Ericsson Expands 5G, DSS Deal With Nex-Tech Wireless
The Kansas-based operator plans to launch its 5G service before July.
VMware Patches Critical Bug That Exposes Sensitive Data
The vulnerability could allow a hacker to “extract highly sensitive information which could be...
Could the CARES Act Close the Digital Divide in the United States?

Last week, the U.S. Congress passed the third stimulus bill in response to the COVID-19 pandemic. This bill primarily focused on economic relief for companies, individuals, cities, states, and tribal communities. It allocates over $2 trillion in funds for a variety of measures intended to ease the burden of COVID-19.
Some of the included measures have been in the news for weeks, including those related to individual checks for those financially impacted by the virus. But there is an element to this bill that is equally important, not only for our ability to cope with the virus now but also to permanently change our country for the better.
These emergency funds allocate $150 billion to states and territories, including $8 billion specifically for Tribal governments, for “coronavirus relief.” What that relief looks like, however, is relatively vague. If a community was financially impacted by the pandemic between March and December of this year, in a way that they did not originally anticipate in their budgets, this fund covers most of those expenses.
And what is one of the biggest impacts we’ve seen? Millions of people have been forced to isolate themselves at home and carry out their daily Continue reading
Bringing Reference Architectures to Multi-Cloud Networking
Recently I attended Aviatrix Certified Engineer training to better understand multi-cloud networking and how Aviatrix is trying to solve its many problems, some of which I have experienced first-hand. Disclaimer: Since 2011, I’ve been an avid listener of the Packet Pushers podcast, where Aviatrix has sponsored 3 shows since December 2019. Ever since I embarked … Continue reading Bringing Reference Architectures to Multi-Cloud NetworkingThe Week in Internet News: Pandemic Puts Spotlight on Access Problems

No working from home: Working from home during the COVID-19 pandemic is tougher in some places than in others. Business Insider finds 17 U.S. cities where Internet access is lower than in much of the rest of the country. Many of the cities listed are across the South and in New Mexico.
Students need access: Alabama’s state schools superintendent is worried about a lack of access for some students while schools are shut down during the pandemic, AL.com reports. There are several “gaps” in access for students, but some school districts are using buses to deliver WiFi.
100,000 laptops: Meanwhile, in Arizona, more than 100,000 students need laptops in order to do school work from home, AZcentral.com reports. The Greater Phoenix Chamber Foundation has been running a laptop drive to reduce that number. Access is also a problem in some rural areas, with some areas having only 25 percent of households with Internet access.
Fundraising for access: In Maine, the Bangor School Department has turned to fundraising to provide 350 families with Internet access so students can participate in distance learning, the Bangor Daily News reports. The school department raised about $28,000 in a week on the Continue reading
Helping sites get back online: the origin monitoring intern project


The most impactful internship experiences involve building something meaningful from scratch and learning along the way. Those can be tough goals to accomplish during a short summer internship, but our experience with Cloudflare’s 2019 intern program met both of them and more! Over the course of ten weeks, our team of three interns (two engineering, one product management) went from a problem statement to a new feature, which is still working in production for all Cloudflare customers.
The project
Cloudflare sits between customers’ origin servers and end users. This means that all traffic to the origin server runs through Cloudflare, so we know when something goes wrong with a server and sometimes reflect that status back to users. For example, if an origin is refusing connections and there’s no cached version of the site available, Cloudflare will display a 521 error. If customers don’t have monitoring systems configured to detect and notify them when failures like this occur, their websites may go down silently, and they may hear about the issue for the first time from angry users.
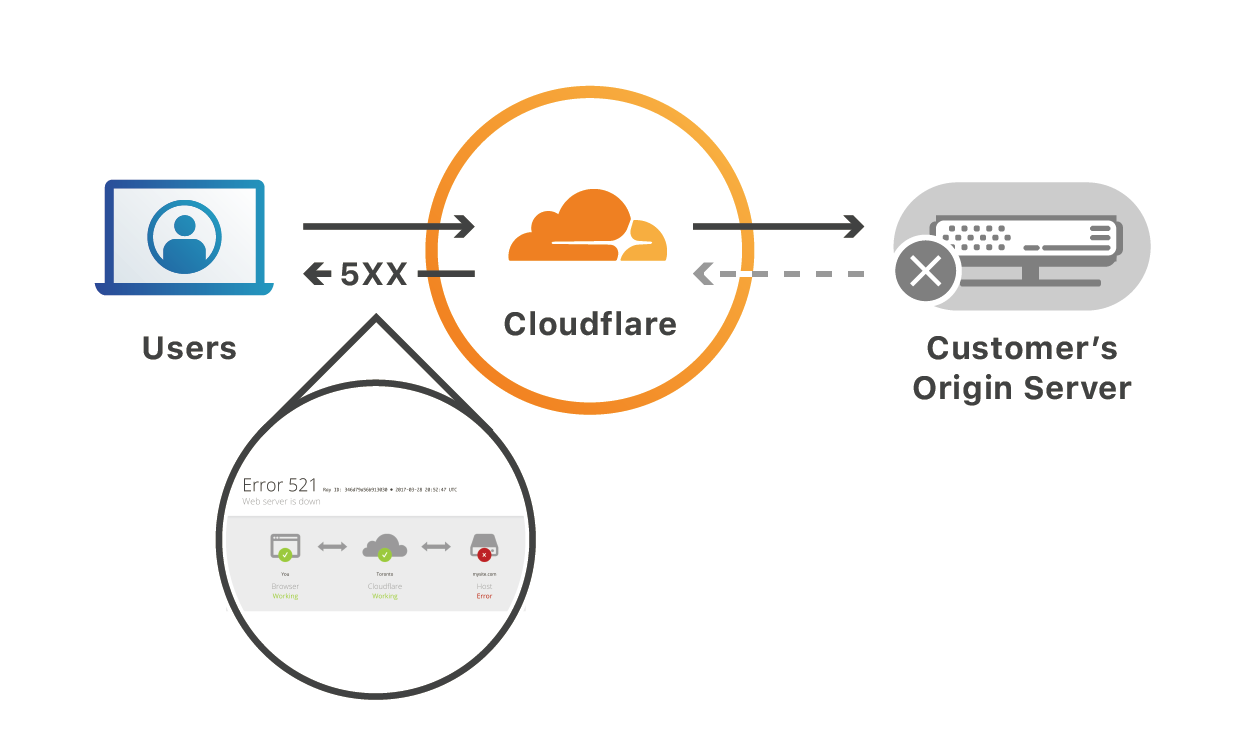

This problem became the starting Continue reading
HS. Part 2. Automatic generation and visualisation of the network topology.
Hello my friend,
Surprisingly for myself in the previous post about networking I’ve started completely new topic. It was about the Microsoft Azure SONIC running inside the Docker container and network between those containers. Why is that new? Why does it matter? What is in it for you?
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
Network automation training – boost your career
To be able to understand and, more important, to create such a solutions, you need to have a holistic knowledge about the network automation. Come to our network automation training to get this knowledge and skills.

At this training we teach you all the necessary concepts such as YANG data modelling, working with JSON/YAML/XML data formats, Linux administration basics, programming in Bash/Ansible/Python for multiple network operation systems including Cisco IOS XR, Nokia SR OS, Arista EOS and Cumulus Linux. All the most useful things such as NETCONF, REST API, OpenConfig and many others are there. Don’t miss the opportunity to improve Continue reading
COVID-19 Profiteers?
Numerous online companies are using the COVID-19 crisis to make their products better known (PacketPushers collected some of them). Nothing wrong with that - they’re investing into providing free- or at-cost resources, and hope to get increased traction in the market. Pretty fair and useful.
Then there are others… Here’s a recent email I got:
Money Moves: March 2020
Palo Alto paid $420M for CloudGenix; Microsoft acquired Affirmed; AWS pledged $20 million to...
Altiostar CEO: Open RAN Will Dominate in 3 Years
“In the next three years economic forces will drive operators to go to open RAN," said Altiostar...
Remote work, regional lockdowns and migration of Internet usage

The recommendation for social distancing to slow down the spread of COVID-19 has led many companies to adopt a work-from-home policy for their employees in offices around the world, and Cloudflare is no exception.
As a result, a large portion of Internet access shifted from office-focused areas, like city centers and business parks, towards more residential areas like suburbs and outlying towns. We wanted to find out just precisely how broad this geographical traffic migration was, and how different locations were affected by it.
It turns out it is substantial, and the results are quite stunning:
Gathering the Data
So how can we determine if Internet usage patterns have changed from a geographical perspective?
In each Cloudflare Point of Presence (in more than 200 cities worldwide) there's an edge router whose responsibility it is to switch Internet traffic to serve the requests of end users in the region.
These edge routers are the network's entry point and for monitoring and debugging purposes each router samples IP packet information regarding the traffic that traverses them. This data is collected as flow records and contains layer-3 related information, such as the source and destination IP address, port, packet size etc.
These statistical Continue reading
APRS
Another post in my burst of amateur radio blog posts.
To say that the documentation for APRS is not great is an understatement. What should be the best source of information, aprs.org, is just a collection of angry rants by the inventor of APRS, angrily accusing implementations and operators of using his invention the wrong way. There’s no documentation about what the right way is, just that everyone is wrong.
So here I’ll attempt to write down what it is, in one place, in an effort to both teach others, and for people who know more than me to correct me.
The best source of APRS information for me has actually been Kenwood radio manuals. See resources at the bottom.
APRS in short
APRS is a way to send short pieces of digital information as packets of data. The messages are:
- Status about you
- Your position (optionally not exact)
- Your heading
- Your QSY (frequency you’re tuned to if someone wants to call)
- Weather reports
- Status about “items” and “objects”. This is objects that are not you, and aren’t a radio. For example where the meeting point is, or a hurricane.
- Short messages
The protocol
As an operator you Continue reading
Daily Roundup: Cisco Vows No Job Cuts
Cisco pledged to preserve jobs; AWS added direct storage to ECS, Fargate; and SAP prepped for...
Zscaler Buys Cloud Security Startup Cloudneeti
Gartner recommends all security vendors invest in cloud security posture management and forecasts...
AI Surges In Response to Pandemic
Spending on AI is poised to jump, particularly among enterprises that are deploying the technology...
Cisco, Other Tech Firms Vow No Job Cuts
Cisco CEO Chuck Robbins said his company has the wherewithal to survive the pandemic without laying...
Heavy Networking 511: A Wireless Upgrade Case Study
Today's Heavy Networking is all about wireless. Guest Bryan Ward, Lead Network Engineer at Dartmouth College, takes us through a campus-wide wireless upgrade that the institution is currently undertaking. We get nerdy about planning, infrastructure, cabling, and more, and dive into why the college is switching vendors.
The post Heavy Networking 511: A Wireless Upgrade Case Study appeared first on Packet Pushers.