, and are cloud-friendly. But if you're a hardware hugger or have been been burned by virtualization in the past, should you avoid NFV? Today's Heavy Networking guests want to change your mind. The Packet Pushers speak with Michael Pfeiffer, a Cloud Networking Architect for a VAR; and Brad Gregory, Senior Product Manager at Equinix.Planning For The Worst Case You Can’t Think Of

Remember that Slack outage earlier this month? The one that happened when we all got back from vacation and tried to jump on to share cat memes and emojis? We all chalked it up to gremlins and went on going through our pile of email until it came back up. The post-mortem came out yesterday and there were two things that were interesting to me. Both of them have implications on reliability planning and how we handle the worst-case scenarios we come up with.
It’s Out of Our Hands
The first thing that came up in the report was that the specific cause for the outage came from an AWS Transit Gateway not being able to scale fast enough to handle the demand spike that came when we all went back to work on the morning of January 4th. What, the cloud can’t scale?
The cloud is practically limitless when it comes to resources. We can create instances with massive CPU resources or storage allocations or even networking pipelines. However, we can’t create them instantly. No matter how much we need it takes time to do the basic provisioning to get it up and running. It’s the old story of Continue reading
Stable: GNS3 2.2.17 + VMware Fusion 12.1.0 + macOS 11.1 (Build 20C69)
Even with minor caveats, I seem to be in a better place with macOS 11.1 Big Sur versus macOS 10.15.7 Catalina. Big Sur is not a flawless experience for me yet, but I have hope it will become so as software makers have time to adjust to all of Apple's changes. And I'll take being able to run GNS3 labs without kernel panics as a big win.
The post Stable: GNS3 2.2.17 + VMware Fusion 12.1.0 + macOS 11.1 (Build 20C69) appeared first on Packet Pushers.
Weekend Reads 012221
or perhaps the friday fifteen …
Defining and measuring programmer productivity is something of a great white whale in the software industry. It’s the basis of enormous investment, the value proposition of numerous startups, and one of the most difficult parts of an engineering manager or Continue reading