0
Cisco bolsters Tetration for better cloud, workload security
Cisco this week expanded its Tetration Analytics system to let users quickly detect software vulnerabilities and more easily manage the security of the key components in their data centers.Introduced in 2016, the Cisco Tetration Analytics system gathers information from hardware and software sensors and analyzes the information using big data analytics and machine learning to offer IT managers a deeper understanding of their data center resources. The idea behind Tetration includes the ability to dramatically improve enterprise security monitoring, simplify operational reliability and move along application migrations to Software Defined Networking.To read this article in full, please click here

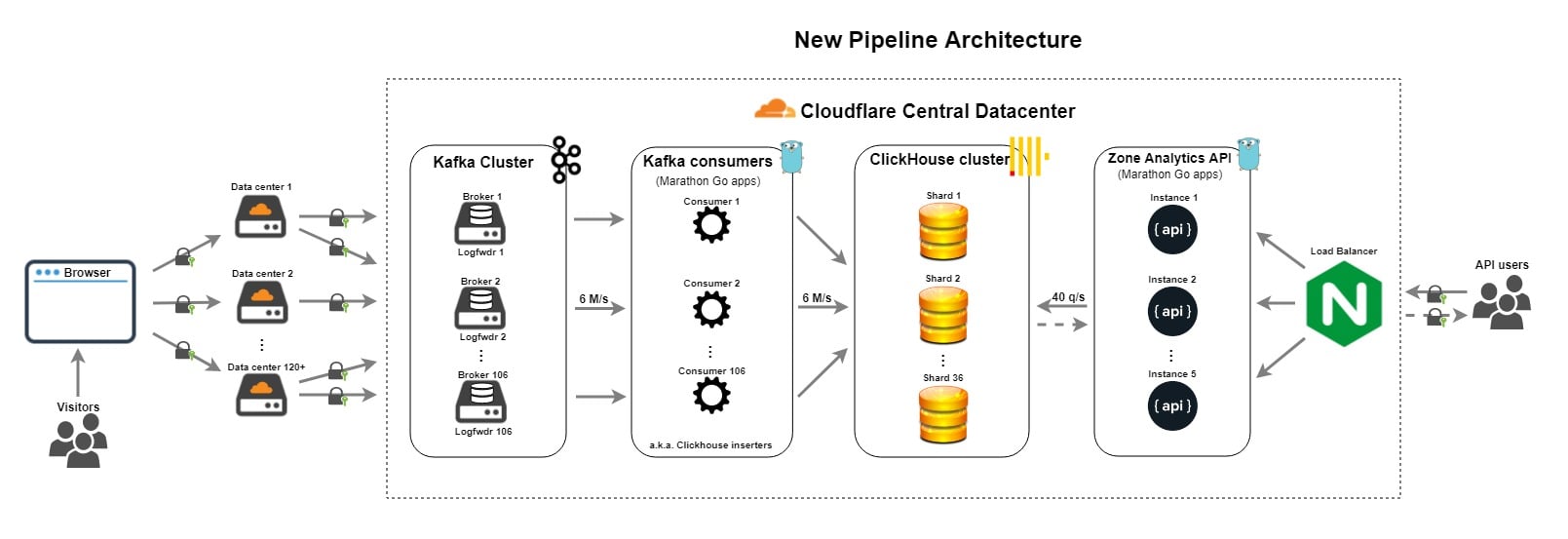
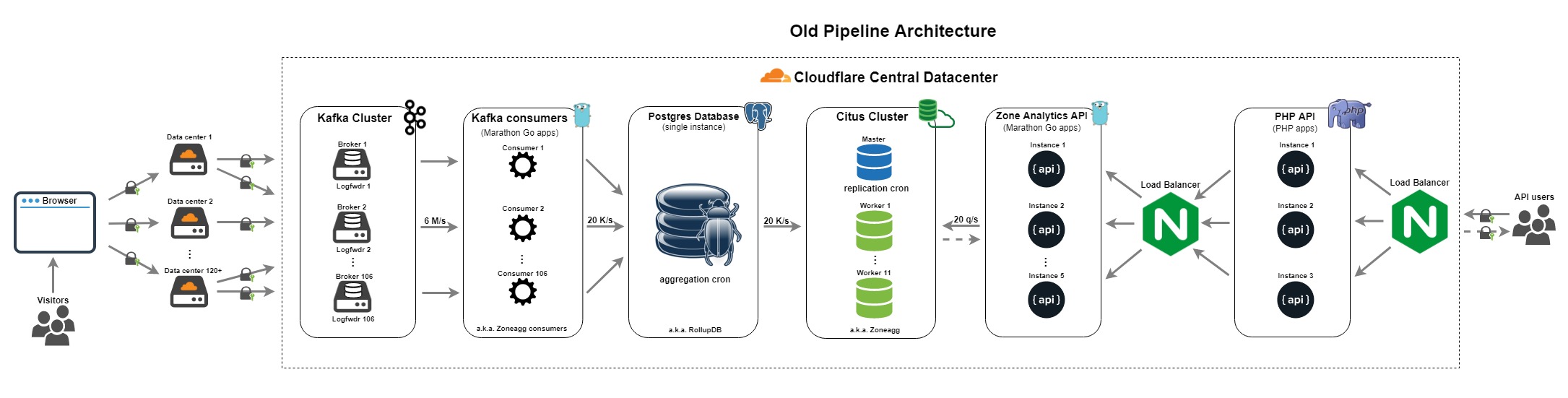

 The project was the first adopted by CNCF.
The project was the first adopted by CNCF. AT&T's Chris Rice, SVP of Domain 2.0, praises the new chip.
AT&T's Chris Rice, SVP of Domain 2.0, praises the new chip. He'll report to VMware Founder and former CEO Diane Greene at Google Cloud.
He'll report to VMware Founder and former CEO Diane Greene at Google Cloud.