A look at Internet traffic trends during Super Bowl LVIII

After winning Super Bowl LVII in 2023, the Kansas City Chiefs entered Super Bowl LVIII with an opportunity to pull off back-to-back wins, a feat last achieved by the New England Patriots two decades earlier, in 2003 and 2004. They faced the San Francisco 49ers, five-time Super Bowl champions, although their last win was nearly three decades ago, in 1995. The game started slowly, remaining scoreless until the start of the second quarter, after which both teams traded the lead until a tie score at the end of the game made it only the second Super Bowl to go into overtime. And if you weren’t watching it for the football, the advertisements certainly didn’t disappoint. And if you weren’t watching it for the football or the advertisements, but instead were waiting to see how many times CBS cut away to a shot of Taylor Swift during the game, the answer is… 16. (By my count, at least.)
In this blog post, we will explore which Super Bowl advertisements drove the largest spikes in traffic, as well as examine how traffic to food delivery services, social media, sports betting, and video platform websites and applications changed during the game. In Continue reading
Cloudflare defeats patent troll Sable at trial
For almost seven years, Cloudflare has been fighting against patent trolls. We’ve been doing this successfully through the efforts of our own legal team, external counsel, and the extraordinary efforts of people on the Internet looking for prior art (and getting rewarded for it) through our Project Jengo.
While we refuse to pay trolls for their meritless claims, we’ve been happy to award prizes to Project Jengo participants who help stop the trolls through prior art that invalidates their patents or claims. Project Jengo participants helped us in the past roundly beat the patent troll Blackbird (who subsequently went out of business).
Today, we’re back to talk about yet another win thanks to a lot of work by us, our external counsel, and Project Jengo participants.
Sable
Last Thursday, on a clear, sunny morning in Waco, Texas, a jury returned a verdict after less than two hours of deliberation. The jury found that Cloudflare did not infringe the patent asserted against Cloudflare by patent trolls Sable IP and Sable Networks.
And while that would have been enough to decide the case by itself, the jury went further and found that Sable’s old and broadly-written patent claim was invalid and never Continue reading
Can We Skip the Network Layer?
I mentioned that you don’t need node addresses when dealing with only two entities. Now and then, someone tries to extend this concept and suggests that the network layer addressing isn’t needed if the solution is local. For instance, if we have a solution that is supposed to run only on a single Ethernet segment, we don’t need network layer addressing because we already have data link layer addresses required for Ethernet to work (see also: ATAoE).
Too often in the past, an overly ingenious engineer or programmer got the idea to simplify everyone’s life and use the data link layer addresses as the ultimate addresses of individual nodes. They would then put the transport layer on top of that to get reliable packet transport. Finally, put whatever application on top of the transport layer. Problem solved.
Can We Skip the Network Layer?
I mentioned that you don’t need node addresses when dealing with only two entities. Now and then, someone tries to extend this concept and suggests that the network layer addressing isn’t needed if the solution is local. For instance, if we have a solution that is supposed to run only on a single Ethernet segment, we don’t need network layer addressing because we already have data link layer addresses required for Ethernet to work (see also: ATAoE).
Too often in the past, an overly ingenious engineer or programmer got the idea to simplify everyone’s life and use the data link layer addresses as the ultimate addresses of individual nodes. They would then put the transport layer on top of that to get reliable packet transport. Finally, put whatever application on top of the transport layer. Problem solved.
Home Lab
https://codingpackets.com/blog/home-lab
Solving the In-building Cellular Signal Propagation Dilemma
5G signal attenuation greatly impacts in-building cellular coverage. A new Corning solution tries to address the issue.DNS OARC 42
The DNS Operations, Analysis, and Research Center (DNS-OARC) brings together DNS service operators, DNS software implementors, and researchers together to share concerns, information and learn together about the operation and evolution of the DNS. They meet between two to three times a year in a workshops format. The most recent workshop was held in Charlotte, North Carolina in early February 2024. Here are my thoughts on the material that was presented and discussed at this workshop.DNS OARC 42
The DNS Operations, Analysis, and Research Center (DNS-OARC) brings together DNS service operators, DNS software implementors, and researchers together to share concerns, information and learn together about the operation and evolution of the DNS. They meet between two to three times a year in a workshops format. The most recent workshop was held in Charlotte, North Carolina in early February 2024. Here are my thoughts on the material that was presented and discussed at this workshop.Catalyst SD-WAN 20.13 – RBAC
Catalyst SD-WAN has supported Role Based Access Control (RBAC) for a long time. It has been possible to use predefined roles or create custom roles and defining what areas the user should have access to. However, before 20.13 it was not possible to define a scope. In large companies it’s quite common that one group manages one set of devices, for example all the sites in EU, all the sites in the US, etc. There may also be multiple business units within the company which may share some infrastructure but operate autonomously from each other where a BU should only have access to its own set of devices. As of 20.13, it is not possible to define scope when using RBAC in Catalyst SD-WAN.
There is another feature, called Network Hierarchy that is somewhat related to RBAC. When onboarding devices, you assign a Site ID to the device. The site is then assigned a name in the format of SITE_SiteID, for example SITE_10 when using a Site ID of 10. By default all sites belong to the global node as can be seen below:
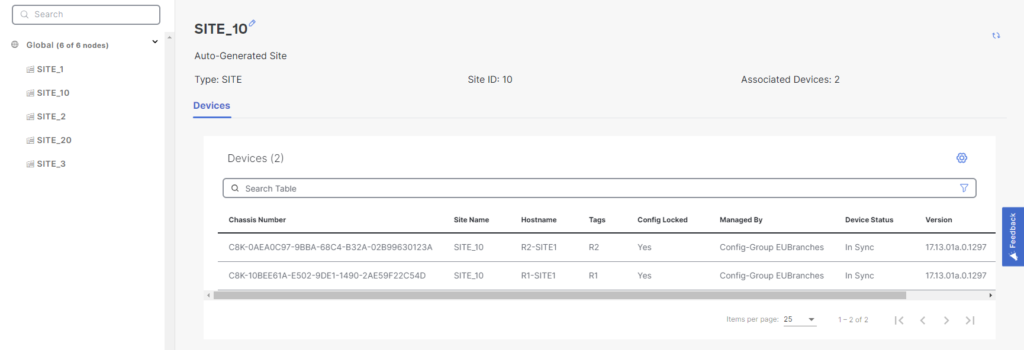
Note that it says Auto-Generated site. It is possible to edit the site Continue reading
Boat design phase
I purposely bought a boat that needed work so that I could customise it to my needs and learn how everything works. The wooden interior was dated and gloomy, it only had 1 DC socket, no working AC (no fuse board or inverter), no hot water (water heater broken) and a rusted up stove with 1 radiator run off it. After 5 months of hardship and an ever decreasing bank balance whether that was a good idea is debatable…..
VPP on FreeBSD – Part 1
About this series

Ever since I first saw VPP - the Vector Packet Processor - I have been deeply impressed with its performance and versatility. For those of us who have used Cisco IOS/XR devices, like the classic ASR (aggregation services router), VPP will look and feel quite familiar as many of the approaches are shared between the two. Over the years, folks have asked me regularly “What about BSD?” and to my surprise, late last year I read an announcement from the FreeBSD Foundation [ref] as they looked back over 2023 and forward to 2024:
Porting the Vector Packet Processor to FreeBSD
Vector Packet Processing (VPP) is an open-source, high-performance user space networking stack that provides fast packet processing suitable for software-defined networking and network function virtualization applications. VPP aims to optimize packet processing through vectorized operations and parallelism, making it well-suited for high-speed networking applications. In November of this year, the Foundation began a contract with Tom Jones, a FreeBSD developer specializing in network performance, to port VPP to FreeBSD. Under the contract, Tom will also allocate time for other tasks such as testing FreeBSD on common virtualization platforms to improve the desktop experience, improving Continue reading
Hedge 212: Shift Left? w/Chris Romeo
How many times have you heard you should “shift left” in the last few years? What does “shift left” even mean? Even if it had meaning once, does it still have any meaning today? Should we abandon the concept, or just the term? Listen in as Chris Romeo joins Tom Ammon and Russ White to talk about the origin, meaning, and modern uselessness of the term “shift left.”
download
The Mystery Of Tianhe-3, The World’s Fastest Supercomputer, Solved?
We don’t like a mystery and we particularly don’t like it when what is very likely the most powerful supercomputer in the world – at this time anyway – is veiled in secrecy. …
The Mystery Of Tianhe-3, The World’s Fastest Supercomputer, Solved? was written by Timothy Prickett Morgan at The Next Platform.
Technology Short Take 174
Welcome to Technology Short Take #174! For your reading pleasure, I’ve collected links on topics ranging from Kubernetes Gateway API to recent AWS attack techniques to some geeky Linux and Git topics. There’s something here for most everyone, I’d say! But enough of my rambling, let’s get on to the good stuff. Enjoy!
Networking
- I want to be Ivan Pepelnjak when I grow up. Why? Read this article on his response to someone wanting to use NSX to create availability zones.
- Nico Vibert has a tutorial that takes readers through using Cilium’s Gateway API functionality to do L7 traffic management (HTTP redirects, HTTP rewrites, and HTTP mirroring).
Security
- Nick Frichette discusses what he calls “one of the more egregious mistakes” that can be made in an AWS environment.
- Cybernews is covering what is being called the “mother of all breaches.” The amount of data rumored to be included—26 billion records—is almost impossible to comprehend.
- Martin McCloskey and Christophe Tafani-Dereeper of Datadog Security Labs share some information on recent attack techniques they’ve observed.
- Lee Holmes shines a light on the security risks of Postman, although the risks really could apply to just about any cloud-connected application. (And via this Continue reading
HN720: What Yale Learned about RADIUS Load Balancing
Yale’s efforts to load-balance RADIUS servers is a case study in system design for resiliency. First, there was a lone, redundant PSN. Next, F5s load balancers entered the picture. Then the network team realized a feature in IOS-XE was the answer… and brought Cisco along the learning journey with them. Hear it all from the... Read more »Navigating Single Cloud, Multi-Cloud, and Hybrid Cloud Environments
Before deciding on a cloud strategy, enterprises must fully understand the possibilities and the limitations that come with single cloud, multi-cloud, and hybrid cloud environments.Repetition Without Repetition

I just finished spending a wonderful week at Cisco Live EMEA and getting to catch up with some of the best people in the industry. I got to chat with trainers like Orhan Ergun and David Bombal and see how they’re continuing to embrace the need for people in the networking community to gain knowledge and training. It also made me think about a concept I recently heard about that turns out to be a perfect analogy to my training philosophy even though it’s almost 70 years old.
Practice Makes Perfect
Repetition without repetition. The idea seems like a tautology at first. How can I repeat something without repeating it. I’m sure that the people in 1967 that picked up the book by Soviet neurophysiologist Nikolai Aleksandrovitsch Bernstein were just as confused. Why should you do things over and over again if not to get good at performing the task or learning the skill?
The key in this research from Bernstein lay in how the practice happens. In this particular case he looked at blacksmiths to see how they used hammers to strike the pieces they were working on. The most accurate of his test subjects didn’t just perform the Continue reading
Making Dollars And Sense Of Arm Holdings
The only thing stronger than having absolute control, as happens in monopolies and oligopolies, is the strength that comes from numbers. …
Making Dollars And Sense Of Arm Holdings was written by Timothy Prickett Morgan at The Next Platform.