Headcount: The Latest in Hirings, Firings, and Retirings — November 9, 2017
 Nutanix adds to its exec team and board; HPE names CIO to restructure IT.
Nutanix adds to its exec team and board; HPE names CIO to restructure IT.
 Nutanix adds to its exec team and board; HPE names CIO to restructure IT.
Nutanix adds to its exec team and board; HPE names CIO to restructure IT.
Nutanix has been on a journey for well over a year to transform itself from a supplier for software for hyperconverged infrastructure to a company with a platform that allows enterprises to build private datacenter environments that give them the same kinds of tools, automation, agility, scalability and consumption options that they can find in public clouds like Amazon Web Services and Microsoft Azure.
Nutanix was one of several vendors whose software helped propel the fast-growing hyperconverged infrastructure space through partnerships with such top-tier system OEMs like Dell EMC, IBM and Lenovo, and is among the last independent companies standing, …
Nutanix Expands Adds Breadth to Cloud Platform was written by Jeffrey Burt at The Next Platform.
No matter the starting point, one day we'll arrive at a true virtual network.
 Enterprises see security risks, unfamiliar workflow, replacing legacy products, and IoT as barriers to container adoption.
Enterprises see security risks, unfamiliar workflow, replacing legacy products, and IoT as barriers to container adoption.
 Now you can get deep visibility into your XenApp and XenDesktop deployment from a single web-based console as part of Citrix NetScaler Management and Analytics Service. The same features that have been tried and tested in the on-premises version of NetScaler MAS now are available in a Citrix Cloud service. And best of all, you... Read more →
Now you can get deep visibility into your XenApp and XenDesktop deployment from a single web-based console as part of Citrix NetScaler Management and Analytics Service. The same features that have been tried and tested in the on-premises version of NetScaler MAS now are available in a Citrix Cloud service. And best of all, you... Read more →
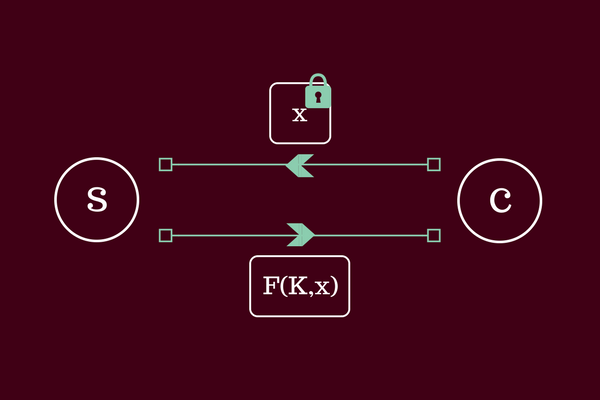
This is a guest post by Alex Davidson, a PhD student in Cryptography at Royal Holloway, University of London, who is part of the team that developed Privacy Pass. Alex worked at Cloudflare for the summer on deploying Privacy Pass on the Cloudflare network.
During a recent internship at Cloudflare, I had the chance to help integrate support for improving the accessibility of websites that are protected by the Cloudflare edge network. Specifically, I helped develop an open-source browser extension named ‘Privacy Pass’ and added support for the Privacy Pass protocol within Cloudflare infrastructure. Currently, Privacy Pass works with the Cloudflare edge to help honest users to reduce the number of Cloudflare CAPTCHA pages that they see when browsing the web. However, the operation of Privacy Pass is not limited to the Cloudflare use-case and we envisage that it has applications over a wider and more diverse range of applications as support grows.
In summary, this browser extension allows a user to generate cryptographically ‘blinded’ tokens that can then be signed by supporting servers following some receipt of authenticity (e.g. a CAPTCHA solution). The browser extension can then use these tokens to ‘prove’ honesty in future communications with the Continue reading


Cloudflare supports Privacy Pass, a recently-announced privacy-preserving protocol developed in collaboration with researchers from Royal Holloway and the University of Waterloo. Privacy Pass leverages an idea from cryptography — zero-knowledge proofs — to let users prove their identity across multiple sites anonymously without enabling tracking. Users can now use the Privacy Pass browser extension to reduce the number of challenge pages presented by Cloudflare. We are happy to support this protocol and believe that it will help improve the browsing experience for some of the Internet’s least privileged users.
The Privacy Pass extension is available for both Chrome and Firefox. When people use anonymity services or shared IPs, it makes it more difficult for website protection services like Cloudflare to identify their requests as coming from legitimate users and not bots. Privacy Pass helps reduce the friction for these users—which include some of the most vulnerable users online—by providing them a way to prove that they are a human across multiple sites on the Cloudflare network. This is done without revealing their identity, and without exposing Cloudflare customers to additional threats from malicious bots. As the first service to support Privacy Continue reading
IT teams are inundated by security alerts, but artificial intelligence can help manage threats.
on November 8, oVirt 4.2 saw the introduction of an important behind-the-scenes enhancement.
The change is associated with the exchange of information between the engine and the VDSM. It addresses the issue of multiple abstraction layers, with each layer needing to convert its input into a suitably readable format in order to report to the next layer.
This change improves data communication between the engine and Libvirt - the tool that manages platform virtualization.
Previously, the configuration file for a newly created virtual machine (VM) originated in the engine as a map or dictionary. Then, in the VDSM, it was converted into an XML file that was readable by Libvirt. This process required a greater coding effort which in turn slowed down the development process.
Now, this map or dictionary has been replaced by engine XML, an XML configuration file that complies with the Libvirt API. VDSM now simply routes this Libvirt-readable file to/from Libvirt, in VM lifecycle (virt) related flows.
As an oVirt user, it’s business as usual.
However, if you are a developer dealing with debugging issues that involve running a VM, simply be aware that the Domain XML is now generated by ovirt-engine, Continue reading
It’s always great to see students enrolled in Building Network Automation Solutions online course using ideas from my sample playbooks to implement a wonderful solution that solves a real-life problem.
James McCutcheon did exactly that: he took my LLDP-to-Graph playbook and used it to graph VLANs stretching across multiple switches (and provided a good description of his solution).
The Internet of Things (IoT) is a major buzzword around the Internet industry and the broader technology and innovation business arenas. We are often asked what the IETF is doing in relation to IoT and in this Rough Guide to IETF 100 post I’d like to highlight some of the relevant sessions scheduled during the upcoming IETF 100 meeting in Singapore. Check out the IETF Journal IoT Category, the Internet Society’s IoT page, or the Online Trust Alliance IoT page for more details about many of these topics.
The Thing-to-Thing Research Group (T2TRG) investigates open research issues in turning the IoT into reality. The research group will be holding a half-day joint meeting with the Open Connectivity Foundation (OCF) on the Friday before IETF, and they will also be meeting on Tuesday afternoon in Singapore to report out on their recent activities. Included on the agenda is the upcoming Workshop on Decentralized IoT Security and Standards (DISS). This workshop will be held in conjunction with the Network and Distributed System Security (NDSS) Symposium on 18 February 2018 in San Diego, CA, USA. The DISS workshop will gather researchers and the open standards community together to help address Continue reading
 Larger operators are letting AT&T lead, for now.
Larger operators are letting AT&T lead, for now.
It is going to be a busy week for chip maker Qualcomm as it formally jumps from smartphones to servers with its new “Amberwing” Centriq 2400 Arm server processor during the same week that it has received an unsolicited $130 billion takeover offer from sometimes rival chipmaker Broadcom.
The Centriq 2400 is the culmination of over four years of work and investment, which according to the experts in the semiconductor industry we have talked to, easily took on the order of $100 million to $125 million to make happen – remember there was a prototype as well as the …
Qualcomm’s Amberwing Arm Server Chip Finally Takes Flight was written by Timothy Prickett Morgan at The Next Platform.
One of the arguments Intel officials and others have made against Arm’s push to get its silicon designs into the datacenter has been the burden it would mean for enterprises and organizations in the HPC field that would have to modify application codes to get their software to run on the Arm architecture.
For HPC organizations, that would mean moving the applications from the Intel-based and IBM systems that have dominated the space for years, a time-consuming and possibly costly process.
Arm officials over the years have acknowledged the challenge, but have noted their infrastructure’s embrace of open-source software and …
Arm Smooths the Path for Porting HPC Apps was written by Nicole Hemsoth at The Next Platform.
One of the nicer perks I have here at Cloudflare is access to the latest hardware, long before it even reaches the market.
Until recently I mostly played with Intel hardware. For example Intel supplied us with an engineering sample of their Skylake based Purley platform back in August 2016, to give us time to evaluate it and optimize our software. As a former Intel Architect, who did a lot of work on Skylake (as well as Sandy Bridge, Ivy Bridge and Icelake), I really enjoy that.
Our previous generation of servers was based on the Intel Broadwell micro-architecture. Our configuration includes dual-socket Xeons E5-2630 v4, with 10 cores each, running at 2.2GHz, with a 3.1GHz turbo boost and hyper-threading enabled, for a total of 40 threads per server.
Since Intel was, and still is, the undisputed leader of the server CPU market with greater than 98% market share, our upgrade process until now was pretty straightforward: every year Intel releases a new generation of CPUs, and every year we buy them. In the process we usually get two extra cores per socket, and all the extra architectural features such upgrade brings: hardware AES and CLMUL in Westmere, Continue reading