NeoPhotonics Lights Up 400G Transceiver Customer Trials
NeoPhotonics claims its 400-GB/s capable transceivers are the first to deliver 32 terabits of...
Cisco Patches More ‘Critical’ DCNM Flaws
The latest vulnerabilities are in the Data Center Network Manager authentication mechanism and...
Open Storage Lifts Off With Cumulus, HPE Partnership
The partnership makes Cumulus Linux operating system and NetQ performance monitoring available on...
Will Dell Technologies Fetch $3B for RSA?
Dell acquired the cybersecurity software company when it bought EMC in 2016. Since then it has...
The Week in Internet News: New Chinese Law Regulates Encryption

Crypto-regulation: A new law in China regulates the use of encryption, but it’s aimed at strengthening it, at least in some settings, Reuters reports. The law is aimed at aiding the development of a digital currency in China, and it is focused on “facilitating the development of the cryptography business and ensuring the security of cyberspace and information,” according to the official Xinhua news agency said. The law also that all state secrets be stored and transmitted using “core and common” encryption, Engadget says.
Build your own: Some rural Colorado communities are tired of waiting for large broadband providers to bring them service and are seeking grants or forming partnerships to build their own networks, the Canon City Daily Record says. Grants from the state at the Federal Communications Commission are helping communities build fiber networks.
Not so secure: Wyze Labs, the maker of a line of IoT-connected security cameras, has announced a data breach affecting 2.4 million customers. The breach included WiFi network details and customer email addresses, Salon reports. The security cameras don’t appear to be compromised, but compromised email addresses can lead to further customer data breaches, the story notes. Also, there’s this: “The blog Twelve Security Continue reading
Review: Webinars in 2019
A year ago I wrote about ipSpace.net plans for 2019. While we created over 50 hours of webinar content and over 20 hours of course content in 2019, let’s see how well we delivered on my promises.
Following AWS Networking webinar, we’ll do a similar one on Azure (in early autumn 2019) and GCP (late 2019 or early 2020)
Azure: done. GCP: postponed. Let’s see how serious Google is about that particular project.
Read more ...Headcount: Firings, Hirings, and Retirings — December 2019
Juniper CTO Bikash Koley calls it quits; Larry Ellison says Oracle will not replace Hurd; plus the...
Cisco Champion 2020
Dear friend,
I hope you have a relaxing holiday period and now you are ready to kick off the new year. For us year has already started 2 days ago…
… With announcement that our blog is chosen to be Cisco Champion in 2020. We are very delightful to be a Cisco Champion two times in a row (2019 and 2020). Thank you very much for supporting us, for your interest and your questions.
The good news for you is that the application is yet opened for a couple of days, so you can try to apply yourself.
Discalimer
If you even more interested in your future, join our network automation training we start on 18th and 22nd of January, where we cover the details of the data modelling, NETCONF/YANG, REST API, Python and Ansible in the multivendor environment with Cisco, Nokia, Arista and Cumulus Linux as network functions.

Support us
Configuration Creation with Nornir
I tend to assess automation tools in four different contexts which is, in fact, a very general networking and automation workflow: Discovery How easy is it to find out about the network, document its configuration (the configuration of a device itself) and state (show commands "snapshotting" its state)? Configuration Creation How easy is it to READ MORE
The post Configuration Creation with Nornir appeared first on The Gratuitous Arp.
Nornir – A New Network Automation Framework
nornir (formerly brigade) - A new network automation framework Before getting started, let me say that I'm big fan of Ansible. It is one of my go-to automation frameworks. Having said that, there have been use cases where I've run into some of the limitations of Ansible and to be fair some of those limitations may READ MORE
The post Nornir – A New Network Automation Framework appeared first on The Gratuitous Arp.
Cloudflare Expanded to 200 Cities in 2019
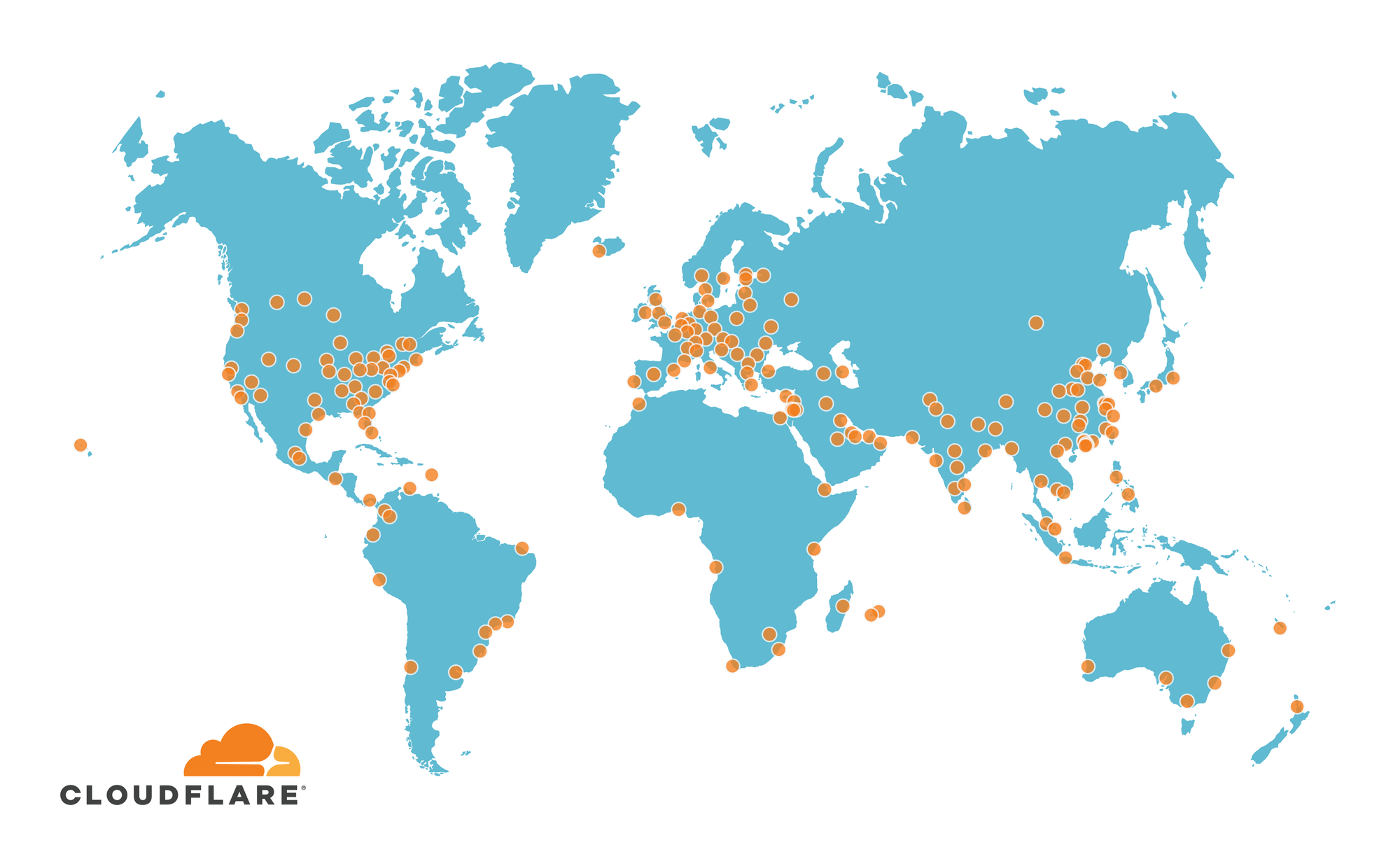
We have exciting news: Cloudflare closed out the decade by reaching our 200th city* across 90+ countries. Each new location increases the security, performance, and reliability of the 20-million-plus Internet properties on our network. Over the last quarter, we turned up seven data centers spanning from Chattogram, Bangladesh all the way to the Hawaiian Islands:
- Chattogram & Dhaka, Bangladesh. These data centers are our first in Bangladesh, ensuring that its 161 million residents will have a better experience on our network.
- Honolulu, Hawaii, USA. Honolulu is one of the most remote cities in the world; with our Honolulu data center up and running, Hawaiian visitors can be served 2,400 miles closer than ever before! Hawaii is a hub for many submarine cables in the Pacific, meaning that some Pacific Islands will also see significant improvements.
- Adelaide, Australia. Our 7th Australasian data center can be found “down under” in the capital of South Australia. Despite being Australia’s fifth-largest city, Adelaide is often overlooked for Australian interconnection. We, for one, are happy to establish a presence in it and its unique UTC+9:30 time zone!
- Thimphu, Bhutan. Bhutan is the seventh SAARC (South Asian Association for Regional Cooperation) country Continue reading
Worth Reading: Understanding Scale Computing HC3 Edge Fabric
A long while ago someone told me about a "great" idea of using multi-port server NICs to build ad-hoc (or hypercube or whatever) server-only networks. It's pretty easy to prove that the approach doesn't make sense if you try to build generic any-to-any-connectivity infrastructure... but it makes perfect sense in a small environment.
One can only hope Scale Computing keeps their marketing closer to reality than some major vendors (that I will not name because I'm sick-and-tired of emails from their employees telling me how I'm unjustly picking on the stupidities their marketing is evangelizing) and will not start selling this approach as save-the-world panacea... but we can be pretty sure there will be people out there using it in way-too-large environments, and then blame everything else but their own ignorance or stubbornness when the whole thing explodes into their faces.
Fourth Annual inSIG Boosts India’s Capacity to Shape the Internet’s Future

Earlier this month, the fourth India School on Internet Governance (inSIG2019) was held in Kolkata on 15-17 November, expanding its network of leaders and professionals active in shaping the Internet’s future.
With support from sponsors, 50 fellows from various academic, cultural, and regional backgrounds participated in inSIG2019. Through panel discussions, workshops, role plays, and group activities the three-day school covered a myriad of topics related to the Internet, boosting participants’ understanding of the complexity of Internet Governance and its importance in the future of the Internet.
The sessions covered fundamental topics like the history, principles, and status of the Internet. The hurdles around online safety, human rights, online radicalization, and cybersecurity were extensively examined and many perspectives were brought out which were thought-provoking and ingenious. Status and challenges of emerging technologies, content regulation, and the multilingual Internet were also discussed widely, and valuable feedback and inputs were provided by the participants.
The importance of the multistakeholder model of Internet Governance was stressed upon, and the Dutch approach to Internet Governance was presented in which Arnold van Rhijn spoke about how a collaborative consultation with multiple stakeholders reduces future friction in policymaking.
The event had global experts from Internet-related Continue reading
Inspur’s Edge Servers Boast Nvidia EGX, NGC-Ready Certification
Inspur's Nvidia EGX-based NE5260M5 edge server is already being deployed by the China Mobile...
AT&T Misses Network Virtualization Goal
“We aim to control 75% of our core network functions with software by the end of 2020 and, by...