VMware Cloud on AWS SDDC 1.7: New NSX Features
The latest version of VMware Cloud on AWS SDDC (SDDC Version 1.7) was released recently and is being rolled out to customers. In this post, I’ll discuss the new NSX Networking and Security features.
Looking at the features released in VMware Cloud on AWS SDDC 1.7 in the below diagram, we can see the features can be grouped into three categories: Connectivity, Services, and Operations. Further below I go into more detail in each of these specific NSX features. For a complete list of all new features in VMware Cloud on AWS SDDC 1.7 in general, check out the release notes here. Continue reading
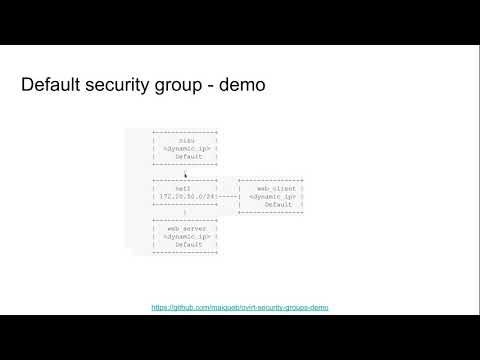
Security group support in OVN external networks
In this post I will introduce and showcase how security groups can be used to enable certain scenarios.
Security groups allow fine-grained access control to - and from - the oVirt VMs attached to external OVN networks.
The Networking API v2 defines security groups as a white list of rules - the user specifies in it which traffic is allowed. That means, that when the rule list is empty, neither incoming nor outgoing traffic is allowed (from the VMs perspective).
A demo recording of the security group feature can be found below.
Provided tools
This repo adds tools, and information on how to use them, to help manage the security groups in oVirt, since currently there is no supported mechanism to provision security groups, other than the REST API, and ManageIQ. ManageIQ also doesn't fully support security groups, since it lacks a way to attach security groups to logical ports.
Demo scenarios
In the following links you can also find playbooks that can be built upon to reach different types of scenarios.
Building Fabric Infrastructure for an OpenStack Private Cloud
An attendee in my Building Next-Generation Data Center online course was asked to deploy numerous relatively small OpenStack cloud instances and wanted select the optimum virtual networking technology. Not surprisingly, every $vendor had just the right answer, including Arista:
We’re considering moving from hypervisor-based overlays to ToR-based overlays using Arista’s CVX for approximately 2000 VLANs.
As I explained in Overlay Virtual Networking, Networking in Private and Public Clouds and Designing Private Cloud Infrastructure (plus several presentations) you have three options to implement virtual networking in private clouds:
Read more ...A Simple Virtual Network based on proxy ARP and Policy Based Routing
Introduction Choosing a Virtual networking to connect VMs or Containers across Hosts is always a complicated decision. Most of us would have found the virtual networking on a single VM/Container Host to be very simple, easy to implement and debug. Just plug the VM/Container to a bridge and your are done. For access from the … Continue reading A Simple Virtual Network based on proxy ARP and Policy Based RoutingSystem Monitoring: Glances at Top
System monitoring is one of the topics that has got a lot of attention lately. A lot of options already exists in the open but every-time I search a for a system monitoring tool I am presented with options suitable for large scale cluster of machines, capturing metrics over time, showing trends of resource utilization … Continue reading System Monitoring: Glances at TopNo surprise performance test
Recently I had a need to deploy some python FLASK based application. Although FLASK has a convenience CLI built-in to run your application while developing the deployment documentation provided a bunch of production ready deployment method. After going through the various documentation and learning about the event loop based implementation of Gevent, I decided to … Continue reading No surprise performance testAutomating NSX-T
An attendee of our Building Network Automation Solutions online course decided to automate his NSX-T environment and sent me this question:
I will be working on NSX-T quite a lot these days and I was wondering how could I automate my workflow (lab + production) to produce a certain consistency in my work.
I’ve seen that VMware relies a lot on PowerShell and I’ve haven’t invested a lot in that yet … and I would like to get more skills and become more proficient using Python right now.
Always select the most convenient tool for the job, and regardless of personal preferences PowerShell seems to be the one to use in this case.
Read more ...Test Driving transmission for multi-site file sync
As the industry moves towards more distributed deployment of services, syncing files across multiple location is a problem that often needs to be solved. In the world of file synching there are two algorithms that are outstanding. One being rsync which is a very efficient tool for synching files. It works great when you have … Continue reading Test Driving transmission for multi-site file syncCross-vCenter NSX at the Center for Advanced Public Safety
Jason Foster is an IT Manager at the Center for Advanced Public Safety at the University of Alabama. The Center for Advanced Public Safety (CAPS) originally developed a software that provided crash reporting and data analytics software for the State of Alabama. Today, CAPS specializes in custom software mostly in the realm of law enforcement and public safety. They have created systems for many states and government agencies across the country.
Bryan Salek, Networking and Security Staff Systems Engineer, spoke with Jason about network virtualization and what led the Center for Advanced Public Safety to choosing VMware NSX Data Center and what the future holds for their IT transformation.
The Need for Secure and Resilient Infrastructure
As part of a large modernize data center initiative, the forward-thinking CAPS IT team began to investigate micro-segmentation. Security is a primary focus at CAPS due to the fact that the organization develops large software packages for various state agencies. The applications that CAPS writes and builds are hosted together, but contain confidential information and need to be segmented from one another.
Once CAPS rolled out the micro-segmentation use-case, the IT team decided to leverage NSX Data Center for disaster recovery purposes as Continue reading
Making Performance A Priority With Virtualized GPUs
VMware is not the first company that comes to mind when you think of GPU computing, but the company has quietly been developing technologies that enables performance-minded users to get the most out of these born-again vector processors. …
Making Performance A Priority With Virtualized GPUs was written by Michael Feldman at .
High-Speed IPsec on Snabb Switch on Software Gone Wild
In previous Software Gone Wild episodes we covered Snabb Switch and numerous applications running on it, from L2VPN to 4over6 gateway and integration with Juniper vMX code.
In Episode 98 we focused on another interesting application developed by Max Rottenkolber: high-speed VPN gateway using IPsec on top of Snabb Switch (details). Enjoy!
Last Week on ipSpace.net (2019W4)
The crazy pace of webinar sessions continued last week. Howard Marks continued his deep dive into Hyper-Converged Infrastructure, this time focusing on go-to-market strategies, failure resiliency with replicas and local RAID, and the eternal debate (if you happen to be working for a certain $vendor) whether it’s better to run your HCI code in a VM and not in hypervisor kernel like your competitor does. He concluded with the description of what major players (VMware VSAN, Nutanix and HPE Simplivity) do.
On Thursday I started my Ansible 2.7 Updates saga, describing how network_cli plugin works, how they implemented generic CLI modules, how to use SSH keys or usernames and passwords for authentication (and how to make them secure), and how to execute commands on network devices (including an introduction into the gory details of parsing text outputs, JSON or XML).
The last thing I managed to cover was the cli_command module and how you can use it to execute any command on a network device… and then I ran out of time. We’ll continue with sample playbooks and network device configurations on February 12th.
You can get access to both webinars with Standard ipSpace.net subscription.
Federate oVirt engine authentication to OpenID Connect infrastructure
In this post I will introduce how to integrate OIDC with oVirt engine using Keycloak and LDAP user federation.
Prerequisites: I assume you have already setup the 389ds directory server, but the solution is very similar for any other LDAP provider.
As OIDC is not integrated into oVirt directly, we use Apache to do the OIDC authentication for us. The mod_auth_openidc module nicely covers all needed functionality.
Overview
Integrate with external OpenID Connect Identity Provider (IDP) to provide Single Sign-On (SSO) across products that use the IDP for authenticating users. We currently have oVirt SSO for providing unified authentication across Administrator and VM portals. The oVirt engine SSO also provides tokens for REST API clients and supports bearer authentication to reuse tokens to access oVirt engine RESTAPI. With external IDP integration the internal oVirt SSO is disabled and browser users will be redirected to the external IDP for authentication. After successful authentication users can access both Admin and VM portals as they normally do. REST API clients don't have to change, they can still obtain a token from engine SSO and use the token for bearer authentication to access oVirt engine RESTAPI. Engine SSO acts as a proxy obtaining the Continue reading
oVirt and OKD
This is a series of posts to demonstrate how to install OKD 3.11 on oVirt and what you can do with it. Part I - How to install OKD 3.11 on oVirt

How to install OKD 3.11 on oVirt (4.2 and up)
Installing OKD or Kubernetes on oVirt has many advantages, and it's also gotten a lot easier these days. Admins and users who want to take container platform management for a spin, on oVirt, will be encouraged by this.
Few of the advantages are:
- Virtualizing the control plane for Kubernetes - provide HA/backup/affinity capabilities to the controllers and allowing hardware maintenance cycles
- Providing persistent volume for containers via the IAAS, without the need for additional storage array dedicated to Kubernetes
- Allowing a quick method to build up/tear down Kubernetes clusters, providing hard tenancy model via VMs between clusters.
The installation uses openshift-ansible and, specifically the openshift_ovirt ansible-role. The integration between OpenShift and oVirt is tighter, and provides storage integration. If you need persistent volumes for your containers you can get that directly from oVirt using ovirt-volume-provisioner and ovirt-flexvolume-driver.
For the sake of simplicity, this example will cover an all-in-one OpenShift cluster, on a single VM.
Continue reading
Extending my Private Lab behind NAT to AWS
WordPress on EC2 with DB in private LAN We have all known and talked about a hybrid cloud solution to spill over an On-Prem infrastructure to cloud providers like AWS. Recently I had a need to do (a POC that needed) the same for my private lab where part of my software runs on the … Continue reading Extending my Private Lab behind NAT to AWSVMworld 2018 Europe Sessions on NSX Networking and Security in VMware Cloud on AWS
VMworld 2018 Europe in Barcelona is a week away. Want to learn more about NSX Networking and Security in VMware Cloud on AWS, how you can easily deploy and secure workloads in the cloud, or how to build hybrid cloud solutions with the familiarity and capabilities of vSphere? Make sure to attend the below sessions at VMworld 2018 Europe next week. We will go into a deep dive of all the functionality and show how VMware Cloud on AWS is being used by customers. Continue reading
VMware NSX: The Good, the Bad and the Ugly
After four live sessions we finished the VMware NSX Technical Deep Dive webinar yesterday. Still have to edit the materials, but right now the whole thing is already over 6 hours long, and there are two more guest speaker sessions to come.
Anyways, in the previous sessions we covered all the good parts of NSX and a few of the bad ones. Everything that was left for yesterday were the ugly parts.
Read more ...Test Driving Inter Regional VPC peering in AWS
Connect AWS VPCs hosted in different regions. AWS Virtual Private Cloud(VPC) provides a way to isolate a tenant’s cloud infrastructure. To a tenant a VPCs provide a view of his own virtual infrastructure in the cloud that is completely isolated, has its own compute, storage, network connectivity, security settings etc. In the physical world, Amazon’s … Continue reading Test Driving Inter Regional VPC peering in AWSCustom VPC and Internet Access in AWS
Create your VPC, launch EC2 instances and get internet access with Public IP. With a Virtual Private Cloud(VPC), tenants can create his own cloud based infrastructure in AWS. While AWS provides a default VPC for a new tenant, there are always use cases that need creation of custom VPC. While exploring custom VPC, I found … Continue reading Custom VPC and Internet Access in AWSVXLAN and EVPN on Hypervisor Hosts
One of my readers sent me a series of questions regarding a new cloud deployment where the cloud implementers want to run VXLAN and EVPN on the hypervisor hosts:
I am currently working on a leaf-and-spine VXLAN+ EVPN PoC. At the same time, the systems team in my company is working on building a Cloudstack platform and are insisting on using VXLAN on the compute node even to the point of using BGP for inter-VXLAN traffic on the nodes.
Using VXLAN (or GRE) encap/decap on the hypervisor hosts is nothing new. That’s how NSX and many OpenStack implementations work.
Read more ...