Ampere Targets Intel, AMD With Cloud-First Chips, Oracle Partnership
Oracle, which holds a $40 million stake in Ampere, has announced plans to leverage the Altra...
Oracle, which holds a $40 million stake in Ampere, has announced plans to leverage the Altra...
Today, Cumulus Networks is announcing the release of its production-ready automation solution for organizations moving towards fully automated networks in order to take advantage of infrastructure-as-code deployment models.
At the forefront of the networking industry, we see our customers caught in the shifting tides as the modern data center moves toward fully automated networking. As they look to take advantage of innovative technology like 5G, cloud, IoT and more, organizations are looking to innovative networking deployments that incorporate new ways of thinking about automation like infrastructure-as-code, CI/CD and more. As network traffic continues to grow at an exponential rate, organizations are left with infrastructure that is harder to manage and deploy. Bogged down by the cost and time it takes to build out bits and pieces of fully automated solutions, these organizations are in need of a solution to help them innovate their networks at the speed business demands.
Cumulus is now offering the first open source, out-of-the-box, robust, end-to-end automated configuration and testing solution using Ansible. Customers no longer have to piece together their network automation from disparate and untested scripts and proof-of-concept playbooks. Cumulus is offering a framework for an elegant push-button solution for those looking for cutting-edge Continue reading
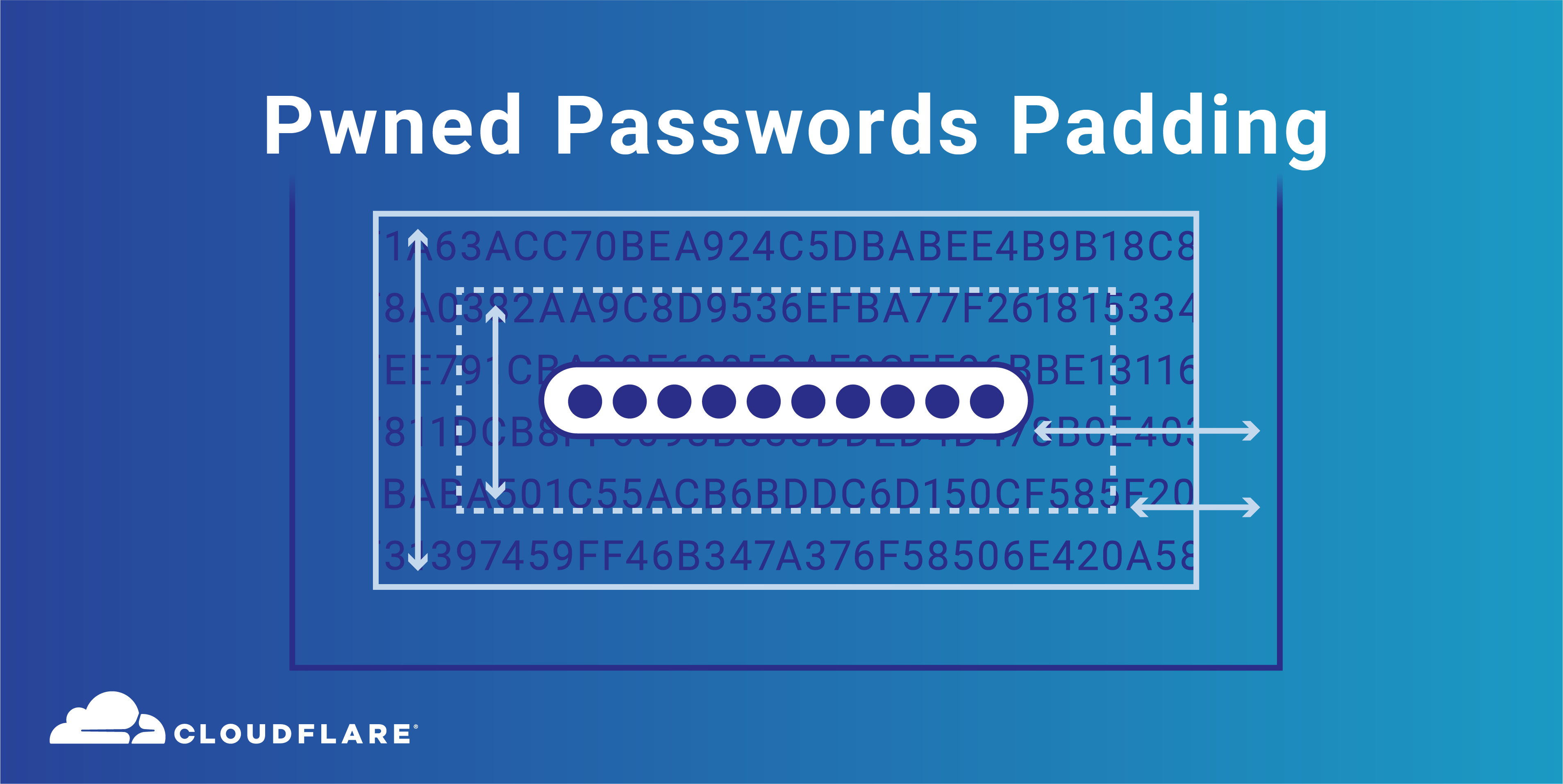
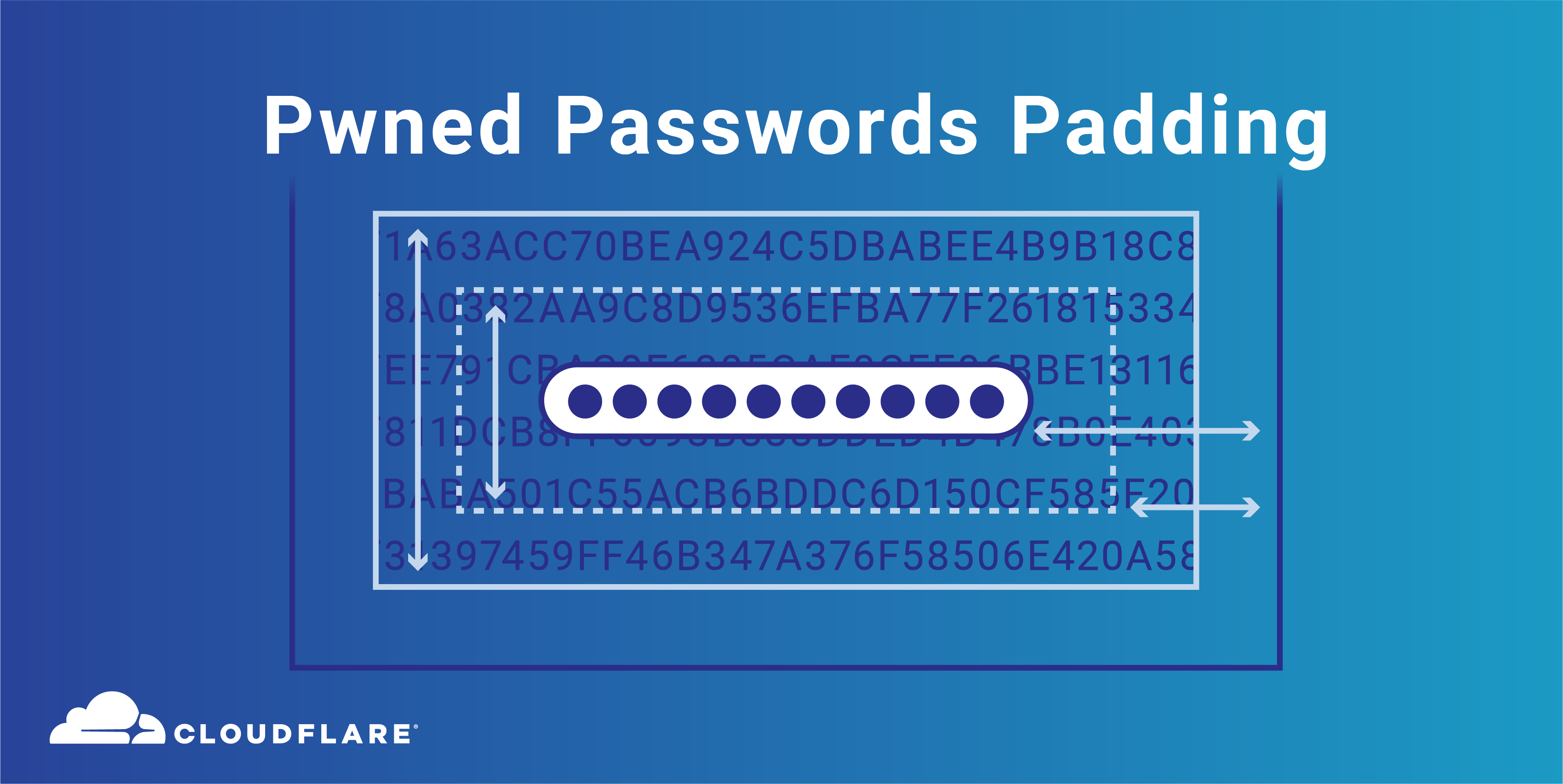
The Pwned Passwords API (part of Troy Hunt’s Have I Been Pwned service) is used tens of millions of times each day, to alert users if their credentials are breached in a variety of online services, browser extensions and applications. Using Cloudflare, the API cached around 99% of requests, making it very efficient to run.
From today, we are offering a new security advancement in the Pwned Passwords API - API clients can receive responses padded with random data. This exists to effectively protect from any potential attack vectors which seek to use passive analysis of the size of API responses to identify which anonymised bucket a user is querying. I am hugely grateful to security researcher Matt Weir who I met at PasswordsCon in Stockholm and has explored proof-of-concept analysis of unpadded API responses in Pwned Passwords and has driven some of the work to consider the addition of padded responses.
Now, by passing a header of “Add-Padding” with a value of “true”, Pwned Passwords API users are able to request padded API responses (to a minimum of 800 entries with additional padding of a further 0-200 entries). The padding consists of randomly generated hash suffixes with the usage Continue reading
On 27 February 2020, I took and passed the Cisco Certified DevNet Professional Core (DEVCOR) exam on my first attempt. For those who like to memorize dates, yes, I did pass DEVASC and DEVCOR on the same day to cut down on trips to the test center. Like DEVASC, this exam was fair and all blueprint topics were appropriately represented. You can read about my DEVASC blog here (provide link to other blog).
I want to focus on what I did to succeed and less about the exam structure itself. You can learn more about the official certification here. This blog is focused primarily on the DEVCOR exam. Before talking about the exam, just know that you need to pass the core exam plus one concentration exam to earn the Cisco Certified DevNet Professional certification. I also passed the ENAUTO exam, which focuses on enterprise network automation. I’ll write about it in “part 2” later.
Before attempting this certification, you should already have a DevNet Associate certification (not required) or comparable knowledge, plus at least 3 years of software development/automation experience. The DEVCOR exam was no joke. It was harder than the CCIE RS and SP written exams, and about Continue reading
AI is the new SDN, and we’re constantly bombarded with networking vendor announcements promising AI-induced nirvana, from reinventing Clippy to automatic anomaly- and threat identifications.
If you still think these claims are realistic, it’s time you start reading what people involved in AI/ML have to say about hype in their field. I posted a few links in the past, and the Packet Pushers Human Infrastructure magazine delivered another goodie into my Inbox.
You REALLY SHOULD read the original article, here’s the TL&DR summary for differently-attentive:
AI is the new SDN, and we’re constantly bombarded with networking vendor announcements promising AI-induced nirvana, from reinventing Clippy to automatic anomaly- and threat identifications.
If you still think these claims are realistic, it’s time you start reading what people involved in AI/ML have to say about hype in their field. I posted a few links in the past, and the Packet Pushers Human Infrastructure magazine delivered another goodie into my Inbox.
You REALLY SHOULD read the original article, here’s the TL&DR summary for differently-attentive:
Read more ...Millions of tiny databases, Brooker et al., NSDI’20
This paper is a real joy to read. It takes you through the thinking processes and engineering practices behind the design of a key part of the control plane for AWS Elastic Block Storage (EBS): the Physalia database that stores configuration information.
In the same spirit as Paxos Made Live, this paper describes the details, choices and tradeoffs that are required to put a consensus system into production.
The core algorithms (chain-replication, Paxos-based consensus) aren’t the stars of the show here, instead the paper focuses on how these algorithms are deployed, and the software engineering practices behind the creation of a mission-critical production system employing them.
Engineering decisions involve making lots of trade-offs. If you want to emerge with a coherent design, then it’s well worth spending some time thinking about the principle(s) by which you’re going to make them. For Physalia, and for AWS more generally, the guiding principle is minimise the blast radius.
Over the decade since [the introduction of Availability Zones], our thinking on failure and availability has continued to evolve, and we paid increasing attention to blast radius and correlation of failure. Continue reading

Routing is the foundation of every IP network. Even a router as small as the one in your home has a routing table and makes routing decisions.
Selecting a routing architecture is a critical but often overlooked step to ensure that a startup WISP can provide the necessary performance, scalability and resiliency to its subscribers.
This post will go through each the major design types and highlight pros/cons and when it is appropriate to use a particular routing architecture.
A note on IPv6
Dual stack is assumed in all of the designs presented. The cost of IPv4 public will continue to climb.
It’s no longer a scalable option in 2020 to build an ISP network without at least a plan for IPv6 and ideally a production implementation.
“Behind the L3 boundary, there be L2 dragons”
-ancient network proverb
Unfortunately, this is often the worst choice for all but the smallest WISPs that don’t have any plans to scale beyond 1 to 100 subscribers.
Bridged networks with one or more subnets in the same L2 broadcast domain are the most commonly deployed routing design that Continue reading
As the hyperscalers and cloud builders go, so goes the enterprise. …
A Flare For SmartNICs was written by Timothy Prickett Morgan at The Next Platform.
We are excited to announce the general availability of Calico Enterprise 2.7. With this release, Fortinet’s 400,000 customers can use FortiGate to enforce network security policies into and out of the Kubernetes cluster as well as traffic between pods within the cluster.

We have also added many new exciting capabilities that help platform engineers blow through barriers blocking their path to production, and advanced cybersecurity capabilities for those already running production workloads.
As the adoption of Kubernetes continues to accelerate, our customers are seeing the number of clusters in their environments rapidly multiplying. This has created a management challenge for IT Ops teams who are constantly pushed to find ways Continue reading


I am delighted to share that I have joined Cloudflare as its first Chief Information Officer to help scale the company in this new phase of its business. It’s an incredibly exciting time to be joining Cloudflare, and I am grateful for the opportunity to do my part to help build a better Internet.
At one of my previous companies, I made a bet on Cloudflare to equip us with security and performance solutions across a very decentralized global set of products and services. This is something that would have been very difficult without a cloud solution like Cloudflare’s. Since then I’ve been watching Cloudflare grow, and have always been very impressed by the speed of innovation and transparency, but also how Cloudflare operates: doing the right thing, with integrity, and above all building trust with customers and partners. The “do the right thing, even if it’s hard” mentality that I saw from Cloudflare since I started doing business with them as a customer, was key for me. When I heard that Cloudflare was looking for its first CIO I was excited to have a discussion to see if I could help.
During the interview process I got a sense Continue reading
Coronavirus canceled more tech events; Equinix paid $335 million for Packet; and Rakuten Mobile...
Security professionals tend to be at least a moderately paranoid bunch, and adding a real virus to...
Xilinx claims its smartNIC will allow customers to offload 90% of Open vSwitch processing from the...
At this point in the history of information technology, there is no way to introduce a new processor that does not appeal to the hyperscalers and cloud builders. …
Ampere Aims For The Clouds With Altra Arm Server Chip was written by Timothy Prickett Morgan at The Next Platform.
The open RAN framework is 40% cheaper than traditional telecommunication infrastructure, according...
The company is moving the event to an all-digital experience, and there will not be any keynotes or...
