0
Review: 4 open-source network management tools improve usability, performance
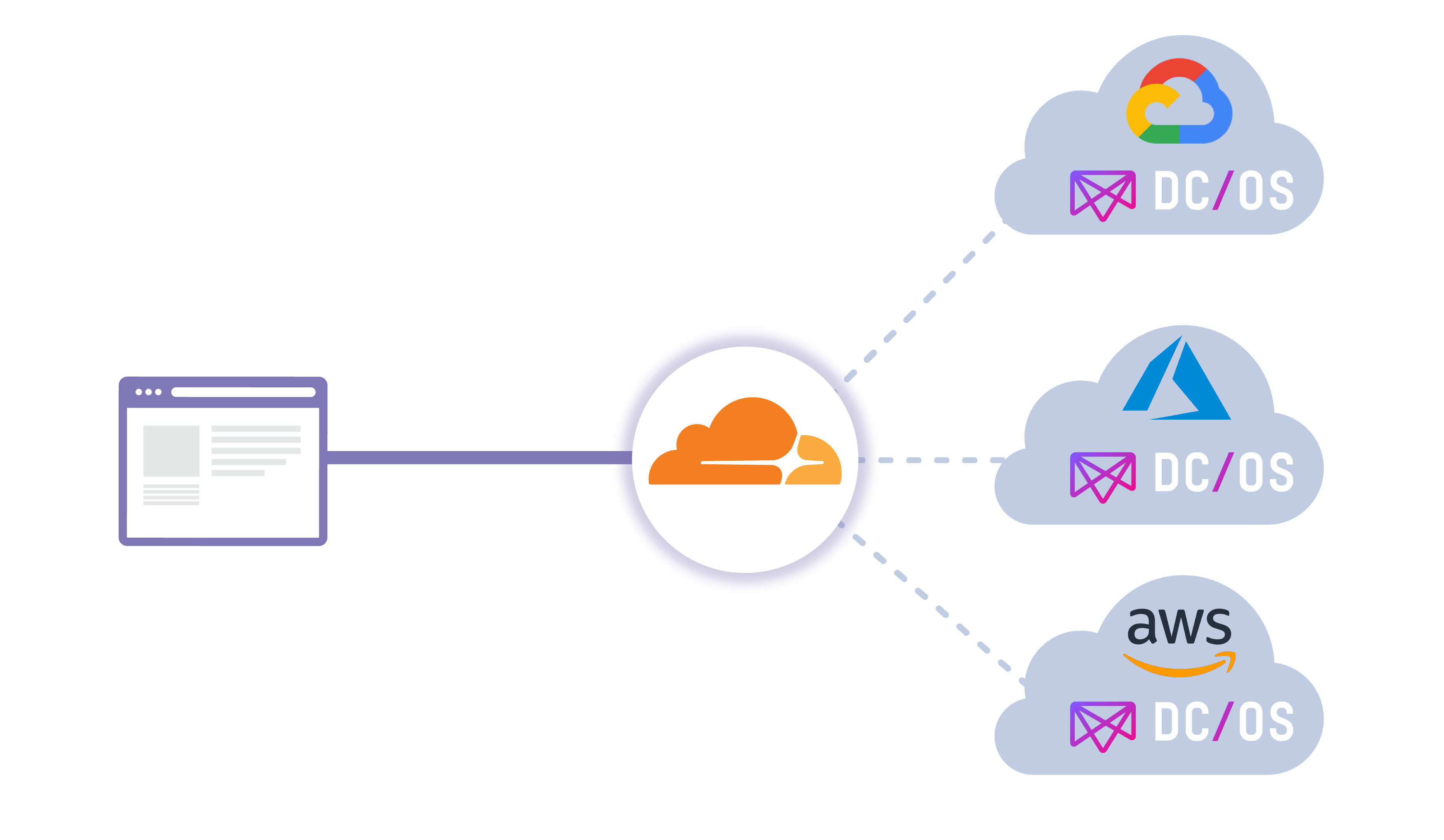
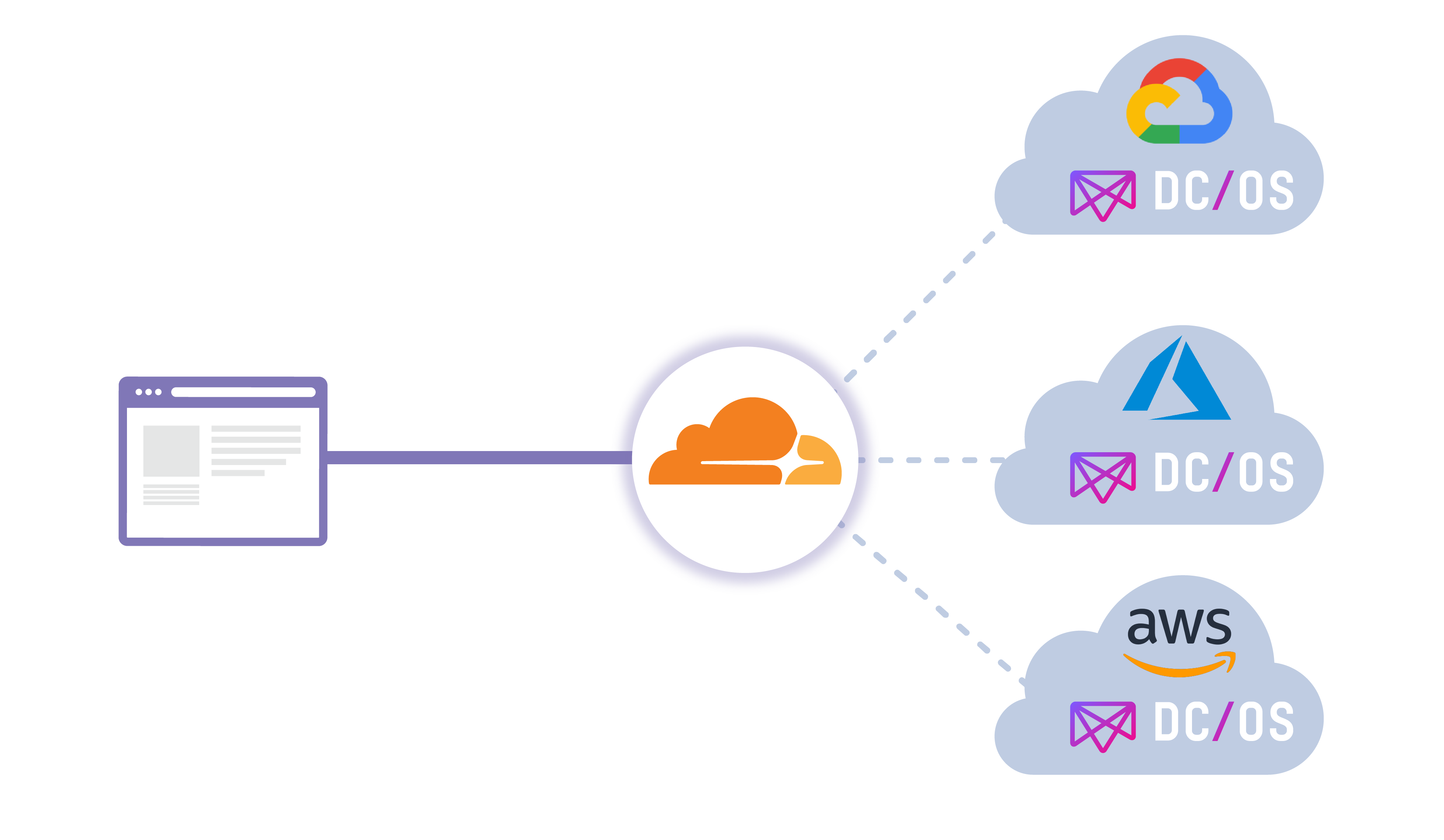
Network management tools have come a long way from the early command-line products with arcane, text-based configuration files that kept everyone except the resident (typically Linux) guru in the dark. Today’s management tools, replete with desktop or web-based GUIs, easy installs and configuration wizards, are far more accessible. With each iteration vendors find ways to make these tools more powerful and easier to use. For this review, we evaluated newer versions of three established open-source network management products – OpenNMS, Zenoss Core and NetXMS – as well as a relative newcomer, Sensu Core. All four products are free and open source.To read this article in full, please click here
 They are mobile 5G, fixed wireless, and edge computing, and AT&T says it is building its networks to allow “LTE to work efficiently in parallel with 5G.” “
They are mobile 5G, fixed wireless, and edge computing, and AT&T says it is building its networks to allow “LTE to work efficiently in parallel with 5G.” “ Accenture has been working on a commercial version of ONAP to support providers’ transition from hardware-based to software-based networks.
Accenture has been working on a commercial version of ONAP to support providers’ transition from hardware-based to software-based networks. But “this rate of investment is not sustainable,” Strategic Cyber Ventures warns. There are likely many security “zombies” that initially raised big rounds but now growth has slowed.
But “this rate of investment is not sustainable,” Strategic Cyber Ventures warns. There are likely many security “zombies” that initially raised big rounds but now growth has slowed.
 According to EdgeMicro, these proof-of-concept edge computing tests are the last step before deployment.
According to EdgeMicro, these proof-of-concept edge computing tests are the last step before deployment. Research group sees reasons to be cheerful as mobile infrastructure market set to see turnaround after three consecutive years of declining revenues thanks to 5G New Radio.
Research group sees reasons to be cheerful as mobile infrastructure market set to see turnaround after three consecutive years of declining revenues thanks to 5G New Radio.