Heavy Networking 522: How CIOs Prioritize Security – Cisco’s CIO Perspectives 2020 Survey (Sponsored)
Today's Heavy Networking, sponsored by Cisco, examines results and insights from 1,300 global CIOs in Cisco's CIO Perspectives 2020 survey. Guest Jo Peterson, VP of Cloud & Security for Clarify360, shares highlights and learnings on CIO priorities, security, digital transformation, empowering teams, and more.Strengthening Communities, Improving Lives and Livelihoods: The Internet Society Foundation Launches SCILLS

When people connect to the Internet, they can change the world for the better. And so many people have done just that, using this transformative technology to make strides in education, economic opportunity, and health outcomes. But Internet access is only part of the equation. There’s now a different kind of divide: the gap between those who have the knowledge and skills to use the Internet to empower themselves and their communities – and those who don’t.
To address this gap, the Internet Society Foundation is launching SCILLS: Strengthening Communities, Improving Lives and Livelihoods. The program aims to expand economic growth, improve health outcomes, and increase educational opportunities – by supporting communities to more knowledgeably and skillfully use the Internet.
Are you working to close this gap? The Internet Society Foundation wants to hear from you!
In its pilot year, the program is open to eligible organizations in Bangladesh, Colombia, and Senegal, with expansion to additional countries planned in coming years. It provides grants of up to $150,000 USD for projects lasting up to 24 months. Applications are open between 9 June and 3 July, and grantees will be announced in early September.
The Internet is for everyone – a critical lifeline that can Continue reading
UtahFS: Encrypted File Storage
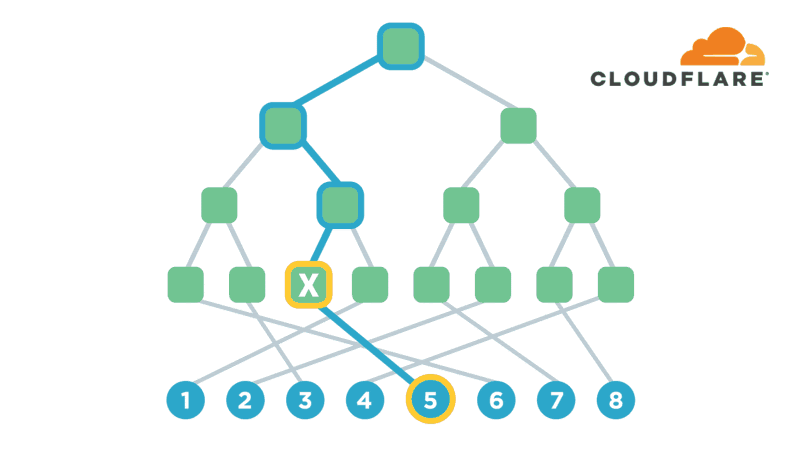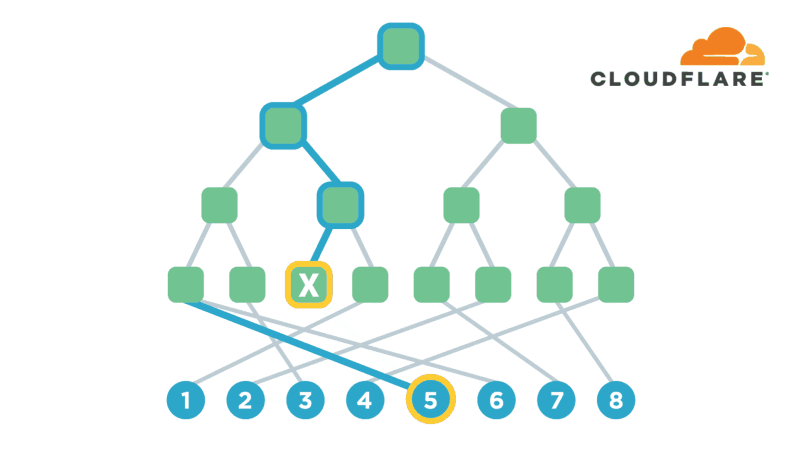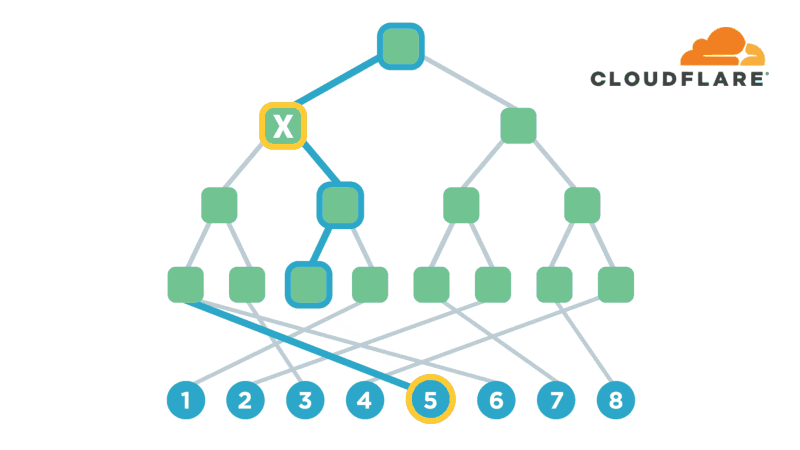
Encryption is one of the most powerful technologies that everyone uses on a daily basis without realizing it. Transport-layer encryption, which protects data as it’s sent across the Internet to its intended destination, is now ubiquitous because it’s a fundamental tool for creating a trustworthy Internet. Disk encryption, which protects data while it’s sitting idly on your phone or laptop’s hard drive, is also becoming ubiquitous because it prevents anybody who steals your device from also being able to see what’s on your desktop or read your email.
The next improvement on this technology that’s starting to gain popularity is end-to-end encryption, which refers to a system where only the end-users are able to access their data -- not any intermediate service providers. Some of the most popular examples of this type of encryption are chat apps like WhatsApp and Signal. End-to-end encryption significantly reduces the likelihood of a user’s data being maliciously stolen from, or otherwise mishandled by a service provider. This is because even if the service provider loses the data, nobody will have the keys to decrypt it!
Several months ago, I realized that I had a lot of sensitive files on my computer (my diary, if Continue reading
Cloud Networking Architectures
There’s one thing no cloud vendor ever managed to change: virtual machines running on top of cloud infrastructure expect to have Ethernet interfaces.
It doesn’t matter if the virtual Ethernet Network Interface Cards (NICs) are implemented with software emulation of actual hardware (VMware emulated the ancient Novell NE1000 NIC) or with paravirtual drivers - the virtual machines expect to send and receive Ethernet frames. What happens beyond the Ethernet NIC depends on the cloud implementation details.
Real-Time Monitoring Critical to Service Assurance
As service providers adopt virtualization and SDN capabilities, they are being held back by...
Daily Roundup: AT&T First to Activate DSS
AT&T activated the first US dynamic spectrum sharing deployment; Ericsson burned cash on China...
ShortestPathFirst Now Has a New Twitter Account – @ShortestFirst
Thrilled to announce that ShortestPathFirst now has a Twitter account so that we can share all the exciting developments in this new venture. We’re excited to share our passion for cutting-edge technology and solutions with customers and colleagues throughout the IT industry.Cumulus content roundup: May 2020
May means more content! There was a very exciting announcement from us this month, and if you missed it don’t worry, you can read all about it below. In addition, we were keeping very busy with fresh podcast episodes, informative blog posts and much more. Ready to dive into all things open networking? Get comfortable and let’s dive in.
From Cumulus Networks
UCMP: Augmenting L3 only designs: So what makes a purely L3 design so aspirational? Can a UCMP increase efficiency? Read this blog post by Rama Dharba as he addresses these questions and more. He delves into the challenges surrounding this type of design, possible solutions and a recent augmentation in Cumulus Linux 4.1 that increases the design’s ability for flexibility.
Kernel of Truth season 3 episode 6: Building modern campus networks: Let’s talk about all things modern campus networks. In this new Kernel of Truth episode, Brain O’Sullivan, Roopa Prabhu, Eric Pulvino and David Marshall dive into trends, technologies, architecture and much more. Grab your headphones and get ready to hear first-hand experiences from building these networks as well as tips and tricks learned along the way.
Build an OpenStack/ Ceph cluster with Cumulus Networks in Continue reading
Quit Manspreading. Tech Needs Women More Than Ever
Companies can kiss their dream of a future dominated by smart machines goodbye unless they start...
Is QUIC really Quicker?
QUIC is a relatively new data transport protocol developed by Google, and currently in line to become the default transport for the upcoming HTTP standard. Because of this, it behooves every network engineer to understand a little about this protocol, how it operates, and what impact it will have on the network. We did record a History of Networking episode on QUIC, if you want some background.
In a recent Communications of the ACM article, a group of researchers (Kakhi et al.) used a modified implementation of QUIC to measure its performance under different network conditions, directly comparing it to TCPs performance under the same conditions. Since the current implementations of QUIC use the same congestion control as TCP—Cubic—the only differences in performance should be code tuning in estimating the round-trip timer (RTT) for congestion control, QUIC’s ability to form a session in a single RTT, and QUIC’s ability to carry multiple streams in a single connection. The researchers asked two questions in this paper: how does QUIC interact with TCP flows on the same network, and does UIC perform better than TCP in all situations, or only some?
To answer the first question, the authors tried running QUIC Continue reading
Ericsson Burns Cash to Gain China 5G Deals
The vendor's business in China has grown as of late, having inked contracts with the country’s...
Chef Dishes Compliance, Desktop Automation
The updates follow a move by Chef last year to revamp its development, platforms, and go-to-market...
Large flow marking using BGP Flowspec
Elephant Detection in Virtual Switches & Mitigation in Hardware discusses a VMware and Cumulus demonstration, Elephants and Mice, in which the virtual switch on a host detects and marks large "Elephant" flows and the hardware switch enforces priority queueing to prevent Elephant flows from adversely affecting latency of small "Mice" flows.SDN and WAN optimization describes a presentation by Amin Vahdat describing Google's SDN based wide area network traffic engineering solution in which traffic prioritization allows Google to reduce costs by fully utilizing WAN bandwidth.
Deconstructing Datacenter Packet Transport describes how priority marking of packets associated with large flows can improve completion times for flows crossing the data center fabric. Simulation results presented in the paper show that prioritization of short flows over large flows can significantly improve throughput (reducing flow completion times by a factor of 5 or more at high loads).
This article demonstrates a self contained real-time Elephant flow marking solution that leverages the real-time visibility and control features available using commodity switch hardware.
The diagram shows the elements of the solution. An instance of the sFlow-RT real-time analytics engine receives streaming sFlow telemetry from a pair of edge routers. A mix of many small flows mixed Continue reading
Tech Bytes: Payomatic Cuts Costs, Revamps WAN With Fortinet Secure SD-WAN (Sponsored)
Today’s Tech Bytes episode, sponsored by Fortinet, explores an SD-WAN deployment with PAYOMATIC, a lending company in NYC. We talk about how PAYOMATIC cut costs by migrating off MPLS, and how Fortinet Secure SD-WAN positioned the company to take advantage of new infrastructure options. Our guest is Michael Saraceno, CISO and VP of IT at PAYOMATIC.Tech Bytes: Payomatic Cuts Costs, Revamps WAN With Fortinet Secure SD-WAN (Sponsored)
Today’s Tech Bytes episode, sponsored by Fortinet, explores an SD-WAN deployment with PAYOMATIC, a lending company in NYC. We talk about how PAYOMATIC cut costs by migrating off MPLS, and how Fortinet Secure SD-WAN positioned the company to take advantage of new infrastructure options. Our guest is Michael Saraceno, CISO and VP of IT at PAYOMATIC.
The post Tech Bytes: Payomatic Cuts Costs, Revamps WAN With Fortinet Secure SD-WAN (Sponsored) appeared first on Packet Pushers.
Making the Most of Our MANRS Partnerships – NIC.br and Brazil Lead the MANRS Pack

Read this blog in Portuguese
Improving the state of routing security is no small task. It requires network operators, IXPs, and CDN and cloud providers of all sizes across the globe to work together, improve their own networks, and open lines of communications with both their friends and competitors to make a real difference.
One of the ways we’ve been able to spread the MANRS message so far and wide is through partnerships. We’re lucky to have dedicated, strong partners in several regions of the world. In this post, we’ll talk about one partnership in particular – NIC.br – and how their efforts have changed the landscape for routing security in Brazil and beyond.
A Little History
NIC.br is responsible for the administrative and operational functions related to the .br (Brazil) domain. In addition, NIC.br goes beyond similar entities in other countries, investing in actions and projects that bring a series of benefits to the improvement of activities related to the available Internet infrastructure in Brazil.
In 2017, NIC.br hosted a Safer Internet Program, which the Internet Society supported. NIC.br invited Andrei Robachevsky to speak on a fairly new initiative called MANRS addressing routing security as Continue reading
Network Break 287: Open Compute Infrastructure Makes Its Mark; Cisco Live Postponed
Today's Network Break podcast discusses the growth of the infrastructure market based on Open Compute specs, the decline in switch and routing revenues, Cisco postponing its 2020 Cisco Live virtual event, VMware's latest acquisition, and more tech news.Network Break 287: Open Compute Infrastructure Makes Its Mark; Cisco Live Postponed
Today's Network Break podcast discusses the growth of the infrastructure market based on Open Compute specs, the decline in switch and routing revenues, Cisco postponing its 2020 Cisco Live virtual event, VMware's latest acquisition, and more tech news.
The post Network Break 287: Open Compute Infrastructure Makes Its Mark; Cisco Live Postponed appeared first on Packet Pushers.

