0
It should come as no surprise how much emphasis organizations place on security today. Threats are becoming more and more sophisticated and the number of threats grow to uncontrollable rates every day.
One of the biggest downsides is that the rising cost of data breaches in 2019 alone, a global average of $3.92 million as reported by the Ponemon Institute and IBM Security July 2019 report, is enough to cause organizations to rethink or increase emphasis on their security strategies and how they can help secure their most important assets by improving the cyber hygiene in their organizations.
What is Cyber Hygiene?
Cyber hygiene refers to what an organization can do to improve their security postures around physical hardware, software, and applications. If you’ve seen Pat Gelsinger’s keynote from 2017, he goes into the 5 pillars of good cyber hygiene and what organizations can do to improve basic and fundamental security for their business.
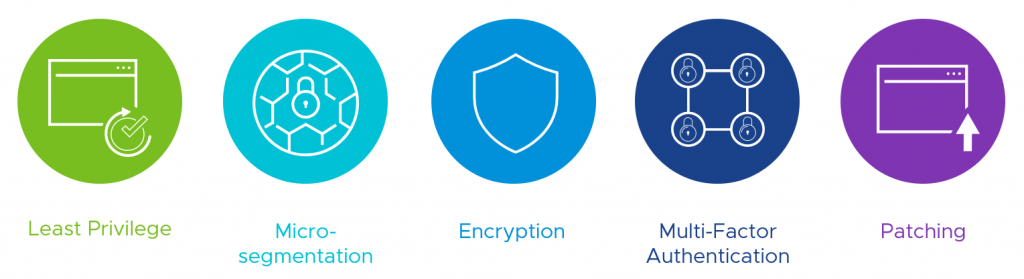
Over the last several years, VMware has been focusing on helping organizations move to Software-Defined Data Centers (SDDC) to improve their agility and meet the speed of business. As more organizations adopted the SDDC model, VMware found itself in a unique position Continue reading




