Dissecting IBGP+EBGP Junos Configuration
Networking engineers familiar with Junos love to tell me how easy it is to configure and operate IBGP EVPN overlay on top of EBGP IP underlay. Krzysztof Szarkowicz was kind enough to send me the (probably) simplest possible configuration (here’s another one by Alexander Grigorenko)
To learn more about EVPN technology and its use in data center fabrics, watch the EVPN Technical Deep Dive webinar.
Read more ...SafeKeeper: protecting web passwords using trusted execution environments
SafeKeeper: protecting web passwords using trusted execution environments Krawiecka et al., WWW’18
(If you don’t have ACM Digital Library access, the paper can be accessed either by following the link above directly from The Morning Paper blog site, or from the WWW 2018 proceedings page).
Today’s paper is all about password management for password protected web sites / applications. Even if we assume that passwords are salted and hashed in accordance with best practice (NIST’s June 2017 digital identity guidelines now mandate the use of keyed one-way functions such as CMAC), an adversary that can obtain a copy of the back-end database containing the per-user salts and the hash values can still mount brute force guessing attacks against individual passwords.

SafeKeeper goes a lot further in its protection of passwords. What really stands out is the threat model. SafeKeeper keeps end user passwords safe even when we assume that an adversary has unrestricted access to the password database. Not only that, the adversary is able to modify the content sent to the user from the web site (including active content such as client-side scripts). And not only that! The adversary is also able to read all Continue reading
OpenStack Members Argue About the Definition of ‘the Edge’
 Many of the groups working on edge computing are associated with telco networking. But edge computing is definitely not limited to telco networks.
Many of the groups working on edge computing are associated with telco networking. But edge computing is definitely not limited to telco networks.
Rate Limiting: Delivering more rules, and greater control
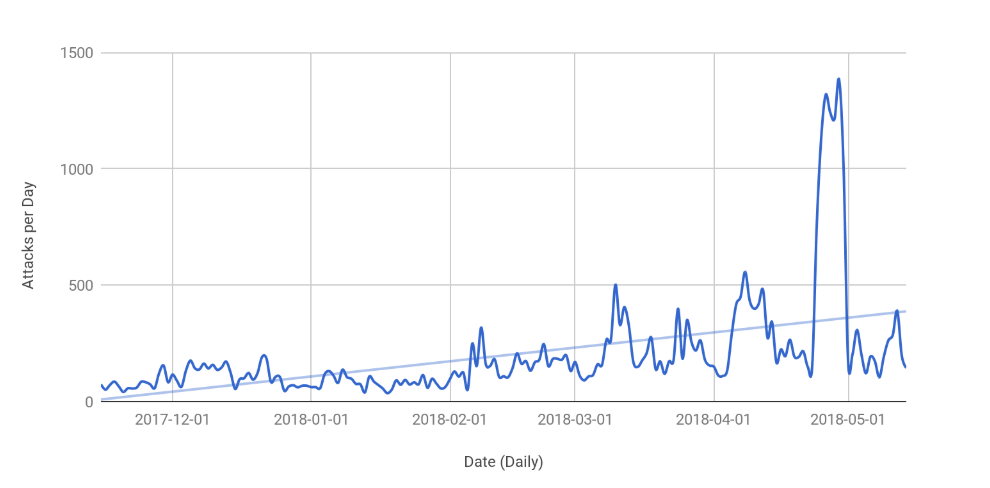
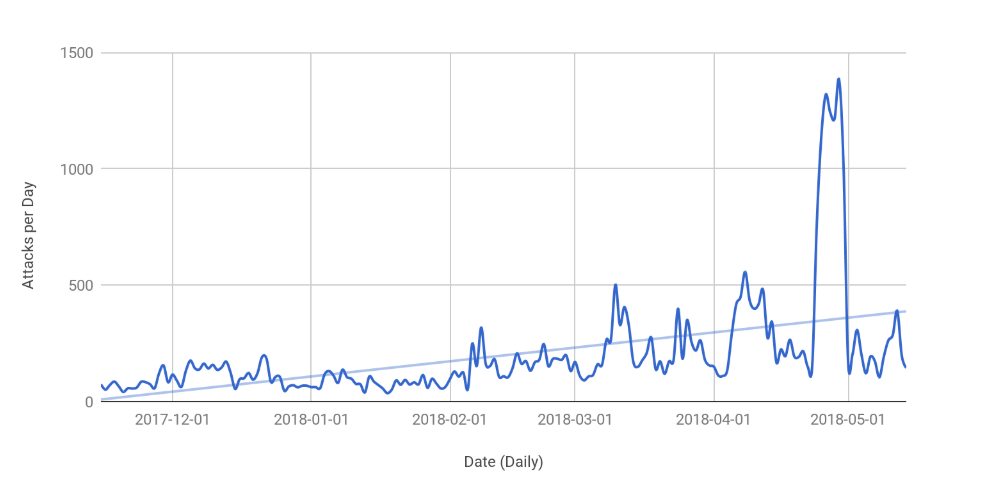
With more and more platforms taking the necessary precautions against DDoS attacks like integrating DDoS mitigation services and increasing bandwidth at weak points, Layer 3 and 4 attacks are just not as effective anymore. For Cloudflare, we have fully automated Layer 3/4 based protections with our internal platform, Gatebot. In the last 6 months we have seen a large upward trend of Layer 7 based DDoS attacks. The key difference to these attacks is they are no longer focused on using huge payloads (volumetric attacks), but based on Requests per Second to exhaust server resources (CPU, Disk and Memory). On a regular basis we see attacks that are over 1 million requests per second. The graph below shows the number of Layer 7 attacks Cloudflare has monitored, which is trending up. On average seeing around 160 attacks a day, with some days spiking up to over 1000 attacks.
A year ago, Cloudflare released Rate Limiting and it is proving to be a hugely effective tool for customers to protect their web applications and APIs from all sorts of attacks, from “low and slow” DDoS attacks, through to bot-based attacks, such as credential stuffing and content scraping. We’re pleased about the Continue reading
The Inevitability Of Death, Taxes, And Clouds
“Death and taxes” is a phrase that is usually attributed to Benjamin Franklin from a quote in a 1789 letter: “In this world nothing can be said to be certain, except death and taxes.” Public cloud computing providers didn’t exist back in the days of Franklin, but if they did, they would have no doubt made the list. Here’s why. Public clouds for large data analysis, just like death and taxes, are clearly inevitable because of two things. One simple and now rather worn out cliché. That would be scale and the slightly more subtle data.
Nation states are racing …
The Inevitability Of Death, Taxes, And Clouds was written by James Cuff at The Next Platform.
Kontron Supports Latest OpenStack, Kubernetes Releases, Keeps Them Separate
 Operators are moving aggressively to tighten their use of OpenStack and Kubernetes to bolster cloud deployments.
Operators are moving aggressively to tighten their use of OpenStack and Kubernetes to bolster cloud deployments.
Research: Robustness in Complex Systems
While the network engineering world tends to use the word resilience to describe a system that will support rapid change in the real world, another word often used in computer science is robustness. What makes a system robust or resilient? If you ask a network engineer this question, the most likely answer you will get is something like there is no single point of failure. This common answer, however, does not go “far enough” in describing resilience. For instance, it is at least sometimes the case that adding more redundancy into a network can actually harm MTTR. A simple example: adding more links in parallel can cause the control plane to converge more slowly; at some point, the time to converge can be reduced enough to offset the higher path availability.
In other cases, automating the response to a change in the network can harm MTTR. For instance, we often nail a static route up and redistribute that, rather than redistributing live routing information between protocols. Experience shows that sometimes not reacting automatically is better than reacting automatically.
This post will look at a paper that examines robustness more deeply, Robustness in Complexity Systems,” by Steven Gribble. While this Continue reading
Qualcomm’s New 5G NR Small Cell Platform Uses a Software-Defined Modem
 The small cell platform supports interface splits between the central unit and the remote radio head, which means operators can use it for fronthaul.
The small cell platform supports interface splits between the central unit and the remote radio head, which means operators can use it for fronthaul.
Microsoft Buys Conversational AI Startup Semantic Machines
 The startup’s technology aims to make digital assistants and bots sound more human.
The startup’s technology aims to make digital assistants and bots sound more human.
Google GKE Usage Surged 9x in 2017, Now Integrates Kubernetes 1.10
 Microsoft earlier this month said it has seen a 10x increase in Kubernetes usage on Azure.
Microsoft earlier this month said it has seen a 10x increase in Kubernetes usage on Azure.
Network Break 185: HPE Acquires Plexxi; New Batch Of Cisco Security Advisories
Take a Network Break! In this week’s episode we examine why HPE acquired Plexxi, dig into the latest batch of security advisories from Cisco, and discuss Intel’s reference architecture for new uCPE gear.
The Appropriations Committee in the U.S. Congress wants to keep up sanctions pressure against ZTE, AWS adds Verizon as a customer, and a new DDoS attack technique looks to thwart a common filter.
Toshiba clears its last hurdle to sell is semiconductor business, Cisco posts a positive third quarter, and Symantec announces an internal audit into its financial results.
Sponsor: ThousandEyes
ThousandEyes gives you performance visibility from every user to every app over any network, both internal and external, so you can smoothly migrate to the cloud, transform your WAN, troubleshoot faster and deliver exceptional user experiences. Sign up for a free account at thousandeyes.com/packetpushers and choose a free ThousandEyes t-shirt.
Sponsor: Cisco Systems
Find out how Cisco and its trusted partners Equilibrium Security and ePlus/IGX can help your organization tackle the General Data Protection Regulation, or GDPR. Tune into Packet Pushers Priority Queue episode 147 to get practical insights on how to get your arms around these wide-ranging rules.
Show Links:
It’s Called Distributed Computing, Even When It Shouldn’t Be
Success can be its own kind of punishment in this world.
Since the dawn of modern computing 130 years ago with tabulating machines derived from looms, there have always been issues of scale when it comes to compute and storage. While all modern businesses worry about the IT infrastructure and how dependent they are on it, there are special classes of systems that are at organizations that have intense computing and storage demands, and usually also severe networking requirements, and they of necessity push the boundaries of what can be done simply because things need to be done.
They have …
It’s Called Distributed Computing, Even When It Shouldn’t Be was written by Timothy Prickett Morgan at The Next Platform.
SD-WAN: Managed or DIY?
 In this eBrief from SDxCentral, we compare the pros and cons of using a managed SD-WAN service vs. the DIY model. In addition, we talk to one enterprise about its SD-WAN experience.
In this eBrief from SDxCentral, we compare the pros and cons of using a managed SD-WAN service vs. the DIY model. In addition, we talk to one enterprise about its SD-WAN experience.
Cisco Live Update – App Updates!
There have been some updates to the Cisco Events app this year that I wanted to share. I also just …
The post Cisco Live Update – App Updates! appeared first on Fryguy's Blog.