Open19 Data Centers Pick Up Steam
 The open data center effort added Packet’s CEO as a board member and will soon sell Open19 compliant servers on its online marketplace.
The open data center effort added Packet’s CEO as a board member and will soon sell Open19 compliant servers on its online marketplace.
 The open data center effort added Packet’s CEO as a board member and will soon sell Open19 compliant servers on its online marketplace.
The open data center effort added Packet’s CEO as a board member and will soon sell Open19 compliant servers on its online marketplace.
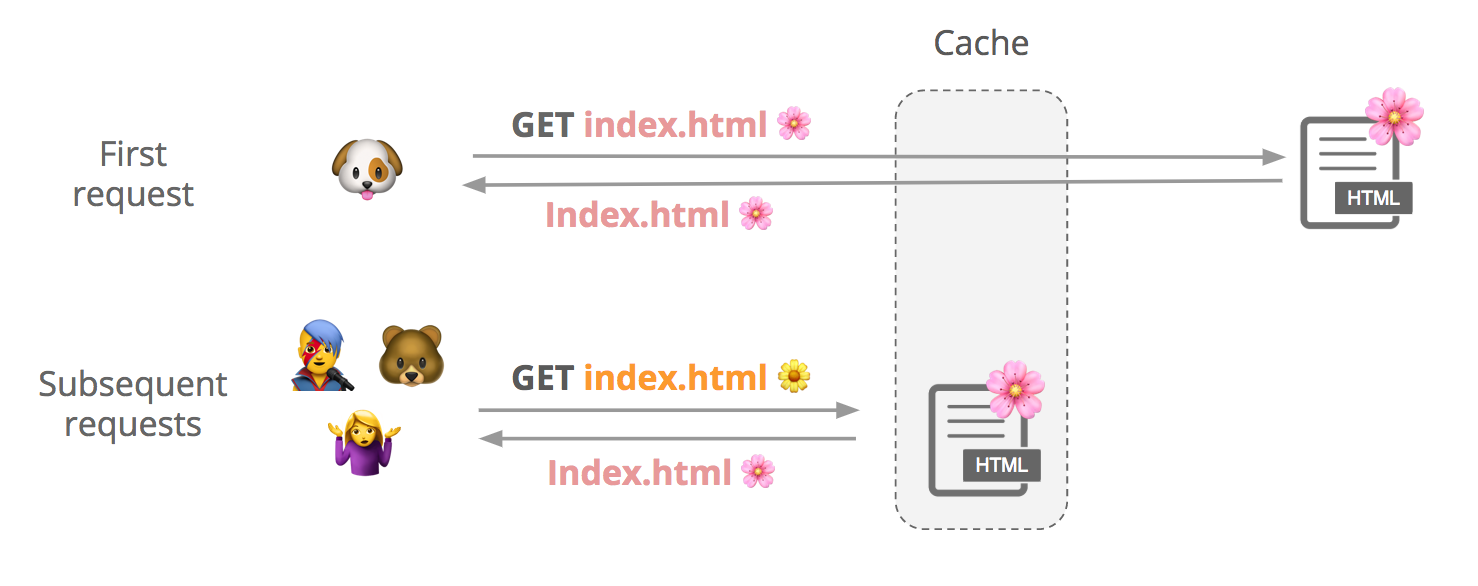
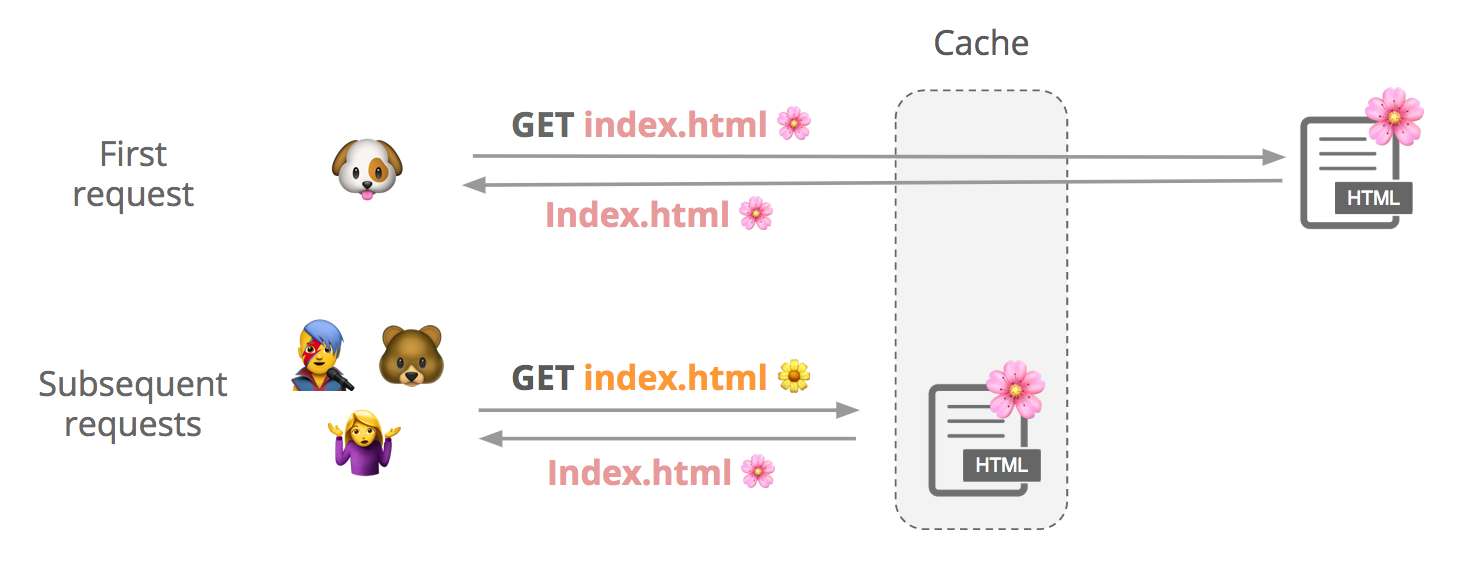
A few days ago, Cloudflare — along with the rest of the world — learned of a "practical" cache poisoning attack. In this post I’ll walk through the attack and explain how Cloudflare mitigated it for our customers. While any web cache is vulnerable to this attack, Cloudflare is uniquely able to take proactive steps to defend millions of customers.
In addition to the steps we’ve taken, we strongly recommend that customers update their origin web servers to mitigate vulnerabilities. Some popular vendors have applied patches that can be installed right away, including Drupal, Symfony, and Zend.
Say a user requests a cacheable file, index.html. We first check if it’s in cache, and if it’s not not, we fetch it from the origin and store it. Subsequent users can request that file from our cache until it expires or gets evicted.
Although contents of a response can vary slightly between requests, customers may want to cache a single version of the file to improve performance:
(See this support page for more info about how to cache HTML with Cloudflare.)
How do we know it’s the same file? We create something Continue reading
 This eBrief from SDxCentral takes a look at some of the security issues facing serverless and containers and delves into some of the tools and methodologies available to overcome these challenges.
This eBrief from SDxCentral takes a look at some of the security issues facing serverless and containers and delves into some of the tools and methodologies available to overcome these challenges.
That was quick: The new Malaysian government has repealed a fake news law passed earlier this year, The Hill reports. The past government had used the law to charge several opposition leaders. The maximum penalty for violating the law was six years in prison and a fine of about US$128,000.
They love us: A community-run ISP in Chattanooga, Tennessee, is the highest-rated broadband provider in the United States in a Consumer Reports survey, notes Motherboard. The community-run service gets high ranks for speed, reliability, and value, the story says.
Legislating backdoors: The Australian government is targeting companies like Facebook, Google, and WhatsApp in a proposal that would require tech companies to decrypt customer communications on demand, CNet reports. The details of the draft proposal are unclear, but the government would require tech companies to provide more assistance to law enforcement agencies, The Register says.
AI doesn’t want your job: Workers don’t need to worry about Artificial Intelligence taking their jobs, Forbes says. AI will replace boring tasks, but generally not replace whole positions, according to one group of AI experts.
97 and counting: The Kashmir region of India has seen 97 Internet shutdowns in six years after and 11-hour Continue reading
I was recently working on a blog post involving the use of TLS certificates for encryption and authentication, and was running into errors. I’d checked all the “usual suspects”—AWS security groups, host-level firewall rules (via iptables), and the application configuration itself—but still couldn’t get it to work. When I did finally find the error, I figured it was probably worth sharing the commands I used in the event others might find it helpful.
The error was manifesting itself in that I was able to successfully connect to the application (with TLS) on the loopback address, but not the IP address assigned to the network adapter. Using ss -lnt, I verified that the application was listening on all IP addresses (not just loopback), and as I mentioned earlier I had also verified that AWS security groups and host-level firewall weren’t in play. This lead me to believe that there was something wrong with my TLS configuration.
Since the application’s error message was extremely vague (and not even remotely TLS-related), I decided to try using curl to verify that TLS was working correctly. First I ran this command:
curl --cacert /path/to/CA/certificate https://127.0.0.1 -v
After some output, curl Continue reading
Organizations are beginning to invest in the infrastructure to support artificial intelligence, requiring network managers to bone up on skills including data science and security.
A comprehensive view of Africa’s Internet peering and interconnection ecosystem from the region’s top networks and experts, opportunities to strengthen and build new peering relationships with over 300 attendees using an open to all “bilateral meeting” scheduling tool, insightful presentations, studies and reports delivered by a strong lineup of speakers, and a technical village are some of the interesting activities that participants to iWeek/AfPIF 2018 can expect.
The sessions have been spiced up to include a technical village, with vendors offering masterclasses, a super teachers award honoring Africa’s tech teachers, and a beers for peers session, to allow participants to network more.
“This year’s agenda reflects the growing interests from our rapidly evolving regional industry with an increased focus on regional networks, carrier-neutral data centers, cloud services, and regulation in addition to our traditional line-up of quality technical content,” said Kyle Spencer, Co-Coordinator of the African IXP Association.
This year, the Africa Peering and Interconnection Forum (AfPIF) joined hands with the South Africa ISP Association to hold sessions during iWeek. This provides extensive training sessions and opportunities for participants.
“Participants will have opportunities to meet with industry leaders to discuss one on one or in groups the various issues around Continue reading
At Cloudflare we’re accelerating web assets in a number of different ways. Part of this is caching, by storing the response given by the origin server directly within our 151+ global data centers. This will dramatically improve the delivery of the resources as the visitor will directly get them from the data center closest to them, instead of waiting for us to fetch the request from the origin web server.
The subject we’re gonna cover today is the concept of Edge-Side-Includes. And what’s better than a real use-case to introduce what it is used for? Let’s take a website where all pages are including advertisements at the head and bottom. Could we consider these pages static? We couldn’t as at least part of this page is dynamic. Could we consider caching it? That’s a no again as it would mean the first dynamic part rendered will be cached and served for the other visitors trying to get the page. It would be a catastrophe if the advertisements are user-specific.
So the issue here is that we can’t cache the page. That’s quite a shame as it means that we’ll fetch Continue reading
Tom Hollingsworth published a great blog post summarizing Cloud Field Day presentation by Ben Sigelman.
TL&DR: You’re not Google, you don’t have their problems, and so you’re probably not a good match for their tools.
While this shouldn’t come as a surprise to regular readers of my blog (here’s what I wrote on the topic in 2016), it’s refreshing to see it spelled out so eloquently (and by an ex-Googler).
Filter before you parse: faster analytics on raw data with Sparser Palkar et al., VLDB’18
We’ve been parsing JSON for over 15 years. So it’s surprising and wonderful that with a fresh look at the problem the authors of this paper have been able to deliver an order-of-magnitude speed-up with Sparser in about 4Kloc.
The classic approach to JSON parsing is to use a state-machine based parsing algorithm. This is the approach used by e.g. RapidJSON. Such algorithms are sequential and can’t easily exploit the SIMD capabilities of modern CPUs. State of the art JSON parsers such as Mison are designed to match the capabilities of modern hardware. Mison uses SIMD instructions to find special characters such as brackets and colons and build a structural index over a raw json string.
… we found that Mison can parse highly nested in-memory data at over 2GMB/s per core, over 5x faster than RapidJSON, the fastest traditional state-machine based parser available.
How can we parse JSON even faster? The key lies in re-framing the question. The fastest way to parse a JSON file is not to parse it at all. Zero ms is a hard lower bound ;). In other Continue reading

Looking back at our historical data, we realized how much the Internet and Cloudflare grew. With more than 150 datacenters, 10 percent of web-based applications, customers everywhere around the world, from the tiny islands in the Pacific to the big metropolises, we have an Internet landscape of almost every country and continent.
Cloudflare’s mission is to help build a better Internet. To do that we operate datacenters across the globe. By having datacenters close to end user we provide a fast, secure experience for everyone. Today I’d like to talk about our datacenters in Africa and our plans to serve a population of 1.2 billion people over 58 countries.
Internet penetration in developed countries skyrocketed since the 2000s, Internet usage is growing rapidly across Africa. We are seeing a 4% to 7% increase in traffic month on month. As of July 2018, we have 8 datacenters on the African Continent: