The Hedge Podcast #50: The Challenge of Growing People

Many network engineers complain about their companies not giving them opportunities—but how many think about helping the company grow in a way that allows them to have the opportunities they desire? Scott Morris, aka “evil ccie,” joins Tom and Russ on this episode of the Hedge to talk about the challenges of certifications, growing people, and people learning how to grow in a way what improves the business. Sometimes growing means creating opportunities rather than just waiting for them to knock.
The Internet Society Welcomes the Comoros Chapter

We are excited to announce the new Internet Society Comoros Chapter! ISOC Comoros officially launched in July in front of an in-person and online audience at the Retaj Hotel.
Journalists joined several distinguished guests, including:
- Dawit Bekele, Internet Society’s Regional Vice-President for Africa
- Mohamed Said Abdallah Mchangama, President of the Federation of Comorian Consumers (FCC)
- Amina Abdallah, Coordinator of the World Bank’s Phase 4 of the Regional Communications Infrastructure Program for Africa (RCIP-4)
- Hamidou Mhoma, President of the Comorian ICT Association
- Chamsoudine Soudjay, Secretary General of the Comorian ICT Association
- Amroine Mouzaoui, Executive Secretary of the Comorian Movement for Entrepreneurs
- Raymane Ali Matoir, Director of Human Resources of Telma Comores
- Youssouf Abdoulmadjid, Chief Operating Officer of Comor’Lab
- Moussa Abdallah Moumine, Coordinator of the General Inspectorate of National Education
Since the country’s very first connection to the Internet in July 1998, the Internet industry has continued to evolve, along with telecommunications. The country is beginning to benefit from the rise in competition in the ICT sector, and as such the establishment of ISOC Comoros brings an added dimension to the development, promotion, and use of the Internet for the greater good of the entire country.
The Internet is for everyone and Continue reading
Example: Securing AWS Deployment
Nadeem Lughmani created an excellent solution for the securing your cloud deployment hands-on exercise in our public cloud online course. His Terraform-based solution includes:
- Security groups to restrict access to web server and SSH bastion host;
- An IAM policy and associated user that has read-only access to EC2 and VPC resources (used for monitoring)
- An IAM policy that has full access to as single S3 bucket (used to modify static content hosted on S3)
- An IAM role for AWS CloudWatch logs
- Logging SSH events from the SSH bastion host into CloudWatch logs.
Mitigating the Risks of Instance Metadata in AWS EKS
Compromising a pod in a Kubernetes cluster can have disastrous consequences on resources in an AWS Elastic Kubernetes Service (EKS) account if access to the Instance Metadata service is not explicitly blocked. The Instance Metadata service is an AWS API listening on a link-local IP address. Only accessible from EC2 instances, it enables the retrieval of metadata that is used to configure or manage an instance. Although you can only access instance metadata and user data from within the instance itself, the data is not protected by authentication or cryptographic methods.
A recent blog described a scenario where an attacker compromised a pod in an EKS cluster by exploiting a vulnerability in the web application it was running, thus enabling the attacker to enumerate resources in the cluster and in the associated AWS account. This scenario was simulated by running a pod and attaching to a shell inside it.
By querying the Instance Metadata service from the compromised pod, the attacker was able to access the service and retrieve temporary credentials for the identity and access management (IAM) role assigned to the EC2 instances acting as Kubernetes worker nodes. At that point, the attacker was able to pursue multiple exploits, Continue reading
History of Networking: Networking at Google with Richard Hay
Google fascinates network engineers because of the sheer scale of their operations, and their obvious influence over the way networks are built and operated. In this episode of the History of Networking, Richard Hay joins Donald Sharp and Russ White to talk about some past designs and stories of failure and success in one of the world’s largest operating networks.
Two clicks to add region-based Zero Trust compliance
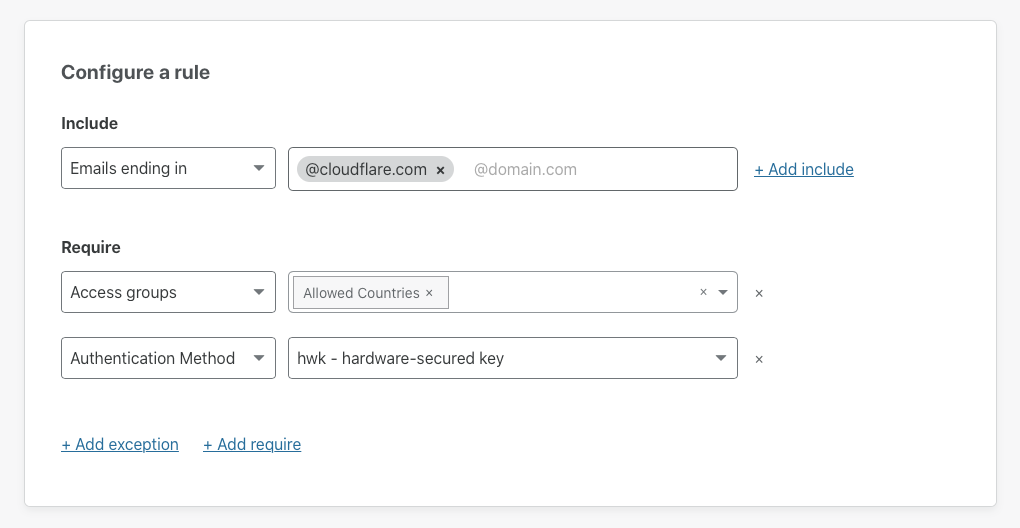
Your team members are probably not just working from home - they may be working from different regions or countries. The flexibility of remote work gives employees a chance to work from the towns where they grew up or countries they always wanted to visit. However, that distribution also presents compliance challenges.
Depending on your industry, keeping data inside of certain regions can be a compliance or regulatory requirement. You might require employees to connect from certain countries or exclude entire countries altogether from your corporate systems.
When we worked in physical offices, keeping data inside of a country was easy. All of your users connecting to an application from that office were, of course, in that country. Remote work changed that and teams had to scramble to find a way to keep people productive from anywhere, which often led to sacrifices in terms of compliance. Starting today, you can make geography-based compliance easy again in Cloudflare Access with just two clicks.
You can now build rules that require employees to connect from certain countries. You can also add rules that block team members from connecting from other countries. This feature works with any identity provider configured and requires no Continue reading
Docker Services 101
Last week I published an overview of how complex (networking-wise) Docker Swarm services can get. This time let’s focus on something that should have been way simpler: running container-based services on a single Linux host.
In the first part of this article I’m focusing on the basics, including exposed ports, and published ports. The behind-the-scenes details are coming in a week or so; in the meantime you can enjoy (most of them) in the Docker Networking Deep Dive webinar.
LXC as Virtual Service Container on IOS XE
In the last tutorial, we have discussed Cisco open service container based on Kernel Virtual Machine (KVM). Virtual machines include the application, binaries and libraries along with entire guest OS. As a result, we can run any guest OS supported by KVM hypervisor. Containers, however share the same kernel with; each container still acts as […]Continue reading...
Pushing to Multiple Git Remotes
How to push to multiple git repos across different git providers.Build DSCP to ToS conversion table with Python
Contents
- Introduction
- Problem description.
- Discovery and research phase
- Plan of action
- Writing tests
- Closing thoughts
- References
- GitHub repository with code for this post
Introduction
In this post we're going to write Python program that generates DSCP to ToS conversion table while avoiding hardcoding values as much as possible. We will then save the final table to csv file with pre-defined column headers.
I got the idea for this blog article from the tweet posted the other day by Nick Russo. I thought it is an interesting problem to tackle as similar ones pop up all the time during early stages of Network Automation journey. What makes this challenge great is that it requires us to carry out tasks that apply to writing larger programs.
- We need to understand the problem and possibly do some research.
- We have to come up with plan of action.
- We need to break down larger tasks into smaller pieces.
- We need to implement all Continue reading
The Digital Divide May Be News, But It’s Not New

This opinion piece was originally published in Morning Consult.
Low-income Americans; Black, Hispanic and Native Americans; the elderly; Americans with a high school education or less; and rural Americans are much more likely to be on the wrong side of the digital divide. Ours remains a nation where too many people, often our most vulnerable citizens, are unconnected or under-connected.
The digital divide may have made the news during the COVID-19 pandemic, but it isn’t new.
For much of the past quarter-century, Washington policymakers have ignored the digital divide. In more recent years, some public officials, for political reasons, have identified the digital divide as primarily a rural issue, noting that approximately 5 million rural American households can’t access broadband networks. In reality, the number of rural households that can’t access broadband is dwarfed by the roughly 20 million American households that can’t afford Internet access, and that number almost certainly has increased as a result of the pandemic.
Today, Washington finally seems willing to engage in addressing the digital divide. What we need now are not the patchwork solutions of the past, but a thoughtful, fully funded, comprehensive effort to ensure broadband connectivity for all Americans.
My colleagues and Continue reading
Tech Bytes: UCT’s Global WAN Performance Sparkles With Silver Peak SD-WAN (Sponsored)
Today's Tech Bytes is a conversation with Silver Peak customer UCT about how it adopted SD-WAN to boost performance and minimize the downtime of critical business applications. With 21 sites in 8 countries, the company relies on its WAN to support in-house applications and manage the logistics of its global operations. Our guest is James Mccoll, Network Engineer at UCT.
The post Tech Bytes: UCT’s Global WAN Performance Sparkles With Silver Peak SD-WAN (Sponsored) appeared first on Packet Pushers.