Conntrack tales – one thousand and one flows
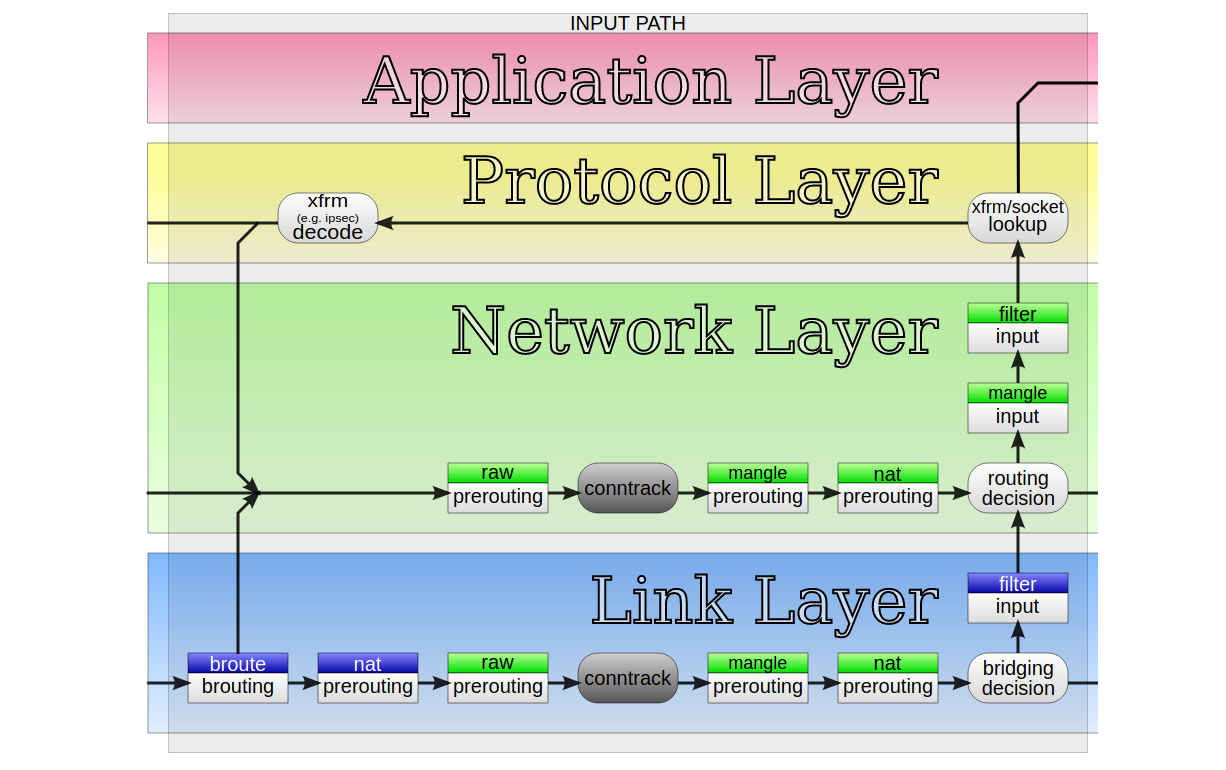
At Cloudflare we develop new products at a great pace. Their needs often challenge the architectural assumptions we made in the past. For example, years ago we decided to avoid using Linux's "conntrack" - stateful firewall facility. This brought great benefits - it simplified our iptables firewall setup, sped up the system a bit and made the inbound packet path easier to understand.
But eventually our needs changed. One of our new products had a reasonable need for it. But we weren't confident - can we just enable conntrack and move on? How does it actually work? I volunteered to help the team understand the dark corners of the "conntrack" subsystem.
What is conntrack?
"Conntrack" is a part of Linux network stack, specifically part of the firewall subsystem. To put that into perspective: early firewalls were entirely stateless. They could express only basic logic, like: allow SYN packets to port 80 and 443, and block everything else.
The stateless design gave some basic network security, but was quickly deemed insufficient. You see, there are certain things that can't be expressed in a stateless way. The canonical example is assessment of ACK packets - it's impossible to say if an ACK Continue reading
BGP on Cisco IOS XRv – Prefix-Sets and Route-Policies
The goal of this tutorial is to practice BGP configuration and filtering incoming and outgoing updates on Cisco IOS XRv. In order to do it, we configure prefix-sets and route-policy that will be applied to a particular BGP neighbor. Let's have a network topology depicted on the Picture 1. The ISP1 (AS number 64500) has […]Continue reading...
The Never-Ending Story of CLI or API
Over the last weekend I almost got pulled into yet-another CLI-or-automation Twitter spat. The really sad part: I thought we were past that point. After all, I’ve been ranting about that topic for almost seven years… and yet I’m still hearing the same arguments I did in those days.
Just for the giggles I collected a few old blog posts on the topic (not that anyone evangelizing their opinions on Twitter would ever take the time to read them ;).
AWS VPC Traffic Mirroring Walkthrough
I was recently playing around with the Traffic Mirroring feature in AWS. As a network geek, this is right up my alley because as some colleagues and I used to say, "the wire never lies!". Being able to pick packets off the wire for detailed inspection has saved the day many a time. Until Traffic Mirroring came along, it wasn't possible to do that in an Amazon VPC. Below are my notes and considerations for using this feature.Ostinato – Drone Mode – Traffic Generator
I have started this below article detailing a small subset of what Ostinato is capable of doing, in short, is a traffic generator with great options to modify and dictate the type of traffic that you want to generate and can do it at decent speeds
What is the Issue: The issue is that Ostinato in default mode is only supported in GUI mode, which is good for many cases but some times especially if you want to send some decent traffic to stress test your MPLS LSP a PC working from home scenario over VPN is not an ideal bet.
Explain more: Well, imagine you have a Cloud provider Instance, most of the instances are CLI based while Ostinato is GUI based.
So How to Proceed: After seeing what Tool is capable of we purchased the full suite which has Python Api support Plugin as well. So it operates something like this

How does it look:
so you have start the drone first, before doing anything else, i was stuck in this phase for more than 2 hours just because i was dumb not to read all the instructions

You can build the packet and save Continue reading
Safer SSH agent forwarding
ssh-agent is a program to hold in memory the private keys used by
SSH for public-key authentication. When the agent is running, ssh
forwards to it the signature requests from the server. The agent
performs the private key operations and returns the results to ssh.
It is useful if you keep your private keys encrypted on disk and you
don’t want to type the password at each connection. Keeping the agent
secure is critical: someone able to communicate with the agent can
authenticate on your behalf on remote servers.
ssh also provides the ability to forward the agent to a remote
server. From this remote server, you can authenticate to another
server using your local agent, without copying your private key on the
intermediate server. As stated in the manual page, this is
dangerous!
Agent forwarding should be enabled with caution. Users with the ability to bypass file permissions on the remote host (for the agent’s UNIX-domain socket) can access the local agent through the forwarded connection. An attacker cannot obtain key material from the agent, however they can perform operations on the keys that enable them to authenticate using the identities loaded into the agent. A safer alternative Continue reading
Headcount: Firings, Hirings, and Retirings — March 2020
Cisco, Hitachi cut hundreds of jobs; Nokia CEO walked the plank; AT&T slashed jobs; plus the...
CEX (Code EXpress) 10. Creating user functions.
Hello my friend,
So far you have learned the most vital tools to start writing your code in Python such as Python’s variables, lists, dictionary data constructions and code flow control for, while and if. Today you will see how to join them all together to create a user defined functions to make your Python’s code cleaner and less error-prone.
Network automation training – boost your career
Don’t wait to be kicked out of IT business. Join our network automation training to secure your job in future. Come to NetDevOps side.

How does the training differ from this blog post series? Here you get the basics and learn some programming concepts in general, whereas in the training you get comprehensive set of knowledge with the detailed examples how to use Python for the network and IT automation. You need both.
What are we going to do today?
User-defined functions is a reusable parts of the Python’s code, which allow you create some processing once in your code and then call it multiple types anywhere you need. So you will learn:
- Why it is useful to create user-defined functions
- How to create the user-defined functions and use them Continue reading
Amateur radio digital voice
It’s a mess.
This post is my attempt at a summary of amateur radio digital voice modes, and what I think of them.
I’m not an expert, so if you have more experience then your opinion is likely more valid than mine. But hopefully at least I’m getting the facts right. Please correct me where I’m mistaken.
Analog and digital voice
In the beginning there was only analog. Traditionally on HF you used SSB, and on VHF/UHF you use FM. Analog works, and while yes there are different modes, radios tend to support all of them, or at least the common ones (e.g. most VHF/UHF radios don’t support SSB, because most traffic there is FM). Usually HT traffic is VHF/UHF FM, and for SSB while there is LSB and USB, radios will support both.
But analog isn’t perfect. By going digital we can send metadata such as call signs, positions, and even pictures and files. And for audio quality digital will get rid of the static of analog noise. Digital works better for longer distances, uses less spectrum, and retains voice clarity much longer.
Yes, there’s a sharp cliff when digital voice modes can no longer Continue reading
Versa CMO Stakes Claim in Competitive SD-WAN Market
Wood is no stranger to the SD-WAN market. He joined Versa’s executive team in February after a...
The Serverlist: Built with Workers, Single-Tenant Architecture, and more!

Check out our fourteenth edition of The Serverlist below. Get the latest scoop on the serverless space, get your hands dirty with new developer tutorials, engage in conversations with other serverless developers, and find upcoming meetups and conferences to attend.
Sign up below to have The Serverlist sent directly to your mailbox.
Hyperscalers Crystallize 5G, Edge Strategies
“As the 5G edge unfolds, we’ll start to see more of a marriage between the telcos and...
Daily Roundup: AT&T Sees 700% SD-WAN Surge
AT&T saw a 700% SD-WAN surge; VMware, FBI warned of cybercriminals targeting teleworkers; and...
BiB091: Rancher Open Source K8s Management Releases 2.4
Rancher has announced version 2.4, which might seem like...meh...no big deal. Companies publish incremental software releases all the time. Well, Rancher 2.4 is interesting because it indicates where Kubernetes is heading. That is...Kubernetes everywhere, running production workloads. In your data center. At the edge. In the public cloud.BiB091: Rancher Open Source K8s Management Releases 2.4
Rancher has announced version 2.4, which might seem like...meh...no big deal. Companies publish incremental software releases all the time. Well, Rancher 2.4 is interesting because it indicates where Kubernetes is heading. That is...Kubernetes everywhere, running production workloads. In your data center. At the edge. In the public cloud.
The post BiB091: Rancher Open Source K8s Management Releases 2.4 appeared first on Packet Pushers.
Terraform an HA-VPN between GCP and Cisco
Doing Infrastucture-as-Code (IaC) with Ansible has given me a headache – so I’ve recently been playing around with Terraform as an alternative to Ansible for certain tasks that require Cloud IaaS interactions. The goal of this blog post is to build an HA-VPN solution between GCP and an on-premises Cisco IOS-XE device (CSR) using Terraform. […]
The post Terraform an HA-VPN between GCP and Cisco appeared first on Overlaid.
Heavy Networking 510: Take A Modern Approach To SD-WAN And Networking With Fortinet (Sponsored)
On today's sponsored show, we dig into Fortinet's portfolio, including SD-WAN and its security fabric. We discuss customer use cases, examine how the fabric works, and explore how Foritnet integrates its own and third-party security tools to enhance visibility and automation. Our guest is Stephen Watkins, Director and Principal Security Architect at Fortinet.
The post Heavy Networking 510: Take A Modern Approach To SD-WAN And Networking With Fortinet (Sponsored) appeared first on Packet Pushers.