Tech Bytes: Implementing Sensible Network Segmentation With Tufin (Sponsored)
Today's Tech Bytes podcast looks at how to implement sensible network segmentation to ensure compliance with security policies and accelerate business agility. Tufin is our sponsor, and we speak with guest Sagi Bar-Zvi, Strategic Pre-Sales Manager at Tufin.
The post Tech Bytes: Implementing Sensible Network Segmentation With Tufin (Sponsored) appeared first on Packet Pushers.
Tech Bytes: Implementing Sensible Network Segmentation With Tufin (Sponsored)
Today's Tech Bytes podcast looks at how to implement sensible network segmentation to ensure compliance with security policies and accelerate business agility. Tufin is our sponsor, and we speak with guest Sagi Bar-Zvi, Strategic Pre-Sales Manager at Tufin.Heavy Networking 478: Leveraging LTE For SD-WAN With Cradlepoint (Sponsored)
Today's Heavy Networking show is sponsored by Cradlepoint, which provides wireless WAN networking. Our guest Marc Bresniker, VP of Product Management, joins us to discuss using LTE for WAN connections including IoT, and to explore the benefits of using Cradlepoint's LTE solutions as part of your SD-WAN strategy.
The post Heavy Networking 478: Leveraging LTE For SD-WAN With Cradlepoint (Sponsored) appeared first on Packet Pushers.
Network Break 256: Startup Forward Networks Nabs $35 Million; Vodafone Dials OpenRAN For Incumbent Alternatives
Today's Network Break podcast is chock full of inspirational cynicism. We cover fresh funding for Forward Networks, Vodafone trialing OpenRAN gear, SUSE closing the door on OpenStack, Extreme Networks shifting StackStorm to the Linux Foundation, and more tech news.
The post Network Break 256: Startup Forward Networks Nabs $35 Million; Vodafone Dials OpenRAN For Incumbent Alternatives appeared first on Packet Pushers.
Network Break 256: Startup Forward Networks Nabs $35 Million; Vodafone Dials OpenRAN For Incumbent Alternatives
Today's Network Break podcast is chock full of inspirational cynicism. We cover fresh funding for Forward Networks, Vodafone trialing OpenRAN gear, SUSE closing the door on OpenStack, Extreme Networks shifting StackStorm to the Linux Foundation, and more tech news.Forcepoint Web Security Footprint Spans 160 Global PoPs
The vendor rolled out its Web Security platform across 160 points of presence as it builds out a...
Toshiba Taps Cybera’s SD-WAN for Retail Terminals
Under the agreement, Cybera becomes Toshiba's preferred SD-WAN vendor in the Asia-Pacific...
Intel Snaps Up Smart Edge Amid 5G Push
The company is expanding into edge computing, which it estimates will be a $65 billion silicon...
Lenovo’s Charles Ferland Shares What’s in Store for SDN, NFV, and Telecoms
Hear from Lenovo's Charles Ferland as he dives into the company's latest ideas in telecom...
Overcoming the Barriers to Micro-segmentation
It should come as no surprise how much emphasis organizations place on security today. Threats are becoming more and more sophisticated and the number of threats grow to uncontrollable rates every day.
One of the biggest downsides is that the rising cost of data breaches in 2019 alone, a global average of $3.92 million as reported by the Ponemon Institute and IBM Security July 2019 report, is enough to cause organizations to rethink or increase emphasis on their security strategies and how they can help secure their most important assets by improving the cyber hygiene in their organizations.
What is Cyber Hygiene?
Cyber hygiene refers to what an organization can do to improve their security postures around physical hardware, software, and applications. If you’ve seen Pat Gelsinger’s keynote from 2017, he goes into the 5 pillars of good cyber hygiene and what organizations can do to improve basic and fundamental security for their business.
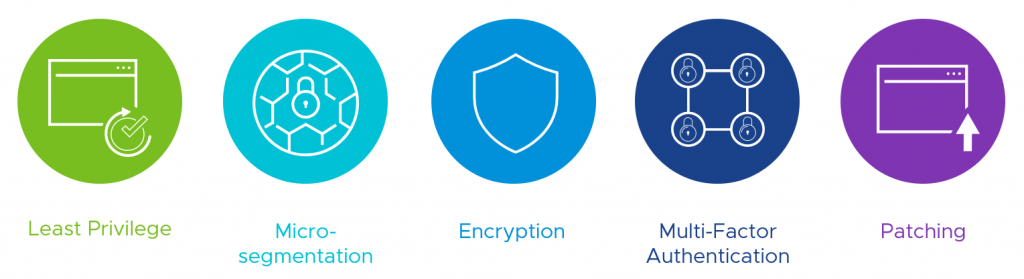
Over the last several years, VMware has been focusing on helping organizations move to Software-Defined Data Centers (SDDC) to improve their agility and meet the speed of business. As more organizations adopted the SDDC model, VMware found itself in a unique position Continue reading
Real Life Financial Network Design – Multicast – BGP – EIGRP – Latency Design Considerations
I was in London last week for CCDE Training. During the training, there was a discussion on Financial network design and one of the students explained how they designed their financial world-wide network. We recorded the discussion and I think you will get great benefit if you want to understand how financial networks are designed, …
The post Real Life Financial Network Design – Multicast – BGP – EIGRP – Latency Design Considerations appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
How Do You Provision a 500-Switch Network in a Few Days?
TL&DR: You automate the whole process. What else do you expect?
During the Tech Field Day Extra @ Cisco Live Europe 2019 we were taken on a behind-the-stage tour that included a chat with people who built the Cisco Live network, and of course I had to ask how they automated the whole thing. They said “well, we have the guy that wrote the whole system onsite and he’ll be able to tell you more”. Turns out the guy was my good friend Andrew Yourtchenko who graciously showed the system they built and explained the behind-the-scenes details.
Read more ...