0
The concern about securing the clusters has grown exponentially and one of the ways to secure it is by isolating the cluster from the Internet to lower the risk of eventual attack. Enterprises that deal with confidential customer data and work with regulatory agencies, such as financial and insurance institutions, require air gap environments for their clusters to create highly secure environments.
What’s an air gap?
The air gap is a security configuration in which the cluster, network, or workload will not have access to the Internet, unless it is explicitly authorized to do so. It is a highly controlled environment and prevents the cluster from establishing external connections without prior authorizations.
The diagram below shows an air gap network:
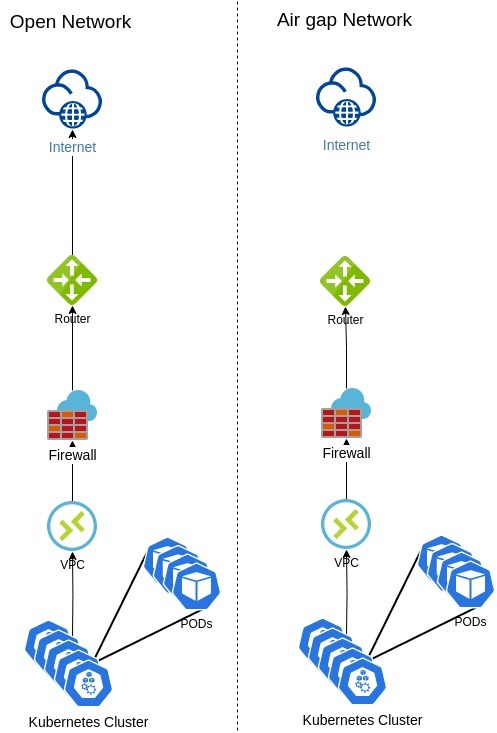
In a containerized environment, the cluster needs to pull the images for spinning up containers and it is usually done by pulling the images from a repository located on the cloud or Internet. However, as the air gap network doesn’t have access to the Internet, pulling images from the Internet is not possible. To address this situation, it is necessary to create a private registry/repository in the air gap network and pull all required images for the cluster into Continue reading
