Take a Network Break! Security researchers are tracking the VPNFilter malware, which has infected an estimated 500,000 devices, GDPR regulations have gone into effect, and the OpenStack Summit debuts a new project called Airship.
Startup Lumina Networks bags $10 million in funding from Verizon, AT&T, and others; Pica8 releases PicaPilot for network fabric orchestration; and Huawei wins “Supplier of the Decade” from Vodaphone.
HPE released its quarterly earnings and warned of challenges for the second half of the year, and Amazon’s Echo unexpectedly recorded and sent a couple’s conversations.
Get links to all these stories after our sponsor message, and stay tuned for a Coffee Talk with Silver Peak.
Sponsor: Cisco Systems
Find out how Cisco and its trusted partners Equilibrium Security and ePlus/IGX can help your organization tackle the General Data Protection Regulation, or GDPR. Tune into Packet Pushers Priority Queue episode 147 to get practical insights on how to get your arms around these wide-ranging rules.
Coffee Talk: Silver Peak and Solis Mammography
On today’s Coffee Talk conversation we discuss SD-WAN with Solis Mammography and how its Silver Peak SD-WAN deployment helped the company streamline the movement of about a petabyte of imaging data efficiently and security.
Show Links:
Continue reading

 ) but we were interested in the areas of programming, automation, orchestration, databases, analytics, and so on. The end goal of the project was to identify what those relevant skills are, have a plan to identify the current skillset in the field, do that gap analysis and then put forward recommendations on how to close the gap.
) but we were interested in the areas of programming, automation, orchestration, databases, analytics, and so on. The end goal of the project was to identify what those relevant skills are, have a plan to identify the current skillset in the field, do that gap analysis and then put forward recommendations on how to close the gap. Multicast this time.
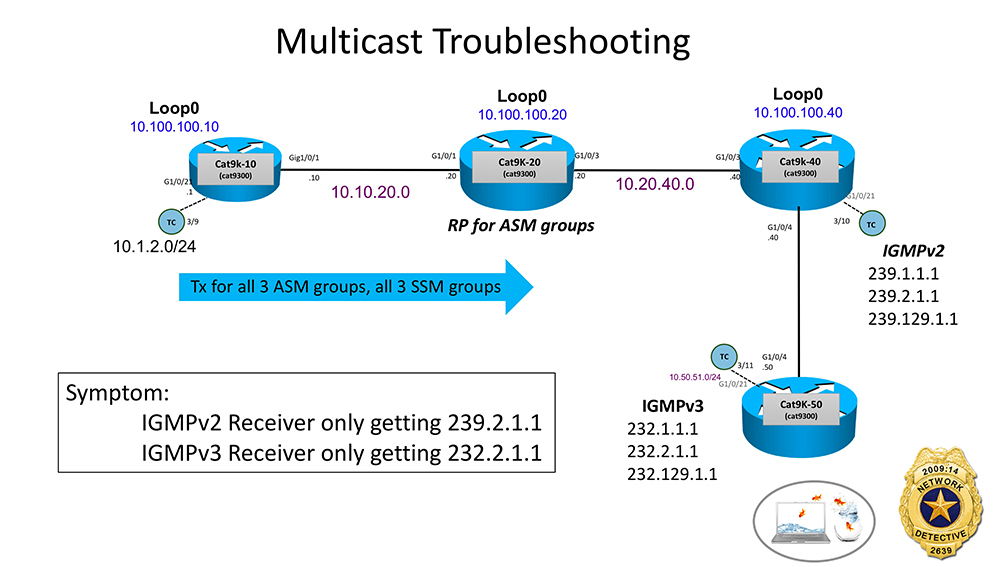
Multicast this time.