Sprint Looks Back on Another Ugly Quarter
Sprint’s debt continues to worsen — it grew by almost by almost 3.9% in 2019, and the operator...
Sprint’s debt continues to worsen — it grew by almost by almost 3.9% in 2019, and the operator...

Join us as we chant the mystic container prayers
The post Dictionary: Church of Kubernology appeared first on EtherealMind.
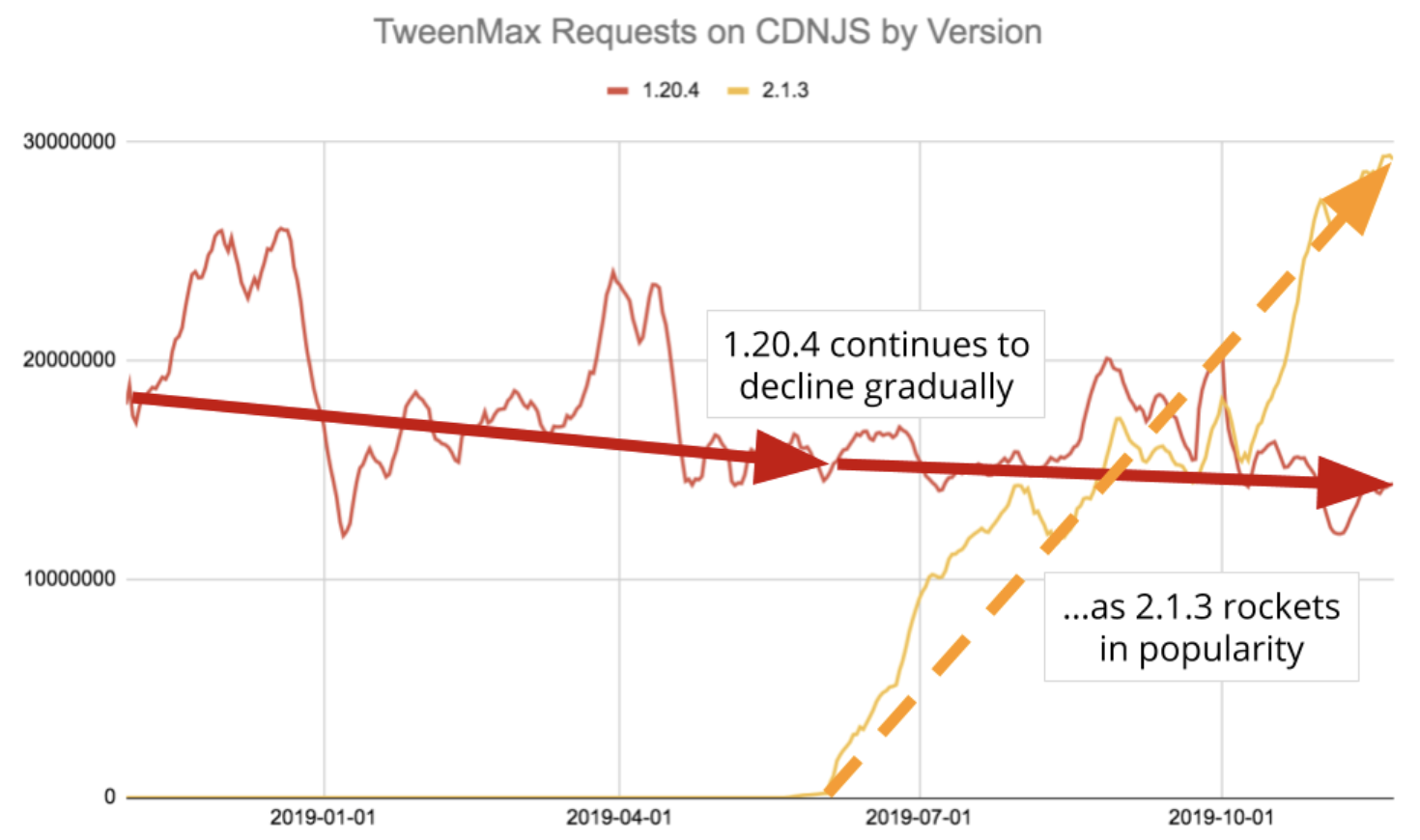
Cloudflare helps run CDNJS, a very popular way of including JavaScript and other frontend resources on web pages. With the CDNJS team’s permission we collect anonymized and aggregated data from CDNJS requests which we use to understand how people build on the Internet. Our analysis today is focused on one question: once installed on a site, do JavaScript libraries ever get updated?
Let’s consider jQuery, the most popular JavaScript library on Earth. This chart shows the number of requests made for a selected list of jQuery versions over the past 12 months:
Spikes in the CDNJS data as you see with version 3.3.1 are not uncommon as very large sites add and remove CDNJS script tags.
We see a steady rise of version 3.4.1 following its release on May 2nd, 2019. What we don’t see is a substantial decline of old versions. Version 3.2.1 shows an average popularity of 36M requests at the beginning of our sample, and 29M at the end, a decline of approximately 20%. This aligns with a corpus of research which shows the average website lasts somewhere between two and four years. What we don’t see is a decline Continue reading
Today's Network Break dives into VMware's Nyansa acquisition, the implications of 3G's expiration date, Microsoft's plans to insert Bing as the default search engine in Chrome browsers for an upcoming Office 365 release, financial results from Intel and IBM, and more.
The post Network Break 268: VMware Acquires Nyansa; Microsoft Plans To Hijack O365 Browser Search appeared first on Packet Pushers.
I recently attended a webinar where the speaker made this comment and it started me thinking about testing in general and what some of the challenges that can present.
We all know that we should be testing, but there are a lot of potential pit falls that one can fall into when starting down this journey. I’m going to jump into the deep end of the pool here and deal with one of the struggles that it took me a while to deal with.
Imagine the following:
And now your GITHUB badges all show red and no one trusts your code. Which brings us to vcrpy
Wow! So glad you asked! vcrpy is a REST Continue reading
Europe is trailing the other major HPC powers in its quest to field exascale supercomputers. …
European Processor Initiative Readies Prototype was written by Michael Feldman at The Next Platform.
Storage systems are inherently data intensive. But the rapid emergence of artificial intelligence as a standard datacenter workload has storage vendors scrambling to design platforms that better meet the more stringent performance needs of these applications. …
AI Is Driving Storage Down New Avenues was written by Nicole Hemsoth at The Next Platform.

Under pressure: Apple has scrapped plans to allow iPhone users to fully encrypt backups of their devices in iCloud after the U.S. FBI complained it would hinder investigations, Reuters reports. About two years ago, Apple told the FBI that it planned to offer users end-to-end encryption when storing their phone data on iCloud, but its plans seem to have changed. Meanwhile, U.S. Attorney General William Barr and President Donald Trump have continued their pressure for tech vendors to build backdoors in encrypted devices, Politico says.
One high-profile phone: Two United Nations rights experts have accused Saudi Arabia of hacking the phone owned by Jeff Bezos, founder of Amazon.com and owner of the Washington Post, the New York Times says. The hack appears to be an attempt to influence the Post’s coverage of the kingdom, the U.N. people say. The hack of Bezos’ phone appears to have bypassed encryption through spyware, adds a Fortune story.
If it’s good for smartphones: Swiss cryptography firm Teserakt has introduced E4, “a sort of cryptographic implant that Internet of Things manufacturers can integrate into their servers,” Wired reports. The open source tool aims to be a comprehensive encryption solution for IoT.
Sundar Pichai, CEO of Google and parent company Alphabet, generated a lot of buzz recently with an op-ed he wrote for the The Financial Times calling for greater regulation of artificial intelligence (AI) technologies, adding a high-profile voice into a debate that has been simmering as innovation around AI, machine learning and deep learning have advanced rapidly. …
The Debate Over Regulating AI Ramps Up was written by Jeffrey Burt at The Next Platform.
One of the most productive meetings I had KubeCon in San Diego last November was a meeting with Docker, Amazon and Microsoft to plan a collaboration around a new version of the CNCF project Notary. We held the Notary v2 kickoff meeting a few weeks later in Seattle in the Amazon offices.
Emphasising that this is a cross-industry collaboration, we had eighteen people in the room (with more dialed in) from Amazon, Microsoft, Docker, IBM, Google, Red Hat, Sylabs and JFrog. This represented all the container registry providers and developers, other than the VMware Harbor developers who could unfortunately not make it in person. Unfortunately, we forgot to take a picture of everyone!
The consensus and community are important because of the aims of Notary v2. But let’s go back a bit as some of you may not know what Notary is and what it is for.
The Notary project was originally started at Docker back in 2015 to provide a general signing Continue reading
It’s amazing how quickly you get “must have feature Y or it should not be called X” comments coming from vendor engineers the moment you mention something vaguely-defined like SD-WAN.
Here are just two of the claims I got as a response to “BGP with IP-SLA is SD-WAN” trolling I started on LinkedIn based on this blog post:
Key missing features [of your solution]:
- real time circuit failover (100ms is not real-time)
- traffic steering (again, 100ms is not real-time)
Let’s get the facts straight: it seems Cisco IOS evaluates route-map statements using track objects in periodic BGP table scan process, so the failover time is on order of 30 seconds plus however long it takes IP SLA to detect the decreased link quality.
Read more ...Reverb: speculative debugging for web applications, Netravali & Mickens, SOCC’19
This week we’ll be looking at a selection of papers from the 2019 edition of the ACM Symposium of Cloud Computing (SoCC). First up is Reverb, which won a best paper award for its record and replay debugging framework that accommodates speculative edits (i.e., candidate bug-fixes) during replay. In the context of the papers we’ve been looking at recently, and for a constrained environment, Reverb is helping its users to form an accurate mental model of the system state, and to form and evaluate hypotheses in-situ.
Reverb has three features which enable a fundamentally more powerful debugging experience. First, Reverb tracks precise value provenance, allowing a developer to quickly identify the reads and writes to JavaScript state that affected a particular variable’s value. Second, Reverb enables speculative bug fix analysis… Third, Reverb supports wide-area debugging for applications whose server-side components use event-driven architectures.
Reverb’s goal is to aid in debugging the client-side of JavaScript web applications. These are "pervasively asynchronous and event-driven" which makes it notoriously difficult to figure out what’s going on. See e.g. "Debugging data flows Continue reading
If the merger is blocked and the operators remain separate companies, their respective 5G plans are...
I have recently replaced my ThinkPad X1 Carbon 2014 (second generation). I have kept it for more than five years, using it every day and carrying it everywhere. The expected lifetime of a laptop is always an unknown. Let me share my feedback.

My configuration embeds an Intel vPro Core i7-4600U, 8 Gib of RAM, a 256 Gib SATA SSD, a matte WQHD display and a WWAN LTE card. I got it in June 2014. It has spent these years running Debian Sid, starting from Linux 3.14 to Linux 5.4.

This generation of ThinkPad X1 Carbon has been subject to a variety of experiences around the keyboard. We are still hunting the culprits. The layout is totally messed up, with many keys displaced.1 I have remapped most of them. It also lacks physical function keys: they have been replaced by a non-customizable touch bar. I do not like it due to absence of tactile feedback and it is quite easy to hit a key by mistake. I would recommend to Continue reading
In this post, I’d like to show readers how to use Pulumi to create a VPC endpoint on AWS. Until recently, I’d heard of VPC endpoints but hadn’t really taken the time to fully understand what they were or how they might be used. That changed when I was presented with a requirement for the AWS EC2 APIs to be available within a VPC that did not have Internet access. As it turns out—and as many readers are probably already aware—this is one of the key use cases for a VPC endpoint (see the VPC endpoint docs). The sample code I’ll share below shows how to programmatically create a VPC endpoint for use in infrastructure-as-code use cases.
For those that aren’t familiar, Pulumi allows users to use one of a number of different general-purpose programming languages and apply them to infrastructure-as-code scenarios. In this example, I’ll be using TypeScript, but Pulumi also supports JavaScript and Python (and Go is in the works). (Side note: I intend to start working with the Go support in Pulumi when it becomes generally available as a means of helping accelerate my own Go learning.)
Here’s a snippet of TypeScript code that Continue reading
I recently had a need to manually load some container images into a Linux system running containerd (instead of Docker) as the container runtime. I say “manually load some images” because this system was isolated from the Internet, and so simply running a container and having containerd automatically pull the image from an image registry wasn’t going to work. The process for working around the lack of Internet access isn’t difficult, but didn’t seem to be documented anywhere that I could readily find using a general web search. I thought publishing it here may help individuals seeking this information in the future.
For an administrator/operations-minded user, the primary means of interacting with containerd is via the ctr command-line tool. This tool uses a command syntax very similar to Docker, so users familiar with Docker should be able to be productive with ctr pretty easily.
In my specific example, I had a bastion host with Internet access, and a couple of hosts behind the bastion that did not have Internet access. It was the hosts behind the bastion that needed the container images preloaded. So, I used the ctr tool to fetch and prepare the images on the bastion, then Continue reading