D2C232: Chaos Engineering: Breaking Things on Purpose
Chaos engineering is all about resilience and reliability… it just takes the harder path to get there. By injecting random and unpredictable behavior to the point of failure, chaos engineers observe systems’ weak points, apply preventative maintenance, and develop a failover plan. Matt Schillerstrom from Harness introduces Ned and Ethan to this wild corner of... Read more »Server And Storage Spending Growth Looks Rosy Out To 2027
For a market that is so integral to the global economy, it sure is hard to get a complete dataset on quarterly and annual spending on information technology. …
Server And Storage Spending Growth Looks Rosy Out To 2027 was written by Timothy Prickett Morgan at The Next Platform.
Join us at CalicoCon 2024, co-located with KubeCon + CloudNativeCon Europe 2024
We are excited to announce CalicoCon 2024, an in-person learning event for Project Calico, taking place March 19th, 2024 as a co-located event with KubeCon + CloudNativeCon Europe 2024.
As Kubernetes continues to expand its presence in both enterprises and small-to-medium businesses, understanding container networking and security in managed or self-managed Kubernetes environments becomes crucial. Organizations are now presented with choices for dataplanes, such as eBPF, Windows HNS, and Linux IP tables, multi-cloud and Kubernetes distributions as they scale their applications and make them more performance-efficient. Additionally, the process of creating new cloud-native applications or modernizing legacy applications also presents Kubernetes users with a selection of cutting-edge and mature container networking and security technologies.
To make these decisions to leverage their existing investments and future-proofing, users require guidance on developing and implementing scalable network security policies, selecting dataplanes, achieving low latency, optimizing resources, and integrating with bare metal and VM workloads.
What can you expect?
At CalicoCon, we will provide KubeCon Paris 2024 attendees with an opportunity to actively participate in a full-day event where they will:
- Discuss how to incorporate the latest Calico eBPF container networking and security innovations into their applications
- Discover best practices for securing Continue reading
Rethinking the Impossible: How AI Makes Edge Computing Even More Powerful
Edge computing has evolved from its legacy foundations to its modern format where servers are closer to the end user. Now, the addition of AI allows real-time, automated analysis and insights at the edge, providing benefits for a wide variety of industries.Fulfilling the promise of single-vendor SASE through network modernization
As more organizations collectively progress toward adopting a SASE architecture, it has become clear that the traditional SASE market definition (SSE + SD-WAN) is not enough. It forces some teams to work with multiple vendors to address their specific needs, introducing performance and security tradeoffs. More worrisome, it draws focus more to a checklist of services than a vendor’s underlying architecture. Even the most advanced individual security services or traffic on-ramps don’t matter if organizations ultimately send their traffic through a fragmented, flawed network.
Single-vendor SASE is a critical trend to converge disparate security and networking technologies, yet enterprise "any-to-any connectivity" needs true network modernization for SASE to work for all teams. Over the past few years, Cloudflare has launched capabilities to help organizations modernize their networks as they navigate their short- and long-term roadmaps of SASE use cases. We’ve helped simplify SASE implementation, regardless of the team leading the initiative.
Announcing (even more!) flexible on-ramps for single-vendor SASE
Today, we are announcing a series of updates to our SASE platform, Cloudflare One, that further the promise of a single-vendor SASE architecture. Through these new capabilities, Cloudflare makes SASE networking more flexible and accessible for Continue reading
With Hybrid Work Still Rising, Verizon Partners with Microsoft to Help Mobilize Teams
Verizon Mobile for Microsoft Teams eliminates the most troublesome limitations of past unified communications solutions, such as blending the mobile, in-office, and remote experiences.Removing FRRouting Configuration Is Not Idempotent
One of the few beauties of most “industry standard CLI” implementations1 is that they’re idempotent: nothing changes (apart from ACLs) if you configure the same stuff a dozen times. Most of these implementations allow you to deconfigure the same stuff multiple times; FRRouting is one of the unfortunate exceptions.
What Am I Talking About?
Imagine you have a bunch of IP prefixes you want to advertise with BGP. You could use network statements within the router bgp configuration to get that done:
Removing FRRouting Configuration Is Not Idempotent
One of the few beauties of most “industry standard CLI” implementations1 is that they’re idempotent: nothing changes (apart from ACLs) if you configure the same stuff a dozen times. Most of these implementations allow you to deconfigure the same stuff multiple times; FRRouting is one of the unfortunate exceptions.
What Am I Talking About?
Imagine you have a bunch of IP prefixes you want to advertise with BGP. You could use network statements within the router bgp configuration to get that done:
DNS and the DELEG Proposal
The DNS is a large-scale distributed database, where the internal structure of the databaase mirrors the hierarchical nature of the name space itself. In the database the points of delegation from one node to another are de noted by DNS Nameserver records. This structure has served the DNS adequately for many decades, so why change it?DNS and the DELEG Proposal
The DNS is a large-scale distributed database, where the internal structure of the databaase mirrors the hierarchical nature of the name space itself. In the database the points of delegation from one node to another are de noted by DNS Nameserver records. This structure has served the DNS adequately for many decades, so why change it?Nvidia’s “Grace” Arm CPU Holds Its Own Against X86 For HPC
In many ways, the “Grace” CG100 server processor created by Nvidia – its first true server CPU and a very useful adjunct for extending the memory space of its “Hopper” GH100 GPU accelerators – was designed perfectly for HPC simulation and modeling workloads. …
Nvidia’s “Grace” Arm CPU Holds Its Own Against X86 For HPC was written by Timothy Prickett Morgan at The Next Platform.
Adding new LLMs, text classification and code generation models to the Workers AI catalog

Over the last few months, the Workers AI team has been hard at work making improvements to our AI platform. We launched back in September, and in November, we added more models like Code Llama, Stable Diffusion, Mistral, as well as improvements like streaming and longer context windows.
Today, we’re excited to announce the release of eight new models.
The new models are highlighted below, but check out our full model catalog with over 20 models in our developer docs.
Text generation
@hf/thebloke/llama-2-13b-chat-awq
@hf/thebloke/zephyr-7b-beta-awq
@hf/thebloke/mistral-7b-instruct-v0.1-awq
@hf/thebloke/openhermes-2.5-mistral-7b-awq
@hf/thebloke/neural-chat-7b-v3-1-awq
@hf/thebloke/llamaguard-7b-awq
Code generation
@hf/thebloke/deepseek-coder-6.7b-base-awq
@hf/thebloke/deepseek-coder-6.7b-instruct-awq
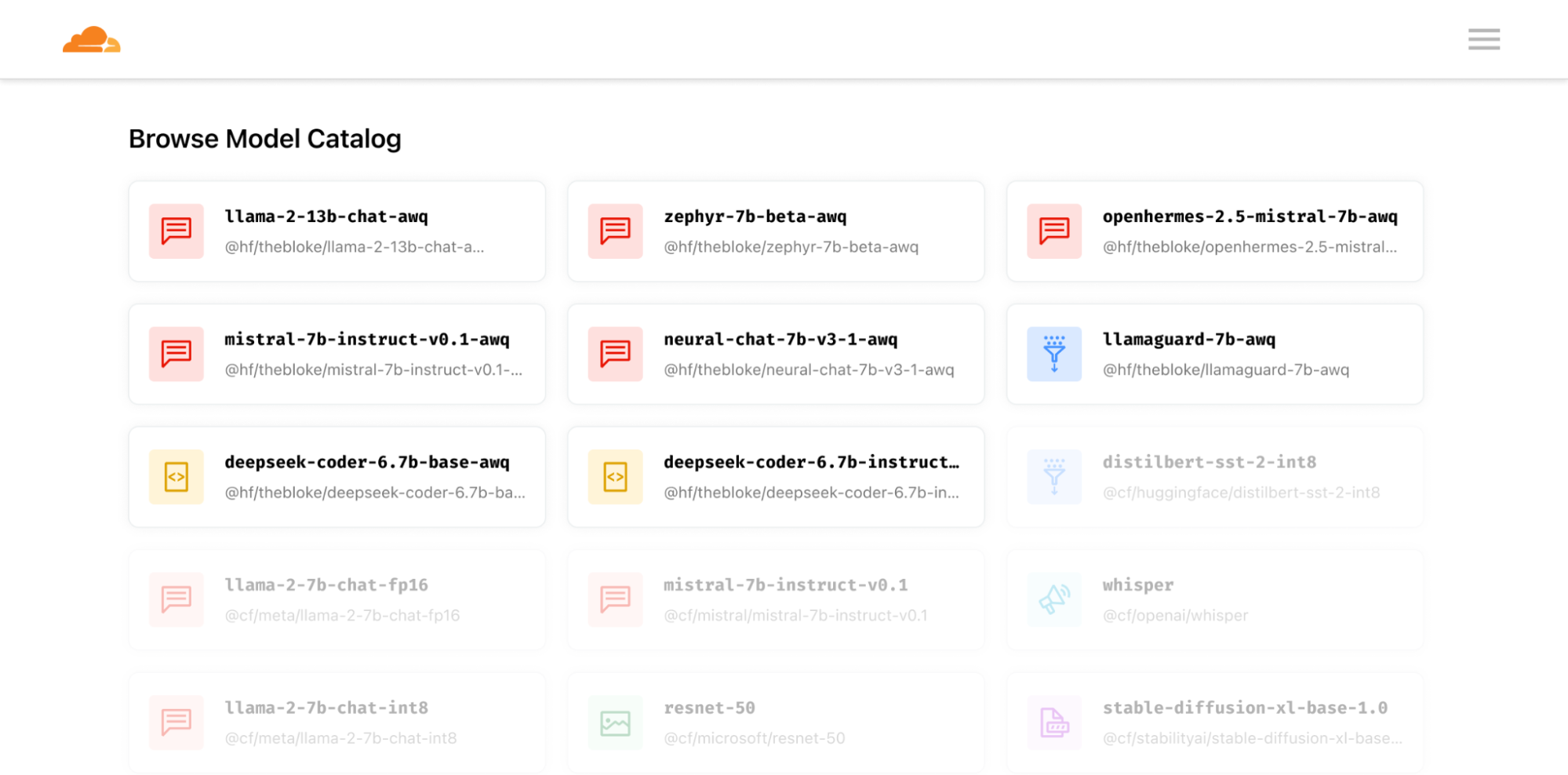
Bringing you the best of open source
Our mission is to support a wide array of open source models and tasks. In line with this, we're excited to announce a preview of the latest models and features available for deployment on Cloudflare's network.
One of the standout models is deep-seek-coder-6.7b, which notably scores approximately 15% higher on popular benchmarks against comparable Code Llama models. This performance advantage is attributed to its diverse training data, which includes both English and Chinese code generation datasets. In addition, the openhermes-2.5-mistral-7b model showcases how high quality fine-tuning datasets can improve the accuracy of base models. Continue reading
HS064: Mastering the Art of Strategy and Architecture with Pocket Change
Welcome, trailblazers and visionaries! Today, I’m thrilled to unpack a treasure trove of wisdom that zooms into the exhilarating realm of strategy architecture and the craft of sculpting strategy roadmaps on a shoestring budget. The Thrill of Resourcefulness In this episode, my esteemed co-host Johna and I dove headfirst into a challenge that plagues countless... Read more »Organizations Left Grappling for Solutions Amid Alarming Cloud Security Gaps
The convergence of a Zero Trust framework with enhanced collaboration between security and development teams is foundational to a robust cloud security posture.HW020: How We Got to Wi-Fi 7 and Where We Go From Here
To understand the newest standard, Wi-Fi 7, it helps to look back at Wi-Fi 5 and 6, and even forward to Wi-Fi 8. What’s the reasoning behind the updates? How have they been experienced at the ground level? Who should make the change and when? Host Keith Parsons and Wi-Fi expert Srikanth Subramanian touch on... Read more »BGP Labs: Use Multiple AS Numbers on the Same Router
Can you use BGP to connect to the global Internet without having a public BGP AS number? Of course, assuming your Internet Service Provider is willing to run BGP with a network using a private AS number. But what happens if you want to connect to two ISPs? It’s ridiculous to expect you’ll be able to persuade them to use the same private AS number.
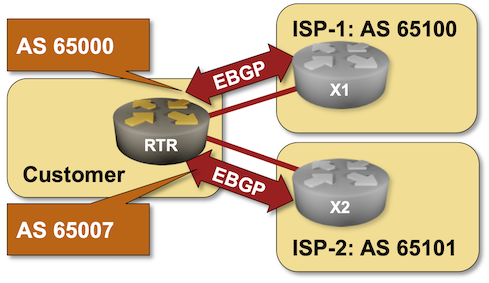
That’s one of the many use cases for the local-as functionality available in most BGP implementations. You can practice it in the Use Multiple AS Numbers on the Same Router lab exercise.
BGP Labs: Use Multiple AS Numbers on the Same Router
Can you use BGP to connect to the global Internet without having a public BGP AS number? Of course, assuming your Internet Service Provider is willing to run BGP with a network using a private AS number. But what happens if you want to connect to two ISPs? It’s ridiculous to expect you’ll be able to persuade them to use the same private AS number.

That’s one of the many use cases for the local-as functionality available in most BGP implementations. You can practice it in the Use Multiple AS Numbers on the Same Router lab exercise.
On Writing Complexity

I’ve been on a bit of a writer’s break after finishing the CCST book, but it’s time to rekindle my “thousand words a day” habit. As always, one part of this is thinking about how I write—is there anything I need to change? Tools, perhaps, or style?
What about the grade level complexity of my writing? I’ve never really paid attention to this, but I’m working on contributing to a site regularly that does. So maybe I should.
I tend to write to the tenth or eleventh-grade level, even when writing “popular material,” like blog posts. The recommended level is around the eighth-grade level. Is this something I need to change?
It seems the average person considers anything above the eighth-grade reading level “too hard” to read, so they give up. Every reading level calculation I’ve looked at essentially uses word and sentence length as proxies for complexity. Long words and sentences intimidate people.
On the other hand, measuring the reading grade level can seem futile. There are plenty of complex concepts described by one- and two-syllable words. Short sentences can still have lots of meaning.
Further, the reading grade level does not tell you if the sentence makes sense. Continue reading