CenturyLink’s Edge Strategy Starts With ‘Several Hundred Million’ Investment
While its edge services today tend to be more “on a bespoke basis,” by 2020 “we expect a huge...
While its edge services today tend to be more “on a bespoke basis,” by 2020 “we expect a huge...

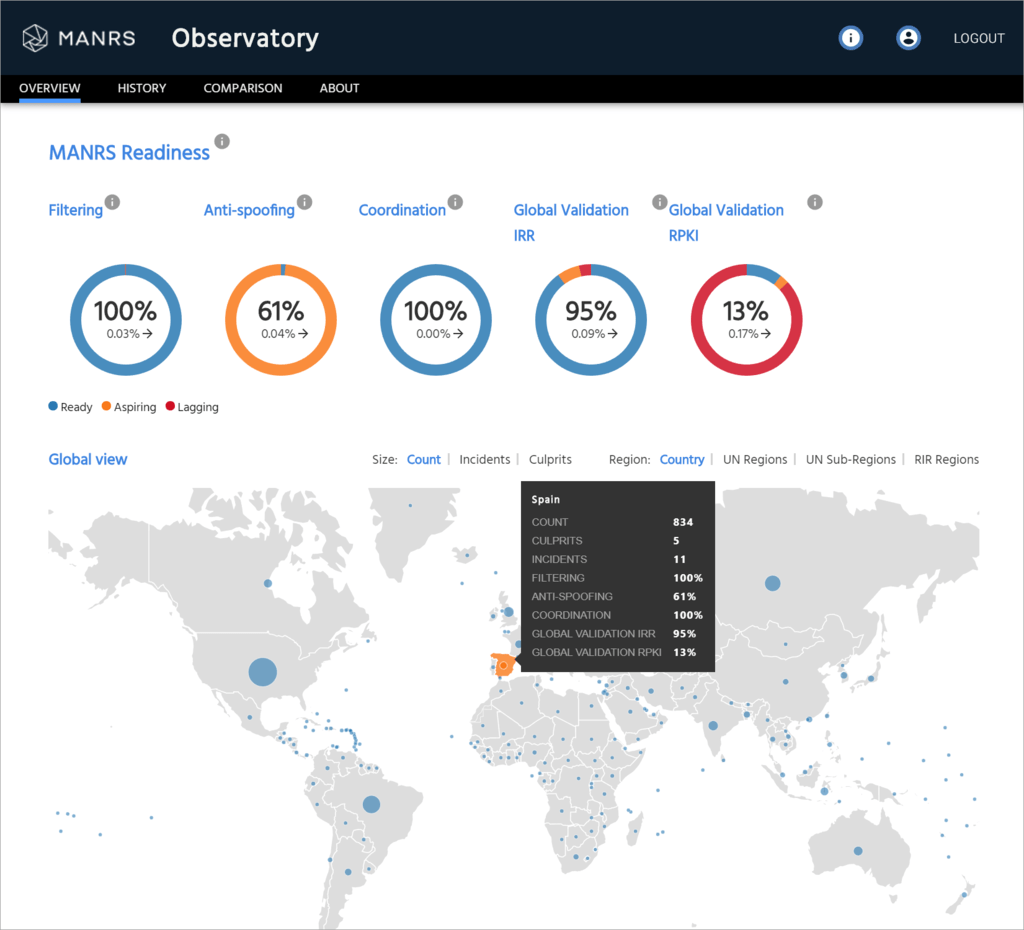
Routing security is vital to the future and stability of the Internet, but it’s under constant threat. Which is why we’ve launched a free online tool so that network operators can see how they’re doing, and what they can improve, while anyone can see the health of the Internet at a glance. The MANRS Observatory measures networks’ adherence to MANRS – their “MANRS readiness” – a key indicator of the state of routing security and resiliency of the Internet.
Here’s what the MANRS Observatory is in a nutshell:
The startup, founded by former VMware and Nutanix execs, built a backup service on Amazon Web...

Today we’re excited to announce Cloudflare Magic Transit. Magic Transit provides secure, performant, and reliable IP connectivity to the Internet. Out-of-the-box, Magic Transit deployed in front of your on-premise network protects it from DDoS attack and enables provisioning of a full suite of virtual network functions, including advanced packet filtering, load balancing, and traffic management tools.

Magic Transit is built on the standards and networking primitives you are familiar with, but delivered from Cloudflare’s global edge network as a service. Traffic is ingested by the Cloudflare Network with anycast and BGP, announcing your company’s IP address space and extending your network presence globally. Today, our anycast edge network spans 193 cities in more than 90 countries around the world.
Once packets hit our network, traffic is inspected for attacks, filtered, steered, accelerated, and sent onward to the origin. Magic Transit will connect back to your origin infrastructure over Generic Routing Encapsulation (GRE) tunnels, private network interconnects (PNI), or other forms of peering.
Enterprises are often forced to pick between performance and security when deploying IP network services. Magic Transit is designed from the ground up to minimize these trade-offs: performance and security are better together. Magic Transit deploys IP security Continue reading
After a long wait, now we know. All three of the initial exascale-class supercomputer systems being funded by the US Department of Energy through its CORAL-2 procurement are going to be built by Cray, with that venerable maker of supercomputers being the prime contractor on two of them. …
Cray Runs The Exascale Table In The United States was written by Timothy Prickett Morgan at .

Today we announced Cloudflare Magic Transit, which makes Cloudflare’s network available to any IP traffic on the Internet. Up until now, Cloudflare has primarily operated proxy services: our servers terminate HTTP, TCP, and UDP sessions with Internet users and pass that data through new sessions they create with origin servers. With Magic Transit, we are now also operating at the IP layer: in addition to terminating sessions, our servers are applying a suite of network functions (DoS mitigation, firewalling, routing, and so on) on a packet-by-packet basis.
Over the past nine years, we’ve built a robust, scalable global network that currently spans 193 cities in over 90 countries and is ever growing. All Cloudflare customers benefit from this scale thanks to two important techniques. The first is anycast networking. Cloudflare was an early adopter of anycast, using this routing technique to distribute Internet traffic across our data centers. It means that any data center can handle any customer’s traffic, and we can spin up new data centers without needing to acquire and provision new IP addresses. The second technique is homogeneous server architecture. Every server in each of our edge data centers is capable of running every task. We Continue reading
Not everything is broken this week although some things definitely are looking grim. We consider how really dead data centers are according to Gartner, Cisco gobbles some more AI for Webex while HPE gets more AI-ish for Bluedata. GTT Communications is in trouble while ATT Bribery case highlights that big companies are dumb. Snark and virtual donuts all round this week.
The post Network Break 247: Data Centers Are Not Quite Dead, AI is a Feature Not A Product appeared first on Packet Pushers.
Under two unrelated US Department of Defense procurements, Cray has been awarded a total of $71 million to supply the Air Force and Army with a trio of HPC systems. …
US Military Buys Three Cray Supercomputers was written by Michael Feldman at .
GTT Communications' stock price plunged to its lowest level in more than five years in the...
Jio will set up a pair of new data centers in the country that will include compute, storage, and...
5G is being led by and positioned for enterprise services, and multiple factors are driving this...
Accelerators of many kinds, but particularly those with GPUs and FPGAs, can be pretty hefty compute engines that meet or exceed the power, thermal, and spatial envelopes of modern processors. …
Xilinx Keeps A Low Profile With Mainstream FPGA Accelerator was written by Michael Feldman at .