NB456: China Flexes Tech Muscles With 1.2Tb Backbone; Will CISOs Mitigate Risk Or Liability?
China demonstrates the strength of its home-grown technology industry by announcing a 1.2Tbit Internet backbone that stretches 3,000 kilometers, Fortinet warns of a 9.8 severity bug in its SIEM product, and we continue our ongoing discussion about the precarious role of the CISO, plus more tech news, in this episode of the Network Break podcast.
The post NB456: China Flexes Tech Muscles With 1.2Tb Backbone; Will CISOs Mitigate Risk Or Liability? appeared first on Packet Pushers.
Zscaler Study Finds Companies are Rushing Towards Generative AI Without Considering the Risks
The research underlines the urgency for businesses to balance the potential of gen AI tools with effective security strategies to ensure safe usage of this emerging technology.2024, the year of elections

2024 is a year of elections, with more than 70 elections scheduled in 40 countries around the world. One of the key pillars of democracy is trust. To that end, ensuring that the Internet is trusted, secure, reliable, and accessible for the public and those working in the election space is critical to any free and fair election.
Cloudflare has considerable experience in gearing up for elections and identifying how our cyber security tools can be used to help vulnerable groups in the election space. In December 2022, we expanded our product set to include Zero Trust products to assist these groups against new and emerging threats. Over the last few years, we’ve reported on our work in protecting a range of election entities and as we prepare for the 2024 elections, we want to provide insight into attack trends we’ve seen against these groups to understand what to expect in the next year.
For this blog post, we identified cyber attack trends for a variety of groups in the elections space based in the United States, as many of our Cloudflare Impact projects provide services to these groups. These include U.S. state and local government websites protected under Continue reading
VXLAN/EVPN Layer-3 Handoff (L3Out) on Arista EOS
A while ago, I published a blog post describing how to establish a LAN/WAN L3 boundary in VXLAN/EVPN networks using Cisco NX-OS. At that time, I promised similar information for Arista EOS. Here it is, coming straight from Massimo Magnani. The useful part of what follows is his; all errors were introduced during my editing process.
In the cases I have dealt with so far, implementing the LAN-WAN boundary has the main benefit of limiting the churn blast radius to the local domain, trying to impact the remote ones as little as possible. To achieve that, we decided to go for a hierarchical solution where you create two domains, local (default) and remote, and maintain them as separate as possible.
VXLAN/EVPN Layer-3 Handoff (L3Out) on Arista EOS
A while ago, I published a blog post describing how to establish a LAN/WAN L3 boundary in VXLAN/EVPN networks using Cisco NX-OS. At that time, I promised similar information for Arista EOS. Here it is, coming straight from Massimo Magnani. The useful part of what follows is his; all errors were introduced during my editing process.
In the cases I have dealt with so far, implementing the LAN-WAN boundary has the main benefit of limiting the churn blast radius to the local domain, trying to impact the remote ones as little as possible. To achieve that, we decided to go for a hierarchical solution where you create two domains, local (default) and remote, and maintain them as separate as possible.
Weekend Reads 111923
Bad queries tend to propagate to the root zone due to the hierarchical nature of DNS, so studying traffic at a root server can provide key insights into overall network usage.
This blog covers an interesting case of suspected abuse in a gTLD registry between February and April 2023.
Gartner has raised the specter of departments outside of tech running their own IT Continue reading
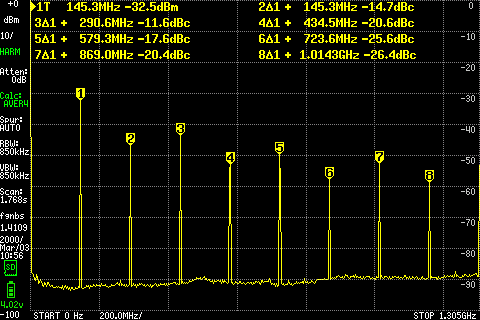
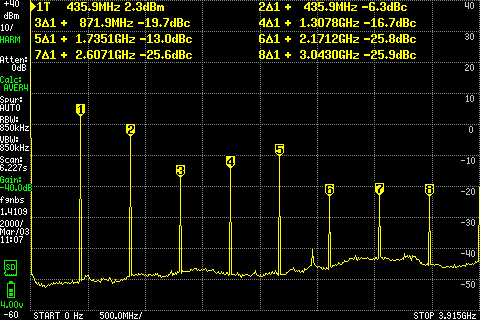
SDR transmit and clean signals
If you have a transmit capable SDR, you may have heard that you need to filter its output, before transmitting to the world. Certainly before amplifying the signal.
I have a TinySA Ultra spectrum analyzer, and will here show you some screenshots about just how true that is.
I tested this with my USRP B200, transmitting a pure carrier around 145MHz and 435MHz.
Oh, and a word of caution: If you want to replicate this, make sure to add an inline attenuator, to not damage your spectrum analyzer. I had a cheap 40dB one, but the values in the graphs have been adjusted to show the real signal strength, as if I hadn’t.
tl;dr
- Harmonics can be almost as strong as the fundamental. You need to filter these.
- Transmitting at maximum output gain may cause lots of unwanted signals right around your fundamental. You cannot filter these. You need to not generate them.
Harmonics
Reducing the output gain did not meaningfully fix the problem. The best I saw from using half output gain was to make the strongest harmonic 9dB less than the fundamental. That’s way too strong.
I added a cheap band pass filter (FBP-144), which made Continue reading
AX.25 and 9600bps G3RUH decoding
I’ve been coding more on my rust SDR framework, and want to improve my ability to send/receive data packets efficiently and reliably.
There are two main ways I use learn to do this better: designing a new protocol, and making the best implementation possible for an existing one. This post is about refining the latter.
AX.25 and APRS
First a detour, or background.
AX.25 is the standard amateur radio data protocol. It’s mostly an OSI layer 2-4 protocol, mashing the layers together into one. Contrast this with IP, which just encapsulates the next layer.
Layer 3 (IP stack equivalent: IP itself) consists of the ability to
add, in addition to source and destination, a variable number of
intermediate repeaters. This allows limited source routing. In APRS
the repeaters are usually not named, but instead uses “virtual” hops
like WIDE1-1.
Layer 4 (IP stack equivalent: TCP and UDP) allows both connected and disconnected communication channels. In my experience connected AX.25 works better over slow simplex radio than TCP. If TCP was ever optimized for high delay low bandwidth, it’s not anymore.
For the physical layer, there are three main “modems”:
-
300 baud bell 103, used Continue reading
Pushing The Limits Of HPC And AI Is Becoming A Sustainability Headache
As Moore’s law continues to slow, delivering more powerful HPC and AI clusters means building larger, more power hungry facilities. …
The post Pushing The Limits Of HPC And AI Is Becoming A Sustainability Headache first appeared on The Next Platform.
Pushing The Limits Of HPC And AI Is Becoming A Sustainability Headache was written by Timothy Prickett Morgan at The Next Platform.
HN710: The Future Of Networking With Brad Casemore – Part 2
We continue our Future of Networking series with part two of our conversation with Brad Casemore. Now retired, Brad has participated in the industry as both a technologist and IDC analyst. In this episode we look at the rise of zero trust and what it means for campus networking. We discuss how geopolitics influences IT... Read more »HN710: The Future Of Networking With Brad Casemore – Part 2
Analyst Brad Casemore offers his takes on the rise of zero trust, the influence of geopolitics on IT, what's driving the need for visibility and observability on prem and in the cloud, and whether 5G will ever live up to the hype.
The post HN710: The Future Of Networking With Brad Casemore – Part 2 appeared first on Packet Pushers.
SC23 Over 6 Terabits per Second of WAN Traffic
The world’s fastest temporary internet service gets turned on in Denver for one week only describes the SCinet temporary network built to support the The International Conference for High Performance Computing, Networking, Storage, and Analysis (SC23) this week in Denver. The SC23 WAN Stress Test chart demonstrates that the provisioned 6.71 terabits bits per second capacity was pushed to the limits. SC23 SCinet traffic describes the architecture of the real-time monitoring system used to comprehensively monitor the SCinet network and generate these charts. This chart shows that over 175 Petabytes of data were transfered during the show.SC23 Dropped packet visibility demonstration describes a joint demonstration by InMon Corp and Arista Networks of one of newest developments in sFlow telemetry, identifying every dropped packet, the reason it was dropped, and the location it was dropped across all the switches in real-time. SC23 WiFi Traffic Heatmap shows a real-time view of WiFi usage at the conference displayed on a conference floorplan. Finally, SC23 Data Transfer Node TCP Metrics demonstrates how standard metrics maintained by the Linux kernel can be used to augment sFlow telemetry and track the performance of large science data transfers.Top US Gov’t CISO Details Zero-Trust Strategy Race
After an executive order mandated that US federal agencies adopt a zero-trust security strategy by 2024, security leaders had to spring to action quickly.How to execute an object file: Part 4, AArch64 edition

Translating source code written in a high-level programming language into an executable binary typically involves a series of steps, namely compiling and assembling the code into object files, and then linking those object files into the final executable. However, there are certain scenarios where it can be useful to apply an alternate approach that involves executing object files directly, bypassing the linker. For example, we might use it for malware analysis or when part of the code requires an incompatible compiler. We’ll be focusing on the latter scenario: when one of our libraries needed to be compiled differently from the rest of the code. Learning how to execute an object file directly will give you a much better sense of how code is compiled and linked together.
To demonstrate how this was done, we have previously published a series of posts on executing an object file:
- How to execute an object file: Part 1
- How to execute an object file: Part 2
- How to execute an object file: Part 3
The initial posts are dedicated to the x86 architecture. Since then the fleet of our working machines has expanded to include a large and growing number of ARM CPUs. This Continue reading
Saying Goodbye to the Full Stack Journey
In January 2016, I published the first-ever episode of the Full Stack Journey podcast. In October 2023, the last-ever episode of the Full Stack Journey podcast was published. After almost seven years and 83 episodes, it was time to end my quirky, eclectic, and unusual podcast that explored career journeys alongside various technologies, products, and open source projects. In this post, I wanted to share a few thoughts about saying goodbye to the Full Stack Journey.
First and foremost, let me say that I really enjoyed being the host of the Full Stack Journey podcast—far more than I expected I would, if I’m honest. While I didn’t love the logistics of producing a podcast, I did love getting to talk with folks, hear their stories, and learn about new things. So, while part of me is thankful to have a little less work to do, another part—a larger part—is sad to see it end.
That being said, some of you are probably wondering why it ended. I mentioned that I didn’t enjoy the logistics of producing a podcast; specifically, I didn’t enjoy audio editing. Some folks like it, but I didn’t. It was truly a chore for me. That was Continue reading
Video: Outages Caused by Bugs in BGP Implementations
The previous BGP-related videos described how fat fingers and malicious actors cause Internet outages.
Today, we’ll focus on the impact of bugs in BGP implementations, from malformed AS paths to mishandled transitive attributes. The examples in the video are a few years old, but you can see similar things in the wild in 2023.
Video: Outages Caused by Bugs in BGP Implementations
The previous BGP-related videos described how fat fingers and malicious actors cause Internet outages.
Today, we’ll focus on the impact of bugs in BGP implementations, from malformed AS paths to mishandled transitive attributes. The examples in the video are a few years old, but you can see similar things in the wild in 2023.
What To Do When You Can’t Get Nvidia H100 GPUs
In a world where allocations of “Hopper” H100 GPUs coming out of Nvidia’s factories are going out well into 2024, and the allocations for the impending “Antares” MI300X and MI300A GPUs are probably long since spoken for, anyone trying to build a GPU cluster to power a large language model for training or inference has to think outside of the box. …
The post What To Do When You Can’t Get Nvidia H100 GPUs first appeared on The Next Platform.
What To Do When You Can’t Get Nvidia H100 GPUs was written by Timothy Prickett Morgan at The Next Platform.