Heavy Networking 518: Learning To Live With SNMP
Perhaps the most arcane technology in networking is the Simple Network Management Protocol (SNMP), which, despite its name, is one of the utmost confusing pieces of technology to actually use. Guests Michael W. Lucas and Allan Jude share tips and lessons on how to get the most you can out of this protocol.Member News: Internet Society Chapters Assist Communities with Telework, Remote Education

Keep working: In recent months, several Internet Society Chapters have focused on helping people to keep working during COVID-19 lockdowns. The Benin Chapter recently published a guide to remote work, with recommendations for videoconferencing apps, project management software, and file storage services. “We are facing a real health crisis, COVID-19, which is shaking up our habits and pushing companies to adapt to new working methods,” the Chapter’s post says. “Authorizing employees to telecommute is the ideal solution for the continuity of your activity and avoiding contagion within your teams.”
Building your brand: Meanwhile, the Israel Chapter hosted a webinar on employment and careers in the digital industry. Speaker Shani Haddad, CEO and founder of Brainnu, talked about the importance of people marketing themselves and telling their own stories.
Learning at a distance: It’s not just workers dealing with new situations during the COVID-19 pandemic. The Samoan Chapter has posted about distance learning, noting that the Samoa Information Technology Association has developed an e-learning platform for students attending school from home. Education is “one of the key areas that is being heavily affected by the lockdown,” the post notes.
No censorship: The Chapter in Spain has raised concerns Continue reading
Tom’s Virtual Corner at Cisco Live US 2020

One of the things that I look forward to most during Cisco Live is the opportunity to meet with people. It’s been quite a few years since I’ve been to a session during the conference. My work with Tech Field Day has kept me very busy for the past several Cisco Live events. But at the end of the day I enjoy strolling down to the Social Media hub and talking to anyone I see. Because people make Cisco Live what it is.
The Legend of Tom’s Corner has grown over the years. It’s more than just a few tables in a place where people hang out. It stands for a community. It means a lot to so many different people. It’s about meeting new friends and catching up with old ones and feeling like you belong. For so many, Tom’s Corner and the Social Media Hub is the center of Cisco Live.
And yet, we now live in extraordinary times. The plan we had for what Cisco Live would look like for us earlier this year is radically different right now. Prohibitions on travel and meetings in large groups means we will be experiencing Cisco Live from our homes Continue reading
Verizon 5G Challenges Linger as Network Gains Uplink
“Competition in the near term will be a marketing war of coverage and speed," said William Ho,...
Releasing Cloudflare Access’ most requested feature
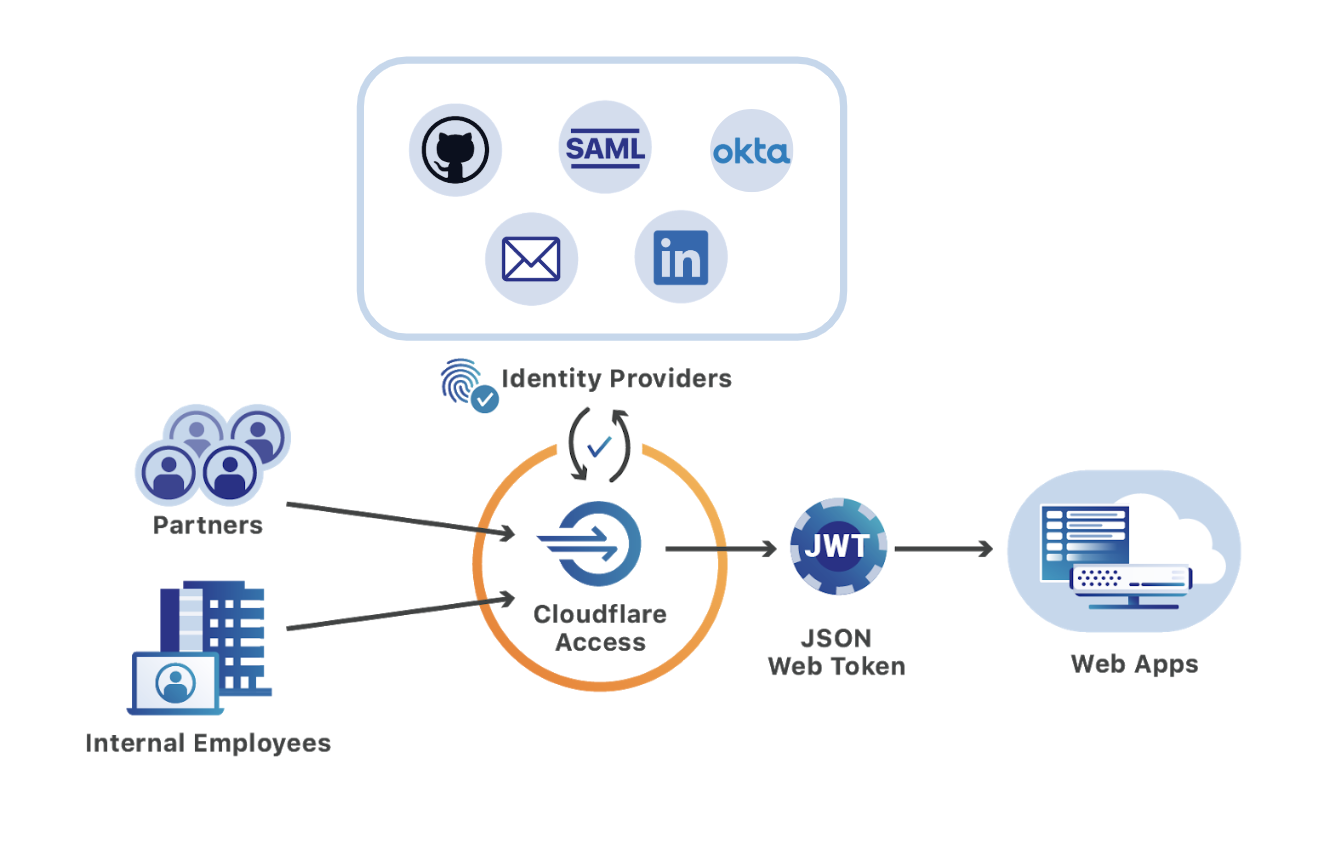
Cloudflare Access, part of Cloudflare for Teams, replaces legacy corporate VPNs with Cloudflare’s global network. Instead of starting a VPN client to backhaul traffic through an office, users visit the hostname of an internal application and login with your team’s SSO provider. While the applications feel like SaaS apps for end users, your security and IT departments can configure granular controls and audit logging in a single place.
Since Access launched two years ago, customers have been able to integrate multiple SSO providers at the same time. This MultiSSO option makes it seamless for teams to have employees login with Okta or Azure AD while partners and contractors use LinkedIN or GitHub.
The integrations always applied globally. Users would see all SSO options when connecting to any application protected by Cloudflare Access. As more organizations use Cloudflare Access to connect distributed and mixed workforces to resources, listing every provider on every app no longer scales.
For example, your team might have an internal GitLab instance that only employees need to access using your corporate G Suite login. Meanwhile, the marketing department needs to share QA versions of new sites with an external agency who authenticates with LinkedIn. Asking both Continue reading
Weekly Wrap: Oracle Challenges AWS to Cloud Calculator Duel
SDxCentral Weekly Wrap for May 22, 2020: Oracle claims cloud cost-superiority over AWS; Google hugs...
Video: Cisco SD-WAN Solution Architecture and Components
After describing Cisco SD-WAN fundamentals and its network abstraction mechanisms, David Penaloza explained the components of Cisco SD-WAN solution and its architecture, including in which plane each element operates and its assigned role in the overlay network.
It’s 2020 And Android’s IPv6 Is Still Broken
I got into some interesting discussions about IPv6 on Twitter. Then someone asked if Android is getting DHCPv6 support in version 11 of the OS.
When IPv6 was developed, initially with RFC 2460, there was this idea that:
Forget all you've learned about IPv4, and design IPv6 from the ground up
This sounds good in theory but ignores completely the lessons we’ve learned from IPv4. Not to mention, there is no such thing as greenfield. Almost all networks, are existing ones, you don’t get to start all over again. There was this very shiny view of end to end connectivity, /64 everywhere and only SLAAC allowed. I get all of that, it’s like saying “I wish there were no wars”, but unfortunately, people are stupid, so there will be wars. There’s this naivety, similar to a teenager that is growing up. You want to change the world, then you realize the world is run by money, mega corps, and dirty politicians.
This whole mess led to the holy wars of SLAAC + RDNSS vs DHCPv6. Please note that SLAAC Continue reading
HPE Cuts Salaries Companywide as COVID-19 Wrecks Q2
HPE reported fiscal 2020 Q2 revenues of $6 billion, down 15% from a year ago, with a drop in...
Palo Alto Networks Weathers Pandemic With Strong Earnings
The company’s Q3 revenues hit $869.4 million, up 20% year over year, bolstered by a pandemic...
BGP AS Numbers on MLAG Members
I got this question about the use of AS numbers on data center leaf switches participating in an MLAG cluster:
In the Leaf-and-Spine Fabric Architectures you made the recommendation to have the same AS number on all members of an MLAG cluster and run iBGP between them. In the Autonomous Systems and AS Numbers article you discuss the option of having different AS number per leaf. Which one should I use… and do I still need the EBGP peering between the leaf pair?
As always, there’s a bit of a gap between theory and practice ;), but let’s start with a leaf-and-spine fabric diagram illustrating both concepts:
Scaling EVPN Multi-Site Overlays using Route-Servers
Cisco’s EVPN Multi-Site it’s a great technology that allows us to achieve massive scale of an EVPN network. With the latest release, the official scalability numbers give us something in the realm of over 12000 VTEPs (512 VTEPs per site x 25 sites).
I’m in no way suggesting that you would need such a big topology and you definitely should segment way sooner you reach the limit, but still…
The main configuration requirement for the Multi-Site overlay is to have a full mesh of eBGP peering between all border gateways.
This has scalability drawbacks as usual. Not only each leaf will have ever growing number of peers which will soon grow out of control, but maybe, worse is the fact that after one site is added, every other site must be touched too.

To avoid a full mesh, for iBGP topologies we would be using a Route Reflector, but with eBGP that’s obviously not an option. So, instead of a RR they way to scale eBGP peerings is to leverage a Route-Server.

A Route-Server provides route reflection capabilities and as such it must ensure that NLRIs attributes like the Next Hop and route-targets aren’t changed.
In Cisco’s EVPN implementation, the Continue reading
The Hedge Episode 36: Rich Alderson and the Living Computer History Museum
The Living Computers History Museum and Labs was founding by Paul Allen to collect early computer systems and keep the constrained resource coding practices used on these systems alive. Over time it has developed into a living museum and lab, with hands-on access to some of the earliest examples of computing history. Rich Alderson joins us for this episode of the Hedge to describe the museum and its exhibits.
Central African Peering Forum: A Defining Moment for Peering and Interconnection

The first-ever Central African Peering Forum comes at a defining moment for Internet peering and interconnection. In the midst of the COVID-19 pandemic, countries have implemented measures to restrict people from moving from their homes, while only allowing essential movements and services.
But life cannot stop.
Kids still need to study and attend school. People still need to access financial services, conduct personal and business transactions, access government services, pay their taxes, and access health services. Most importantly, people need to access accurate and timely information. But now these services must be provided at a larger scale – via reliable Internet infrastructure. Moreover, some of this content and these services do not exist in digital format. They need to be created, sometimes in the language of local communities.
COVID-19 has uncovered gaps, missing elements, and key challenges, which need to be addressed so that life can smoothly transition to the new normal. Failing to address these challenges may result in severe socioeconomic consequences.
We are now a few months down the path since lockdown measures have been implemented in most countries. It is time to reflect on the lessons learnt so far, with respect to the reliability of the Internet Continue reading
Day Two Cloud 049: The Gritty Details Of Designing And Running A Private Cloud
On today's Day Two Cloud we tackle the practical aspects of private cloud, including designing the infrastructure and creating policies before you start racking gear, and why thinking about services is critical. Our guest is Brett Johnson, a Senior Consultant at VMware.
The post Day Two Cloud 049: The Gritty Details Of Designing And Running A Private Cloud appeared first on Packet Pushers.
Day Two Cloud 049: The Gritty Details Of Designing And Running A Private Cloud
On today's Day Two Cloud we tackle the practical aspects of private cloud, including designing the infrastructure and creating policies before you start racking gear, and why thinking about services is critical. Our guest is Brett Johnson, a Senior Consultant at VMware.The Latest Modern Innovation in Architecture
Architecture is constantly changing. New materials and ideas, as well as the needs of clients, drive new innovation in architecture. The latest innovation in architecture is that there are no defining standards, allowing for a wide variety of different styles and designs.
Modern architecture places emphasis on horizontal and vertical lines, as well as 90-degree angles. Modern architecture depends a great deal on sculpture forms, smooth surfaces, circular voids, and overhead shading systems.
Innovations in architecture include such features as large horizontal windows and ample natural light, as well as outdoors entertainment areas.
Architecture Innovations for Those on a Budget
In the last few years, one of the biggest innovations in architecture is the designing of tiny houses for those on a budget. These tiny homes need to be well thought out and the innovation comes in when architects have to come up with innovative ways to fit everything that normal homes have in a small space often no larger than a small bedroom.
Some of the innovations in this include such things as built in storage solutions and multifunctional furniture to make the most of the limited living space.
Another architecture innovation is the turning shipping containers into cute Continue reading