OCP Global Summit 2024
AI networking is a popular topic at the up coming OCP Global Summit in San Jose, California, with an entire morning on Wednesday October 16 devoted to the subject. Of particular interest is the talk, Leveraging open technologies to monitor packet drops in AI cluster fabrics, by Aldrin Isaac, eBay, describing the challenge, AI clusters operate most efficiently over lossless networks for optimum job completion times which can be significantly impacted by dropped packets. Although networks can be designed to minimize packet loss by choosing the right network topology, optimizing network devices and protocols, an effective monitoring and troubleshooting network performance tool is still required. Such tool should capture packet drops, raise notifications and identify various drop reasons and pin point where the drops caused congestions. In turn, it allows the governing management application to tune configurations of relevant infrastructure components, including switches, NICs and GPU servers.The talk will share the results and best practices of a TAM (Telemetry and Monitoring) solution being prepared for deployment at eBay. It leverages OCP’s SAI and open sFlow drop notification technologies as part of eBay’s ongoing initiatives to adopt open networking hardware and community SONiC for its data centers.
AI for Network Engineers: Backpropagation Algorithm
Introduction
This chapter introduces the training model of a neural network based on the Backpropagation algorithm. The goal is to provide a clear and solid understanding of the process without delving deeply into the mathematical formulas, while still explaining the fundamental operations of the involved functions. The chapter also briefly explains why, and in which phases the training job generates traffic to the network, and why lossless packet transport is required. The Backpropagation algorithm is composed of two phases: the Forward pass (computation phase) and the Backward pass (adjustment and communication phase).
In the Forward pass, neurons in the first hidden layer calculate the weighted sum of input parameters received from the input layer, which is then passed to the neuron's activation function. Note that neurons in the input layer are not computational units; they simply pass the input variables to the connected neurons in the first hidden layer. The output from the activation function of a neuron is then used as input for the connected neurons in the next layer. The result of the activation function in the output layer represents the model's prediction, which is compared to the expected value (ground truth) using the error function. The output Continue reading
How Do You Get Experience in IT?
A question I often get is, how do you get experience in IT? For people trying to break into this industry, what can they do to gain experience? How can they showcase that experience to a potential employer even if they are applying for their first job? Breaking into a new industry can be the most difficult thing, you lack experience and most of all you probably lack a network. Here are my thoughts on how you can gain that experience.
University studies
The ROI on university studies will vary depending on if you live in a country like me where studies are financed by tax and there is no tuition, or in a country where it can be very costly. That’s not the argument here, university studies can give some things that is difficult to achieve in any other way. I did three years at a university and here’s why I think it’s really valuable.
Time – Having two or three years of dedicated studies is a luxury you won’t have at any other point in your career. You have a full-time job and trying to learn a new discipline on top of that is going to be much Continue reading
Using BGP NO_EXPORT Community to Filter Transit Routes
In previous BGP policy lab exercises, we covered several mechanisms you can use to ensure your autonomous system is not leaking transit routes (because bad things happen when you do, particularly when your upstream ISP is clueless).
As you probably know by now, there’s always more than one way to get something done with BGP. Today, we’ll explore how you can use the NO_EXPORT community to filter transit routes.
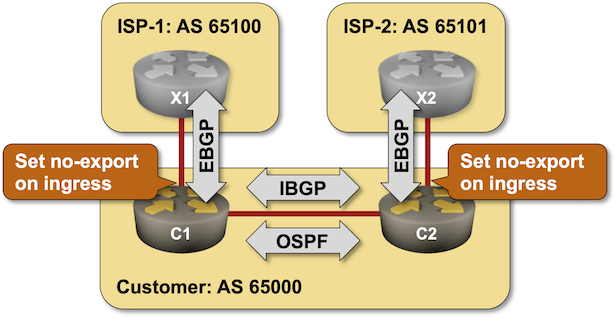
Click here to start the lab in your browser using GitHub Codespaces (or set up your own lab infrastructure). After starting the lab environment, change the directory to policy/d-no-export and execute netlab up.
How to Protect GlobalProtect Portal from Brute Force Attacks?

As soon as you configure GlobalProtect and go to the monitor tab, you will see hundreds or even thousands of attempts on your firewall's public IP on port 443. While protecting your portal with MFA generally mitigates major concerns, it’s still wise to implement as many security measures as possible. In this blog post, we will look at some simple ways to protect your GlobalProtect deployment.
We will look at the following methods.
- Disable GlobalProtect Portal
- Block access from malicious IPs (EDL)
- Security policy based on geo IPs
- Blacklist IPs using a Vulnerability Profile
Understanding Intrazone Policy
Before we proceed, just a quick note on how Intrazone policy works. By default, the firewall comes with two predefined security rules at the very bottom. The Interzone rule denies traffic between two zones that are not matched by a specific policy above.

However, the default intrazone action is to allow, so traffic within the same zone is allowed by default. If someone initiates traffic from the WAN zone to Palo Alto’s public interface in Continue reading
Hedge 246: Complexity and Deployment

In this roundtable episode of the Hedge, Tom, Eyvonne, and Russ discuss complexity and deployment. Why do some protocols fail to deploy, or require decades, while others deploy quickly?
TNO005: Making Networking Cool Again with Meter (Sponsored)
Meter CEO Anil Varanasi joins Scott Robohn on this sponsored episode of Total Network Operations to talk about Meter’s vision for networking and network operations. In this podcast, recorded the day before Meter’s first public MeterUp event, Anil and Scott discuss Meter’s approach to building new networking equipment, vertical integration of their hardware and software,... Read more »Packet Pushers: Chat with Eric Chou
A while ago, Eric Chou invited me to a friendly chat in his Network Automation Nerds podcast.
The episode was published a few days ago; I hope you’ll enjoy listening to it.
Memos – Amazing Open Source, Self-hosted Notes App

I've tried many note-taking apps like Evernote, OneNote, and Apple Notes, but none really satisfied me, if I'm being honest. I've always wanted something simple, without any over-complication, and either free or cost-effective. Although, I have to admit, at the moment, I'm using an app called 'Bear Notes,' which costs around £2 per month, and I love the app. It's so minimalist and very user-friendly, but it doesn't have a web GUI or an app for Windows. I'm an Apple user, so it's not a big issue.
That being said, I recently stumbled upon another great self-hosted note-taking app called 'Memos' I just couldn't believe that I didn't know about this until very recently. It's so minimalist and has a Twitter-like feed where you can just chuck on any note, links, or even attachments.

Memos Installation
If you already have Docker installed, the installation will take just a few seconds. You can use either docker run or docker-compose.
docker run -d \
--init \
--name memos \
--publish 5230:5230 \
--volume ~/.memos/:/var/opt/memos \
neosmemo/memos:stableservices:
memos:
image: neosmemo/memos:stable
container_name: memos
volumes:
- ~/.memos/:/var/opt/memos
ports:
- 5230:5230In the Docker configuration for Continue reading
TL005: Navigating the Practical and Emotional Challenges of Tech Layoffs
Layoffs are a sensitive topic in the tech industry. Host Laura Santamaria discusses the emotional and practical impacts on employees and leaders. She also covers the signs of potential layoffs, and strategies for job searching post-layoff while maintaining perspective. She concludes with a tips for leaders to more effectively lead their teams through a layoff.... Read more »CJ Desai: Why I joined Cloudflare as President of Product and Engineering
I am thrilled to embark on this journey to run Product and Engineering at Cloudflare, driving forward the mission of helping build a better Internet.
While I was a graduate student at University of Illinois, the university introduced the Mosaic web browser to students. In addition to being super easy to install and use, it displayed pictures next to text for the first time. This may not seem impressive today, but back then it felt like a magical step forward.
This simple but powerful upgrade opened up the once niche user base from academics to the masses, transforming the world wide web to become an Internet phenomenon. Since then, I’ve always sought to be part of teams that worked on transformational technologies, including Software-as-a-Service, cloud computing, and AI. Innovation is the life blood of every technology company. To this day, I’m inspired by building products and technology that get adopted at mass scale.
The world is in a very interesting moment for technological innovation: the AI landscape is uncharted and developing at an exponential rate; the urgency for enterprises to reduce tech debt and reliance on legacy applications is at an all Continue reading
What’s new in Cloudflare One: Digital Experience (DEX) monitoring notifications and seamless access to Cloudflare Gateway with China Express
At Cloudflare, we are constantly innovating and launching new features and capabilities across our product portfolio. We are introducing roundup blog posts to ensure that you never miss the latest updates across our platform. In this post, we are excited to share two new ways that our customers can continue to keep their web properties performant and secure with Cloudflare One: new Digital Experience Monitoring (DEX) notifications help proactively identify issues that can affect the end-user digital experience, and integration with China Express enables secure access to China-hosted sites for Cloudflare Gateway customers.

As with other notification types, DEX notifications can be configured and reviewed from Cloudflare dashboard notifications.
DEX notifications address the challenge of proactively identifying issues affecting the digital experience of your end users. By monitoring device health and conducting synthetic tests from WARP clients deployed on your fleet's end-user devices, DEX provides valuable insights. These notifications empower IT administrators to quickly identify and address connectivity and application performance problems before they impact a wide range of users.
By proactively notifying administrators when problems arise, DEX helps minimize user disruption and provides Continue reading
CJ Desai: Why I joined Cloudflare as President of Product and Engineering
I am thrilled to embark on this journey to run Product and Engineering at Cloudflare, driving forward the mission of helping build a better Internet.
While I was a graduate student at University of Illinois, the university introduced the Mosaic web browser to students. In addition to being super easy to install and use, it displayed pictures next to text for the first time. This may not seem impressive today, but back then it felt like a magical step forward.
This simple but powerful upgrade opened up the once niche user base from academics to the masses, transforming the world wide web to become an Internet phenomenon. Since then, I’ve always sought to be part of teams that worked on transformational technologies, including Software-as-a-Service, cloud computing, and AI. Innovation is the life blood of every technology company. To this day, I’m inspired by building products and technology that get adopted at mass scale.
The world is in a very interesting moment for technological innovation: the AI landscape is uncharted and developing at an exponential rate; the urgency for enterprises to reduce tech debt and reliance on legacy applications is at an all time Continue reading
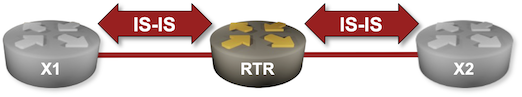
IS-IS Labs: Explore IS-IS Data Structures
In the first exercise in the IS-IS labs series, you configured IS-IS routing for IPv4. Before moving on to more complex topics, let’s explore the data structures IS-IS created to represent your network.
Setting up Active Directory for ISE Lab
A key component of an ISE home lab is having Active Directory installed. In this post I’ll go through setting up basic AD for use with ISE. This post is not going to cover licensing. I’m assuming you are running the eval version, which is good for 180 days, or that you already have a valid license.
My server is running in an ESX environment based on the following specs:
- OS – Windows Server 2022
- CPU – 4 vCPU
- RAM – 16 GB
- Disk – 90 GB
I’m using more than the minimum requirements. Spec it as you like based on what capacity you have available.
The first step is installing the OS. This part is easy and pretty much only requires you to set an Administrator password.
When the server has booted, start by changing the name of the server. It’s better to do this before changing any roles. Go to System Settings -> Computer Name and click Change… Set the desired name. I’m using the name dc01 in my lab. Click OK.

Changing the name is going to trigger a restart. Choose Restart Now.
From Server Manager, click Add roles and features. Click Next until you get to Continue reading
What’s new in Cloudflare One: Digital Experience (DEX) monitoring notifications and seamless access to Cloudflare Gateway with China Express
At Cloudflare, we are constantly innovating and launching new features and capabilities across our product portfolio. We are introducing roundup blog posts to ensure that you never miss the latest updates across our platform. In this post, we are excited to share two new ways that our customers can continue to keep their web properties performant and secure with Cloudflare One: new Digital Experience Monitoring (DEX) notifications help proactively identify issues that can affect the end-user digital experience, and integration with China Express enables secure access to China-hosted sites for Cloudflare Gateway customers.

Digital Experience Monitoring (DEX) offers device, application, and network performance monitoring, providing IT administrators with insights to quickly identify and resolve issues. With DEX notifications , account administrators can create configurable alert rules based on available algorithms (z-score, SLO) and existing DEX filters. When notification criteria are satisfied, customers are notified via email, Pagerduty, or Webhooks
As with other notification types, DEX notifications can be configured and reviewed from Cloudflare dashboard notifications.
DEX notifications address the challenge of proactively identifying issues affecting the digital experience of your end users. Continue reading
NAN075: Mastering Networking in the Age of AI: Advice for Aspiring Engineers
Ivan Pepelnjak joins host Eric Chou to reflect on his extensive career, his decision to reduce his content creation, and offer advice for young engineers. They discuss the evolution of networking technologies, emphasizing the importance of mastering Linux and obtaining relevant certifications. Ivan highlights the significance of creating professional visibility and owning one’s content. The... Read more »Improving platform resilience at Cloudflare through automation
Failure is an expected state in production systems, and no predictable failure of either software or hardware components should result in a negative experience for users. The exact failure mode may vary, but certain remediation steps must be taken after detection. A common example is when an error occurs on a server, rendering it unfit for production workloads, and requiring action to recover.
When operating at Cloudflare’s scale, it is important to ensure that our platform is able to recover from faults seamlessly. It can be tempting to rely on the expertise of world-class engineers to remediate these faults, but this would be manual, repetitive, unlikely to produce enduring value, and not scaling. In one word: toil; not a viable solution at our scale and rate of growth.
In this post we discuss how we built the foundations to enable a more scalable future, and what problems it has immediately allowed us to solve.
The Cloudflare Site Reliability Engineering (SRE) team builds and manages the platform that helps product teams deliver our extensive suite of offerings to customers. One important component of this platform is the collection of servers that power critical products such as Durable Objects, Workers, Continue reading
Cisco U – Rev Up to Recert: Programming for Network Engineer

I just completed the Programming for Network Engineers (PRNE) learning path training on Cisco U and would like to share this with you: For a limited time, you have FREE…
The post Cisco U – Rev Up to Recert: Programming for Network Engineer appeared first on AboutNetworks.net.

