Rails 6 Forms With Bootstrap 5 Styling
How to build forms in Rails 6 and style them with Bootstrap 5.Olivier Bonaventure | MPTCP: The coolest protocol you’re already using – but didn’t know
Derick and Brandon chat with Olivier Bonaventure, Professor at Université catholique de Louvain (UCL) and co-founder at Tessares, about the evolution of Multipath TCP, a protocol that is changing the way we experience the Internet.
Going Virtual with Community Networks Voices in the Asia-Pacific: CNX APAC 2020
Each community network deployment has its own characteristics – ranging from the physical terrain to environmental conditions to local and cultural contexts. Having been involved in some 150 deployments, I can safely say no two are the same.
We helped establish CNX APAC in 2017 as a means to better understand the role, relevance, and evolution of community networks (CNs). It was designed to explore the different characteristics that make up CNs, their local context, the challenges they face, and the opportunities they create. It’s an event in the spirit of community, where community network practitioners come to exchange knowledge, share ideas, inspire others, and be inspired themselves.
For the past three years, we have typically held these as physical events located around some of our community networks deployments in the region. This allowed participants to get hands on with a working CN. The events were multi-dimensional in nature with a conference and knowledge-sharing session, coupled with training and technology demonstrations.
“To make community networks sustainable in the long run, the first thing is, the community has to own it, and the community needs to own it.”
— Mahabir Pun, Nepal
The impact of the global pandemic meant that Continue reading
Holiday Season Update from Lisbon


It's the end of the year, so we thought it would be a great time to give you an update on how we're doing and what we're planning for 2021. If you're reading this, you know we like to share everything we do at Cloudflare, including how the organization is evolving.
In July, John Graham-Cumming wrote a blog post entitled Cloudflare's first year in Lisbon. and showed how we went from an announcement, just a few months before, to an entirely bootstrapped and fully functional office. At the time, despite a ramping pandemic, the team was already hard at work doing a fantastic job scaling up and solidifying our presence here.
A few weeks later, in August, I proudly joined the team.
The first weeks
Cloudflare is, by any standard, a big company. There's a lot you need to learn, many people you need to get to know first, and a lot of setup steps you need to get through before you're in a position to do actual real productive work.
Joining the company during COVID was challenging. I felt just as excited as I was scared. We were (and still are) fully working from home, I didn't have a Continue reading
Merry Christmas and Happy New Year 2021
Dear friend,
This year was unbelievable. But despite all the horrible things related to COVID19 and lockdown, you and we are still alive. Moreover, the networking and automation industry is growing. It means, we are together on the right side, but we need continuously sharp existing and develop new skills.
We sincerely thank you for your interest in our projects, blogs and trainings. For your questions, comments and suggestions. It means for us a lot.
We wish you Merry Christmas and Happy New Year! Stay healthy and safe during the holiday times and the whole new year.
All the best,
Team Karneliuk.com
We’re Done for This Year
As always, it’s time to shut down our virtual office and disappear until early January… unless of course you have an urgent support problem. Any paperwork ideas your purchasing department might have will have to wait until 2021.
I hope you’ll be able to disconnect from the crazy pace of networking world, forget all the unicorns and rainbows (and broccoli forest of despair), and focus on your loved ones – they need you more than the dusty router sitting in a remote office. We would also like to wish you all the best in 2021!
We’re Done for This Year
As always, it’s time to shut down our virtual office and disappear until early January… unless of course you have an urgent support problem. Any paperwork ideas your purchasing department might have will have to wait until 2021.
I hope you’ll be able to disconnect from the crazy pace of networking world, forget all the unicorns and rainbows (and broccoli forest of despair), and focus on your loved ones – they need you more than the dusty router sitting in a remote office. We would also like to wish you all the best in 2021!
Beaming the Wave to Make 5G a Reality
Meeting the infrastructure demands of a widespread, reliable 5G network requires adopting a broad approach to densification.Rails 6 Forms With Bootstrap 5 Styling
Forms allow you to receive data from your users via the webapp and store that information in your database and/or send it off for external processing to something like an API. In this post I will go over the process of using forms in rails 6 and styling them with the Bootstrap 5 CSS ...JNCIE-DC lab in EVE-NG
As explained in my previous post on my home servers, I have a bare metal system deployed with EVE-NG Pro installed. As I’m (slowly) preparing for the JNCIE-DC certification I wanted to share the topology that I’m using. As the hardware required to study for the JNCIE-DC is quite significant, it makes a lot of […]
The post JNCIE-DC lab in EVE-NG first appeared on Rick Mur.Chapter Members Pool Ideas to Inspire New Use Case on Content Filtering

Earlier this year, chapter members from around the world were asked to assist a government minister with an important project. The minister had been tasked with giving an emergency briefing on content filtering and needed the chapter members to help assess an important question. Would the critical properties of the Internet Way of Networking – the foundation that makes the Internet work for everyone – be impacted by the minister’s new policy on content filtering?
While some of the Chapter members held experience in Internet policy, others were relative novices. But as they explored the multiple dimensions and implications of different filtering and blocking techniques, they had a new, powerful tool in their arsenal: the Internet Impact Assessment Toolkit.
The government minister was fictitious, part of a mock scenario created by the Internet Society in collaboration with chapter members participating in chapter workshops. It was a powerful demonstration of how the Internet Impact Assessment Toolkit can evaluate the real-world impact of proposed Internet policy.
During the Latin American Chapter Workshop, about 140 people joined the session dedicated to the discussion of content filtering. Once the mock case was presented, participants were invited to explore the various angles of different filtering and Continue reading
Integrating Cloudflare Gateway and Access
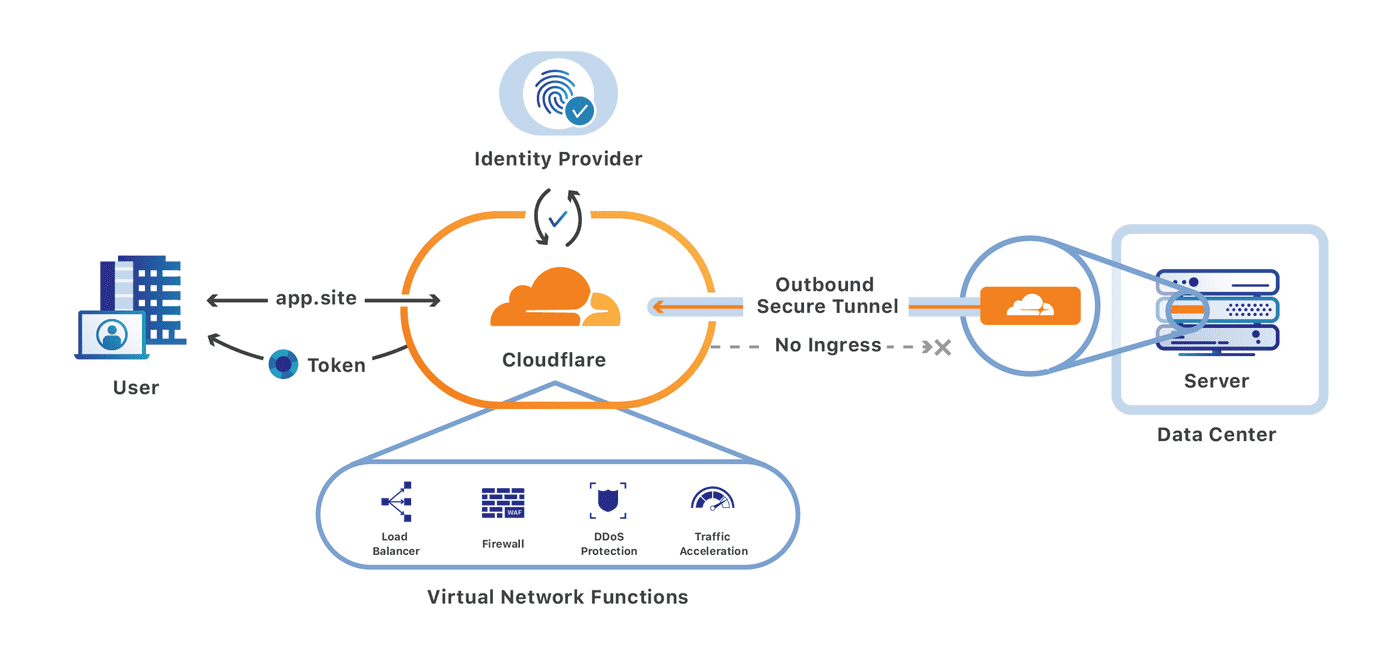
We’re excited to announce that you can now set up your Access policies to require that all user traffic to your application is filtered by Cloudflare Gateway. This ensures that all of the traffic to your self-hosted and SaaS applications is secured and centrally logged. You can also use this integration to build rules that determine which users can connect to certain parts of your SaaS applications, even if the application does not support those rules on its own.
Stop threats from returning to your applications and data
We built Cloudflare Access as an internal project to replace our own VPN. Unlike a traditional private network, Access follows a Zero Trust model. Cloudflare’s edge checks every request to protected resources for identity and other signals like device posture (i.e., information about a user’s machine, like Operating system version, if antivirus is running, etc.).
By deploying Cloudflare Access, our security and IT teams could build granular rules for each application and log every request and event. Cloudflare’s network accelerated how users connected. We launched Access as a product for our customers in 2018 to share those improvements with teams of any size.
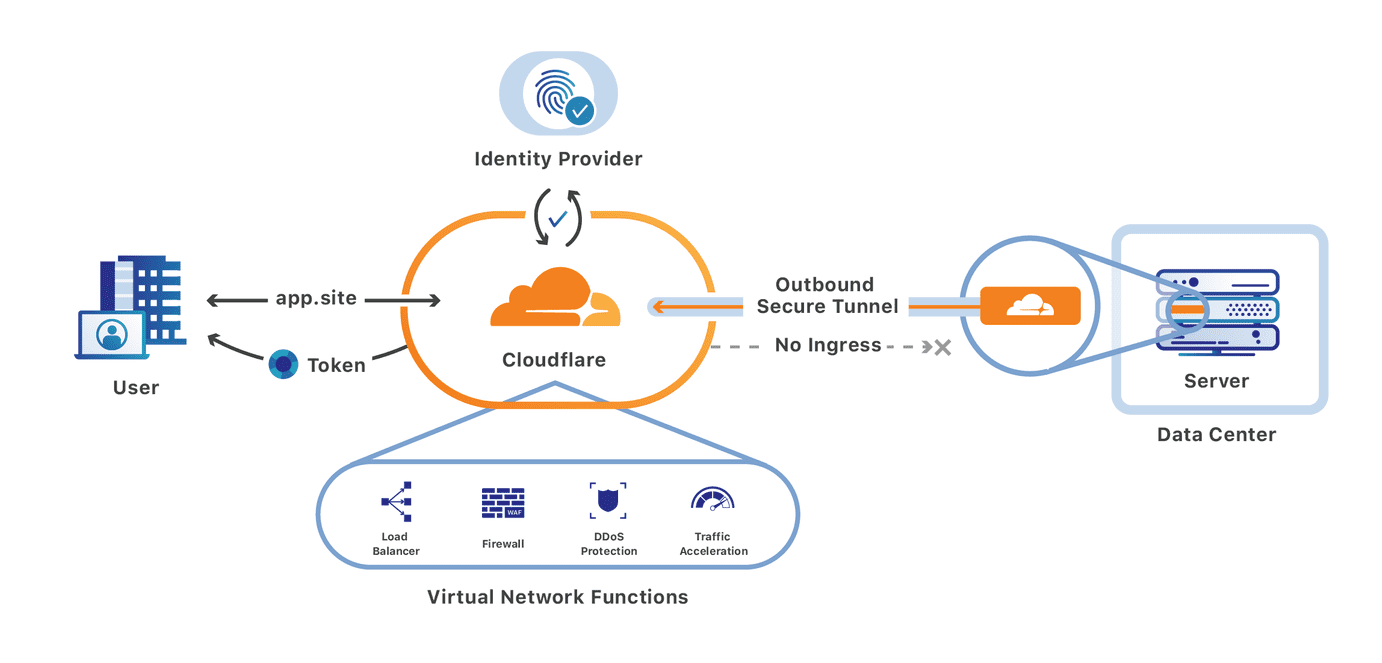
Over the last two years, we Continue reading
2020: Year in Review
The post 2020: Year in Review appeared first on Noction.
VMware NSX-T Install Tips & Tricks
Intro It’s a short list of things that you should probably know when installing VMware NSX-T. Of course, installing NSX-T should be done by following the official documentation. This here is just a few additional points that could help. It’s for your peace of mind afterward. This is an article from the VMware from Scratch series NSX Manager is a Cluster of three VMs You should end up having three NSX-Manager VMs in a cluster when you finish NSX-T installation. The first one will be deployed via .ovf file from vCenter, the other two direct from first NSX Manager GUI
The post VMware NSX-T Install Tips & Tricks appeared first on How Does Internet Work.
What Exactly Happens after a Link Failure?
Imagine the following network running OSPF as the routing protocol. PE1–P1–PE2 is the primary path and PE1–P2–PE2 is the backup path. What happens on PE1 when the PE1–P1 link fails? What happens on PE2?
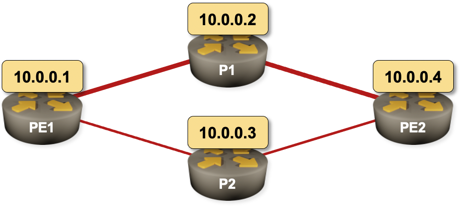
Sample 4-router network with a primary and a backup path
The second question is much easier to answer, and the answer is totally unambiguous as it only involves OSPF: