CEX (Code EXpress) 04. List what you need.
Hello my friend,
We continue discussion about the variable in the Python, which we have started in the previous article. Today we cover new type, which is very useful and, therefore, widely used. In various programming languages, this type is known under various names. So, who is here?
Network automation training – boost your career
Don’t wait to be kicked out of IT business. Join our network automation training to secure your job in future. Come to NetDevOps side.

How does the training differ from this blog post series? Here you get the basics and learn some programming concepts in general, whereas in the training you get comprehensive set of knowledge with the detailed examples how to use Python for the network and IT automation. You need both.
What are we going to do today?
Answering to the question in the end of the preamble, here is the list. It is also known under the name array; however, in the Python’s terminology list is the correct term. The list variable contains any amount of the elements (starting from zero), which are siblings to each other, and they can be of any type as described in the previous article. Continue reading
Kubernetes Security Plagued by Human Error, Misconfigs
Exposures and data breaches due to misconfigurations have become an “alarmingly common” trend...
Lora – Test and results – awesome
What is LORA – Best reference – https://www.thethingsnetwork.org
I will anyways attempt to define this as a newbie who just got into this technology
“with the help of a specific Receiver and Transmitter and using Radio waves you can send small bits of information to long ranges without the need of repeaters or wireless IP networking gear. “
Why is this useful – I have many use cases simple one being measuring soil moisture for plants and measuring water level in an overhead tank.
I currently have a very expensive setup of a Raspberry Pi zero wireless, a Repeater to repeat my Base Ip Network and a solar panel to power the power-hungry sensor as Raspberry pi does not know how to go into Deepsleep and wakeup.
Lora Makes it simple and even in reasonable living space, wireless routers do not perform well to cover the range up till the back yard garden.
What do you need – Listed in the below article and its nicely written
Most of the Sample Code – https://randomnerdtutorials.com/ttgo-lora32-sx1276-arduino-ide/
I have tested its range till 300m without any issues at all, that’s like 4 times what my wireless router can do!

Daily Roundup: Digital Ocean Grabs $300M Life Preserver
Digital Ocean grabbed a $300M life preserver; Microsoft imported AWS logs for free; and U.S....
Cisco Viptela Joins ConvergeOne’s SD-WAN Lineup
The announcement marks Cisco's second service provider announcement in the past month.
NDSS 2020: The Best in Security Research – For the Good of the Internet

On 23 February, the 27th consecutive Network and Distributed System Security Symposium (NDSS) kicks off in San Diego, CA. NDSS is a premier academic research conference addressing a wide range of topics on network and system security. It’s an incubator for new, innovative ideas and research on the security and privacy of the Internet.
NDSS 2020 (23-26 February) will be one of the biggest NDSS symposium yet, featuring 88 peer-reviewed academic papers, 34 posters, 5 workshops, and 2 keynotes on vital and timely topics. Here are some of the highlights.
Workshops
This year’s program officially starts with five workshops on Sunday, 23 February. NDSS workshops are organized around a single topic and provide an opportunity for greater dialogue between researchers and practitioners in the area.
The QUIC Privacy and Security (QUIPS) Workshop focuses on QUIC security and privacy analysis efforts. The IETF QUIC protocol is a modern UDP-based, stream-multiplexing, encrypted transport protocol. Inspired by prior art, QUIC’s packet and header encryption removes cleartext information from the network while simultaneously mitigating ossification of version-specific protocol behavior. The goal of the QUIPS workshop is to bring formal analysis results to the IETF working group and developer communities in order to build confidence Continue reading
Canada’s Innovative Future Relies on Upholding Core Properties of the Capital ‘I’ Internet

As Canada considers how to renew its broadcasting and telecommunications regulatory regime, it should steer clear of recent recommendations that would impact key Internet properties that foster Canadian innovation online.
On Jan. 29 the Broadcasting and Telecommunications Legislative Review (BTLR) panel handed the Canadian government 97 recommendations to consider as it prepares new legislation to update the decades-old Telecommunications Act, Radiocommunication Act and Broadcasting Act.
While it has laudable advice on how to improve access to rural and remote Indigenous communities in Canada, the report’s major flaws would inhibit the same Canadian innovation the recommendations intend to promote.
This includes giving Canadian Radio-television and Telecommunications Commission (CRTC) the authority to treat the Internet like a broadcasting network, and setting unrealistic rules that would harm crucial elements of the Internet in the name of promoting Canadian content online.
There are many reasons you can’t treat the Internet like a traditional broadcaster, but the key one is this: the Internet is not like other technologies.
While it is essentially just an interconnected network of networks – hence the name: Inter-net – the Internet was built with a unique set of properties that were critical to its success to date: openness, decentralization, Continue reading
Full Stack Journey 039: Career Transitions And Finding A Gap To Be An Expert With Lauren Malhoit
Today's Full Stack Journey episode features Lauren Malhoit. Lauren came up in the tech industry as a systems engineer. She's now in technical product marking at Juniper Networks. Lauren and Scott talk about career transitions, leadership vs. management, and "finding a gap where you can be an expert."Full Stack Journey 039: Career Transitions And Finding A Gap To Be An Expert With Lauren Malhoit
Today's Full Stack Journey episode features Lauren Malhoit. Lauren came up in the tech industry as a systems engineer. She's now in technical product marking at Juniper Networks. Lauren and Scott talk about career transitions, leadership vs. management, and "finding a gap where you can be an expert."
The post Full Stack Journey 039: Career Transitions And Finding A Gap To Be An Expert With Lauren Malhoit appeared first on Packet Pushers.
U.S. Cellular Readies 5G Launch on March 6
U.S. Cellular is increasing capex spending in 2020 to a range of $850 million to $950 million,...
Using your devices as the key to your apps
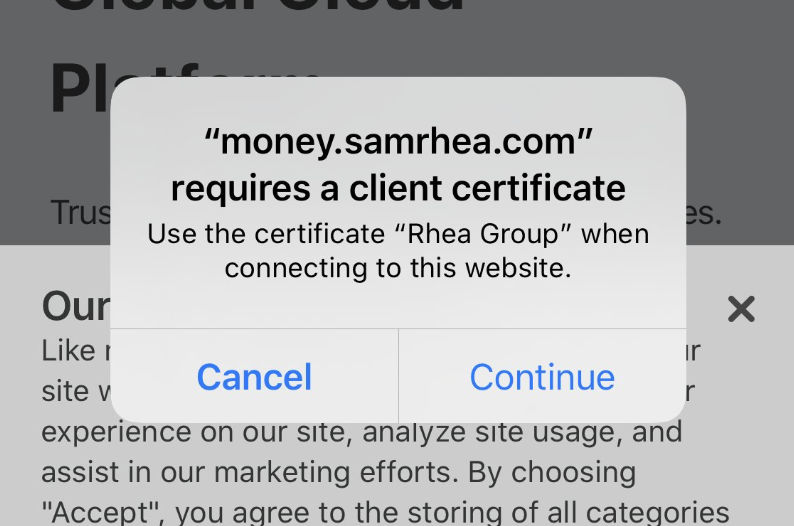
I keep a very detailed budget. I have for the last 7 years. I manually input every expense into a spreadsheet app and use a combination of sumifs functions to track spending.
Opening the spreadsheet app, and then the specific spreadsheet, every time that I want to submit an expense is a little clunky. I'm working on a new project to make that easier. I'm building a simple web app, with a very basic form, into which I will enter one-off expenses. This form will then append those expenses as rows into the budget workbook.
I want to lock down this project; I prefer that I am the only person with the power to wreck my budget. To do that, I'm going to use Cloudflare Access. With Access, I can require a login to reach the page - no server-side changes required.
Except, I don't want to allow logins from any device. For this project, I want to turn my iPhone into the only device that can reach this app.
To do that, I'll use Cloudflare Access in combination with an open source toolkit from Cloudflare, cfssl. Together, I can convert my device into a secure key for this application Continue reading
DigitalOcean Grabs $300M Life Preserver
The bank debt financing comes a month after the company acknowledged that it was laying off dozens...
Weekly Wrap: Dell Sells RSA Security Biz for $2 Billion
SDxCentral Weekly Wrap for Feb. 21, 2020: The RSA deal includes the upcoming RSA security...
Heavy Networking 503: Achieve Multi-Domain Network Automation With Itential (Sponsored)
On today’s Heavy Networking, we talk with sponsor Itential about its network automation approach, where you can take what you’re already using (scripts, Ansible, etc.) and incorporate it into a holistic automation strategy. Itential enables automation across physical, virtual, and cloud domains and takes a low-code approach so that your engineers don’t have to become developers. Our guest is Chris Wade, Itential's co-founder and CTO.Heavy Networking 503: Achieve Multi-Domain Network Automation With Itential (Sponsored)
On today’s Heavy Networking, we talk with sponsor Itential about its network automation approach, where you can take what you’re already using (scripts, Ansible, etc.) and incorporate it into a holistic automation strategy. Itential enables automation across physical, virtual, and cloud domains and takes a low-code approach so that your engineers don’t have to become developers. Our guest is Chris Wade, Itential's co-founder and CTO.
The post Heavy Networking 503: Achieve Multi-Domain Network Automation With Itential (Sponsored) appeared first on Packet Pushers.
Video: FRRouting Configuration and Performance Optimizations
After introducing FRRouting architecture, Donald Sharp dived deep into configuration and performance optimizations, including asynchronous data plane, next hop groups, and commit-and-rollback.
Video: FRRouting Configuration and Performance Optimizations
After introducing FRRouting architecture, Donald Sharp dived deep into configuration and performance optimizations, including asynchronous data plane, next hop groups, and commit-and-rollback.