Some notes on a Hamilton election
At least one elector for Trump has promised to switch his vote, becoming a "Hamilton Elector". Assuming 36 more electors (about 10% of Trump's total) do likewise, and Trump fails to get the 270 absolute majority, then what happens? Since all of the constitutional law scholars I follow haven't taken a stab at this, I thought I would write up some notes.Foreign powers and populists
In Federalist #68, Alexander Hamilton laid out the reasons why electors should switch their vote. The founders feared bad candidates unduly influenced by foreign powers, and demagogues. Trump is unabashedly both. He criticizes our own CIA claiming what every American knows, that Russia interfered in our election. Trump is the worst sort of populist demagogue, offering no solution to problems other than he'll be a strong leader.
Therefore, electors have good reasons to change their votes. I'm not suggesting they should, only that doing so is consistent with our Constitutional principles and history.
So if 10% of Trump's electors defect, how would this actually work?
Failure to get 270 vote absolute majority (math)
Well, to start with, let's count up the number of electors. Each state gets one elector for every House Representative Continue reading
[minipost] Capturing bidirectional traffic of virtual machine (VMs) on vmWare ESX 6.x
Here I was getting a trouble with communication between an ESX virtual machine and the nearby switch (Nuage/DCN controller VM talking with a VTEP switch if someone is interested) and because that switch was direct destination of the control plane packets (OVSDB over TCP) I was not having much success creating a mirroring interface on the switch. So I learned how to capture a specific virtual machine traffic directly on the ESXi host’s SSH console and to not forget that, I will document this here.
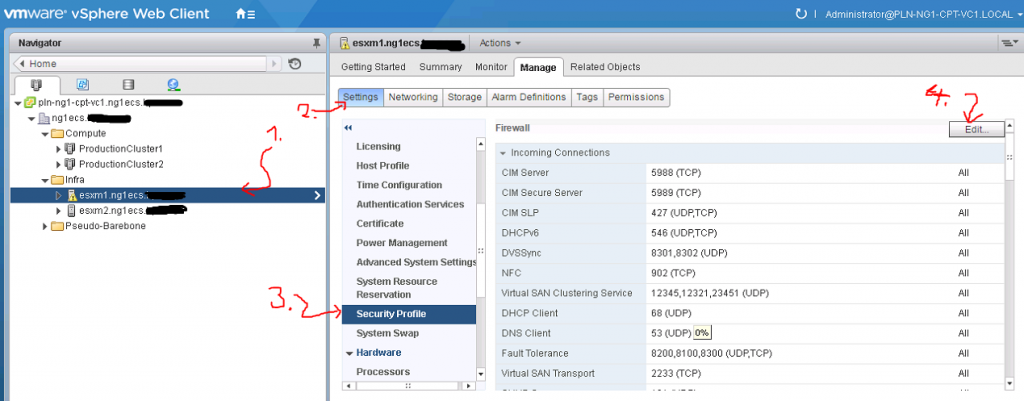
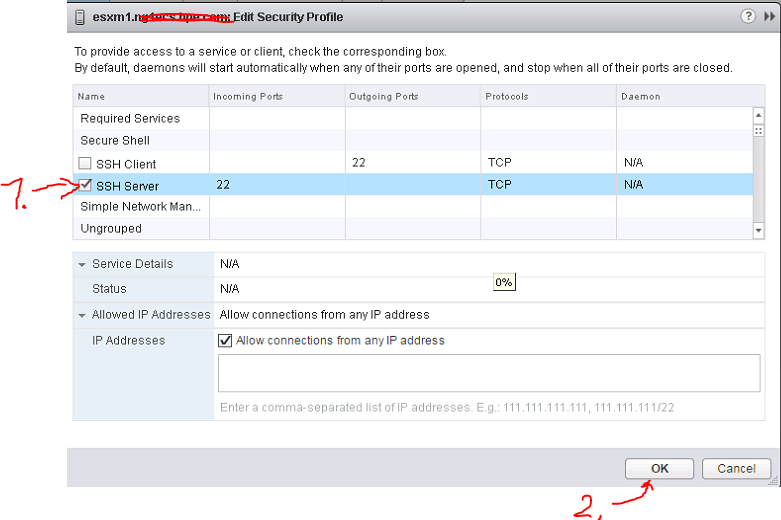
Step 1 – enable SSH to the ESX host
In most cases this is not running by default, so go to the ESXi server direct terminal or iLo and via “F2″enter system customization and enter troubleshooting section:
Right behind this menu should be “SSH Enable” option, and you simply hit that with enter 
ALTERNATIVE: If you have vCenter deployed, you can use its GUI to enable SSH on a specific host like this:
Step 2 – locating switchport ID
My virtual machine was called “DCN4.0R5_VSC1” and was simply connected to logical vswitch0 in Continue reading
Video: Arista Algomatch
Lots of interesting technology has been implemented in the latest Arista switches based on the Cavium Xpliant ASICs.
The post Video: Arista Algomatch appeared first on EtherealMind.
OpenStack SDN With OVN (Part 2) – Network Engineering Analysis
In this post we will see how OVN implements virtual networks for OpenStack. The structure of this post is such that starting from the highest level of networking abstraction we will delve deeper into implementation details with each subsequent section. The biggest emphasis will be on how networking data model gets transformed into a set of logical flows, which eventually become OpenFlow flows. The final section will introduce a new overlay protocol GENEVE and explain why VXLAN no longer satisfies the needs of an overlay protocol.
Continue readingUtilities Could Reap Millions from IoT, Navigant Says
 Navigant says utilities should be to offer IoT-enabled managed services.
Navigant says utilities should be to offer IoT-enabled managed services.
CCIE/CCDE Re-certification Time Again – Go for it? … or Emeritus?
It is “that” time again. Time to start studying for one of the CCxE (CCIE/CCDE) re-certifications. Got my 1st CCIE back in 1997. A couple years later my CCIE SNA/IP. Then back in 2009 I passed my “favorite E” – the CCDE. And now? I’ll tell you a secret that I actually haven’t told anyone at all except for my wife. — I am so tired of studying for the writtens. I prefer spending my time getting my hands dirty in the lab at work in CPOC, learning new technologies, reading pcap files, technically reviewing books, writing blogs, making youtubes, CiscoLive….. Anything but studying… yet again…. just to pass a CCxE written. Especially now with the 10% “evolving technologies” add. For the past few months I’ve been trying so hard to get myself to sit down and do some studying. It has really been a struggle to get myself to study and I have rescheduled my exam twice so far. It has just been really hard to find the motivation when there are so many other things I’d prefer to be doing.
To make matters worse, each and every time I actually Continue reading
Worth Reading: FPGA Accelerated Cloud
The post Worth Reading: FPGA Accelerated Cloud appeared first on 'net work.
Red Hat’s Container Platform Lands on Google Cloud
 The companies team up to advance the Kubernetes cause.
The companies team up to advance the Kubernetes cause.
Tips for Troubleshooting Apps in Production with Docker Datacenter
If you have been using Docker for some time, after the initial phases of building Dockerfiles and running a container here and there, the real work begins in building, deploying and operating multi-container applications in a production environment. Are you operationally ready to take your application to production? Docker Datacenter provides an integrated management framework for your Dockerized environment and applications and when coupled with clear strategies in approaching and resolving anomalies, IT ops teams can be assured in successfully operationalizing Docker.
Let’s use a sports metaphor to approach troubleshooting:
- Pre-Game will cover the planning phase for your applications
- Game Time will cover troubleshooting tools available in Docker Datacenter
- Post-Game will discuss complementary tools to aid in ongoing insights
Pre-Game
Whether or not you are sports fan, you can appreciate the importance of the planning out any task. This is no different than what you would do for your applications. Health checks are a great way to provide a deeper level of insight into how your application is performing. Since Docker 1.12 there is a new HEALTHCHECK directive. We can use this directive to signal to the Docker Engine whether or not the application is healthy.
There are a two ways to implement the HEALTHCHECK Continue reading
Show 318: Future Of Networking With Doug Gourlay
The Future of Networking series continues with Doug Gourlay. He and Greg discuss the state of SDN and where its going. The post Show 318: Future Of Networking With Doug Gourlay appeared first on Packet Pushers.