Oracle Fixes 334 Bugs in Record-Breaking Critical Patch Update
Almost 40 vulnerabilities with a 9.8 severity rating can be exploited over a network without...
Almost 40 vulnerabilities with a 9.8 severity rating can be exploited over a network without...
The company did not provide specifics on the number of jobs that will be cut, but reports indicated...
Welcome to Technology Short Take #123, the first of 2020! I hope that everyone had a wonderful holiday season, but now it’s time to jump back into the fray with a collection of technical articles from around the Internet. Here’s hoping that I found something useful for you!
crypt32.dll, a core Windows cryptographic component) that was rumored Continue reading
Looks Lush.
The post JetBrains Mono: A free and open source typeface for developers appeared first on EtherealMind.
SDxCentral Weekly Wrap for Jan. 17, 2020: 5G competition has been rough on Nokia; Citrix promises a...
What better way to start How Networks Really Work webinar than with fallacies of distributed computing… and that’s exactly what I did in late August 2019.
Synthesizing data structure transformations from input-output examples, Feser et al., PLDI’15
The Programmatically Interpretable Reinforcement Learning paper that we looked at last time out contained this passing comment coupled with a link to today’s paper choice:
It is known from prior work that such [functional] languages offer natural advantages in program synthesis.
That certainly caught my interest. The context for the quote is synthesis of programs by machines, but when I’m programming, I’m also engaged in the activity of program synthesis! So a work that shows functional languages have an advantage for programmatic synthesis might also contain the basis for an argument for natural advantages to the functional style of programming. I didn’t find that here. We can however say that this paper shows “functional languages are well suited to program synthesis.”
Never mind, because the ideas in the paper are still very connected to a question I’m fascinated by at the moment: “how will we be developing software systems over this coming decade?”. There are some major themes to be grappled with: system complexity, the consequences of increasing automation and societal integration, privacy, ethics, security, trust (especially in supply chains), interpretability vs black box models, Continue reading
The gap between the performance of processors, broadly defined, and the performance of DRAM main memory, also broadly defined, has been an issue for at least three decades when the gap really started to open up. …
Cache Is King was written by Timothy Prickett Morgan at The Next Platform.
“If they hired Peter Leav they are setting up to sell,” said analyst Zeus Kerravala.
CenturyLink nabbed $1.6B Interior Department win; Rogers rolled out a 5G first; and Telstra,...
After a decade of vendor consolidation that saw some of the world’s biggest IT firms acquire first-class HPC providers such as SGI, Cray, and Sun Microsystems, as well as smaller players like Penguin Computing, WhamCloud, Appro, and Isilon, it is natural to wonder who is next. …
HPC In 2020: Acquisitions And Mergers As The New Normal was written by Michael Feldman at The Next Platform.

It’s hard to believe that it’s been eight years since I wrote my most controversial post ever. I get all kinds of comments on my NAT66 post even to this day. I’ve been told I’m a moron, an elitist, and someone that doesn’t understand how the Internet works. I’ve also had some good comments that highlight a specific need for tools like NAT66. I wanted to catch up with everything and ask a very important question.
WHY?
APNIC had a great post about NAT66 back in 2018. You should totally read it. I consider it a fair review of the questions surrounding NAT’s use in 2020. Again, NAT has a purpose and when used properly and sparingly for that purpose it works well. In the case of the article, Marco Cilloni (@MCilloni) lays out the need to use NAT66 to use IPv6 at his house due to ISP insanity and the latency overhead of using tunnels with Hurricane Electric. In this specific case, NAT66 was a good tool for him to use to translate his /128 address to something useable in his network.
If you’re brave, you should delve into the comments. A Continue reading
Rogers is working with Ericsson on the 5G network deployment pivoting off of an agreement signed in...
Within 15 minutes of submitting a support ticket, Google promises to connect IT teams with an...
The company’s two-part order with the Interior Department is spread over 11 one-year options that...

Remember WiFi6 was making naming easier. Except when it isn't.
The post Wi-Fi 6 into 6 GHz = WiFi6E. But not 5G but is 5Ghz. appeared first on EtherealMind.

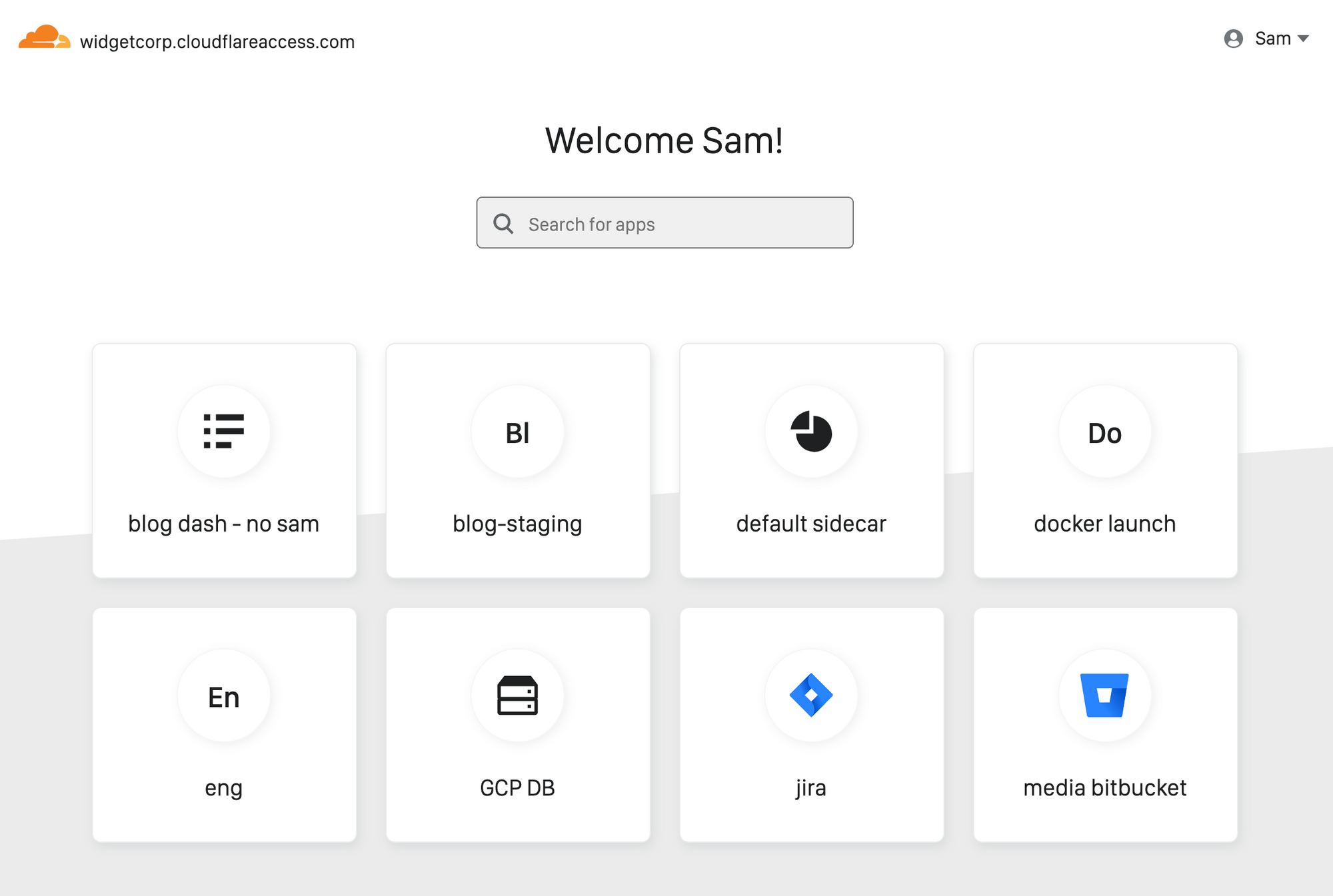
Every person joining your team has the same question on Day One: how do I find and connect to the applications I need to do my job?
Since launch, Cloudflare Access has helped improve how users connect to those applications. When you protect an application with Access, users never have to connect to a private network and never have to deal with a clunky VPN client. Instead, they reach on-premise apps as if they were SaaS tools. Behind the scenes, Access evaluates and logs every request to those apps for identity, giving administrators more visibility and security than a traditional VPN.
Administrators need about an hour to deploy Access. End user logins take about 20 ms, and that response time is consistent globally. Unlike VPN appliances, Access runs in every data center in Cloudflare’s network in 200 cities around the world. When Access works well, it should be easy for administrators and invisible to the end user.
However, users still need to locate the applications behind Access, and for internally managed applications, traditional dashboards require constant upkeep. As organizations grow, that roster of links keeps expanding. Department leads and IT administrators can create and publish manual lists, but those become Continue reading